2016-02-03 - EITEST ANGLER EK SENDS HYDRACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-03-EITest-Angler-EK-sends-HydraCrypt-ransomware.pcap.zip 529.3 kB (529,308 bytes)
- 2016-02-03-EITest-Angler-EK-and-HydraCrypt-ransomware-files.zip 445.7 kB (445,696 bytes)
NOTES:
- More Angler EK from the EITest actor (more info here, here, here, and here).
- The payload is a new one on me. Haven't run across "HydraCrypt" ransomware before.
- Anyone else seen this one? The email address for the ransom payment reminds me of previous FileCoder/Troldesh ransomware.
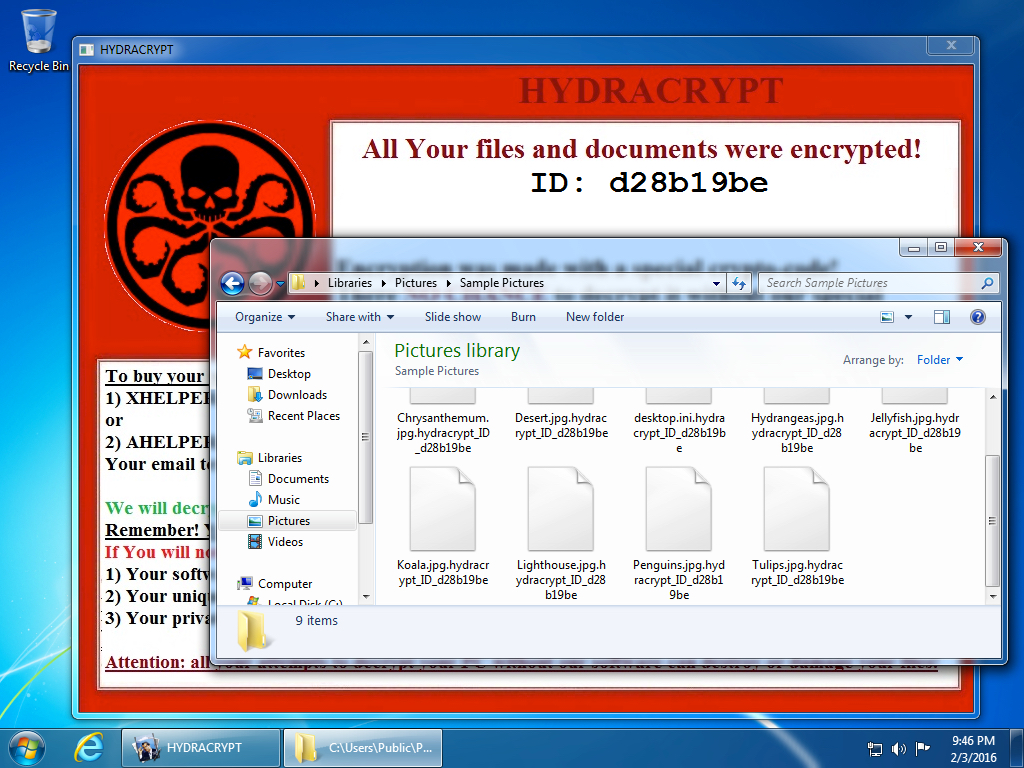
Shown above: A Windows desktop after getting infected with HydraCrypt ransomware.
