2014-05-27 - FIESTA EK FROM 64.202.116[.]151 - BETTERS[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Checked one of the compromised websites I posted about on 2014-05-22 to get an update on Fiesta EK.
CHAIN OF EVENTS
COMPROMISED WEBSITE AND REDIRECT:
- 03:24:26 UTC - 166.78.152[.]216 - undertone[.]com - GET /
- 03:24:27 UTC - 75.102.9[.]195 - maggyrt[.]com - GET /cPL7qUmnKH.js?53kV8RErh=0d47182c45bd6d8f1de770e6b8
FIESTA EK:
- 03:24:31 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/2
- 03:24:35 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/4f822c66d5ea25d247115e09005801010d5e030650530d03075e0c02060500;120000;38
- 03:24:36 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/6abeaf25b7c2f63f450d145e535d05020f5959510356090005595655550004;5110411
- 03:24:37 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/6ae02f691990138d55110e0b005d010e0f595e0450560d0c05595100060000;6
- 03:24:38 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/6ae02f691990138d55110e0b005d010e0f595e0450560d0c05595100060000;6;1
- 03:24:46 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/4d9ffce61990138d5714525d545852010d5c025204535e03075c0d56520553;5
- 03:24:47 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/4d9ffce61990138d5714525d545852010d5c025204535e03075c0d56520553;5;1
- 03:24:48 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/6350735389f80ae65c5d590b050802040f0b0e0455030e06050b0100035503
- 03:24:48 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/67cc0abf4c1489a259580158025a55510f0f585752515953050f5753055155
- 03:24:48 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/67cc0abf4c1489a259580158025a55510f0f585752515953050f5753055155
- 03:24:49 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/099d79a0731c393d53415c5f050256070901025055095a0503010d54035f57;1;3
- 03:24:50 UTC - 64.202.116[.]151 - betters[.]in[.]ua - GET /v20idaf/099d79a0731c393d53415c5f050256070901025055095a0503010d54035f57;1;3;1
NOTES:
- I didn't see any activity from the sandbox analysis, so I ran the malware payload on a physical host.
- Nothing exciting happened, but I got the following traffic:
- 2014-05-27 04:23:45 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:23:50 UTC - 67.51.218[.]185:80 - kuqqqgskcsmkgyai[.]org - POST / HTTP/1.1
- 2014-05-27 04:23:53 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:24:09 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:24:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:24:54 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:25:10 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:25:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:25:19 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:25:20 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:25:24 UTC - 67.51.218[.]185:80 - kuqqqgskcsmkgyai[.]org - POST / HTTP/1.1
- 2014-05-27 04:25:36 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:25:41 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:25:53 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:26:09 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:26:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:26:20 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:26:35 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:26:40 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:26:53 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:27:09 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:27:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:27:20 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:27:35 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:27:40 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:27:54 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:28:10 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:28:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:28:20 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:28:35 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:28:38 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:28:53 