2024-08-12 (MONDAY): XLOADER/FORMBOOK INFECTION
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2024-08-12-XLoader-Formbook-malspam-0312-UTC.eml.zip 776.4 kB (776,435 bytes)
- 2024-08-12-XLoader-Formbook-infection-traffic.pcap.zip 7.8 MB (7,765,631 bytes)
- 2024-08-12-XLoader-Formbook-malware.zip 1.5 MB (1,459,037 bytes)
HEADER LINE INFORMATION FROM THE EMAIL:
- Received: from inolab
MALWARE
FILES FROM THE INFECTION:
- SHA256 hash: c1bbaa4c8755f137f915709e710c62cc507ce4055cb2fb498d0656f82f66b31a
- File size: 727,946 bytes
- File name: THEMETAL NEW ORDERFOB$ _KORIA PORT.exe
- File type: RAR archive data, v5
- File description: RAR archive seen as the email attachment
- SHA256 hash: 992c1fa1d6584c711280bd3a519018a88c7766728ca0b51024484d9a83ef6d9c
- File size: 779,272 bytes
- File name: THEMETAL NEW ORDERFOB$ _KORIA PORT.exe
- File type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
- File description: 32-bit Windows executable (EXE) for XLoader/Formbook extracted from the above RAR archive
INFECTION TRAFFIC
DOMAINS FROM THE INFECTION TRAFFIC:
- www.354388
IMAGES
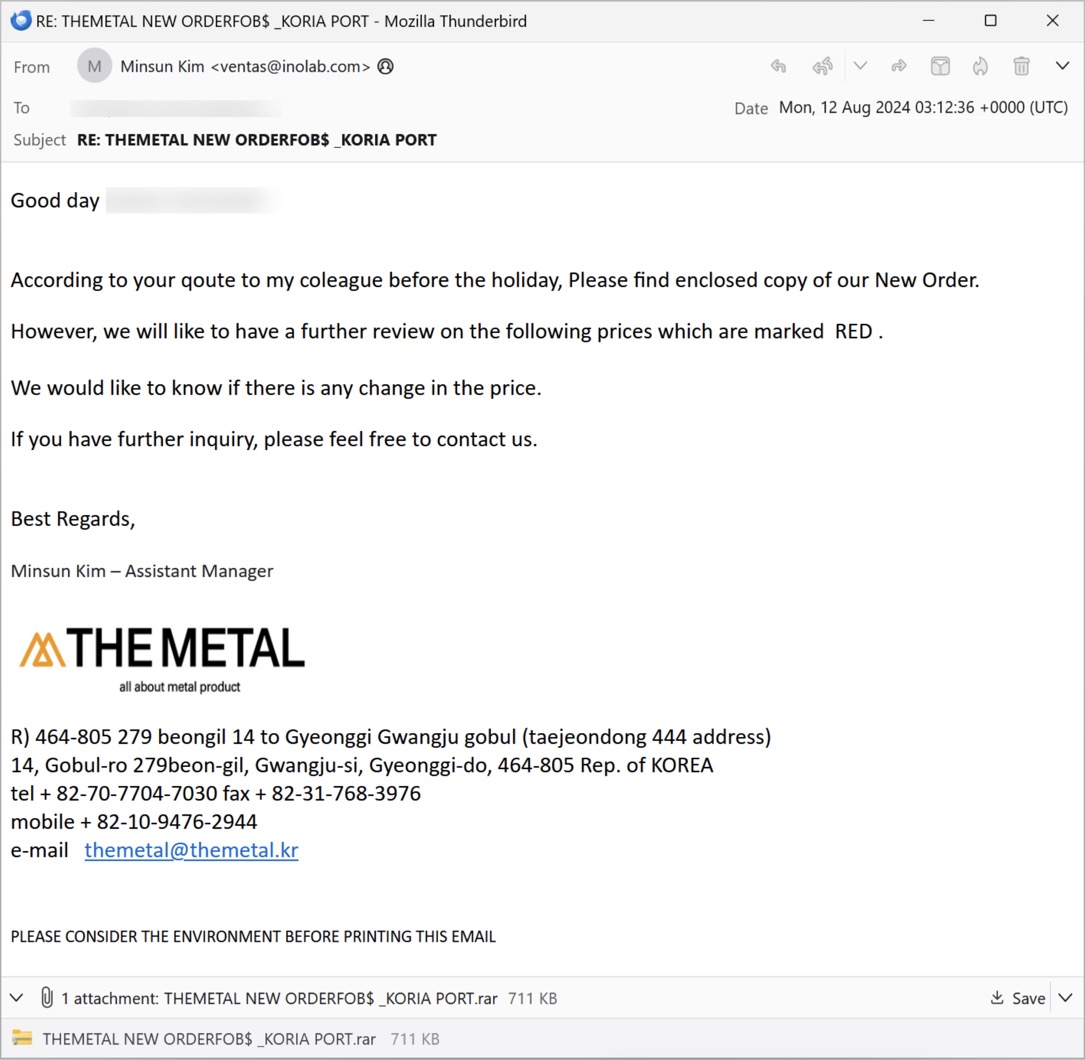
Shown above: Screenshot of the email in Thunderbird.
