2024-08-29 (THURSDAY): PHISHING EMAIL AND TRAFFIC TO FAKE WEBMAIL LOGIN PAGE
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
- Every once in a while, I get a good example of a phishing email and web traffic to the fake login page.
- In this case, I could use HTTP instead of HTTPS for the URL to the fake webmail login page.
- So I recorded the packet capture (pcap), sanitized parts of the email, and posted the information here.
ASSOCIATED FILES:
- 2024-08-29-phishing-email-0415-UTC.eml.zip 1.7 kB (1,686 bytes)
- 2024-08-29-phishing-website-traffic.pcap.zip 721.9 kB (721,947 bytes)
HEADER LINE INFORMATION FROM THE EMAIL:
- Received: from s940027.srvape
[information removed]; Thu, 29 Aug 2024 04:15:53 +0000 (UTC)
by s940027.srvape[.]com (Postfix) with ESMTP id 617B56EE2A2
for <admin@malware-traffic-analysis[.]net>; Wed, 28 Aug 2024 12:06:27 +0200 (CEST)
TRAFFIC
URL FROM THE EMAIL:
- hxxps[:]//email.procedure[.]best/management.aspx?good=admin@malware-traffic-analysis[.]net
- NOTE: The server for this fake webmail page is behind Cloudflare, so the IP address is dynamic, somewhere within 172.67.0[.]0/16 or 104.21.0[.]0/16.
IMAGES
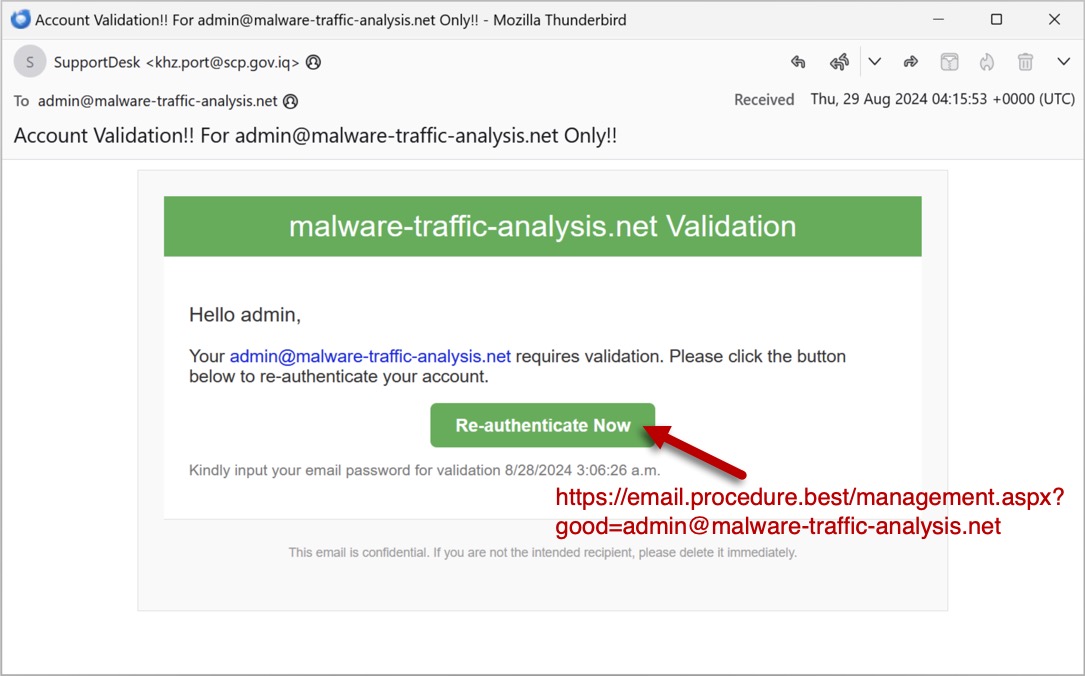
Shown above: Screenshot of the email.

Shown above: Viewing the website in Microsoft Edge using HTTP instead of HTTPS for the URL.