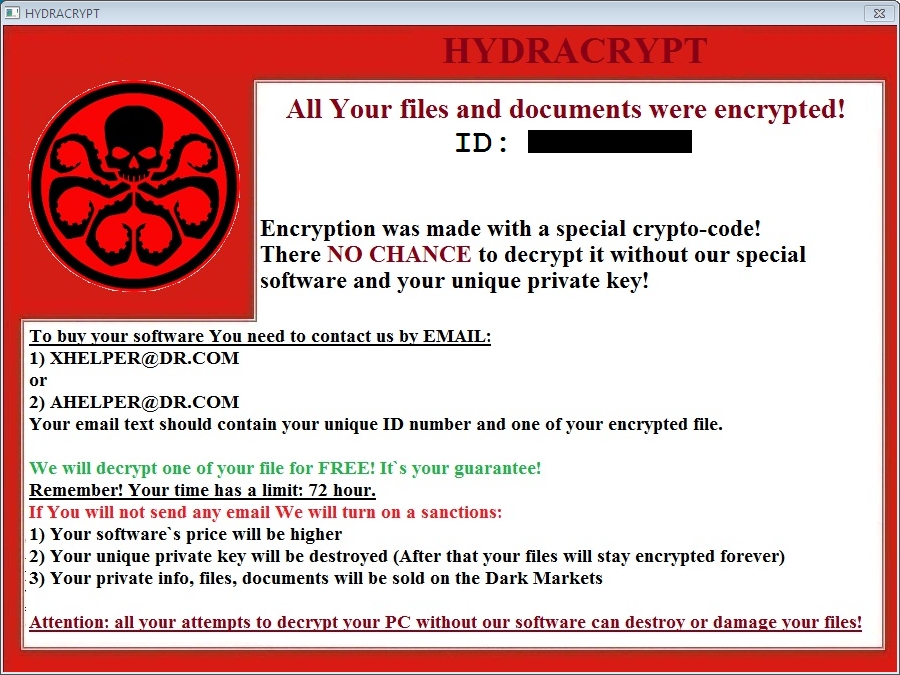
Shown above: The image/window that appeared on the Windows desktop after the infection.
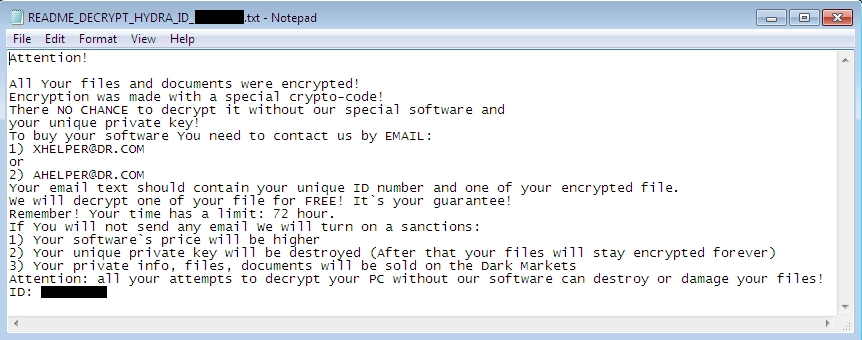
Shown above: The instructions in a text file left on the infected Windows host.
TRAFFIC
ASSOCIATED DOMAINS:
- 208.43.108[.]11 port 80 - www.harbourfrontcentre[.]com - Compromised website
- 85.93.0[.]32 port 80 - vyetbr[.]tk - EITest gate
- 86.106.93[.]66 port 80 - qywr2kr.spyscj[.]site - Angler EK
- 185.97.253[.]128 port 80 - drivers-softprotect[.]eu - HydraCrypt ransomware callback traffic
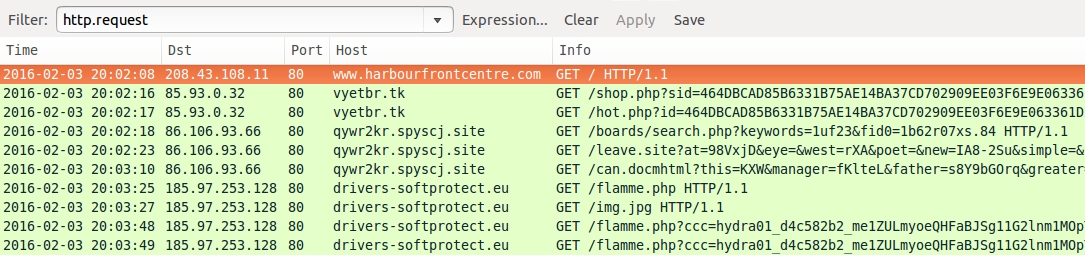
Shown above: Traffic from the infection traffic filtered in Wireshark.