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:29:09 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:29:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:29:20 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:29:35 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:29:40 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:29:54 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:30:10 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:30:14 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:30:20 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:30:34 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:30:39 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:30:54 UTC - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:31:09 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:33:22 UTC - 74.125.227.240:80 - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:33:24 UTC - 74.125.227.240:80 - www.google[.]com - GET / HTTP/1.1
- [Restarted the computer]
- 2014-05-27 04:33:26 UTC - 107.14.36.129:80 - www.msftncsi[.]com - GET /ncsi.txt HTTP/1.1
- 2014-05-27 04:33:29 UTC - 178.18.26[.]16:80 - kuqqqgskcsmkgyai[.]org - POST / HTTP/1.1
- 2014-05-27 04:33:29 UTC - 74.125.227.240:80 - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:33:44 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:33:49 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:34:24 UTC - 74.125.227.240:80 - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:34:38 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:34:43 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- 2014-05-27 04:35:24 UTC - 74.125.227.240:80 - www.google[.]com - GET / HTTP/1.1
- 2014-05-27 04:35:40 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET / HTTP/1.1
- 2014-05-27 04:35:44 UTC - 79.143.87[.]185:80 - wonder-search[.]com - GET /search.png HTTP/1.1
- [Repeats]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-05-27-Fiesta-EK-flash-exploit.swf
File size: 10,046 bytes
MD5 hash: 91292f649c23ff7339c35d5651862643
Detection ratio: 0 / 53
First submission: 2014-05-27 03:41:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/599906e03b0931f5de0abee134a4d990ec995681dd2f334074f217328ae265f4/analysis/
File name: 2014-05-27-Fiesta-EK-flash-exploit-uncompressed.swf
File size: 15,609 bytes
MD5 hash: 89881e33e533068bde2416b6a641bcbe
Detection ratio: 0 / 53
First submission: 2014-05-27 03:42:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/e3e812cf2bd17710e9f370573591d7b9c8129b97b4a3623799f6ca2745216500/analysis/
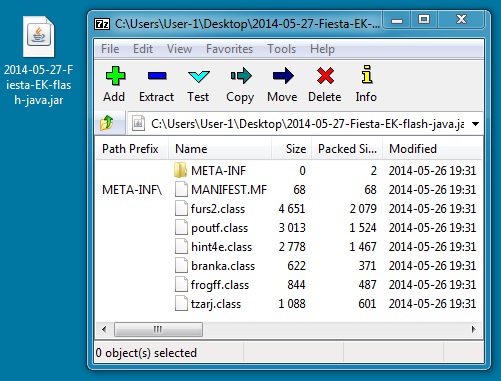
JAVA EXPLOIT
File name: 2014-05-27-Fiesta-EK-flash-java.jar
File size: 7,561 bytes
MD5 hash: c0447d6f0ffd94e2c4268c457e9aff90
Detection ratio: 1 / 51
First submission: 2014-05-27 03:40:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/6558539a9a51512893875aa977fa7591c441698587929da815c1f61bc73677b1/analysis/
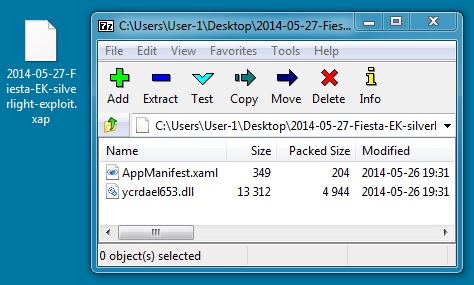
SILVERLIGHT EXPLOIT
File name: 2014-05-27-Fiesta-EK-silverlight-exploit.xap
File size: 5,382 bytes
MD5 hash: d5504c146e1c906d02dc9309d6b49249
Detection ratio: 7 / 51
First submission: 2014-05-27 03:40:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/e552576f2ca29102e793304a3fba50add822d4bb11a9b7488d4ce40279575458/analysis/
MALWARE PAYLOAD
File name: 2014-05-27-Fiesta-EK-malware-payload.exe
File size: 271,360 bytes
MD5 hash: 62e1eccb403a08c55d619c7ea5e44c5d
Detection ratio: 2 / 53
First submission: 2014-05-27 03:40:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/97e10f7c6e9e3e5c994276bad0a1bbf5dfce2719fc043d01bc53ef68546c8be8/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
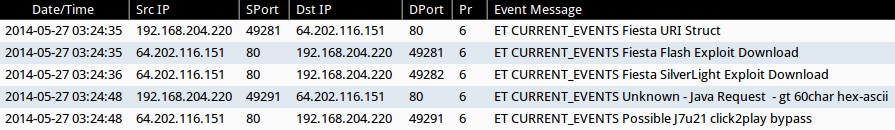
- 2014-05-27 03:24:35 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-05-27 03:24:35 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-05-27 03:24:36 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-05-27 03:24:48 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-05-27 03:24:48 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
Click here to return to the main page.