2015-03-01 - MAGNITUDE EK - 188.138.68[.]68 - EFD6D9.02.3F.9874379.73336DA.A6800E.7B.XRDIP554S7QW.MATTERHANDLES[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Malware samples from today's Magnitude EK are the same as seen previously on 2015-02-13 (link): CryptoWall 3.0, Redyms/Ramdo, Zbot/Bunitu, and Simda.
- There are minor differences in the callback traffic for each piece of malware, and they all have different file hashes than last time.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 188.138.68[.]68 - efd6d9.02.3f.9874379.73336da.a6800e.7b.xrdip554s7qw.matterhandles[.]in - Magnitude EK
MANGITUDE EK:
- 2015-03-01 17:04:29 UTC - efd6d9.02.3f.9874379.73336da.a6800e.7b.xrdip554s7qw.matterhandles[.]in - GET /?245641425056454a57484550410a434b4b4348410a474b49
- 2015-03-01 17:04:30 UTC - efd6d9.02.3f.9874379.73336da.a6800e.7b.xrdip554s7qw.matterhandles[.]in - GET /44f20bd8ef5104400c86c084ff32e857
- 2015-03-01 17:04:31 UTC - 188.138.68[.]68 - GET /?6cf5942ee73761f8054bc23bb1e077f0
- 2015-03-01 17:04:39 UTC - 188.138.68[.]68 - GET /?50cbdd6198c70c6550c5660d9d5afd6a
- 2015-03-01 17:06:19 UTC - 188.138.68[.]68 - GET /?6cf5942ee73761f8054bc23bb1e077f0
- 2015-03-01 17:06:21 UTC - 188.138.68[.]68 - GET /?69af9cfa288261dbf4fc302bb697ec41
ALERTS
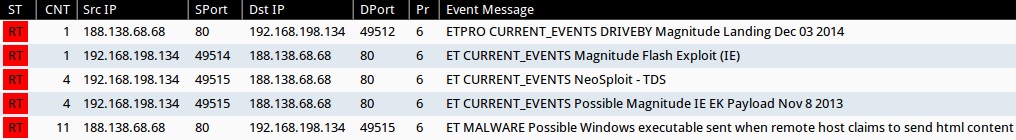
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 188.138.68[.]68 port 80 - ETPRO CURRENT_EVENTS DRIVEBY Magnitude Landing Dec 03 2014 (sid:2809273)
- 188.138.68[.]68 port 80 - ET CURRENT_EVENTS Magnitude Flash Exploit (IE) (sid:2019799)
- 188.138.68[.]68 port 80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 188.138.68[.]68 port 80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 188.138.68[.]68 port 80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 188.138.68[.]68 port 80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
- 188.138.68[.]68 port 80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 188.138.68[.]68 port 80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 188.138.68[.]68 port 80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 188.138.68[.]68 port 80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 188.138.68[.]68 port 80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request
- 188.138.68[.]68 port 80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP
- 188.138.68[.]68 port 80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-03-01-Magnitude-EK-flash-exploit.swf
File size: 10,011 bytes
MD5 hash: 5200317aadd2161c0c7e1d5a69e54475
