2015-09-11 - BIZCN GATE ACTOR NEUTRINO EK FROM 46.108.156[.]189 PORT 32393 - SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-09-11-BizCN-gate-actor-Neutrino-EK-traffic-sends-CryptoWall-3.0-ransomware-traffic.pcap.zip 412.5 kB (412,459 bytes)
- 2015-09-11-BizCN-gate-actor-Neutrino-EK-and-CryptoWall-3.0-ransomware-files.zip 268.1 kB (268,118 bytes)
NOTES:
- The BizCN gate actor I've been tracking switched from Nuclear EK to Neutrino EK since I last posted about this group.
- Today, the BizCN gate actor sent CryptoWall 3.0 ransomware
- Bitcoin payment address for this CryptoWall 3.0 ransomware sample is: 1GL5LyWc3ZfxSEC2HZjoJoGR2CJhbWPTxp
- My previous blog posts tracking the BizCN gate actor, back when it was doing Nuclear EK:
- 2015-07-05 - BizCN gate actor using Nuclear EK (documenting BizCN gate actor's switch from Fiesta EK to Nuclear EK in June 2015)
- 2015-07-07 - BizCN gate actor Nuclear EK on 107.191.63[.]163 - various domains
- 2015-07-08 - BizCN gate actor Nuclear EK on 108.61.188[.]92 - newsolar[.]ga
- 2015-07-09 - BizCN gate actor Nuclear EK on 104.238.187[.]29 - alefreed[.]ml
- 2015-07-13 - BizCN gate actor Nuclear EK on 185.92.220[.]196 - joston2[.]xyz
- 2015-07-14 - BizCN gate actor Nuclear EK on 108.61.167[.]124 - andrian2[.]xyz
- 2015-07-15 - BizCN gate actor Nuclear EK on 104.207.131[.]131 - foundhere[.]xyz & namesoizze[.]xyz
- 2015-07-16 - BizCN gate actor Nuclear EK on 216.170.114[.]126 - imhed[.]xyz
- 2015-07-17 - BizCN gate actor Nuclear EK on 188.166.120[.]33 - andsoresto[.]link
- 2015-07-30 - BizCN gate actor Nuclear EK on 46.101.18[.]39 - mukasore[.]xyz & florenses[.]xyz
- 2015-08-14 - BizCN gate actor Nuclear EK on 89.238.181[.]74 - free3dprint[.]cf
- 2015-08-19 - BizCN gate actor Nuclear EK on 31.214.157[.]20 - blizfone[.]cf
- 2015-08-28 - BizCN gate actor examples (Nuclear EK on 5.175.196[.]167 - bidgerhol[.]ml)
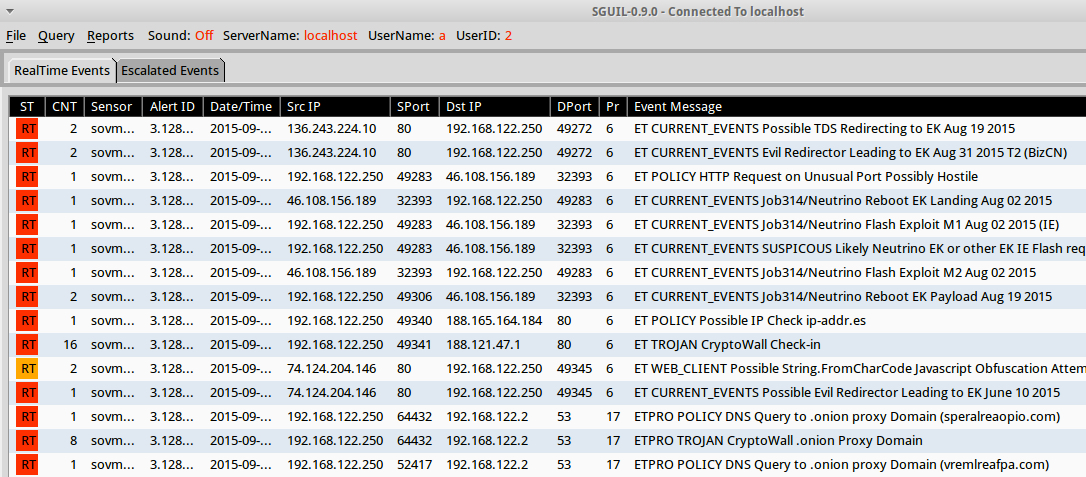
Shown above: Alerts from Sguil on Security Onion after using tcpreplay on a pcap of today's infection traffic.
