2014-06-20 - 32X32 GATE TO ANGLER EK ON 107.181.246[.]213 - L7QRZ.HONIGIWACE[.]INFO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
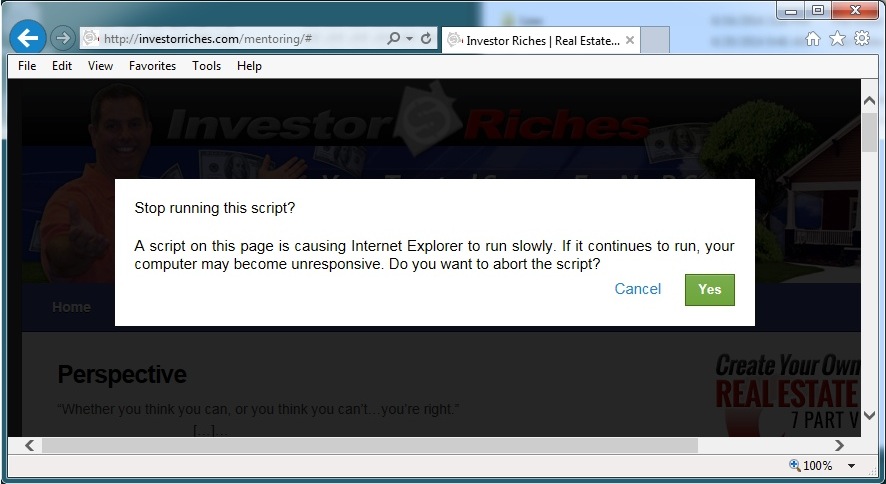
- Today revealed another 32-byte by 32-byte PHP EK Gate with HTTP POST leading to Angler EK
- This one has a different pop-up than the previous ones noted on 2014-05-07 and 2014-05-13.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 198.57.149[.]88 - investorriches[.]com - Compromised website
- 88.80.190[.]66 - quemooono[.]com - 32x32 gate
- 107.181.246[.]213 - l7qrz.honigiwace[.]info - Angler EK
- 62.109.24[.]233:443 - nosanoarick[.]ru - Post-infection HTTPS traffic
- 62.109.27[.]104 - activababy[.]ru - Post-infection call for more malware
COMPROMISED WEBSITE AND 32X32 GATE:
- 16:23:59 - 198.57.149[.]88:80 - investorriches[.]com - GET /mentoring/
- 16:24:04 - 88.80.190[.]66:80 - quemooono[.]com - POST /219aeeaac37e73188691349bae82334c.php?q=35bd0ba4240a085cef06bd956e544143
ANGLER EK:
- 16:24:05 - 107.181.246[.]213:80 - l7qrz.honigiwace[.]info - GET /unc9xdig1e
- 16:24:09 - 107.181.246[.]213:80 - l7qrz.honigiwace[.]info - GET /ZQjSBe3KjRk54Bm8nyKC2w_xWH9yzn5peZUe-AD5STRbcfMiuw8yNo3mdCThqyS1
- 16:24:19 - 107.181.246[.]213:80 - l7qrz.honigiwace[.]info - GET /rwoZFh5SJ3iiwgb7_eow3M9N6wborqlSjNzyG2wVUElzFY1JQ7EMCK6NTgmJSPU0
- 16:24:34 - 107.181.246[.]213:80 - l7qrz.honigiwace[.]info - GET /ImqmC4Yq9oC0mo0r0M8IEXh19BQbcc1m8FQ403qrZqx-ZnYKl-bcBqOX7IknbNUQ
- 16:24:34 - 107.181.246[.]213:80 - l7qrz.honigiwace[.]info - GET /ImqmC4Yq9oC0mo0r0M8IEXh19BQbcc1m8FQ403qrZqx-ZnYKl-bcBqOX7IknbNUQ
- 16:24:37 - 107.181.246[.]213:80 - l7qrz.honigiwace[.]info - GET /9TxUt-0mlM8oQVdbPtBtrvmRa3JIFQb7stOxeI_FOFmmeuwWNyI8JakgHZfY2CMU
POST-INFECTION TRAFFIC:
- 16:24:25 - 62.109.24[.]233:443 - nosanoarick[.]ru - HTTPS traffic
- 16:24:25 - 62.109.24[.]233:443 - nosanoarick[.]ru - HTTPS traffic
- 16:24:31 - yandex[.]ru - GET /
- 16:24:32 - www.yandex[.]ru - GET /
- 16:24:36 - 62.109.27[.]104:80 - activababy[.]ru - GET /run.exe
- 16:24:41 - 62.109.27[.]104:80 - activababy[.]ru - GET /install.exe [repeats with 404 Not found response]
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