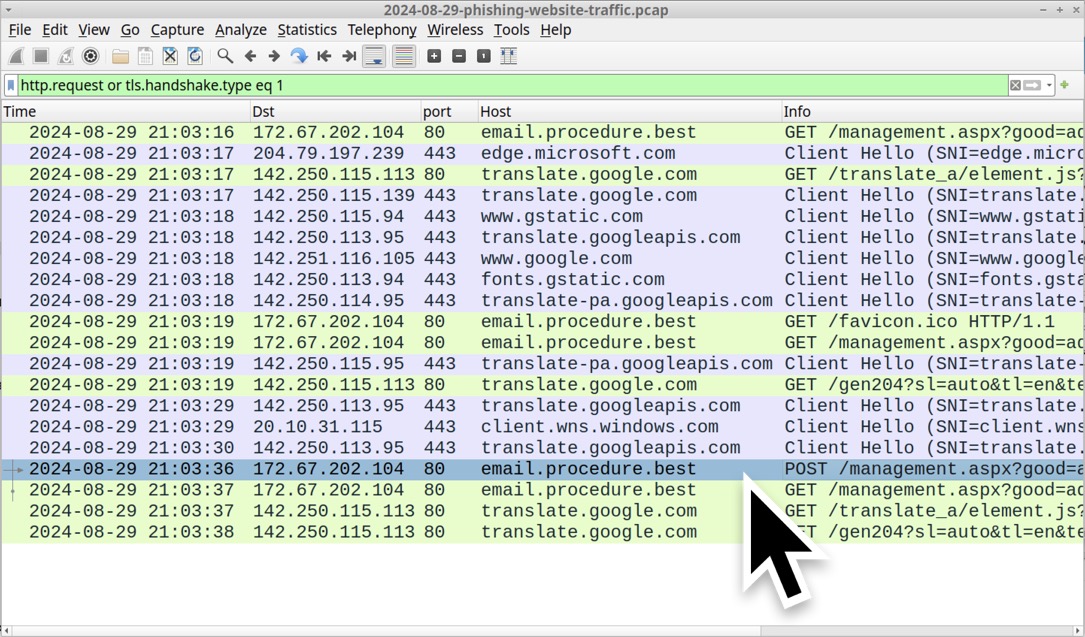
Shown above: Filtered in Wireshark, traffic from visiting the fake webmail page using HTTP instead of HTTPS for the URL.
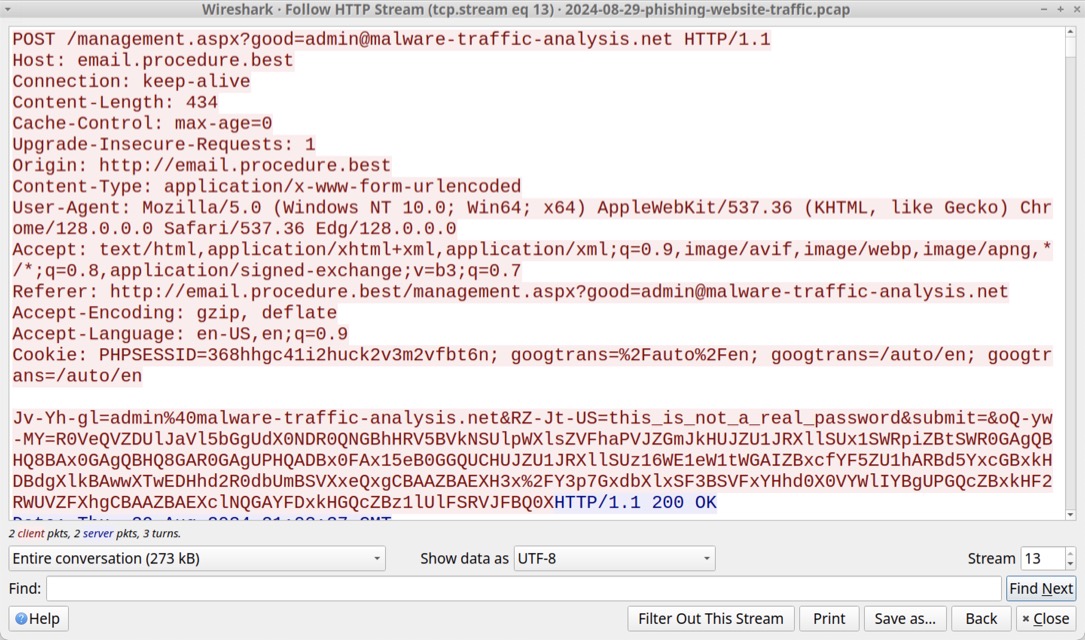
Shown above: TCP stream of the HTTP POST request sending my login credentials.
Click here to return to the main page.
