2016-08-13 - BOLETO CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2016-08-13-Boleto-campaign-traffic.pcap.zip 1.0 MB (1,023,773 bytes)
- 2016-08-13-Boleto-campaign-traffic.pcap (1,490,007 bytes)
- Zip archive of the spreasheet tracker: 2016-08-13-Boleto-campaign-email-tracker.csv.zip 1.2 kB (1,218 bytes)
- 2016-08-13-Boleto-campaign-email-tracker.csv (3,268 bytes)
- Zip archive of the emails, originally collected two days prior: 2016-08-13-Boleto-campaign-emails-17-examples.zip 23.9 kB (23,929 bytes)
- 2016-08-11-Boleto-campaign-email-2002-UTC.eml (1,826 bytes)
- 2016-08-11-Boleto-campaign-email-2021-UTC.eml (1,839 bytes)
- 2016-08-11-Boleto-campaign-email-2043-UTC.eml (1,772 bytes)
- 2016-08-11-Boleto-campaign-email-2056-UTC.eml (1,807 bytes)
- 2016-08-11-Boleto-campaign-email-2106-UTC.eml (1,855 bytes)
- 2016-08-11-Boleto-campaign-email-2120a-UTC.eml (1,811 bytes)
- 2016-08-11-Boleto-campaign-email-2120b-UTC.eml (1,795 bytes)
- 2016-08-11-Boleto-campaign-email-2123-UTC.eml (1,803 bytes)
- 2016-08-11-Boleto-campaign-email-2133-UTC.eml (1,830 bytes)
- 2016-08-11-Boleto-campaign-email-2134-UTC.eml (1,826 bytes)
- 2016-08-11-Boleto-campaign-email-2139-UTC.eml (1,799 bytes)
- 2016-08-11-Boleto-campaign-email-2206-UTC.eml (1,807 bytes)
- 2016-08-11-Boleto-campaign-email-2213-UTC.eml (1,834 bytes)
- 2016-08-11-Boleto-campaign-email-2238-UTC.eml (1,811 bytes)
- 2016-08-11-Boleto-campaign-email-2245-UTC.eml (1,815 bytes)
- 2016-08-11-Boleto-campaign-email-2325-UTC.eml (3,659 bytes)
- 2016-08-11-Boleto-campaign-email-2350-UTC.eml (1,843 bytes)
- Zip archive of the VBS file downloaded on 2016-08-13 from all of the email links: 2016-08-13-Boleto-campaign-VBS-file.zip 0.8 kB (764 bytes)
- VCTO11082016pTCy2RTDtr0dUIc0Cqetctg0GSj0Tntc.vbs (1,092 bytes)
NOTES:
- These are the same type of emails I previously documented on 2016-07-25.
- Unfortunately, for this batch, I forgot to get copies of the follow-up malware from the infected host before I wiped it.
- I'm posting this data, so there's more documentation on this campaign.
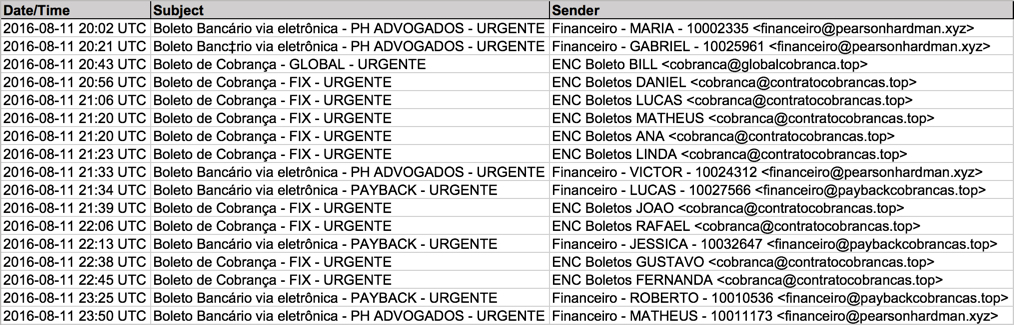
Shown above: Data from the spreadsheet (1 of 2).
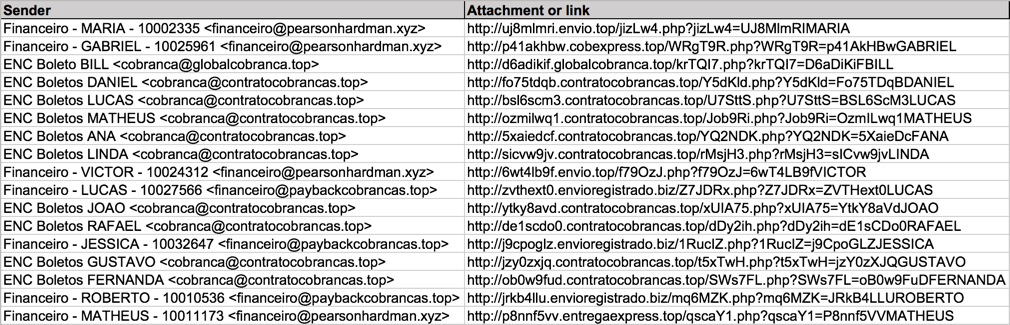
Shown above: Data from the spreadsheet (2 of 2).
TRAFFIC
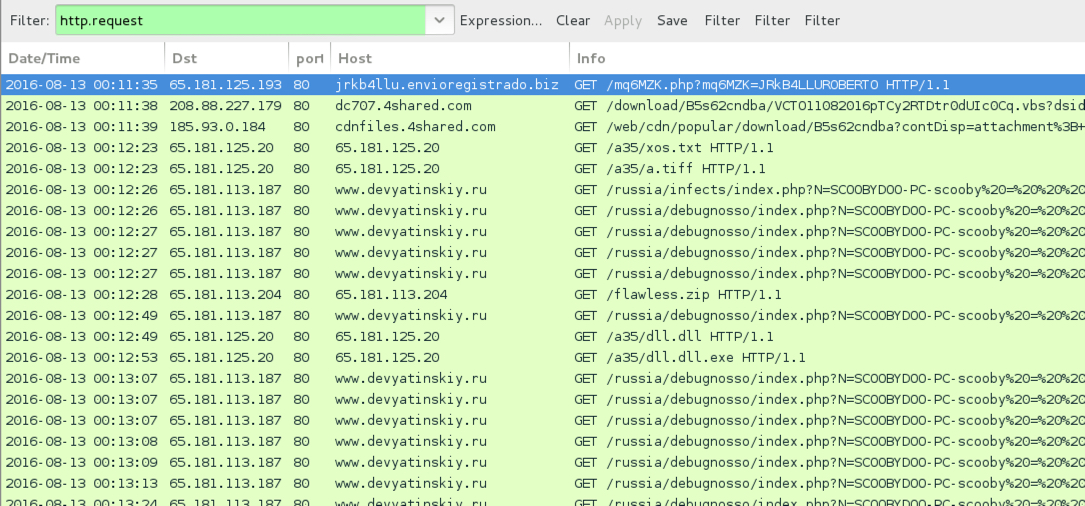
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/xos.txt
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/a.tiff
- 65.181.113[.]187 port 80 - www.devyatinskiy[.]ru - Callback domain with several different URLs containing info about the victim host
- 65.181.113[.]204 port 80 - 65.181.113[.]204 - GET /flawless.zip
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/dll.dll
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/dll.dll.exe
- 65.181.113[.]204 port 443 - ssl.houselannister[.]top - IRC chat
- 198.105.244[.]228 port 443 - xxxxxxxxxxx.localdomain - attempted TCP connections [no response]
Click here to return to the main page.
