2025-03-26 (WEDNESDAY): SMARTAPESG TRAFFIC FOR FAKE BROWSER UPDATE LEADS TO NETSUPPORT RAT AND STEALC
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-03-26-IOCs-for-SmartApeSG-fake-browser-update-leads-to-NetSupport-RAT-and-StealC.txt.zip 2.2 kB (2,189 bytes)
- 2025-03-26-SmartApeSG-leads-to-NetSupport-RAT-and-StealC.pcap.zip 35.7 MB (35,733,687 bytes)
- 2025-03-26-malware-for-NetSupport-RAT-and-StealC.zip 13.1 MB (13,093,505 bytes)
IMAGES
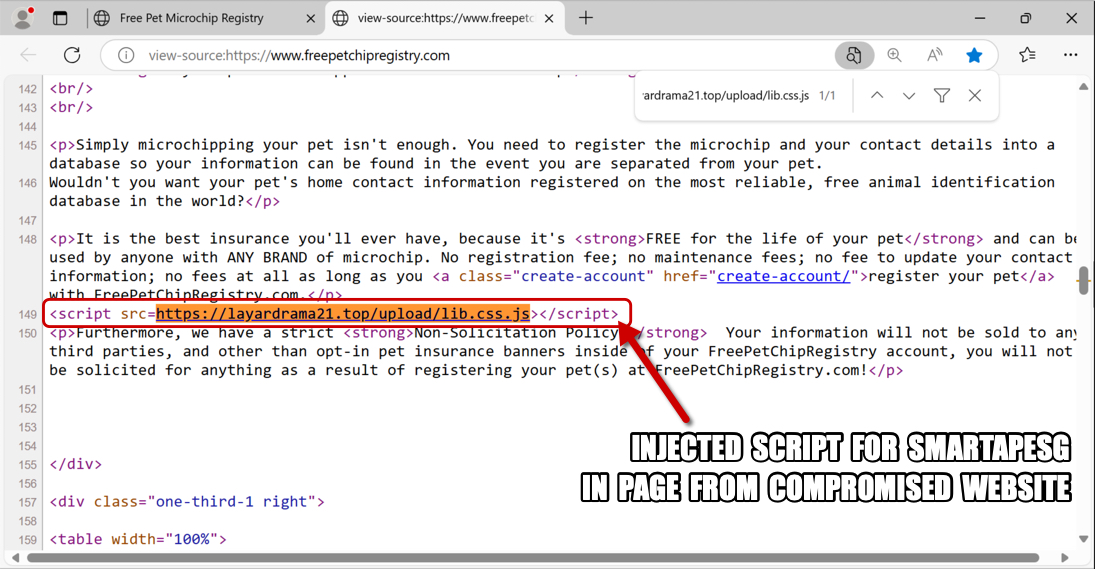
Shown above: Injected script for SmartApeSG in page from compromised website.
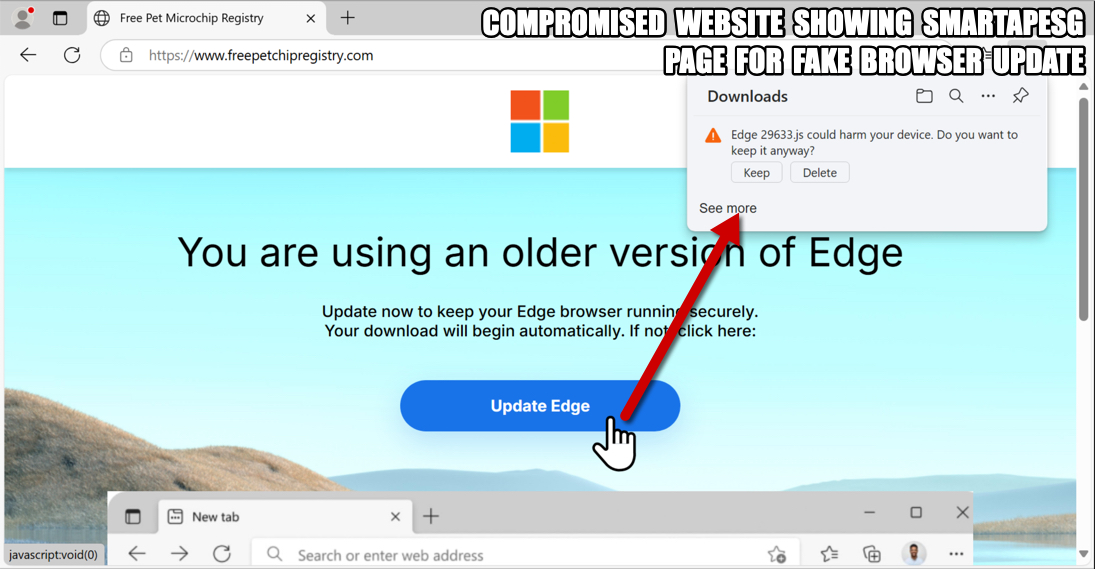
Shown above: Compromised site showing SmartApeSG page for fake browser update.
