2015-11-06 - TRAFFIC ANALYSIS EXERCISE - EMAIL ROULETTE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2015-11-06-traffic-analysis-exercise.pcap.zip 5.2 MB (5,211,550 bytes)
- Zip archive of the emails: 2015-11-06-traffic-analysis-exercise-emails.zip 104.1 kB (104,127 bytes)
SCENARIO
You're working as an analyst at a Security Operations Center (SOC) for a Thanksgiving-themed company.
One quiet evening, you hear someone knocking at the SOC entrance. As you answer the door, an exhausted email server technician stumbles in and quickly falls to the floor. He whispers in a shaky voice, "Mail filters are down... Spam everywhere..."
As you help him up, he looks to the sky and yells, "The gates of hell have opened!"
The technician immediately collapses again and softly whispers, "The horror... The horror..."
The mail filter outage lasted throughout the next day. Fortunately, very few incidents were reported. But one example caught your eye.
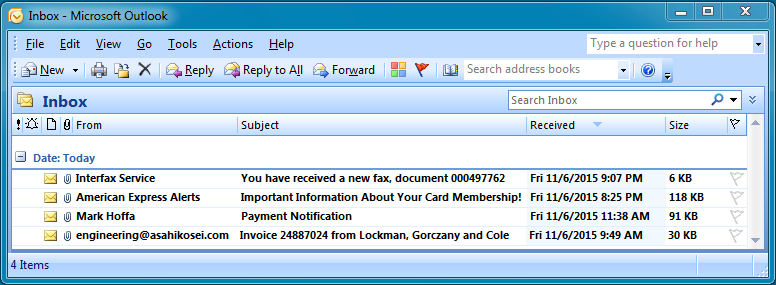
During the mail filter outage, one of the company employees decided to play "email roulette." The employee opened one of the malicious emails from his inbox and treated it as a legitimate message.
YOUR ASSIGNMENT
You've acquired four malicious messages the employee received. You also received a pcap of traffic from his infected computer. Your task? Figure out which email was used to infected his computer.
REPORTING
Be as detailed as you like. At a minimum, your report should include the following:
- Date and approximate time of the infection.
- The infected computer's IP address.
- The infected computer's MAC address.
- The infected computer's host name.
- Which email the employee opened.
ANSWERS
- Click here for the answers.
Click here to return to the main page.