TRAFFIC
ASSOCIATED DOMAINS:
- forums.macnn[.]com - Compromised website
- 136.243.224[.]10 port 80 - kroentro[.]com - BizCN-registered gate
- 46.108.156[.]189 port 32393 - wotpga.zukonline[.]xyz - Neutrino EK
- ip-addr[.]es - IP address check by CryptoWall 3.0 ransomware
- 188.121.47[.]1 port 80 - g6securitysystems[.]com - CryptoWall 3.0 ransomware callback
- 74.124.204[.]146 port 80 - essayspro[.]com - CryptoWall 3.0 ransomware callback
- 192.232.249[.]212 port 80 - europe-academy[.]net - CryptoWall 3.0 ransomware callback
- 50.63.95[.]1 port 80 - greenevap[.]com - CryptoWall 3.0 ransomware callback
- 95.128.181[.]13 port 80 - ayh2m57ruxjtwyd5.speralreaopio[.]com - User checking a page for the decrypt instructions
- 95.128.181[.]13 port 80 - ayh2m57ruxjtwyd5.vremlreafpa[.]com - User checking a page for the decrypt instructions
- ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - Domain for one of the decrypt instructions pages (didn't resolve in DNS)
- ayh2m57ruxjtwyd5.askhoreasption[.]com - Domain for one of the decrypt instructions pages (didn't resolve in DNS)
COMPROMISED WEBSITE AND REDIRECT:
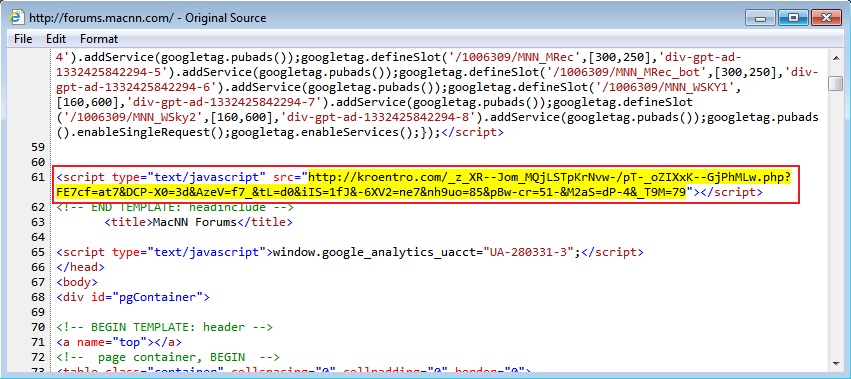
- 2015-09-11 14:39:38 UTC - forums.macnn[.]com - GET /
- 2015-09-11 14:39:40 UTC - kroentro[.]com - GET /_z_XR--Jom_MQjLSTpKrNvw-/pT-_oZIXxK--GjPhMLw.php?FE7cf=at7&DCP-X0=3d&AzeV=f7_&tL=d0&
iIS=1fJ&-6XV2=ne7&nh9uo=85&pBw-cr=51-&M2aS=dP-4&_T9M=79
NEUTRINO EK:
- 2015-09-11 14:39:41 UTC - wotpga.zukonline[.]xyz:32393 - GET /till/1668395/amuse-stiff-standard-poor-jump-merry-hopeful-describe-dignity-knight
- 2015-09-11 14:39:41 UTC - wotpga.zukonline[.]xyz:32393 - GET /your/Zmt0Ymc
- 2015-09-11 14:39:43 UTC - wotpga.zukonline[.]xyz:32393 - GET /disturb/1060788/manner-weep-yield-march-rusty-since
- 2015-09-11 14:39:43 UTC - wotpga.zukonline[.]xyz:32393 - GET /amidst/1099567/gown-thomas-noble-type-being-loud
- 2015-09-11 14:39:44 UTC - wotpga.zukonline[.]xyz:32393 - GET /pant/ZnNpb3N6Yms
POST-INFECTION TRAFFIC CAUSED BY THE CRYPTOWALL 3.0 RANSOMWARE PAYLOAD:
- 2015-09-11 14:40:10 UTC - ip-addr[.]es - GET /
- 2015-09-11 14:40:11 UTC - g6securitysystems[.]com - POST /js/ap4.php?u=1rn6826qnv6955
- 2015-09-11 14:40:13 UTC - g6securitysystems[.]com - POST /js/ap4.php?h=8w1ij5m720mwm
- 2015-09-11 14:40:17 UTC - g6securitysystems[.]com - POST /js/ap4.php?k=ssws25wpv4f
- 2015-09-11 14:40:27 UTC - g6securitysystems[.]com - POST /js/ap4.php?j=m3f5emniccq9
- 2015-09-11 14:40:28 UTC - essayspro[.]com - POST /css/fonts/ap4.php?k=m3f5emniccq9
- 2015-09-11 14:40:33 UTC - europe-academy[.]net - POST /wp-admin/user/ap2.php?c=m3f5emniccq9
- 2015-09-11 14:40:36 UTC - greenevap[.]com - POST /mtqzpa/templates/ap5.php?i=m3f5emniccq9
THE USER TRYING TO VIEW EACH OF THE WEB PAGES FOR THE CRYPTOWALL 3.0 RANSOMWARE DECRYPT INSTRUCTIONS (ALL 4 OF THEM):
- 2015-09-11 14:40:42 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /[information removed]
- 2015-09-11 14:40:44 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/style.css
- 2015-09-11 14:40:44 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/flags/us.png