COMPROMISED WEBSITE AND EITEST GATE:
- 2016-02-03 20:02:08 UTC - www.harbourfrontcentre[.]com - GET /
- 2016-02-03 20:02:16 UTC - vyetbr[.]tk - GET /shop.php?sid=464DBCAD85B6331B75AE14BA37CD702909EE03F6E9E063361D274B880AA779EC95C
51A383D2273E24C283D - 2016-02-03 20:02:17 UTC - vyetbr[.]tk - GET /hot.php?id=464DBCAD85B6331B75AE14BA37CD702909EE03F6E9E063361D274B880AA779EC95C
51A383D2273E24C283D
ANGLER EK:
- 2016-02-03 20:02:18 UTC - qywr2kr.spyscj[.]site - GET /boards/search.php?keywords=1uf23&fid0=1b62r07xs.84
- 2016-02-03 20:02:23 UTC - qywr2kr.spyscj[.]site - GET /leave.site?at=98VxjD&eye=&west=rXA&poet=&new=IA8-2Su&simple=&station=
h6ODmarvJ¢ral=HMrF3wsYO&before=iEkhWJy&ten=&night=i2iGAgd
- 2016-02-03 20:03:10 UTC - qywr2kr.spyscj[.]site - GET /can.docmhtml?this=KXW&manager=fKlteL&father=s8Y9bGOrq&greater=a6k4yXP&hope=
PoOdtJVN&place=oFO&political=5eM&south=hRmj24RoE
HYDRACRYPT RANSOMWARE POST-INFECTION TRAFFIC:
- 2016-02-03 20:03:25 UTC - drivers-softprotect[.]eu - GET /flamme.php
- 2016-02-03 20:03:27 UTC - drivers-softprotect[.]eu - GET /img.jpg
- 2016-02-03 20:03:48 UTC - drivers-softprotect[.]eu - GET /flamme.php?ccc=hydra01_[removed]_me1ZULmyoeQHFaBJSg11G2lnm1MOpTCn4B4fP