Detection ratio: 5 / 57
First submission: 2015-03-01 17:41:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/a024fd6928d10a85826ce1f7a01f6661b6a0abfa803ee9db3458a84f239821ae/analysis/
MALWARE PAYLOAD 1 OF 4 - CRYPTOWALL 3.0 RANSOMWARE:
File name: 2015-03-01-Magnitude-EK-payload-1-of-4-CryptoWall-3.0-ransomware.exe
File size: 139,776 bytes
MD5 hash: 6c2221cf298fa4fcf58e696bc09ebe51
Detection ratio: 7 / 57
First submission: 2015-03-01 17:41:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/c67ba1bce6777005635f02739c731d39d94c97a8ccacb475cf4b9dfe22017327/analysis/
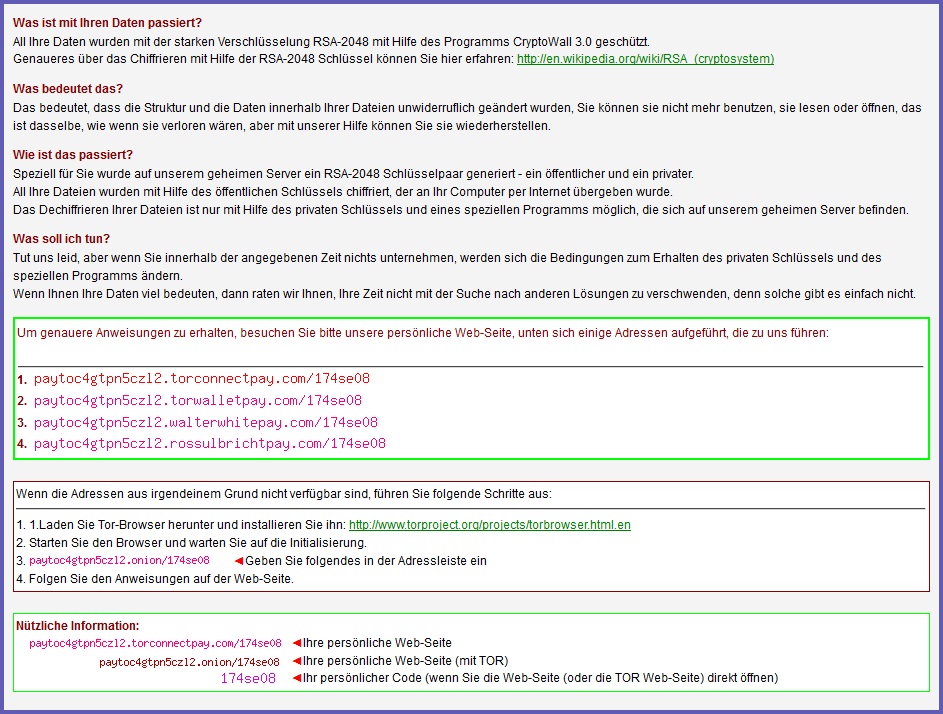
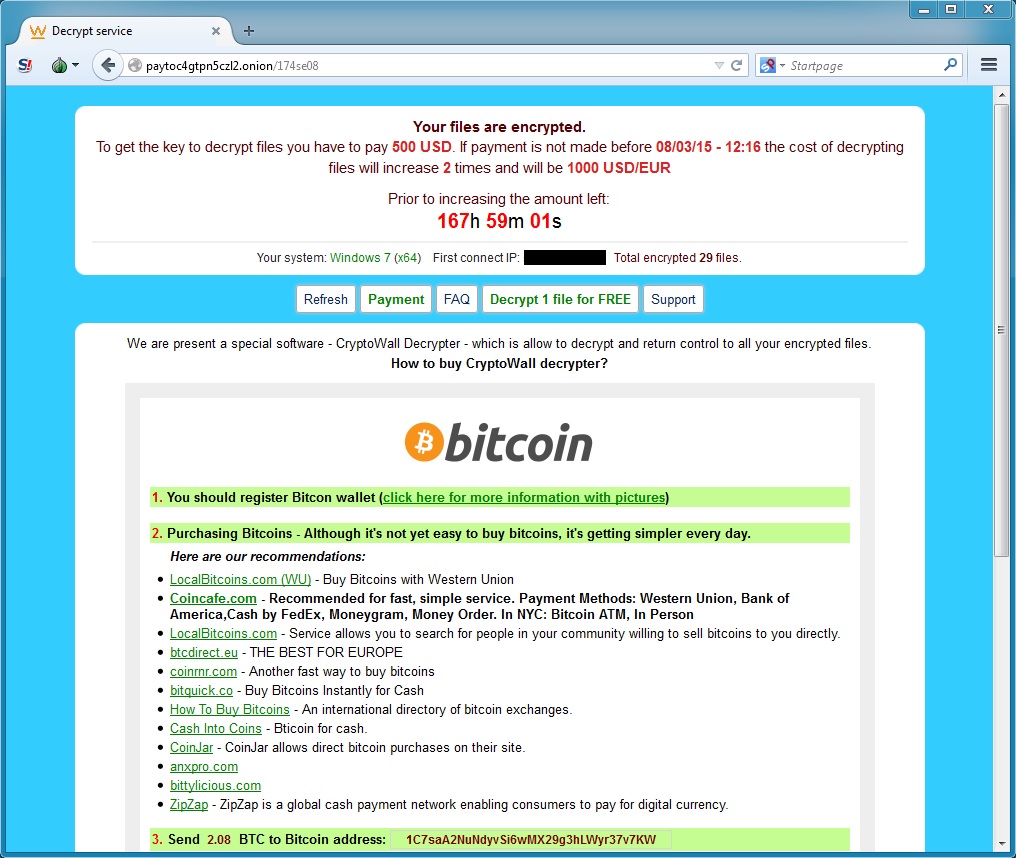
- Bitcoin address for ransomware payment: 1C7saA2NuNdyvSi6wMX29g3hLWyr37v7KW
- Looks like someone has paid ransom to this account: https://blockchain.info/address/1C7saA2NuNdyvSi6wMX29g3hLWyr37v7KW
Post-infection traffic:
- 2015-03-01 19:48:49 UTC - myexternalip[.]com - GET /raw
- 2015-03-01 19:48:49 UTC - 176.31.96[.]224 port 80 - le4um[.]com - POST /img1.php?n=4r7yelv4et89
- 2015-03-01 19:49:11 UTC - 162.144.77[.]82 port 80 - itsafixation[.]com - POST /img2.php?r=4r7yelv4et89
- 2015-03-01 19:49:12 UTC - 91.234.34[.]28 port 80 - freebie[.]net[.]ua - POST /img1.php?d=4r7yelv4et89
- 2015-03-01 19:49:16 UTC - 176.31.96[.]224 port 80 - le4um[.]com - POST /img1.php?u=ozooywrl78x4j
- 2015-03-01 19:49:37 UTC - 162.144.77[.]82 port 80 - itsafixation[.]com - POST /img2.php?q=ozooywrl78x4j
- 2015-03-01 19:49:38 UTC - 91.234.34[.]28 port 80 - freebie[.]net[.]ua - POST /img1.php?e=ozooywrl78x4j
- 2015-03-01 19:49:43 UTC - 176.31.96[.]224 port 80 - le4um[.]com - POST /img1.php?f=46wp4teaoei
- 2015-03-01 19:50:00 UTC - google[.]com - GET /
- 2015-03-01 19:50:01 UTC - www.google[.]co[.]uk - GET /?gfe_rd=cr&ei=aG3zVPL1M8Go8wfU54CoCA
- 2015-03-01 19:50:04 UTC - 162.144.77[.]82 port 80 - itsafixation[.]com - POST /img2.php?o=46wp4teaoei
- 2015-03-01 19:50:05 UTC - 91.234.34[.]28 port 80 - freebie[.]net[.]ua - POST /img1.php?z=46wp4teaoei
- 2015-03-01 19:51:14 UTC - 193.25.112[.]225 port 80 - hoinar[.]info - POST /img2.php?y=k83l3eevau8q
- 2015-03-01 19:51:15 UTC - 183.111.161[.]85 port 80 - basofttech[.]com - POST /renew/img2.php?t=k83l3eevau8q
- 2015-03-01 19:51:16 UTC - 198.154.201[.]232 port 80 - precisioncheck[.]com - POST /img5.php?e=k83l3eevau8q
- 2015-03-01 19:51:21 UTC - 176.31.96[.]224 port 80 - le4um[.]com - POST /img1.php?b=4p7h83nh4x
- 2015-03-01 19:51:22 UTC - 111.221.44[.]235 port 80 - ghostpowered[.]net - POST /img3.php?h=4p7h83nh4x
