2014-11-13 - UPATRE/DYRE INFECTION FROM EMAIL ATTACHMENTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-13-Upatre-Dyre-malspam-tracking.csv.zip 1.3 kB (1,250 bytes)
- 2014-11-13-infection-traffic-in-a-VM.pcap.zip 576.7 kB (576,688 bytes)
- 2014-11-13-malware-and-artifacts-from-the-infection.zip 680.7 kB (680,723 bytes)
NOTES:
- On 2014-11-13 from 10:44 to 11:27 UTC, I saw at least 878 malicious emails with a subject line: You have received a new secure message from BankLine#[8-digit number].
- These emails all contain links to malware, and the URLs ended with: /bankline/message.php
- The links generated a zip file download containing Upatre
- Today's post-infection traffic is similar to previous campaigns that dropped Dyre malware.
- Conrad Longmore reported a similar ADP-themed campaign yesterday at: blog.dynamoo.com/2014/11/adp-past-due-invoice39911564-spam.html
Downloading the Upatre
PREVIOUS BLOG POSTS:
- 2014-09-26 - Upatre/Dyre infection from email attachments
- 2014-10-03 - Upatre/Dyre infection from email attachments
- 2014-10-04 - Rig EK and Upatre/Dyre from phishing emails [emails dated 2014-10-02]
EMAILS SEEN FROM THIS CAMPAIGN
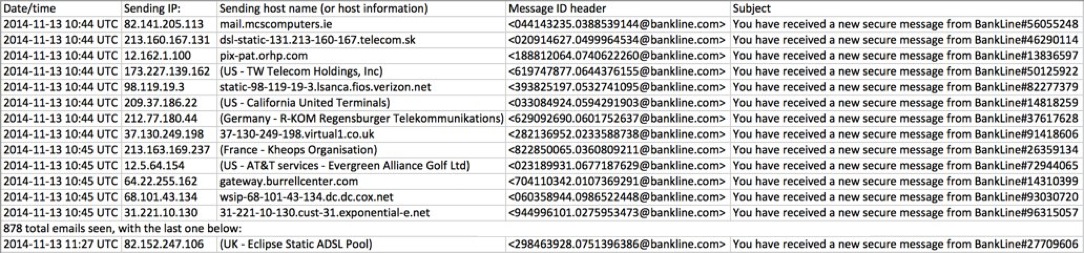
All had a spoofed sender: <secure.message@bankline[.]com>
- 2014-11-13 10:44 UTC - 82.141.205[.]113 - mail.mcscomputers.ie - <044143235.0388539144@bankline[.]com>
- 2014-11-13 10:44 UTC - 213.160.167[.]131 - dsl-static-131.213-160-167.telecom.sk - <020914627.0499964534@bankline[.]com>
- 2014-11-13 10:44 UTC - 12.162.1[.]100 - pix-pat.orhp[.]com - <188812064.0740622260@bankline[.]com>
- 2014-11-13 10:44 UTC - 173.227.139[.]162 - (US - TW Telecom Holdings, Inc) - <619747877.0644376155@bankline[.]com>
- 2014-11-13 10:44 UTC - 98.119.19[.]3 - static-98-119-19-3.lsanca.fios.verizon.net - <393825197.0532741095@bankline[.]com>
- 2014-11-13 10:44 UTC - 209.37.186[.]22 - (US - California United Terminals) - <033084924.0594291903@bankline[.]com>
- 2014-11-13 10:44 UTC - 212.77.180[.]44 - (Germany - R-KOM Regensburger Telekommunikations) - <629092690.0601752637@bankline[.]com>
- 2014-11-13 10:44 UTC - 37.130.249[.]198 - 37-130-249-198.virtual1.co.uk - <282136952.0233588738@bankline[.]com>
- 2014-11-13 10:45 UTC - 213.163.169[.]237 - (France - Kheops Organisation) - <822850065.0360809211@bankline[.]com>
- 2014-11-13 10:45 UTC - 12.5.64[.]154 - (US - AT&T services - Evergreen Alliance Golf Ltd) - <023189931.0677187629@bankline[.]com>
- 2014-11-13 10:45 UTC - 64.22.255[.]162 - gateway.burrellcenter[.]com - <704110342.0107369291@bankline[.]com>