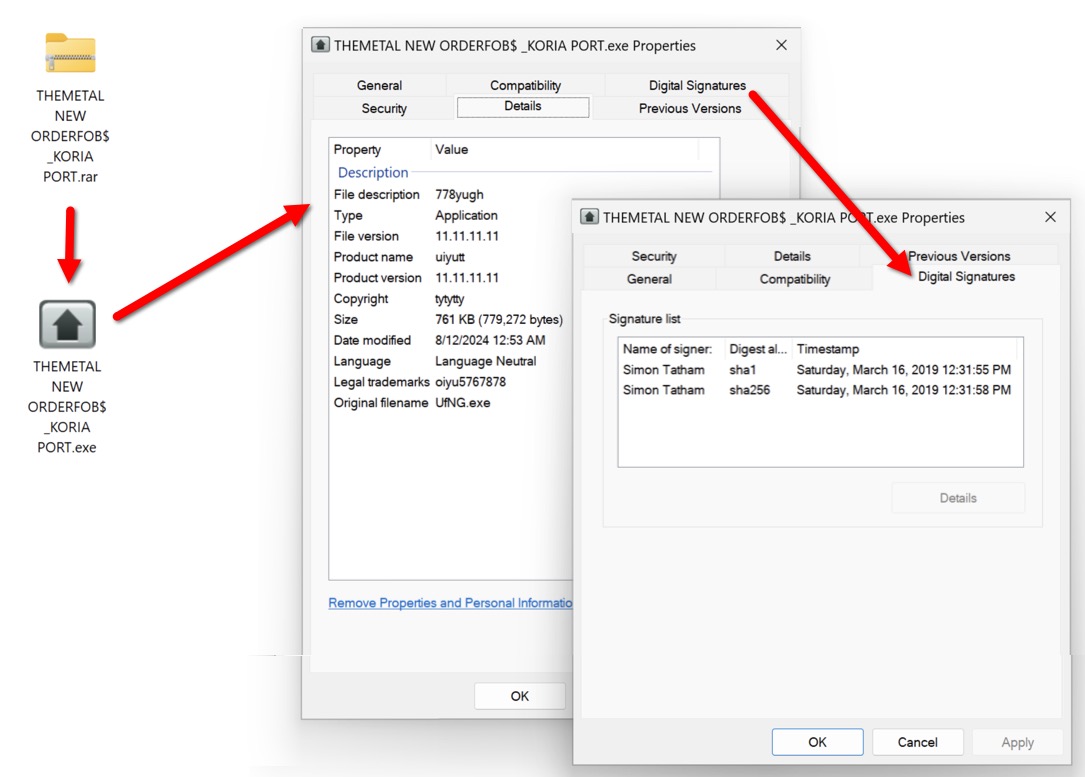
Shown above: Email attachment (RAR archive) and extracted Windows EXE file for XLoader/Formbook.