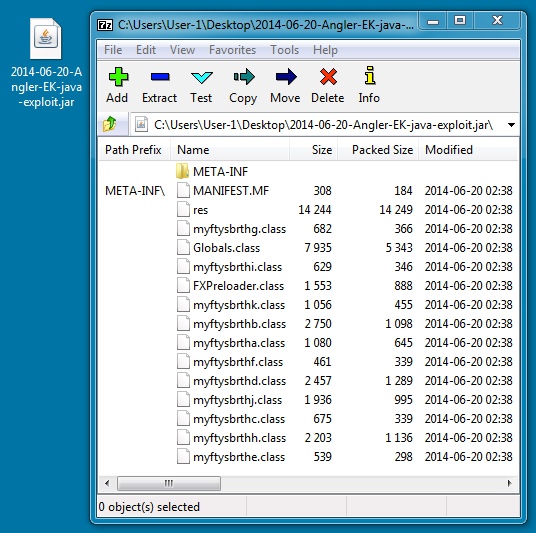
File name: 2014-06-20-Angler-EK-java-exploit.jar
File size: 29,867 bytes
MD5 hash: cf0f7176f40114ee288d7dd4599e926e
Detection ratio: 9 / 53
First submission: 2014-06-21 00:35:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/f4b35756b9f6ea204ca4ff9f69b0df1ec350033e79eb0d00b384443643488254/analysis/
SILVERLIGHT EXPLOIT
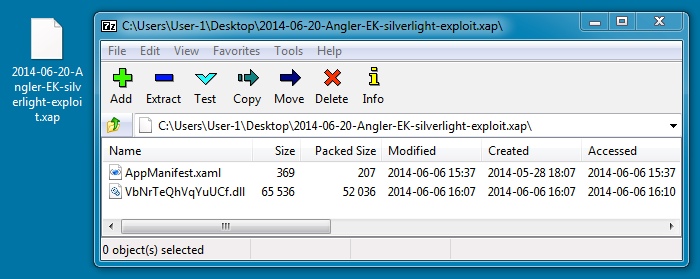
File name: 2014-06-20-Angler-EK-silverlight-exploit.xap
File size: 52,690 bytes
MD5 hash: 98119bc927fe32313a87d6b808a29539
Detection ratio: 3 / 54
First submission: 2014-06-12 12:51:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/3ae82bd0a8eee6d0273d121008dc0968344fcac78bd62ea371178c1e8a1a5017/analysis/
MALWARE PAYLOAD
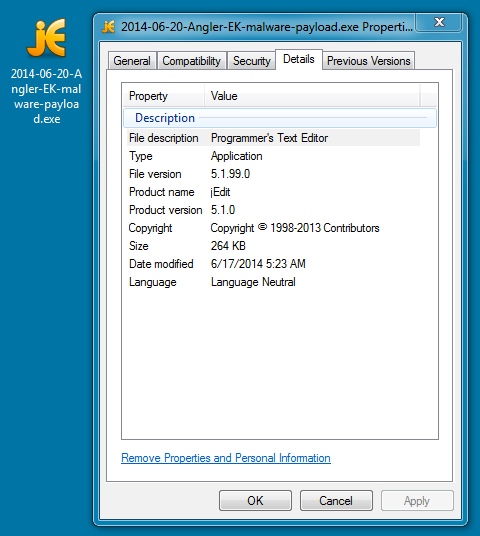
File name: 2014-06-20-Angler-EK-malware-payload.exe
File size: 270,336 bytes
MD5 hash: 7cde5ff3c884e019e6d718cbc4029f14
Detection ratio: 9 / 54
First submission: 2014-06-21 00:36:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/6c2ecb7bf4130a76179b249c5f227069aa3096d9bfcfd52c6f7b9c3d0bf8dd4f/analysis/
FOLLOW-UP MALWARE
File name: run.exe
File size: 591,360 bytes
MD5 hash: 001bf7b9889d7115baf5ca0206ddfd7e
Detection ratio: 21 / 54
First submission: 2014-06-21 00:36:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/529d49f591cc1558705e0b5f6da1f193d75d693ec432c50bad5e5ddf1e036204/analysis/
ALERTS
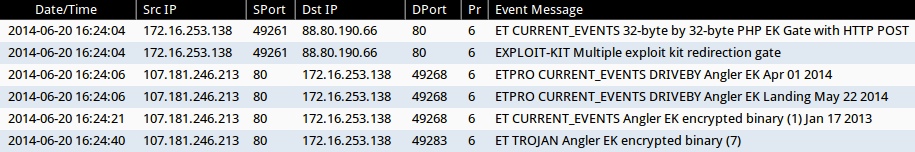
Emerging Threats and ETPRO rulesets:
- 2014-06-20 16:24:04 UTC - 88.80.190[.]66:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2014-06-20 16:24:06 UTC - 107.181.246[.]213:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 2014-06-20 16:24:06 UTC - 107.181.246[.]213:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Landing May 22 2014 (sid:2808076)
- 2014-06-20 16:24:21 UTC - 107.181.246[.]213:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 2014-06-20 16:24:40 UTC - 107.181.246[.]213:80 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset:
- 2014-06-20 16:24:04 UTC - 88.80.190[.]66:80 - EXPLOIT-KIT Multiple exploit kit redirection gate (sid:30920)
NOTE: These alerts were taken from Sguil on Security Onion
Click here to return to the main page.