- 2014-11-13 10:45 UTC - 68.101.43[.]134 - wsip-68-101-43-134.dc.dc.cox.net - <060358944.0986522448@bankline[.]com>
- 2014-11-13 10:45 UTC - 31.221.10[.]130 - 31-221-10-130.cust-31.exponential-e.net - <944996101.0275953473@bankline[.]com>
- 878 total emails seen, with the last one below:
- 2014-11-13 11:27 UTC - 82.152.247[.]106 - (UK - Eclipse Static ADSL Pool) - <298463928.0751396386@bankline[.]com>
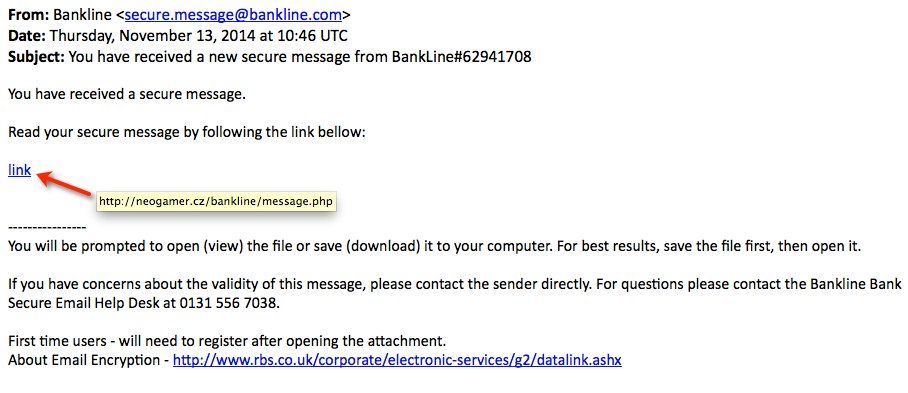
SCREENSHOT FROM ONE OF THE EMAILS:
MESSAGE TEXT FROM ONE OF THE EMAILS:
From: Bankline <secure.message@bankline[.]com>
Date: Thursday, November 13, 2014 at 10:46 UTC
Subject: You have received a new secure message from BankLine#62941708
You have received a secure message.
Read your secure message by following the link bellow:
link
----------------
You will be prompted to open (view) the file or save (download) it to your computer. For best results, save the file first, then open it.
If you have concerns about the validity of this message, please contact the sender directly. For questions please contact the Bankline Bank Secure Email Help Desk at 0131 556 7038.
First time users - will need to register after opening the attachment.
About Email Encryption - hxxp[:]//www.rbs[.]co[.]uk/corporate/electronic-services/g2/datalink.ashx
SOME OF THE LINKS FROM THESE PHISHING EMAILS:
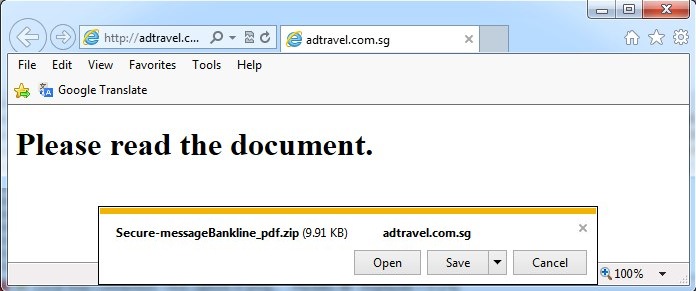
- adtravel[.]com[.]sg - GET /bankline/message.php
- dudok[.]nl - GET /bankline/message.php
- neogamer[.]cz - GET /bankline/message.php
- wp.zontown[.]com - GET /bankline/message.php
PRELIMINARY MALWARE ANALYSIS
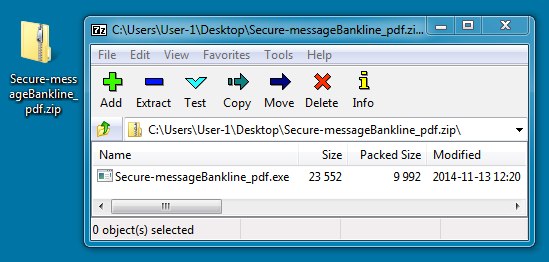
DOWNLOADED ZIP FILE:
File name: Secure-messageBankline_pdf.zip
File size: 10,150 bytes
MD5 hash: f4df9e9ca2c91ba5e826111014d1b1c5
Detection ratio: 21 / 55
First submission: 2014-11-13 10:48:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/2ad9176032de039207d41bafa83b10907ade9c771a478d42b620082fbae3a165/analysis/
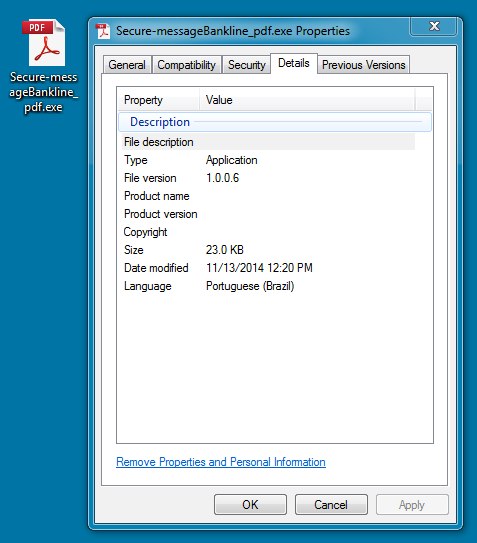
EXTRACTED MALWARE:
File name: Secure-messageBankline_pdf.exe
File size: 23,552 bytes
MD5 hash: c852dff3e4de04eb3a230cd560094d59
Detection ratio: 21 / 53
First submission: 2014-11-13 10:49:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/7f771a240dab091da8af9ec07b10a97079864c45564259ee7ca827d4cfd387a2/analysis/
DROPPED FILES ON THE INFECTED VM:
- C:\Windows\EXE1.INI (0 bytes)
- C:\Windows\OccUbCFuCHafSpy.exe (503,808 bytes)
- C:\Windows\OccUbCFuCHafSpy.INI (0 bytes)
- C:\Users\User-1\AppData\Local\Microsoft\Windows\Temporary Internet Files\cluk2[1].pmg (encrypted file - 365,308 bytes)