- 2015-09-11 14:40:45 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/flags/es.png
- 2015-09-11 14:40:45 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/flags/de.png
- 2015-09-11 14:40:45 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/flags/it.png
- 2015-09-11 14:40:45 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/flags/fr.png
- 2015-09-11 14:40:45 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /picture.php?k=[information removed]&cbcbdb758f54dd280349a331fc51b3a4
- 2015-09-11 14:40:47 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/lb.png
- 2015-09-11 14:40:47 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/rb.png
- 2015-09-11 14:40:47 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/rt.png
- 2015-09-11 14:40:47 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/lt.png
- 2015-09-11 14:40:49 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /favicon.ico
- 2015-09-11 14:40:53 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - POST /[information removed]
- 2015-09-11 14:40:54 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/bitcoin.png
- 2015-09-11 14:40:56 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/button_pay.png
- 2015-09-11 14:41:04 UTC - ayh2m57ruxjtwyd5.speralreaopio[.]com - GET /img/button_pay_sel.png
- 2015-09-11 14:41:24 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /[information removed]
- 2015-09-11 14:41:26 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/style.css
- 2015-09-11 14:41:26 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/us.png
- 2015-09-11 14:41:27 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/fr.png
- 2015-09-11 14:41:27 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/it.png
- 2015-09-11 14:41:27 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/es.png
- 2015-09-11 14:41:27 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/de.png
- 2015-09-11 14:41:27 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /picture.php?k=[information removed]&5633a89c802878b092604ca1d8c5727a
- 2015-09-11 14:41:28 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/lt.png
- 2015-09-11 14:41:29 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/rt.png
- 2015-09-11 14:41:29 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/lb.png
- 2015-09-11 14:41:29 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/rb.png
- 2015-09-11 14:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /favicon.ico
- 2015-09-11 14:41:34 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - POST /[information removed]
- 2015-09-11 14:41:36 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/bitcoin.png
- 2015-09-11 14:41:36 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/button_pay.png
- 2015-09-11 14:41:48 UTC - DNS query for: ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com (DNS reply: No such name)
- 2015-09-11 14:41:52 UTC - DNS query for: ayh2m57ruxjtwyd5.askhoreasption[.]com (DNS reply: Server failure)
Click here to return to the main page.