JP3ZGPUpr4HtHJxzakjeXtGc3z7qsESm8fkl3T0daZJrAhYKQTQfM4MNTLxYu1Ty6eaHFzb2dkI946mhH0hEQGhcizdO8hHTNuOJANPEB8nyvSQQr
U4h_374__0x06,[lonsg string of 0x (hexadecimal) values]/li>
SNORT/SURICATA EVENTS
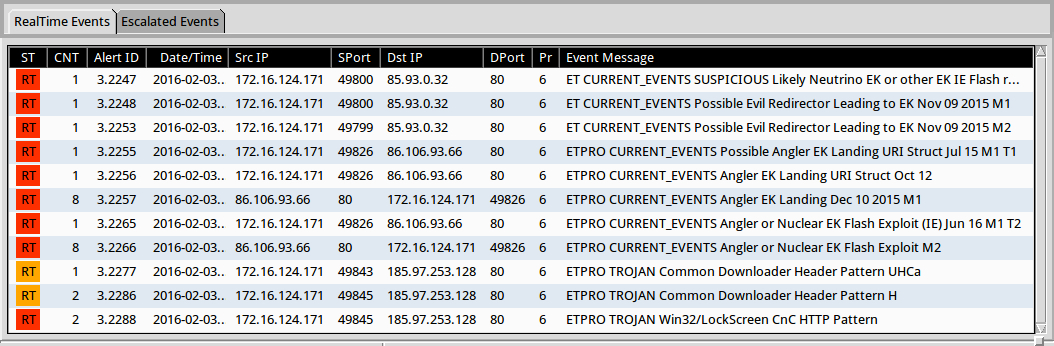
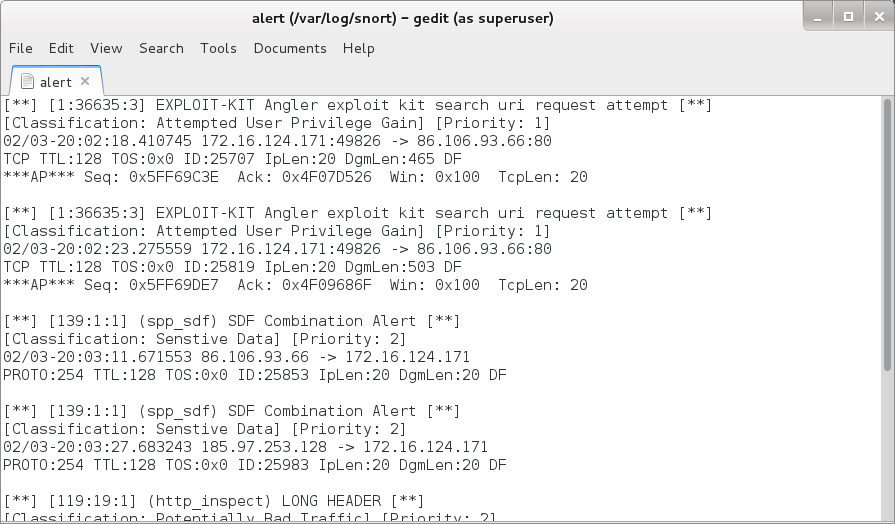
Significant signature hits from Suricata using the Emerging Threats Pro ruleset on Security Onion:
Significant signature hits from the Talos (Sourcefire VRT) registered ruleset using Snort 2.9.8.0 on Debian 7:
PRELIMINARY MALWARE ANAYSIS
ANGLER EK MALWARE PAYLOAD (HYDRACRYPT RANSOMWARE):
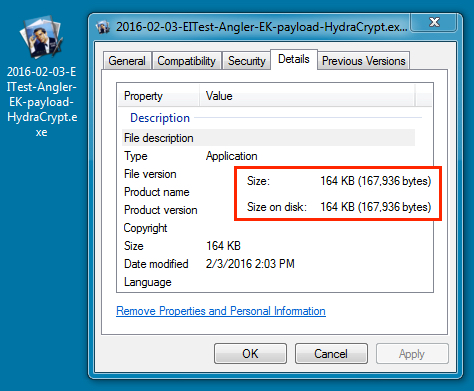
File name: 2016-02-03-EITest-Angler-EK-payload-HydraCrypt.exe
File size: 167,936 bytes
MD5 hash: 08b304d01220f9de63244b4666621bba
SHA1 hash: b7f9dd8ee3434b35fbb3395f69ff43fd5112a0c6
SHA256 hash: afd3b729cf99fb9ea441f42862a4835d1d6eeb36ee535f9b206e3a00382c972e
Detection ratio: 1 / 53 (at the time of submission)
First submission: 2016-02-03 21:24:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/afd3b729cf99fb9ea441f42862a4835d1d6eeb36ee535f9b206e3a00382c972e/analysis/
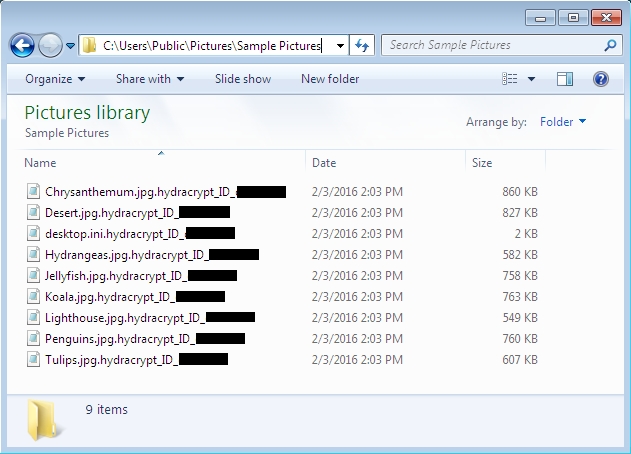
Shown above: Encrypted files were renamed, ending with .hydracrypt_ID_[8 character string].
Click here to return to the main page.