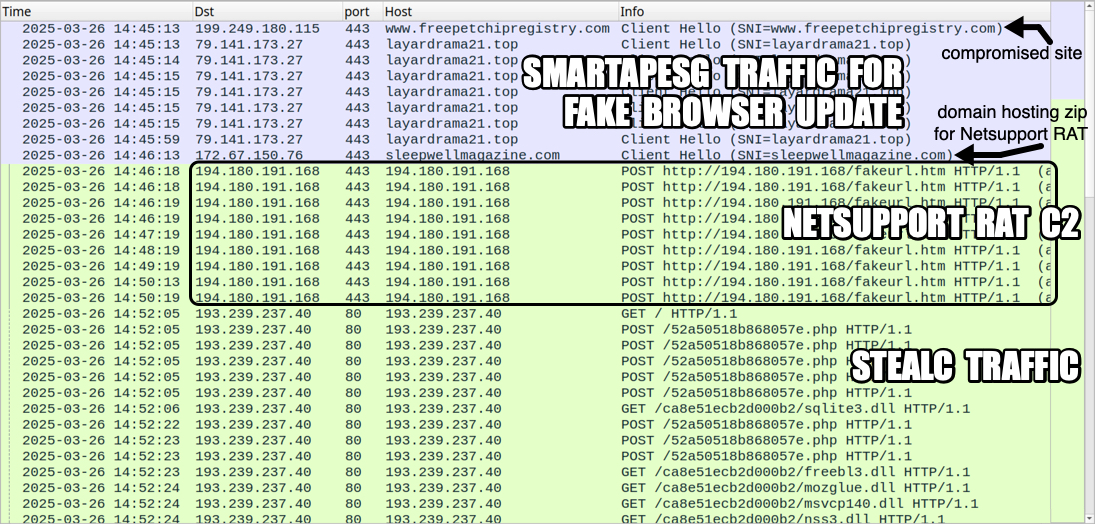
Shown above: Traffic from an infection filtered in Wireshark.
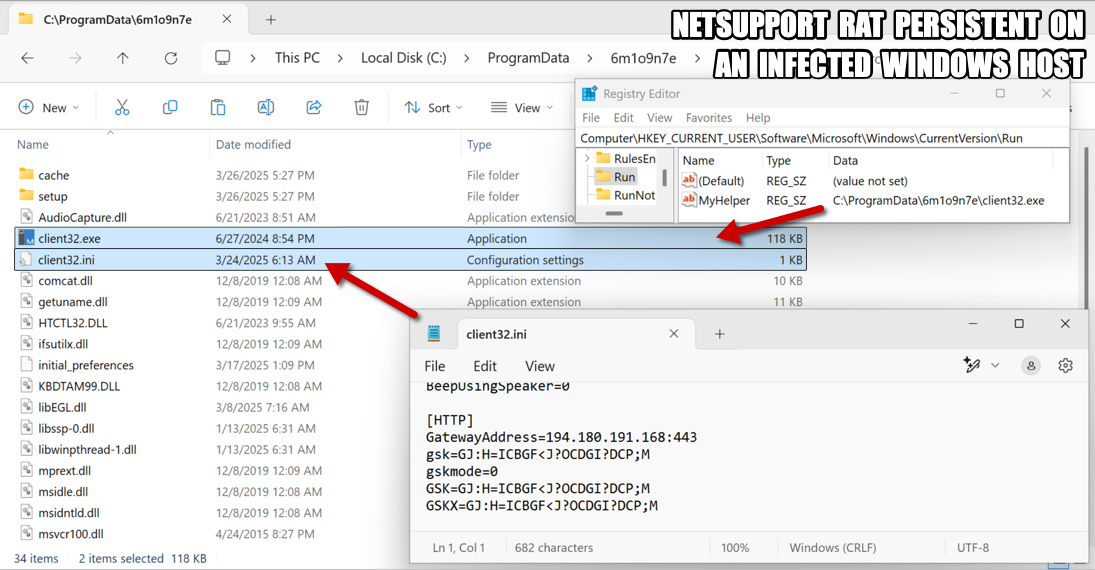
Shown above: NetSupport RAT malware persistent on an infected Windows host.
