2015-09-14 - BIZCN GATE ACTOR NEUTRINO EK FROM 46.108.156[.]189 PORT 35827 - KXHGOKBJQC.UOQBZFYXDCT[.]CF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-09-14-BizCN-gate-actor-Neutrino-EK-sends-CryptoWall-3.0-ransomware.pcap.zip 362.7 kB (362,666 bytes)
- 2015-09-14-Neutrino-EK-and-CryptoWall-3.0-ransomware-files.zip 240.5 kB (240,502 bytes)
NOTES:
- The BizCN gate actor still using Neutrino EK since I last blogged about it on Friday, 2015-09-11.
- Just like last time, the BizCN gate actor sent CryptoWall 3.0 ransomware.
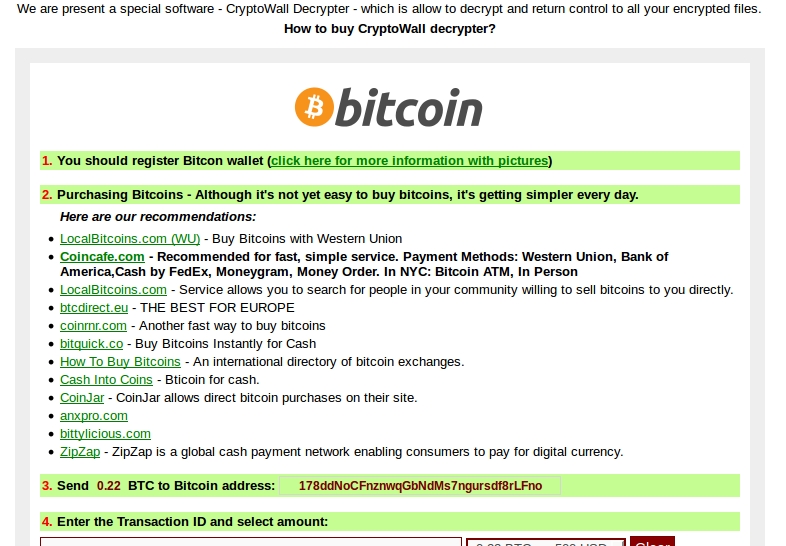
- Bitcoin payment address for this CryptoWall 3.0 ransomware sample is: 178ddNoCFnznwqGbNdMs7ngursdf8rLFno
- My previous blog posts tracking the BizCN gate actor sending Neutrino EK:
- 2015-09-11 - BizCN gate actor Neutrino EK from 46.108.156[.]189 port 32393 - wotpga.zukonline[.]xyz
- 2015-09-14 - BizCN gate actor Neutrino EK from 46.108.156[.]189 port 35827 - yjojvu.uoqbzfyxdct[.]cf (this blog post)
TRAFFIC
ASSOCIATED DOMAINS:
- www.i-programmer[.]info - Compromised website
- 136.243.25[.]244 port 80 - evattown[.]com - BizCN-registered gate domain
- 46.108.156[.]189 port 33509 - yjojvu.uoqbzfyxdct[.]cf - Neutrino EK
- 46.108.156[.]189 port 35827 - kxhgokbjqc.uoqbzfyxdct[.]cf - Neutrino EK
- ip-addr[.]es - IP address check by the CryptoWall 3.0 ransomware payload
- 68.178.254[.]208 port 80 - erointernet[.]com - Post-infection callback by the CryptoWall 3.0 ransomware payload
- 95.110.202[.]149 port 80 - eugeniobonato[.]com - Post-infection callback by the CryptoWall 3.0 ransomware payload
- 50.62.245[.]1 port 80 - fan-out[.]com - Post-infection callback by the CryptoWall 3.0 ransomware payload
COMPROMISED WEBSITE AND REDIRECT:
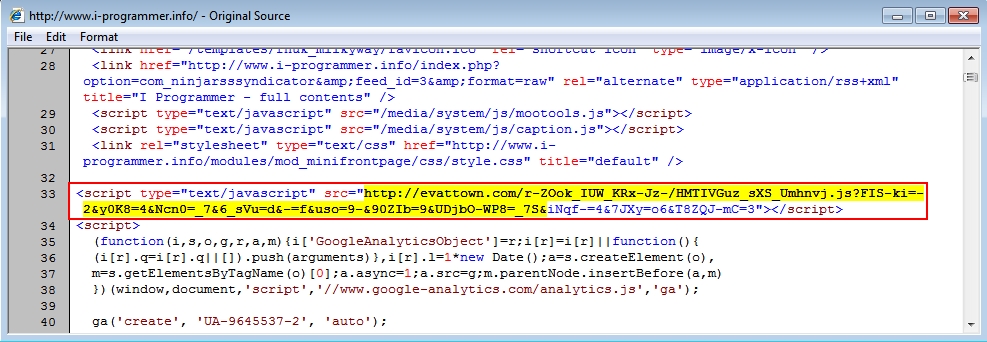
- 2015-09-14 01:56:58 UTC - www.i-programmer[.]info - GET /
- 2015-09-14 01:56:59 UTC - evattown[.]com - GET /r-ZOok_IUW_KRx-Jz-/HMTIVGuz_sXS_Umhnvj.js?FIS-ki=-2&y0K8=4&Ncn0=_7&6_sVu=d&-=f&uso=9-&90ZIb=9&UDjbO-WP8=_7S&iNqf-=4&7JXy=o6&T8ZQJ-mC=3
NEUTRINO EK:
- 2015-09-14 01:57:00 UTC - yjojvu.uoqbzfyxdct[.]cf:33509 - GET /clutch/chocolate-29356228
- 2015-09-14 01:57:01 UTC - yjojvu.uoqbzfyxdct[.]cf:33509 - GET /shade/1353042/which-terrify-further
- 2015-09-14 01:57:04 UTC - kxhgokbjqc.uoqbzfyxdct[.]cf:35827 - GET /victim/bXl2cnN2dmg