- 2015-03-01 19:51:29 UTC - 176.31.96[.]224 port 80 - le4um[.]com - POST /img1.php?w=w9odk5mk24e
- 2015-03-01 19:51:31 UTC - 111.221.44[.]235 port 80 - ghostpowered[.]net - POST /img3.php?r=w9odk5mk24e
- 2015-03-01 19:51:46 UTC - 176.31.96[.]224 port 80 - le4um[.]com - POST /img1.php?o=85f84fgeo00q7
- 2015-03-01 19:51:46 UTC - 111.221.44[.]235 port 80 - ghostpowered[.]net - POST /img3.php?i=85f84fgeo00q7
- 2015-03-01 19:52:19 UTC - DNS query for: paytoc4gtpn5czl2.torconnectpaycom [response: No such name]
Alerts:
- various IP addresses port 80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- DNS query for: paytoc4gtpn5czl2.torconnectpay[.]com - ET TROJAN Cryptowall 3.0 .onion Proxy Domain (sid:2020182)
- various IP addresses port 80 - [1:33450:2] MALWARE-CNC Win.Trojan.FileEncoder variant outbound connection
MALWARE PAYLOAD 2 OF 4 - SIMDA:
File name: 2015-03-01-Magnitude-EK-payload-2-of-4-Simda.exe
File size: 899,584 bytes
MD5 hash: 9c6b7775d502d83ca2094a8514228a90
Detection ratio: 5 / 57
First submission: 2015-03-01 17:43:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/3395bcdef72c88c9fa322aaca468508f8e390e9ed781e15ffb5a6f10ef9e051e/analysis/Post-infection traffic:
- 2015-03-01 17:51:23 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?CE5531=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:23 UTC - 94.242.253[.]106 port 80 - report.3o79my79oc7s317u3m[.]com - POST /
- 2015-03-01 17:51:37 UTC - 94.242.253[.]106 port 80 - update.0bgjbdfg4i[.]com - GET /?fb=kdajxpmmmZJkxcicl52Yy5egZ8ij[long string of characters]
- 2015-03-01 17:51:37 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?1uOCE43=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:37 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?wSKU5m20=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:37 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?7aAA79e17=%96%C6%A3%D1%AA%
- 2015-03-01 17:51:37 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?7uO1o58=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:37 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?cEI3q755=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:42 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?1i93qGM16=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:49 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?79uO709=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:50 UTC - www.bing[.]com - GET /chrome/report.html?55k5y55=%9B%EE%EDk%D9%DF[long string of characters]