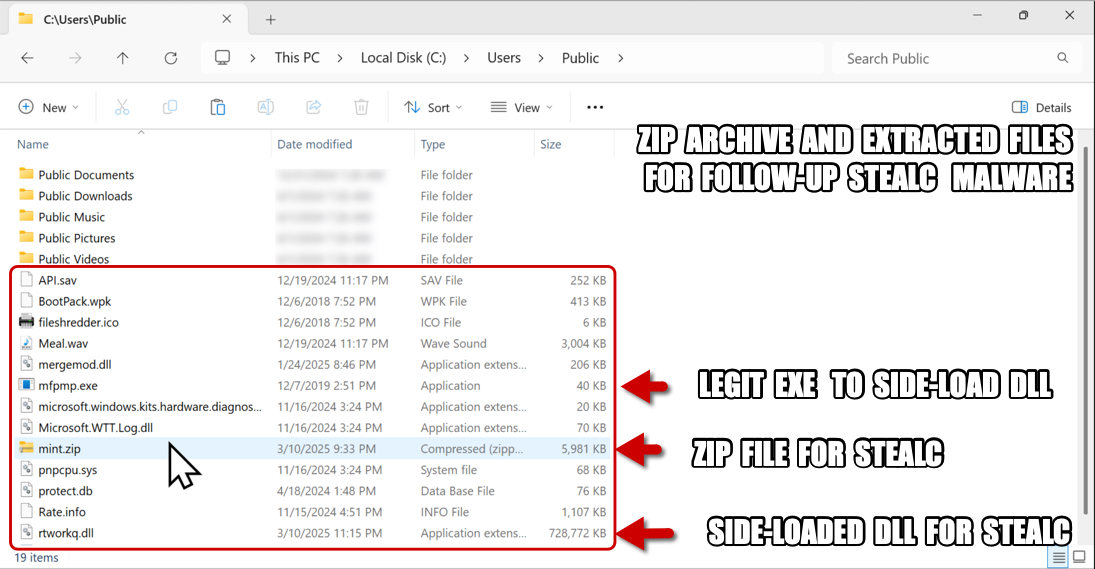
Shown above: Location of zip archive and extracted files for follow-up StealC malware.
2025-03-26 (WEDNESDAY): SMARTAPESG TRAFFIC FOR FAKE BROWSER UPDATE LEADS TO NETSUPPORT RAT AND STEALC
REFERENCES:
- https://www.threatdown.com/blog/smartapesg-06-11-2024/
- https://blogs.vmware.com/security/2023/11/netsupport-rat-the-rat-king-returns.html
- https://malpedia.caad.fkie.fraunhofer.de/details/win.stealc
NOTES:
- SmartApeSG is also known as ZPHP or HANEYMANEY
LEGITIMATE BUT COMPROMISED SITE WITH INJECTED SCRIPT FOR SMARTAPESG:
- hxxps[:]//www.freepetchipregistry[.]com/
TRAFFIC FOR FAKE WEBSITE CAUSED BY INJECTED SCRIPT FOR SMARTAPESG:
- hxxp[:]//layardrama21[.]top/upload/lib.css.js
- hxxp[:]//layardrama21[.]top/upload/index.php?