- C:\Users\User-1\AppData\Local\Temp\utt2FCD.tmp (encrypted file, 365,308 bytes - same as above file)
- C:\Users\User-1\AppData\Local\Temp\ogtur.exe (this is where the extracted malware copied itself)
DROPPED EXE:
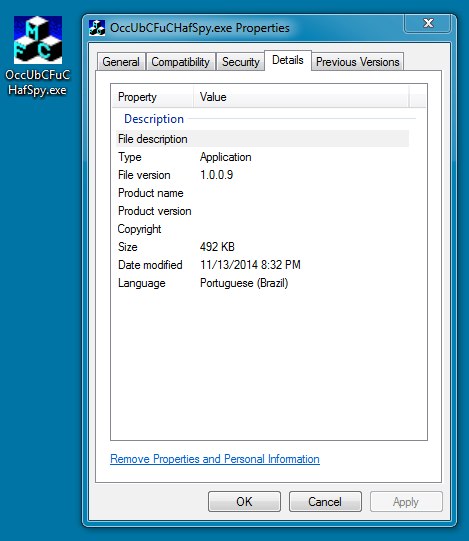
File name: C:\Windows\OccUbCFuCHafSpy.exe
File size: 503,808 bytes
MD5 hash: ca075266749ad6303092ba177177aef3
Detection ratio: 15 / 55
First submission:
VirusTotal link: https://www.virustotal.com/en/file/b642644ca6ba8509b49e0093119190dd2e39130fd5ee2c96b81bb44457f57f39/analysis/
INFECTION TRAFFIC ON A VM
DOWNLOADING THE MALWARE:
- 2014-11-13 20:29:24 UTC - 180.210.201[.]107:80 - adtravel[.]com[.]sg - GET /bankline/message.php
- 2014-11-13 20:29:24 UTC - 180.210.201[.]107:80 - adtravel[.]com[.]sg - GET /favicon.ico
- 2014-11-13 20:29:24 UTC - 180.210.201[.]107:80 - adtravel[.]com[.]sg - POST /bankline/message.php
- 2014-11-13 20:29:26 UTC - 94.23.50[.]48:80 - counter1.statcounterfree[.]com - GET /private/counter.js?c=3cd91faa08a440e1eaaed230a22225c0
- 2014-11-13 20:29:26 UTC - 94.23.50[.]48:8080 - counter1.statcounterfree[.]com:8080 - GET /private/pointeur/pointeur.gif?|[long string of characters]
- 2014-11-13 20:29:26 UTC - 94.23.50[.]48:80 - counter1.freecounterstat[.]com - GET /private/counter.php?c=[long string of characters]
- 2014-11-13 20:29:27 UTC - 180.210.201[.]107:80 - adtravel[.]com[.]sg - GET /bankline/message.php?h=900&w=1440&ua=[long string of characters]
POST-INFECTION TRAFFIC AFTER RUNNING THE MALWARE:
- 2014-11-13 20:32:35 UTC - 188.165.206[.]208 - 188.165.206[.]208:27648 - GET /1311uk2/WIN-QSL42S1ENZ/0/61-SP1/0/
- 2014-11-13 20:32:36 UTC - 188.165.206[.]208 - 188.165.206[.]208:27648 - GET /1311uk2/WIN-QSL42S1ENZ/1/0/0/
- 2014-11-13 20:32:36 UTC - 109.237.138[.]18:80 - enrico-roeske[.]de - GET /requests/cluk2.pmg
- 2014-11-13 20:32:37 UTC - 78.46.70[.]51:80 - santaic8.kilu[.]de - GET /img/cluk2.pmg
- 2014-11-13 20:35:50 UTC - 162.242[.]252.170:80 - icanhazip[.]com - GET /
- 2014-11-13 20:35:50 UTC - 104.156[.]231.126:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:36:36 UTC - 104.156.231[.]126:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:37:37 UTC - 104.156.231[.]126:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:38:18 UTC - 94.23.63[.]195:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:38:20 UTC - 94.23.63[.]195:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:38:36 UTC - 94.23.63[.]195:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:38:38 UTC - 94.23.63[.]195:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:10 UTC - 94.23.63[.]195:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:11 