- 2015-09-14 01:57:05 UTC - kxhgokbjqc.uoqbzfyxdct[.]cf:35827 - GET /1988/12/27/attend/vein/head/weak-consider-contact-duke-abroad-judge-comment.html
- 2015-09-14 01:57:06 UTC - kxhgokbjqc.uoqbzfyxdct[.]cf:35827 - GET /flesh/1568170/visible-clerk-double-tremble-pattern-tail-drive
- 2015-09-14 01:57:18 UTC - kxhgokbjqc.uoqbzfyxdct[.]cf:35827 - GET /stre/YWRwZ29rdmV3
- 2015-09-14 01:57:18 UTC - kxhgokbjqc.uoqbzfyxdct[.]cf:35827 - GET /1999/08/31/nonsense/mental/helpless-blackness-jump.html
POST-INFECTION TRAFFIC CAUSED BY THE CRYPTOWALL 3.0 RANSOMWARE PAYLOAD:
- 2015-09-14 01:57:39 UTC - ip-addr[.]es - GET /
- 2015-09-14 01:57:39 UTC - erointernet[.]com - POST /ap2.php?c=w2qm42db13
- 2015-09-14 01:57:40 UTC - eugeniobonato[.]com - POST /wp-content/uploads/js_composer/ap3.php?p=w2qm42db13
- 2015-09-14 01:57:41 UTC - www.eugeniobonato[.]com - GET /wp-content/uploads/js_composer/ap3.php?p=w2qm42db13
- 2015-09-14 01:57:41 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?b=w2qm42db13
- 2015-09-14 01:57:43 UTC - erointernet[.]com - POST /ap2.php?z=gul17zikbot
- 2015-09-14 01:57:43 UTC - eugeniobonato[.]com - POST /wp-content/uploads/js_composer/ap3.php?b=gul17zikbot
- 2015-09-14 01:57:44 UTC - www.eugeniobonato[.]com - GET /wp-content/uploads/js_composer/ap3.php?b=gul17zikbot
- 2015-09-14 01:57:44 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?v=gul17zikbot
- 2015-09-14 01:57:46 UTC - erointernet[.]com - POST /ap2.php?a=l2d5rsof56nsts
- 2015-09-14 01:57:47 UTC - eugeniobonato[.]com - POST /wp-content/uploads/js_composer/ap3.php?o=l2d5rsof56nsts
- 2015-09-14 01:57:47 UTC - www.eugeniobonato[.]com - GET /wp-content/uploads/js_composer/ap3.php?o=l2d5rsof56nsts
- 2015-09-14 01:57:47 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?y=l2d5rsof56nsts
- 2015-09-14 01:57:58 UTC - erointernet[.]com - POST /ap2.php?f=rvzb087x6j6qw
- 2015-09-14 01:57:58 UTC - eugeniobonato[.]com - POST /wp-content/uploads/js_composer/ap3.php?y=rvzb087x6j6qw
- 2015-09-14 01:57:59 UTC - www.eugeniobonato[.]com - GET /wp-content/uploads/js_composer/ap3.php?y=rvzb087x6j6qw
- 2015-09-14 01:57:59 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?y=rvzb087x6j6qw
Click here to return to the main page.