- hxxp[:]//layardrama21[.]top/upload/assets/css/index.css
- hxxp[:]//layardrama21[.]top/upload/assets/img/microsoft.png
- hxxp[:]//layardrama21[.]top/upload/assets/img/hero-img_desktop%203.png
- hxxp[:]//layardrama21[.]top/upload/assets/js/index.js
- hxxp[:]//layardrama21[.]top/upload/assets/img/edge-bg.png
EXAMPLE OF DOWNLOADED JS FILE:
- SHA256 hash: 68c6411cc9afa68047641932530cf7201f17029167d4811375f1458cae32c7bd
- File size: 831,080 bytes
- File name: Edge 50728.js
- File type: ASCII text, with very long lines
- File description: Installer script for NetSupport RAT
EXAMPLE OF URL GENERATED BY DOWNLOADED JS FILE FOR NETSUPPORT RAT:
- hxxps[:]//sleepwellmagazine[.]com/2mprext.zip?&track=608
ZIP ARCHIVE FOR NETSUPPORT RAT:
- SHA256 hash: 4c048169e303dc3438e53e5abdec31b45b5184f05dc6d1bc39e18caa0e4a3f3e
- File size: 4,041,429 bytes
- File location: hxxps[:]//sleepwellmagazine[.]com/2mprext.zip?&track=608
- File type: Zip archive data, at least v2.0 to extract
- File description: Zip archive for NetSupport RAT retrieved by script installer
NETSUPPORT RAT POST-INFECTION TRAFFIC:
- 194.180.191[.]168 port 443 - POST hxxp[:]//194.180.191[.]168/fakeurl.htm
ZIP ARCHIVE FOR STEALC MALWARE SENT THROUGH NETSUPPORT RAT C2 TRAFFIC:
- SHA256 hash: 45085f479b048dd0ef48bef5b8c78618113bc19bde6349f61d184cdf4331bff0
- File size: 6,124,223 bytes
- File location: C:\Users\Public\misk.zip
- File type: Zip archive data, at least v2.0 to extract
- File description: Zip archive for StealC sent through NetSupport RAT C2 traffic
LEGITIMATE FILE FROM THE ABOVE ZIP ARCHIVE USED FOR DLL SIDE LOADING:
- SHA256 hash: ff7e8ccc41bc3a506103bdd719a19318bf711351ac0e61e1f1cf00f5f02251d5 <-- not malicious
- File size: 40,480 bytes
- File name: mfpmp.exe
- File type: PE32 executable (GUI) Intel 80386, for MS Windows
- File description: Legitimate Windows file for Media Foundation Protected Pipeline EXE
- Note: This file is not malicious, but an old Windows system EXE used to side-load a malware DLL named rtworkq.dll
MALICIOUS DLL FOR STEALC SIDE-LOADED BY THE ABOVE LEGITIMATE EXE:
- SHA256 hash: 2bc17933b9dd18627610a509736f8cf6c149338be5f6bd3d475ea22d0d914ae3
- File size: 746,262,016 bytes
- File name: rtworkq.dll
- File type: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
- File description: Malicious, inflated DLL
- Run method: Inflated StealC malware side loaded by mfpmp.exe
ABOVE DLL, DEFLATED WITH ALL OF THE PADDING REMOVED:
- SHA256 hash: 1ae8f9d618d9b5c7ef474b815a857afebbb9e06b54bdf13726280942501cb48b
- File size: 1,773,056 bytes
FOLLOW-UP STEALC TRAFFIC:
- hxxp[:]//193.239.237[.]40/
- hxxp[:]//193.239.237[.]40/52a50518b868057e.php <-- HTTP POST requests for data exfiltration, repeats several times
Hex value in URL is different for each infected host
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/sqlite3.dll
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/freebl3.dll
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/mozglue.dll
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/msvcp140.dll
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/nss3.dll
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/softokn3.dll
- hxxp[:]//193.239.237[.]40/ca8e51ecb2d000b2/vcruntime140.dll
- NOTES:
-- The above URLs ending in .dll all host legitimate 3rd party DLLs used by StealC during an infection.
-- Those URLs ending in .dll depend on the applications installed on the infected Windows host.
Click here to return to the main page.