- 2015-03-01 17:51:50 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?79a1725=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:50 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?e79kUO57=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:50 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?A79e63=%96%C6%A3%D1%AA[long string of characters]
- 2015-03-01 17:51:50 UTC - 198.37.114[.]178 port 80 - report.3o79my79oc7s317u3m[.]com - GET /?555e518=%96%C6%A3%D1%AA[long string of characters]
Alerts:
- 198.37.114[.]178 port 80 - ET TROJAN Simda.C Checkin (sid:2016300)
- 94.242.253[.]106 port 80 - ETPRO TROJAN Backdoor.Win32.Simda.abpn Checkin (sid:2807145)
- 198.37.114[.]178 port 80 - [1:22937:5] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- 94.242.253[.]106 port 80 - [1:26212:2] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- www.bing[.]com - [1:20661:4] MALWARE-CNC Simbda variant outbound connection
- www.bing[.]com - [1:25038:2] BROWSER-WEBKIT Apple Safari Webkit css title memory corruption attempt
MALWARE PAYLOAD 3 OF 4 - ZBOT/BUNITU VARIANT:
File name: 2015-03-01-Magnitude-EK-payload-3-of-4-Zbot-Bunitu.exe
File size: 101,307 bytes
MD5 hash: dd022fe79d034c42e457a70b2b6e4156
Detection ratio: 4 / 57
First submission: 2015-03-01 17:43:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/18f05733f2d0fefdb27cabac4ad1abe511cdee57b840a2d54b95ea319552c8d7/analysis/Post-infection traffic:
- DNS query for: ns1.dianamyinfin[.]xyz - 110.201.5[.]111 first, then 125.83.138[.]92 throughout rest of the pcap
- 2015-03-01 17:51:38 UTC - 95.211.233[.]121 port 53 - TCP traffic
- 2015-03-01 17:51:39 UTC - google[.]com - TCP connection, but no traffic
- 2015-03-01 17:51:39 UTC - 66.199.229[.]91 port 53 - TCP traffic
- 2015-03-01 17:51:41 UTC - 85.17.144[.]8 port 53 - TCP traffic
- 2015-03-01 17:51:42 UTC - 76.73.102[.]74 port 53 - TCP traffic and continues through rest of the pcap
Alerts:
- 95.211.233[.]121 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel port 53 (sid:2808226)
- 66.199.229[.]91 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 85.17.143[.]84 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 76.73.102[.]74 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 85.17.143[.]84 port 53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
- 76.73.102[.]74 port 53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
MALWARE PAYLOAD 4 OF 4 - REDYMS/RAMDO VARIANT:
File name: 2015-03-01-Magnitude-EK-payload-4-of-4-Redyms-Ramdo.exe
File size: 321,360 bytes
MD5 hash: 2ff5694af15d0bc253654094fec497d8