UTC - 94.23.63[.]195:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:22 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:24 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:25 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:25 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:26 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:28 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:28 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:29 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:39:33 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:42:41 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
- 2014-11-13 20:45:58 UTC - 108.61.199[.]190:4443 - encrypted (possible HTTPS) traffic
POST-INFECTION STUN (SESSION TRAVERSAL UTILITIES for NAT) TRAFFIC OVER UDP:
- 2014-11-13 20:32:50 193.28[.]184.4:3478 - STUN traffic to: stun.ipshka[.]com
- 2014-11-13 20:33:25 107.23[.]150.92:3478 - STUN traffic to: stun.stunprotocol.org
- 2014-11-13 20:33:59 217.10.68[.]152:3478 - STUN traffic to: stun.sipgate.net
- 2014-11-13 20:34:34 77.72.174[.]163:3478 - STUN traffic to: stun.voipbuster[.]com
- 2014-11-13 20:35:08 198.27.81[.]168:3478 - STUN traffic to: stun.callwithus[.]com
SNORT EVENTS FROM THE INFECTED VM
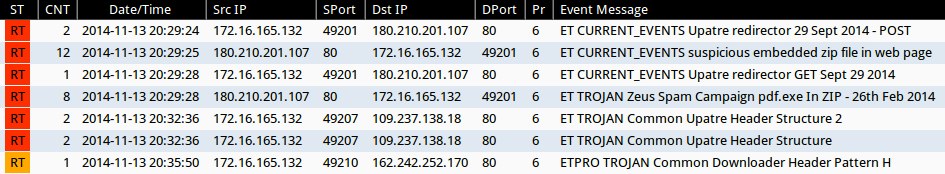
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-11-13 20:29:24 UTC - 180.210.201[.]107:80 - ET CURRENT_EVENTS Upatre redirector 29 Sept 2014 - POST (sid:201932)
- 2014-11-13 20:29:25 UTC - 180.210.201[.]107:80 - ET CURRENT_EVENTS suspicious embedded zip file in web page (sid:2019324)
- 2014-11-13 20:29:28 UTC - 180.210.201[.]107:80 - ET CURRENT_EVENTS Upatre redirector GET Sept 29 2014 (sid:2019311)
- 2014-11-13 20:29:28 UTC - 180.210.201[.]107:80 - ET TROJAN Zeus Spam Campaign pdf.exe In ZIP - 26th Feb 2014 (sid:2018182)
- 2014-11-13 20:32:36 UTC - 109.237.138[.]18:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 2014-11-13 20:32:36 UTC - 109.237.138[.]18:80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 2014-11-13 20:35:50 UTC - 162.242.252[.]170:80 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-11-13 20:29:24 UTC - 180.210.201[.]107:80 - [1:32129:1] MALWARE-CNC Win.Trojan.Downloader variant download attempt
- 2014-11-13 20:32:39 UTC - 78.46.70[.]51 - [139:1:1] (spp_sdf) SDF Combination Alert
- 2014-11-13 20:35:50 UTC - 104.156.231[.]126:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE (x14)
- 2014-11-13 20:35:50 UTC - 104.156.231[.]126:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD (x14)
Click here to return to the main page.