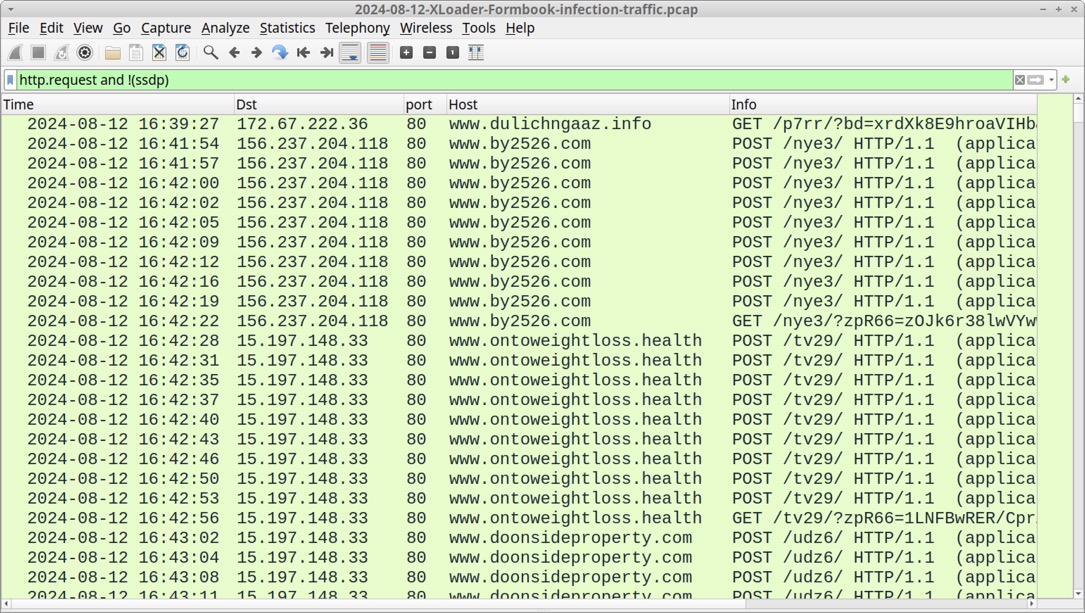
Shown above: Start of the infection traffic filtered in Wireshark.
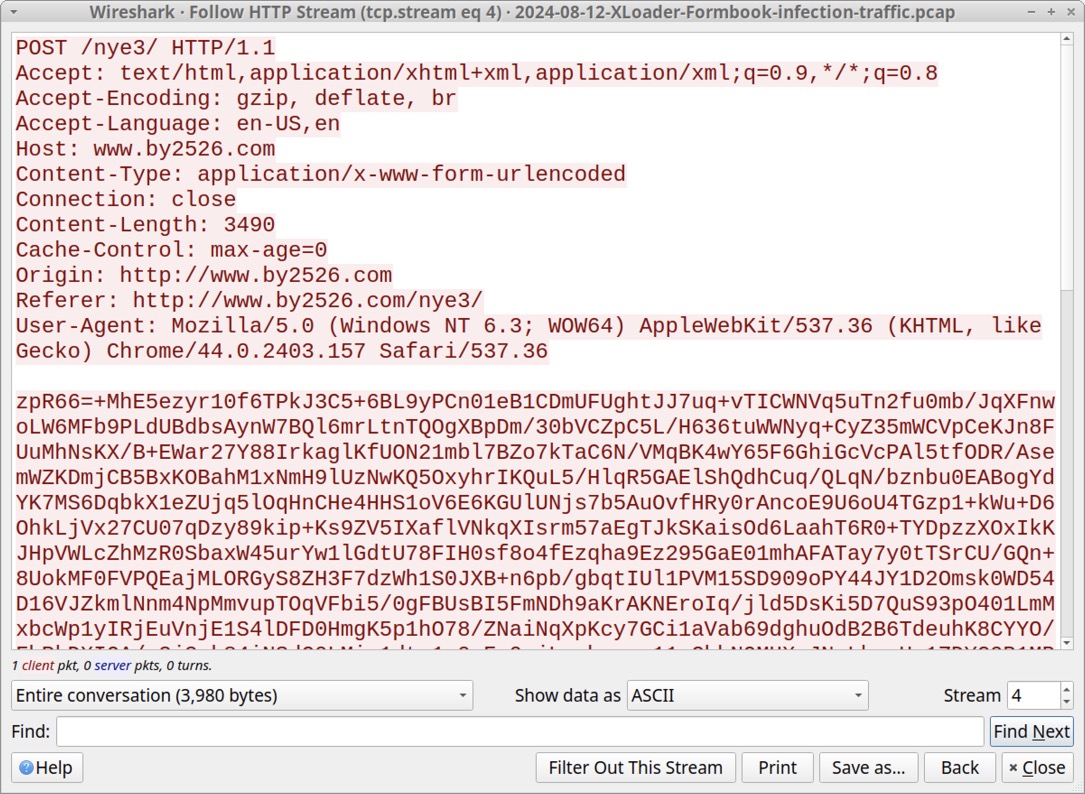
Shown above: TCP stream from one of the HTTP POST requests during the post-infection traffic.
Shown above: Traffic later from the infection, after the HTTP POST requests had stopped.
Click here to return to the main page.