Detection ratio: 0 / 57
First submission: 2015-03-01 17:44:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/7cd4408e9d743e47d8fc193cb10ac591fe6612f42f669f6d8008d8ad43a879c1/analysis/Post-infection traffic:
- 2015-03-01 17:53:14 UTC - www.google[.]com GET /
- 2015-03-01 17:53:14 UTC - DNS query for: ywoqmcmwuqgysmcw[.]org [response: Server failure]
- 2015-03-01 17:53:23 UTC - www.google[.]com GET /
- 2015-03-01 17:54:10 UTC - www.google[.]com GET /
- 2015-03-01 17:54:10 UTC - DNS query for: iqumgmcqwuqgaaus[.]org [response: No such name]
- 2015-03-01 17:54:57 UTC - 166.78.144[.]80 port 80 - sksqqagakeicoeso[.]org POST /
- 2015-03-01 17:54:57 UTC - www.google[.]com GET /
- 2015-03-01 17:55:44 UTC - 192.42.116[.]41 port 80 - uoewuismooowgcui[.]org POST /
- 2015-03-01 17:55:45 UTC - www.google[.]com GET /
- 2015-03-01 17:56:32 UTC - 50.189.9[.]254 port 80 - uociwiiqgmqwwmkq[.]org POST /
- 2015-03-01 17:56:34 UTC - 50.189.9[.]254 port 80 - uociwiiqgmqwwmkq[.]org GET /04.cab
- 2015-03-01 17:56:34 UTC - 50.189.9[.]254 port 80 - uociwiiqgmqwwmkq[.]org GET /04.cab
Alerts:
- www.google[.]com - port 80 - ET WEB_CLIENT SUSPICOUS Possible automated connectivity check (www.google[.]com) (sid:2018430)
- 166.78.144[.]80 - port 80 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 192.42.116[.]41 - port 80 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 166.78.144[.]80 port 80 - ET TROJAN Connection to Georgia Tech Sinkhole IP (Possible Infected Host) (sid:2016994)
- 50.189.9[.]254 port 80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
- 166.78.144[.]80 port 80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
- 192.42.116[.]41 port 80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
- 166.78.144[.]80 port 80 - ET TROJAN Known Sinkhole Response Header (sid:2016803)
- 192.42.116[.]41 port 80 - ET TROJAN Known Sinkhole Response Header (sid:2016803)
- www.google[.]com - port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 50.189.9[.]254 port 80 - [1:30547:2] MALWARE-CNC Win.Trojan.Ramdo variant outbound connection
- 166.78.144[.]80 port 80 - [1:30547:2] MALWARE-CNC Win.Trojan.Ramdo variant outbound connection
- 192.42.116[.]41 port 80 - [1:30547:2] MALWARE-CNC Win.Trojan.Ramdo variant outbound connection
- 166.78.144[.]80 port 80 - [1:25018:3] BLACKLIST Connection to malware sinkhole
- 192.42.116[.]41 port 80 - [1:30320:1] BLACKLIST Connection to malware sinkhole
SCREENSHOTS
Images from the CryptoWall 3.0 ransomware infection:
Click here to return to the main page.